Security Week 41: More SIM Card Vulnerabilities, PDF Decryption
 Last week, a story about attacks on vulnerable software in SIM cards was developed. The previously actively exploited SimJacker attack was not the only one discovered. Researchers at Ginno Security have reported a similar issue in the Wireless Internet Browser component ( news , company blog post). Although the vulnerability in WIB is more difficult to exploit than the problem in S @ T Browser, the method is similar: send a prepared SMS, which without the owner’s knowledge allows you to make a call, send a message or receive an IMEI phone.
Last week, a story about attacks on vulnerable software in SIM cards was developed. The previously actively exploited SimJacker attack was not the only one discovered. Researchers at Ginno Security have reported a similar issue in the Wireless Internet Browser component ( news , company blog post). Although the vulnerability in WIB is more difficult to exploit than the problem in S @ T Browser, the method is similar: send a prepared SMS, which without the owner’s knowledge allows you to make a call, send a message or receive an IMEI phone.
The first report on the vulnerability in S @ T Browser generally looked rather strange: the only company reports the problem, it is difficult to assess the potential damage, and the estimate of the number of affected devices looks exaggerated: hundreds of millions. Therefore, in the Ginno Security study, not even the vulnerability itself is important, but the confirmation of the urgency of the problem from a second source. However, another expert on mobile communications security, Carsten Noll, believes that attacks of this kind are too complicated for mass exploitation: it is easier to clone a SIM card using social engineering methods or take advantage of vulnerabilities in the SS7 protocol used by operators to communicate with each other.
Ginno Security claims to have discovered a vulnerability in the Wireless Internet Browser back in 2015, but did not publish this information. The fact is that it’s difficult to “close” vulnerabilities of such a plan: for this you need to replace the SIM-card with another one, without a problem code.
How many SIM cards are really susceptible to at least one of the two detected attacks? Ginno Security once again gives a rough estimate of "hundreds of millions" of subscriber devices. More precise figures are provided by SRLabs research. Specialists from this team collected data from more than 800 SIM-cards of various operators from different countries. It turned out that most operators no longer include vulnerable components. Only 9.4% of SIM cards have S @ T Browser installed, and 5.6% of the total number of cards examined are actually vulnerable (they don’t even have basic security features that complicate the attack). Wireless Internet Browser is installed on 10.7% of cards, 3.5% are vulnerable. In total, 9.1% of SIM cards were recognized as vulnerable. It seems a little, but if we extrapolate the results of the study to the entire mobile communications market, we will get the very hundreds of millions of subscribers.
How often is the vulnerability exploited? To evaluate, SRLabs used smartphone software that is capable of detecting a number of service SMS messages that directly access components on the SIM card. The data collected from half a million devices revealed a potential attack on 8 users who were sent 29 “prepared” messages. Most of the victims were in Latin and South America. SRLabs also develops and distributes source code software for checking SIM cards for vulnerable components (and not only), but it requires special equipment to work.
Researchers from two universities in Germany showed ( news , research ) a practical attack on encrypted PDF files, which does not depend on the software used to view documents. Both Adobe Reader and the PDF viewer in Google Chrome are equally affected. The vulnerability was found in the PDF standard itself, which also describes the process of encrypting and decrypting documents to ensure compatibility between different versions of client software.
The problem, however, does not affect the encryption method itself: in order to exploit the vulnerability, the attacker needs the PDF to be opened by the rightful owner who knows the password. But then the interactive tools provided for by the standard are involved. For example, you can embed a form in a document into which the contents of the document will be inserted after decryption and sent to the attacker. Similarly, you can embed a hyperlink or JavaScript code. Some PDF viewers block the latter scenario, but if there is no protection, the text is again sent to the attacker.
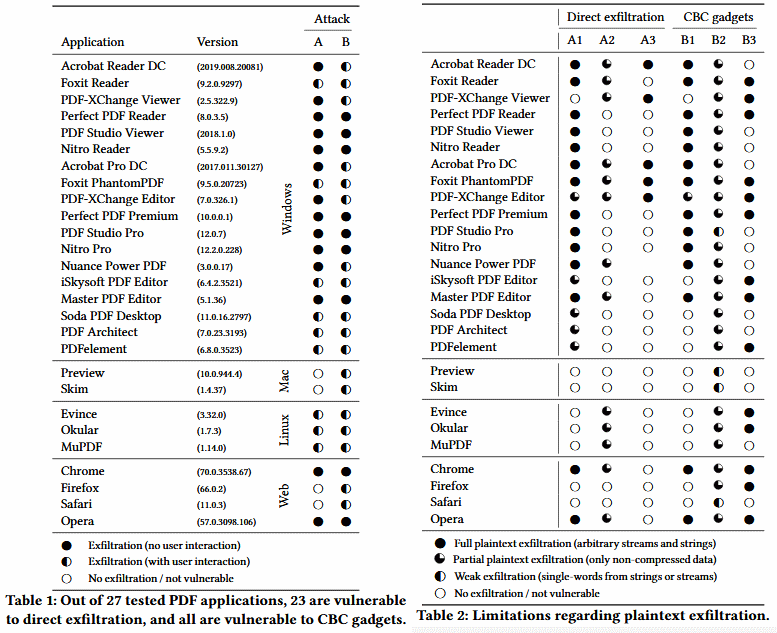
A total of six different methods were discovered for exfiltrating decrypted content. In all cases, the attacker must gain access to the encrypted file, modify the open part of the document and send the PDF to the victim. Testing of common PDF viewers showed that for everyone you can find at least one method of exfiltrating decrypted content.
Disclaimer: The opinions expressed in this digest may not coincide with the official position of Kaspersky Lab. Dear editors generally recommend treating any opinions with healthy skepticism.
All Articles