List of 25 most dangerous software vulnerabilities published

Image: Unsplash
The American organization MITRE has published a list of 25 of the most dangerous software vulnerabilities. Researchers have compiled a table of the most dangerous and common security problems, with identifiers CWE (Common Weakness Enumeration).
The top 25 got a large number of vulnerabilities that allow attackers to completely take control of computer programs, disable them and steal the data processed in them. The list allows information security professionals to better understand the landscape of security threats, but it will also be useful for software developers, testers, and users of software products.
Research methodology
To compile the list, MITRE specialists used information about published vulnerabilities (CVE, Common Vulnerabilities and Exposures), information about them from the NVD (National Vulnerability Database), and CVSS (Common Vulnerability Scoring System) vulnerability ratings. A unique algorithm was developed to assess the prevalence and severity of vulnerabilities.
Top 3 Dangerous Vulnerabilities
According to the report, the most dangerous was a vulnerability called Improper Restriction of Operations within the Bounds of a Memory Buffer. The error occurs when the software runs inside the allocated memory buffer, but at the same time gets the ability to read or write data outside the boundaries of this buffer. Exploitation of this vulnerability allows attackers to execute arbitrary code, steal critical data and completely disable software systems.
In second place in terms of danger was a vulnerability with the code CWE-79 - "Improper Neutralization of Input During Web Page Generation". Cross-site scripting (XSS) is its more common name. Vulnerabilities of this type are common and can lead to serious consequences due to lack of control over the data that users enter on the pages of the site.
In third place is the Invalid Input Validation (CWE-20) vulnerability. An attacker can make a special malicious request and the system will respond to it by providing increased privileges or access to critical data.
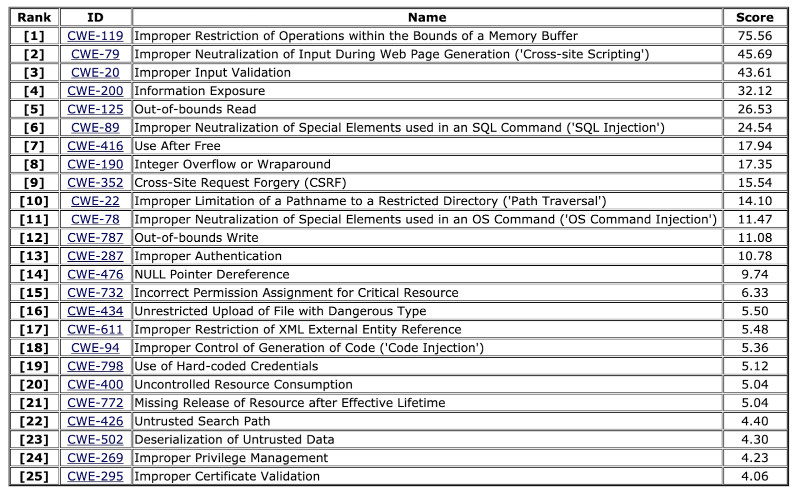
Below is a complete table of the most dangerous vulnerabilities according to MITRE.
Other relevant cyberthreats
The MITRE rating is not the only source of information about current cyber threats. Positive Technologies published a report on attacks on web applications following the results of 2018. The three most common attacks on websites included SQL Injection, Path Traversal, and Cross-Site Scripting (XSS).
In addition, Positive Technologies experts publish analytical reports on current cyber threats once a quarter. So, in the second quarter of 2019, cybercriminals actively exploited the vulnerability in the Exim mail server (CVE-2019-10149). The error is used in different ways: some attackers download cryptocurrency mining software using it, others deploy backdoors to mail servers.
- More analytical materials are available on our website .
- Full translation of MITER notes in our GitHub .
All Articles