How does Cisco monitor the information security of absorbed companies and provide their access to their resources?
Cisco has a rather aggressive strategy of absorbing companies in the market, which not only brings us revenue in key areas of our business, but also creates what foreigners like to call the word challenge, which is often translated into Russian as “challenge”. Perhaps this was once a challenge for our information security service, but now we have successfully solved this problem and I would like to share its solution in this article. The essence of the initial problem was simple - after the announcement of the takeover of any company, on average it takes about one year to fully integrate it, both from the point of view of business and from the point of view of IT infrastructure. But a year is a long enough period during which we must not only provide access to new members of our team access to corporate resources, but also ensure monitoring of the absorbed company from the point of view of information security. About how we solved this problem, I want to talk.
During the integration process, all employees of the acquired companies are required to use the Cisco AnyConnect VPN client to access all internal resources, since their networks are initially considered untrusted and do not comply with our information security requirements. At the same time, Cisco’s security policy prohibits split tunneling, which means that new employees cannot simultaneously work both on the corporate network and directly on the Internet, which creates unusual difficulties for them and reduced productivity (especially for developers). By the way, according to a survey conducted informally by our IS service in large American companies, the ban on split tunneling is a common practice that increases the security of corporate networks.

But back to the employees of the acquired companies. Their untrusted computers may become a point of entry into the corporate network, but we cannot allow this. But at the same time, they should provide the opportunity for new employees to work with all our internal systems until the completion of full integration. We could implement the scheme with Site-to-Site VPN, but it does not solve the original problem, since we do not allow split tunneling, the connected office remains untrusted and access through the ITU will be very limited. Connecting to Cisco corporate resources makes it impossible to access local resources or external services (AWS, GitHub, etc.). Access to them accordingly cuts off access to Cisco resources. Dilemma :-( Even in the case of implementing web authentication, both technical (for example, with IPv6) and organizational difficulties remained - lack of user experience and the inability to verify devices before providing access (which Cisco ISE does on the corporate network). In addition to Moreover, untrusted sites cannot be monitored, since they lack the necessary tools accepted as a standard in Cisco.
It was then that the idea of C-Bridge, a network solution using Cisco routers, switches and security tools, was born to provide fast, secure connections and monitor the security of new, untrusted, outdated, or non-Cisco sites. A little distracted, it is worth noting that exactly the same idea is used by us in SOC construction projects, in which it is necessary to monitor the safety of industrial segments and even sites isolated from the outside world.

C-Bridge is a fully autonomous and mobile solution that uses identity management and verification of user devices to provide access to Cisco corporate resources and other networks (for example, clouds) without compromising the security of our enterprise. From the side, the C-Bridge looks like an ordinary rack, stuffed with appropriate equipment. Now its height is 20RU, but it is filled only at 16RU (4RU remains a reserve for future use). Of these 16RUs, a quarter is devoted to IT tasks, and the remaining three quarters are for security and monitoring purposes.
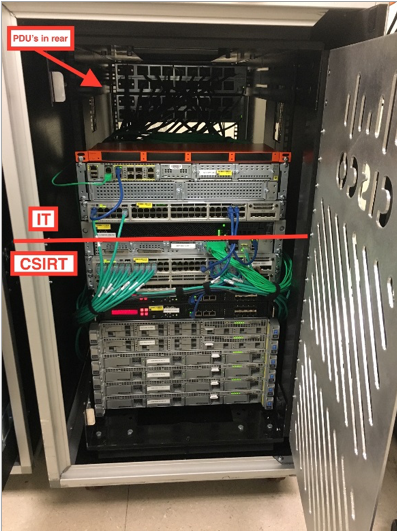
The Cisco CSIRT IS Monitoring and Incident Response service monitors all access to / via the Internet using C-Bridge, including access to our internal resources. The hardware of this rack is as follows:
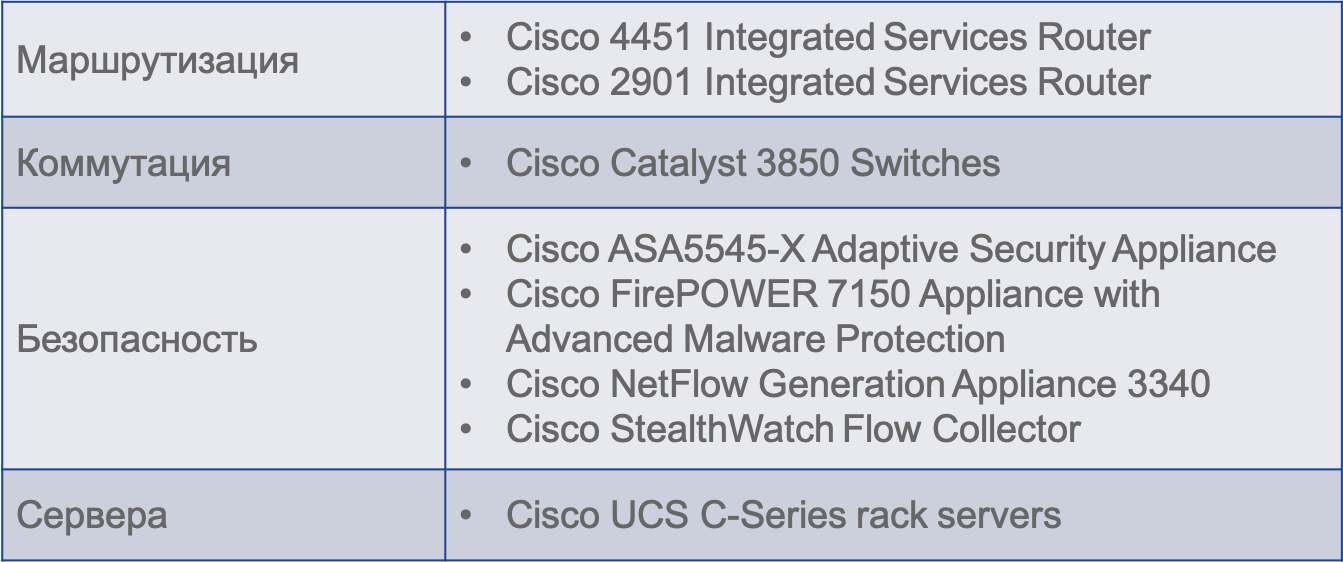
In addition to firewalling and VPN functionality, the following information security solutions are also used:
All traffic from untrusted sites now passes through the C-Bridge, which is the main control point. Remote users using AnyConnect also connect to the Cisco ASA in C-Bridge and can then connect either to our corporate resources or to the Internet. Access to the Cisco network is through the DMVPN tunnel, and traffic to cloud services or Internet resources goes directly, without the need to go through the Cisco network. At the same time, the presence in the C-Bridge of Cisco NGIPS next-generation attack detection system, Cisco Web Security Internet access control system, Cisco AMP anti-malware protection system, Cisco Umbrella DNS monitoring system and Cisco Stealthwatch anomaly detection system help protect an untrusted network from being hit it contains malicious code and other violations of information security.
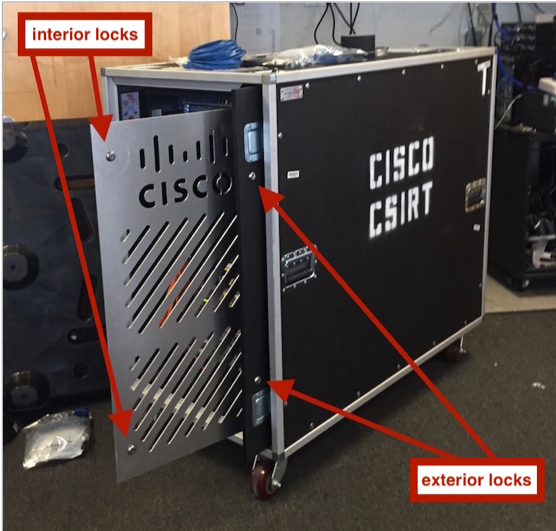
Since C-Bridge is used in an untrusted environment, in addition to the built-in security and access control mechanisms in the security tools themselves, we physically protect the mobile rack located on the side of the acquired company. Two sets of locks are used (inside + outside) on the inside and outside “doors” of the C-Bridge. At the same time, closed doors do not interfere with working with wires to connect them to the network and power supply. After implementation, the outer door may be left open for ventilation.
But this solution does not stand still. Now that we have a secure connection of untrusted sites to the Cisco network, the new features that C-Bridge is equipped with become available. For example, 802.1x support for connecting Telepresence or downloading OS images and software for Cisco corporate laptops. It also becomes possible to integrate between C-Bridge and the Safety & Security Team (physical security) solutions for the early implementation of video surveillance and access control systems in the premises of the acquired company.
Many years of experience with the C-Bridge was very successful, but there were a number of difficulties associated with the size of the 20-tyunite rack. The main one was related to the fact that on small sites:
We have introduced the concept of a lightweight C-Bridge Lite gateway to consolidate IT and information security functions in a small package with minimal requirements for installation area, environmental impact and cost. Reducing the rack led to a decrease in the bandwidth and performance of the C-Bridge, but for small sites this was not critical. As a result, the concept of multilevel security gateways was developed, which are used in offices of various sizes:

The advantages of the C-Bridge solution include:
At the end of the integration process, the C-Bridge gateway is removed from the acquired company, which merges with the Cisco network and no longer requires additional protective mechanisms and tools for its monitoring - it becomes an integral part of our infrastructure.
During the integration process, all employees of the acquired companies are required to use the Cisco AnyConnect VPN client to access all internal resources, since their networks are initially considered untrusted and do not comply with our information security requirements. At the same time, Cisco’s security policy prohibits split tunneling, which means that new employees cannot simultaneously work both on the corporate network and directly on the Internet, which creates unusual difficulties for them and reduced productivity (especially for developers). By the way, according to a survey conducted informally by our IS service in large American companies, the ban on split tunneling is a common practice that increases the security of corporate networks.

But back to the employees of the acquired companies. Their untrusted computers may become a point of entry into the corporate network, but we cannot allow this. But at the same time, they should provide the opportunity for new employees to work with all our internal systems until the completion of full integration. We could implement the scheme with Site-to-Site VPN, but it does not solve the original problem, since we do not allow split tunneling, the connected office remains untrusted and access through the ITU will be very limited. Connecting to Cisco corporate resources makes it impossible to access local resources or external services (AWS, GitHub, etc.). Access to them accordingly cuts off access to Cisco resources. Dilemma :-( Even in the case of implementing web authentication, both technical (for example, with IPv6) and organizational difficulties remained - lack of user experience and the inability to verify devices before providing access (which Cisco ISE does on the corporate network). In addition to Moreover, untrusted sites cannot be monitored, since they lack the necessary tools accepted as a standard in Cisco.
It was then that the idea of C-Bridge, a network solution using Cisco routers, switches and security tools, was born to provide fast, secure connections and monitor the security of new, untrusted, outdated, or non-Cisco sites. A little distracted, it is worth noting that exactly the same idea is used by us in SOC construction projects, in which it is necessary to monitor the safety of industrial segments and even sites isolated from the outside world.

C-Bridge is a fully autonomous and mobile solution that uses identity management and verification of user devices to provide access to Cisco corporate resources and other networks (for example, clouds) without compromising the security of our enterprise. From the side, the C-Bridge looks like an ordinary rack, stuffed with appropriate equipment. Now its height is 20RU, but it is filled only at 16RU (4RU remains a reserve for future use). Of these 16RUs, a quarter is devoted to IT tasks, and the remaining three quarters are for security and monitoring purposes.

The Cisco CSIRT IS Monitoring and Incident Response service monitors all access to / via the Internet using C-Bridge, including access to our internal resources. The hardware of this rack is as follows:

In addition to firewalling and VPN functionality, the following information security solutions are also used:
- Cisco NGIPS with AMP for Networks
- vWSA with AMP for Content integrating with ThreatGrid
- Unsampled Netflow Generation and Transfer to Cisco Stealthwatch vFlowCollector
- CSIRT PDNS and Cisco Umbrella
- Qualys Vulnerability Scanner (virtual)
- BGP Black Hole / Quarantine
- DLP functionality
- Syslog Collection.
All traffic from untrusted sites now passes through the C-Bridge, which is the main control point. Remote users using AnyConnect also connect to the Cisco ASA in C-Bridge and can then connect either to our corporate resources or to the Internet. Access to the Cisco network is through the DMVPN tunnel, and traffic to cloud services or Internet resources goes directly, without the need to go through the Cisco network. At the same time, the presence in the C-Bridge of Cisco NGIPS next-generation attack detection system, Cisco Web Security Internet access control system, Cisco AMP anti-malware protection system, Cisco Umbrella DNS monitoring system and Cisco Stealthwatch anomaly detection system help protect an untrusted network from being hit it contains malicious code and other violations of information security.
Since C-Bridge is used in an untrusted environment, in addition to the built-in security and access control mechanisms in the security tools themselves, we physically protect the mobile rack located on the side of the acquired company. Two sets of locks are used (inside + outside) on the inside and outside “doors” of the C-Bridge. At the same time, closed doors do not interfere with working with wires to connect them to the network and power supply. After implementation, the outer door may be left open for ventilation.

But this solution does not stand still. Now that we have a secure connection of untrusted sites to the Cisco network, the new features that C-Bridge is equipped with become available. For example, 802.1x support for connecting Telepresence or downloading OS images and software for Cisco corporate laptops. It also becomes possible to integrate between C-Bridge and the Safety & Security Team (physical security) solutions for the early implementation of video surveillance and access control systems in the premises of the acquired company.
Many years of experience with the C-Bridge was very successful, but there were a number of difficulties associated with the size of the 20-tyunite rack. The main one was related to the fact that on small sites:
- there was no separate room for the C-Bridge
- the rack could overheat without good air conditioning and ventilation
- being placed in workspaces, the rack was very noisy.
We have introduced the concept of a lightweight C-Bridge Lite gateway to consolidate IT and information security functions in a small package with minimal requirements for installation area, environmental impact and cost. Reducing the rack led to a decrease in the bandwidth and performance of the C-Bridge, but for small sites this was not critical. As a result, the concept of multilevel security gateways was developed, which are used in offices of various sizes:
- Small : 2RU = ISR4451 with Etherswitch, FTD for ISR (UCS-E) and UCS-E for CSIRT VMs, up to 300Mbps
- Medium : 3RU = ISR4451 with switching module and 2x UCS-E for CSIRT VMs + ASA5555X-FTD, up to 600Mbps
- Large : standard solution on ½ rack C-Bridge, 1Gbps +.

The advantages of the C-Bridge solution include:
- Speed . Providing concurrent access to corporate resources and untrusted networks 10 months faster.
- Scalability . The solution can be implemented at one or more sites.
- Reuse . One rack can be reused in new projects.
- Network security . The ability to monitor the Internet and internal traffic in an untrusted network to detect potential threats.
- Productivity of employees . Eliminates the need to use AnyConnect to access local resources.
At the end of the integration process, the C-Bridge gateway is removed from the acquired company, which merges with the Cisco network and no longer requires additional protective mechanisms and tools for its monitoring - it becomes an integral part of our infrastructure.
All Articles