How we built Wi-Fi on Huawei
In the previous three articles ( one , two , three ), we talked about how we upgraded the wired network in the Jet Infosystems office. Now it's time to talk about upgrading the wireless network.
Disadvantages of the old network
The wireless network in our office was built on the equipment of another vendor. And the operation of this network caused serious discontent among both users and system administrators.
What did users not like?
It was not easy to connect to the network. We implemented the concept of BYOD (bring your own device), when the user could independently connect the device to the network. For example, if the device connected to the network is an employee’s corporate laptop, then he needs to provide access to both the company's resources and the Internet. And if the user brought his device - a smartphone, a tablet - then you need to give him access only to the Internet. Despite this possibility, support for the wireless network required a lot of administrative effort, as there were many situations that had to be dealt with individually. Plus a lot of nuances with fragmented platforms when there are no standardized jobs. As a result, the resource costs of settling all aspects turned out to be completely impractical. It was more logical to rebuild everything.
What complaints did administrators have about the Wi-Fi network?
A huge number of applications came from users with various connectivity problems, inability to configure equipment, etc. In addition, the old network was created around 2012-2013, and since then the standards have changed and speeds have become higher.
We calculated and realized that it would be more expensive to upgrade an existing network than to completely replace it with a new one, using the architecture and equipment of Huawei. They decided on that.
As a technical basis for the solution, Huawei AP6050DN and AP6052DN access points were chosen. These are modern devices that support IEEE 802.11b / g / n / ac standards and operate in the 2.4 GHz and 5 GHz bands. We also decided to use the Huawei AC6605 wireless network controller (more precisely, two controllers combined in a cluster) and the Huawei Agile Controller Campus (HACC) hardware and software system for user authorization and access control.
What is the difference between the 2.4 GHz and 5 GHz bands
The 5 GHz band is better suited for servicing a large number of devices in the area of one point, subscribers do not interfere with each other. In the 2.4 GHz range, longer range, waves penetrate better through walls and floors, less interference due to reflections from furniture and structural elements.
Radio Survey

Since we had complaints about the existing Wi-Fi network not only with the connection method, but also with the quality of the radio coverage, we started with a radio survey. Traditionally, this is done bypassing all rooms with a laptop studded with measurement adapters and configured AirMagnet software. In each room, you need to make several measurements, fixing the position of the laptop.
Alexander Gulyaev tells asha77 : there are a lot of long corridors in our office, it is long and tiresome to drag measuring equipment on your own. Having looked like this for a day or two, we were tired and decided to put together something more technological. Googled. On Avito, a half-dead scooter was bought for 2500 rubles. From the remnants of the profiles from the video wall, a semblance of a base was twisted into which pieces of a mercilessly sawed gyro scooter with all its insides plus the Raspberry Pi were integrated. Colleagues adjusted the programmer, and creative Germans (or are they Dutch?) From the github - software, which is poured into the gyroscope controller and allows you to manage commands through RS232 from Raspberry PI. The application on Node.js for controlling the controller from a smartphone was uploaded to PI itself. It turned out a robot (called Robik), which carries a laptop for the operator. Thanks to Robik, a detailed radio survey of the office took almost half the time than in the usual version. This is despite the fact that practically nothing was completed for lack of time.
It was not without Robik's help that it turned out that the signal level was quite good. This means that the access points were placed in the right places with normal density. But some of them in the 2.4 GHz band interfered with each other. Therefore, we decided to disconnect 2.4 GHz and use only 5 GHz after upgrading in places with a high density of points on some of the points.
In addition, in places of high density, we installed AP6052DN series access points, not AP6050DN. They are positioned by the vendor specifically for places with a large number of subscribers. The AP6052DN has two transmitters, one of which operates in two bands and automatically switches to optimal, and the second transmitter operates only at 5 GHz.
Security
Wireless access always implies an authorization mechanism, because radio is an open environment and anyone can listen to it. Therefore, security issues - encryption, authorization - should be given maximum attention. With this, you need to start designing a wireless network.
We have three types of access: production access, guest access, and the connection of employees' own devices.
Production Access
Production access is used on corporate laptops. Employees can access the same corporate resources as when connecting via wire. The industry for this option has long developed a standard WPA2 authorization scheme.
Authorization is made according to personal user certificates. In the old network, the vendor authorization solution was a separate certification authority and independently generated user certificates. It worked on the principle of “once set up and everything works”, but if something went wrong, our technical support could not extract the generated certificate and put it on the user's device manually.
Therefore, we decided that we would no longer have a proprietary solution, and we would integrate with the existing Microsoft corporate certification authority. There are three ways to install a user certificate on a user's computer: through AD group policies, bring a laptop to the IT department, whose employee will issue a certificate, or use auto-provisioning.
Let's talk about the third method. How it works? A user is trying to connect to our wireless production network. If he does this for the first time, he will automatically be redirected to our internal portal Huawei, which is implemented using the Agile Controller Campus product, and offered to run a small utility.
This utility initiates the call of Huawei Agile Controller Campus to the corporate certification authority, generating an individual user certificate, and installing it in the certificate store on the local computer.
In general, in companies where all workplaces are more or less standard, it is more convenient to distribute certificates to workstations using Microsoft group policies using Active Directory. But with us this is not possible for the entire organization, because many computers run on Linux. Therefore, those developers who have installed various domestic versions of Linux are most affected. A variety of modern IT solutions for such OS, unfortunately, appear last.
In connection with all of the above, there should always be the ability to manually configure the workstation.
Guest Access

Any employee of our company can invite a guest. If he needs Internet access, then when connected to a corporate Wi-Fi network, the system automatically redirects it to the authorization portal (Captive Portal). In this case, the guest receives the username and password from the employee who invited him.
But where does the employee get this login with a password? Previously, IT specialists once every two or two months generated sets of logins and passwords, which could be obtained at the reception desk. Any employee could go to the secretaries and ask for data to enter the network. Then the secretaries sent a letter to the information and technical support service with information to which employees and for which visitors the information was provided.
As you can imagine, the circuit was too inconvenient and outdated. Therefore, in the new network, we took a completely different approach. Now we have a section on the internal portal where it is enough to enter the company name and the guest’s mobile phone. An SMS with login data is sent to his phone, and an employee receives a confirmation of a successful operation by e-mail. As a backup option for the transition period, we left the usual scheme with secretaries.
The Huawei Agile Controller Campus (HACC) product has several web interfaces for use for various purposes: a guest authorization portal, admin interface, self-service portal and a SOAP module. The SOAP module has various APIs that can be used to control HACC from third-party software. Therefore, we wrote an interface for the interaction of our corporate portal with the Huawei solution.
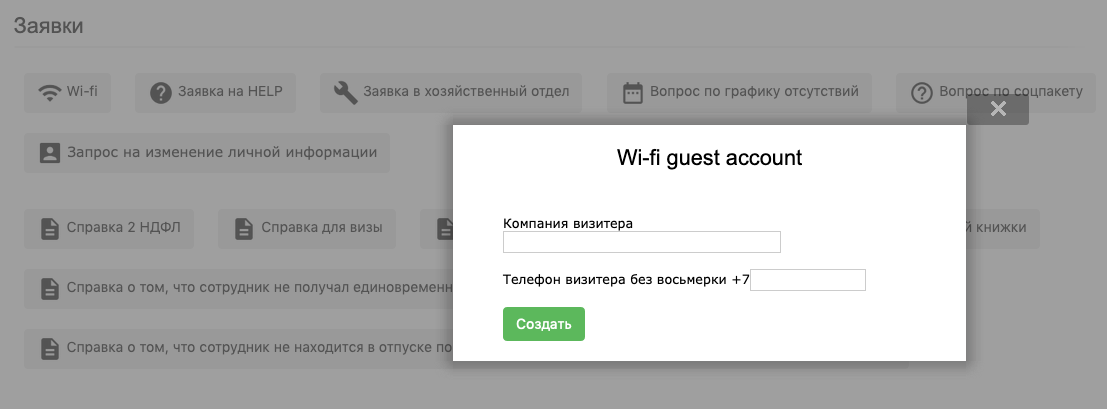
For guest Wi-Fi, we provide access to the Internet and to company resources open to an external network. We do not allow torrents and network traffic that are considered botnets; Access to adult resources and to hosts designed to circumvent restrictions is prohibited. Thanks to this policy, we haven’t had any outbursts of crazy traffic from guest Wi-Fi, and we do not limit the bandwidth.
Own mobile devices
In our new network, the EAP-TTLS protocol is used to authorize our own devices, rather than EAP-TLS, that is, certificates are not used on the user side, because it is extremely difficult to automatically install a certificate on an arbitrary device. I would venture to suggest that no vendor can solve it.
At the same time, EAP-TTLS connection has its own drawback: an attacker can set up his access point and try to somehow catch the logins and password hashes of our users on the air. Therefore, with logins and passwords that are used to access corporate resources, you cannot connect to the guest network.
We have introduced separate usernames and passwords for connecting personal mobile devices. They are generated according to the same principle as guest ones: any user can register their mobile device on a special self-service portal. Now it is implemented through one of the web forms of Huawei Agile Controller Campus. Registration is valid for a certain period, which ends along with the date of the mandatory password change in accordance with IS corporate policies.
If one of the employees wants to bring his own laptop, tablet or smartphone and get access not only to the Internet, but also to corporate resources, then he will have to coordinate this with the security service management, then go to the IT department, where he generate and install a separate certificate, similar to the corporate laptop connection scheme.
Freelancers

In addition to full-time employees, we also have freelance employees who also need to go online to work, including via Wi-Fi. For them, we use the same profile as for connecting the mobile devices of full-time employees. This eliminates the need to create personal accounts for freelancers, you do not need to enter them into the corporate Active Directory system, you do not need to deal with complex coordination with the security service - in general, there is much less headache. But at the same time, we can provide them with Internet access controlled by us.
Or, say, some employee bought a personal laptop. He wants to connect it right away, put the latest updates and so on. In this case, he does not need to go to the department of information and technical support and coordinate the connection of his laptop to the network. He independently connects it to a wireless network and immediately starts working. And although access to internal corporate resources is blocked for him, please go to the Internet for updates.
Networking
Access points connect to the same access switches as user workstations. They are connected in separate VLANs, which are set up in separate VRFs. Access points connect with Huawei AC6605 WLAN controllers via CAPWAP protocol. The controllers are combined into a fail-safe cluster, one controller acts as the primary, the second as the backup. Huawei Agile Controller Campus acts as the authorization server for them.
As a result, Wi-Fi traffic goes between access points only through the controller. The performance drop is insignificant for us, but from the point of view of controllability and implementation of various information protection functions, such a scheme is much more convenient.
The controller transfers wireless traffic from mobile devices to the main network. Traffic from different SSIDs is transmitted using different VRFs. We got them in the amount of two pieces - one for guests and employees' own devices, the second for the working network.
Users receive IP addresses from the corporate DHCP server. Previously, for each SSID we had one large range for 512 devices, and now for guest access we have four IP ranges (for 256 devices each), and for working access and our own devices we have 8 ranges (also 256 devices each) . From whatever range the user may initially receive an IP address, for any movement around the office this IP address will be saved by the user.
At the same time, the network architecture we have chosen has its drawbacks - there are more control points to monitor. In particular, when a user connects, not only the only default gateway, but also other IP addresses are visible to him from our network infrastructure. For guest access, this is not very good from the point of view of information security, because the less information about our infrastructure is available to the guest, the better.
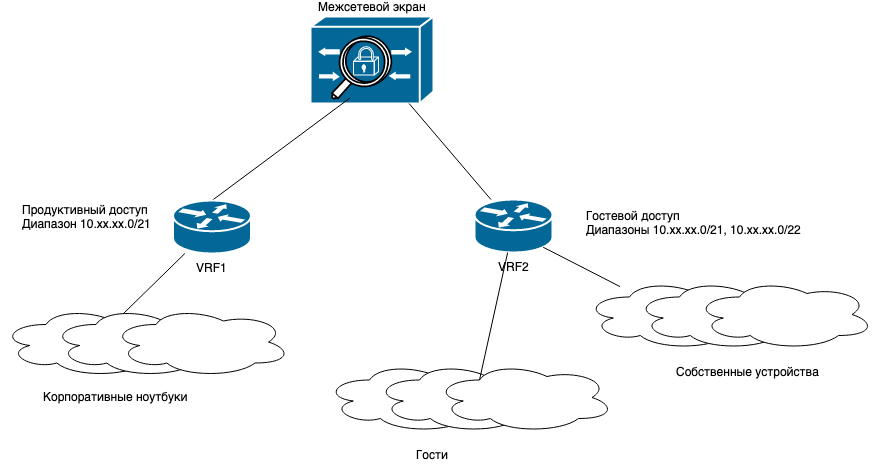
To solve these problems in guest networks, we adopted the following basic security measures:
- turned on the so-called private mode in order to exclude the transfer of traffic between connected wireless devices;
- blocked access to all network devices that are routers in the guest IP ranges with ordinary access lists.
Huawei Agile Controller Campus
Huawei Agile Controller Campus is a software and hardware complex. The software is written in Java using the Tomcat framework and runs on a server running Windows Server 2012 (it can also work under SUSE Linux). Either Microsoft SQL Server or Oracle can be used as a database.
When we initiated the project of restructuring the office network, Huawei provided HACC only in the physical version, so we had to purchase as many as three servers. One of them is called System Manager - it contains a database and all web interfaces. The other two servers equally reserve each other - these are System Controllers. It is with them that the WLAN controller interacts (via the RADIUS protocol) when connecting and authorizing users. That is, the WLAN controller each time asks any available System Controller whether such a user with such credentials can access Wi-Fi.
While we were implementing our project, Huawei offered the ability to virtualize servers. Of course, we immediately took advantage of this. Now, instead of three physical servers, we have two virtual machines. This immediately eliminated a lot of problems, in particular, with fault tolerance, System Manager backup and database backup (because the virtual machine is copied using a snapshot and is backed up by the virtualization farm).
SMS Newsletter

And finally, a few words about the SMS distribution mechanism with logins and passwords for guest access. Complete with physical HACC servers was a GSM modem that connects via a serial port. Unfortunately, you can’t connect the COM port to the virtual machine, but we found a solution. It turned out that our engineers involved in access control in the office buy special gateways that allow traffic from the serial port to be wrapped in Ethernet.
We used the EverFocus EA-LAN1 model. Usually they are used to connect readers of electronic passes, but for the Chinese GSM-modem, this gateway fit perfectly. A virtual serial port driver is attached to the gateway, with which the HACC works no worse than with the physical one. So we seamlessly implemented sending SMS from virtual machines.
Maxim Klochkov
Senior Consultant, Network Audit and Integrated Projects
Network Solution Center
Jet Infosystems
Alexander Gulyaev,
chief systems architect
Network Solution Center
Jet Infosystems
All Articles