GeekBrains Vulnerabilities: Why pay money for courses if you can just download them?

A small tale about a small error, with the help of which access to all paid courses and homework on resources was obtained. And also a little about other vulnerabilities found.
Background
In the evenings, in between reading school literature for the summer, I participated in a bug bounty program from Mail.ru Group.
I was looking for new subdomains and services owned by Mail.ru, they often encounter all sorts of vulnerabilities.
At that time I already knew about the educational IT project GeekBrains , I did not think that I could get something interesting out there, but I was wrong.
API
Having delved into testing the user's personal account, I immediately came across an API service .
Using DIRB, I went to the projects method, sorting through the id of the projects, I fell into a curious URL.

This is an open Amazon S3 bucket. On it in "free access" are materials and educational literature for almost all courses of the resource.

For example, a presentation on the course "Information Security"
Or, here’s a Java developer class homework
There is also a large amount of private information for each participant in the course.
Move on
Logically, if they have one S3 bucket, then maybe there are others!
At this point, I took advantage of lazys3 . A pretty handy tool for finding S3 buckets.
After busting, I found another bucket, it was geekbrains-uploads.s3.amazonaws.com
Unfortunately, direct viewing of files is not available, but it is possible to upload your own.
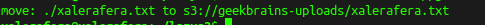
Using the standard AWS utility, upload the TXT file to the server.
aws s3 mv xalerafera.txt s3: // geekbrains-uploads
Here you can upload an executable file or other muck.
At this point, I reported vulnerabilities, and a few days later I received payments for them.
In addition to these two holes, I also discovered XSS in private messages .
There is another vulnerability that I would like to talk about, but it is still Triaged.
Summary
Close your S3 buckets, this can lead to serious losses.
I want to thank AlexShmel for helping me write this article.
All Articles