Vulnerabilities of ERP-systems of KII objects
With the tendency to digitalize enterprises around the world, enterprise resource management systems - ERP systems - are gaining popularity. The largest player in this segment in the global and Russian markets has long been the German company SAP.
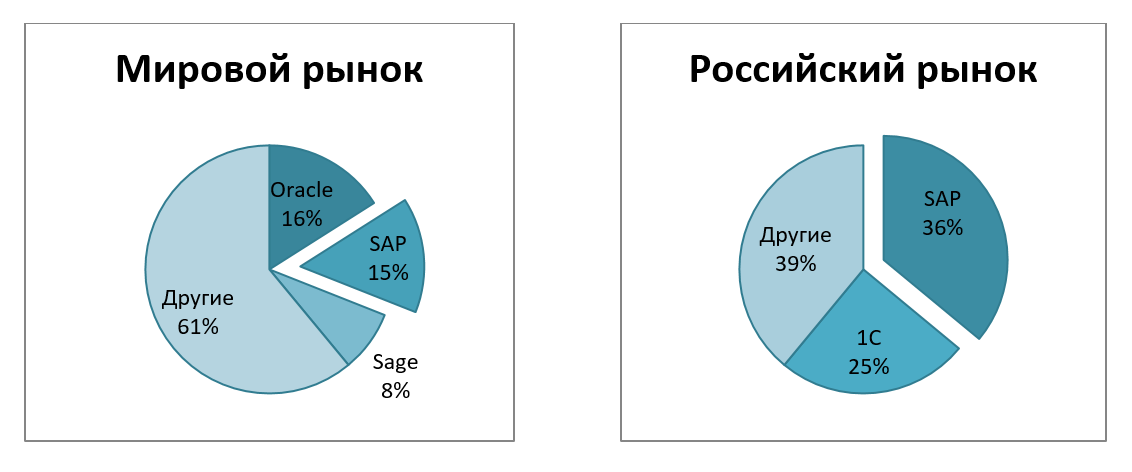
It is worth noting that Gartner defines this type of system as “business critical”, which is not surprising in view of the extensive functionality that they provide: finance, manufacturing, supply chain management, CRM, product life cycles, BI, etc. So, for example, the share of industries applying these solutions for the largest number of implementation projects that the TAdviser portal leads is as follows:
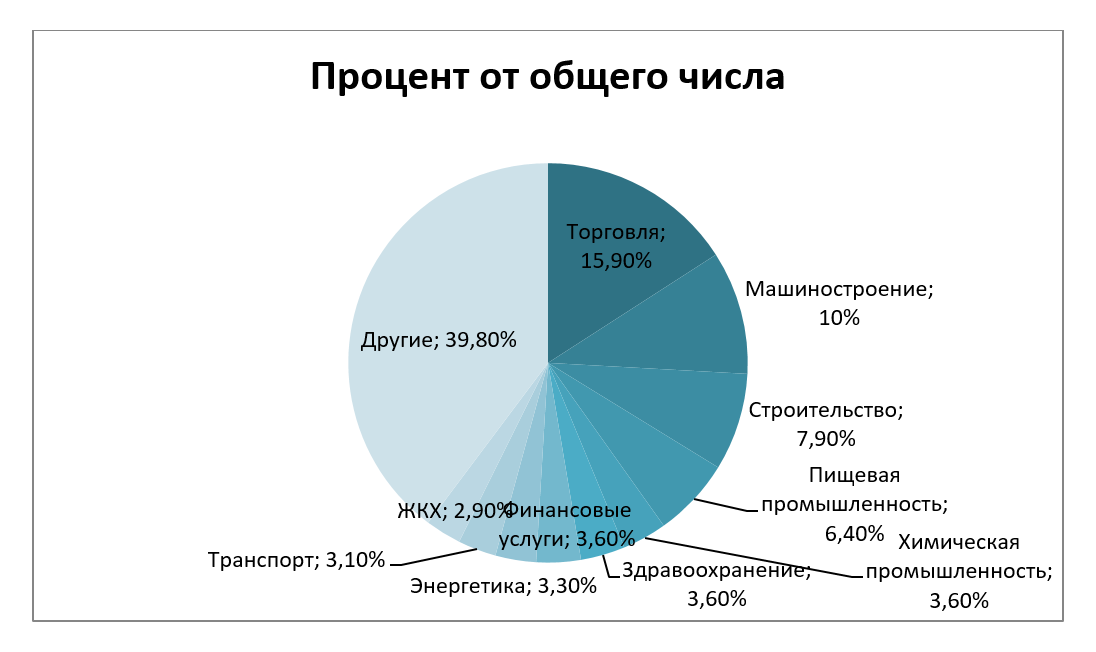
However, despite the relevance of these business critical decisions, industries still suffer from a lack of information about attack vectors for such systems used by cybercriminals in industrial espionage, hacker attacks for profit or politically motivated purposes.
The spread of information technology also leads to an increase in the number of detected software vulnerabilities (software), and therefore the total number of vulnerable components of systems increases. Since the implementation of business processes often involves the interaction of remote systems from each other via the Internet, this represents the greatest danger, because in this case, enterprise ERP systems have access to an open network.

Thanks to specialized Internet search resources such as Shodan and Censys, as well as the use of certain Google queries (called Google Dorks), which are published daily, for example, on the Exploit-DB online service, more than 17,000 applications can be found accessible via the Internet ERP systems and at least 500 SAP configuration files that remain freely available in insecure file storages.
For example, in 2016, the US Department of Homeland Security CERT issued a directive stating that at least 36 global organizations were hacked by exploiting a vulnerability in SAP systems that had been known for more than five years. An even more “hot” example: in April 2019, the 10KBLAZE exploit was presented at a conference in Dubai, which endangered thousands of companies, although security instructions that “close” this gap in the systems were published before 2013.
The number of publicly available exploits or detailed instructions for exploiting a particular vulnerability is growing steadily (data from the Exploit-DB online service). Many of them use published security guidelines, and some are completely automated for use in utilities like Metasploit, which allows automated penetration testing.

It is worth noting that often, large, backbone enterprises in a wide variety of areas become the target of attacks. In part, to resolve this problem, Federal Law No. 187 “On the Security of the Critical Information Infrastructure of the Russian Federation” (KII) was adopted, and a year and a half has passed since its entry into force. First of all, the adoption of this law is aimed at tightening control over compliance with the safety requirements of KII facilities and increasing fault tolerance when conducting computer attacks against them. In addition to this, informing about computer incidents from the subject of KII will require integration with the state system for the detection, prevention and elimination of the consequences of computer attacks (SOSOPKA).
Also, subsequently, in addition to this Federal Law, normative legal acts were adopted that presented both organizational and technical requirements for significant (falling into the first, second or third category of significance assigned to the established procedure for categorization in accordance with the criteria of significance and indicators of their values ) objects of critical information infrastructure.
For example, in the process of modeling information security threats, it is necessary to analyze the possible vulnerabilities of a significant object and its software and firmware, as well as determine possible ways to implement these threats.
Taking into account the fact that SAP is a leader not only in the Russian, but also in the global market, it can be concluded that for some companies from the areas listed in Fig. 1, the implementation of the requirements of the law “On the security of critical information infrastructure” will be directly ensuring the security status of their ERP (including SAP) solutions.

Fig. 1: Spheres that combine the objects of KII (in accordance with Federal Law No. 187)
The complexity of large landscapes of SAP ERP systems, whose management servers can be physically located at a sufficient distance from each other, the management of enterprises with tens of thousands of employees - all this complicates the process of monitoring and analyzing the security of SAP systems.
However, the “openness” of an information system on the Internet is not always regarded as a negative factor. For example, many KII objects have a closed, isolated network, which only complicates the security analysis process, since in this case the system does not have direct access to the Internet, which means that the built-in means for checking for updates cannot always fulfill its function, as a result of which security breaches remain open to some types of attacks.
Based on the foregoing, several areas of work are seen in the implementation of the requirements of the Federal Law "On the security of KII":
The need for the design, implementation and application of domestic SAP security tools in this context is especially acute. Ubiquitous import substitution requires not only the further development of domestic products by vendors, but also a more integrated approach to the implementation of ERP-systems by enterprises, taking into account the most relevant information security requirements.
Boris Pasynkov , design engineer, Gazinformservice

It is worth noting that Gartner defines this type of system as “business critical”, which is not surprising in view of the extensive functionality that they provide: finance, manufacturing, supply chain management, CRM, product life cycles, BI, etc. So, for example, the share of industries applying these solutions for the largest number of implementation projects that the TAdviser portal leads is as follows:

However, despite the relevance of these business critical decisions, industries still suffer from a lack of information about attack vectors for such systems used by cybercriminals in industrial espionage, hacker attacks for profit or politically motivated purposes.
The spread of information technology also leads to an increase in the number of detected software vulnerabilities (software), and therefore the total number of vulnerable components of systems increases. Since the implementation of business processes often involves the interaction of remote systems from each other via the Internet, this represents the greatest danger, because in this case, enterprise ERP systems have access to an open network.

Thanks to specialized Internet search resources such as Shodan and Censys, as well as the use of certain Google queries (called Google Dorks), which are published daily, for example, on the Exploit-DB online service, more than 17,000 applications can be found accessible via the Internet ERP systems and at least 500 SAP configuration files that remain freely available in insecure file storages.
For example, in 2016, the US Department of Homeland Security CERT issued a directive stating that at least 36 global organizations were hacked by exploiting a vulnerability in SAP systems that had been known for more than five years. An even more “hot” example: in April 2019, the 10KBLAZE exploit was presented at a conference in Dubai, which endangered thousands of companies, although security instructions that “close” this gap in the systems were published before 2013.
The number of publicly available exploits or detailed instructions for exploiting a particular vulnerability is growing steadily (data from the Exploit-DB online service). Many of them use published security guidelines, and some are completely automated for use in utilities like Metasploit, which allows automated penetration testing.

It is worth noting that often, large, backbone enterprises in a wide variety of areas become the target of attacks. In part, to resolve this problem, Federal Law No. 187 “On the Security of the Critical Information Infrastructure of the Russian Federation” (KII) was adopted, and a year and a half has passed since its entry into force. First of all, the adoption of this law is aimed at tightening control over compliance with the safety requirements of KII facilities and increasing fault tolerance when conducting computer attacks against them. In addition to this, informing about computer incidents from the subject of KII will require integration with the state system for the detection, prevention and elimination of the consequences of computer attacks (SOSOPKA).
Also, subsequently, in addition to this Federal Law, normative legal acts were adopted that presented both organizational and technical requirements for significant (falling into the first, second or third category of significance assigned to the established procedure for categorization in accordance with the criteria of significance and indicators of their values ) objects of critical information infrastructure.
For example, in the process of modeling information security threats, it is necessary to analyze the possible vulnerabilities of a significant object and its software and firmware, as well as determine possible ways to implement these threats.
Taking into account the fact that SAP is a leader not only in the Russian, but also in the global market, it can be concluded that for some companies from the areas listed in Fig. 1, the implementation of the requirements of the law “On the security of critical information infrastructure” will be directly ensuring the security status of their ERP (including SAP) solutions.

Fig. 1: Spheres that combine the objects of KII (in accordance with Federal Law No. 187)
The complexity of large landscapes of SAP ERP systems, whose management servers can be physically located at a sufficient distance from each other, the management of enterprises with tens of thousands of employees - all this complicates the process of monitoring and analyzing the security of SAP systems.
However, the “openness” of an information system on the Internet is not always regarded as a negative factor. For example, many KII objects have a closed, isolated network, which only complicates the security analysis process, since in this case the system does not have direct access to the Internet, which means that the built-in means for checking for updates cannot always fulfill its function, as a result of which security breaches remain open to some types of attacks.
Based on the foregoing, several areas of work are seen in the implementation of the requirements of the Federal Law "On the security of KII":
- Improvement and development of measures for timely software updates;
- The use of additional protective equipment imposed;
- Analysis of the source code of programs and implementation of secure software development processes.
The need for the design, implementation and application of domestic SAP security tools in this context is especially acute. Ubiquitous import substitution requires not only the further development of domestic products by vendors, but also a more integrated approach to the implementation of ERP-systems by enterprises, taking into account the most relevant information security requirements.
Boris Pasynkov , design engineer, Gazinformservice
All Articles