Security Week 37: vulnerability in Android, Microsoft versus deepfakes, popularity of Windows 7
 Vulnerabilities in iOS we discussed last week, the turn of vulnerabilities in Android has come. On September 4, information about the problem in Android was published by researchers from the Zero Day Initiative ( news, bulletin ), and at the time of publication, it was not closed. In the patch set for Android released the day before, two critical errors were fixed in the Media Framework, but this problem in the Video4Linux 2 driver is still relevant.
Vulnerabilities in iOS we discussed last week, the turn of vulnerabilities in Android has come. On September 4, information about the problem in Android was published by researchers from the Zero Day Initiative ( news, bulletin ), and at the time of publication, it was not closed. In the patch set for Android released the day before, two critical errors were fixed in the Media Framework, but this problem in the Video4Linux 2 driver is still relevant.
Therefore, few details are disclosed. ZDI estimates vulnerability at 7.8 according to CVSS. The essence of the problem is that the driver does not check the existence of the object before conducting operations on it. A bug for operation requires local access to the system. In other words, an application with malicious code and low privileges can get full access to the smartphone, but this application needs to be installed somehow.
Representatives of Google have not yet commented on the vulnerability report. According to ZDI, the Android developer received information about the problem back in March this year, in June said that he was working on a patch, but did not respond to subsequent requests for the release date of the patch. The vendor’s assessment is still important: for example, Apple last week responded to Google’s research on vulnerabilities in iOS with a statement confirming the existence of a malicious campaign, but refuting claims about the duration of the attack. According to Apple, the campaign lasted two months, not two years.
Microsoft and Facebook, with the participation of several American universities, are embarking on a warpath against deepfakes. The companies organized a contest ( news , project site ) of the Deepfake Detection Challenge, whose task will be to find effective methods of dealing with fake content using machine learning methods. At the end of this year, the project will post a data set (original and modified videos), on the basis of which participants will be able to train fake detection tools. In the spring of 2020, black box testing will be held, which will determine the most effective developments.

Not a single Nicolas Cage was hurt when creating the gif. Source
Deepfake is a relatively recent topic, which began a broad discussion in 2017. Then in social networks videos began to appear in which the person’s face was replaced by another, sometimes with incredible credibility. The term itself appeared thanks to one of Reddit users with the nickname deepfakes, alluding to the type of end product (fake) and the method of its manufacture (deep learning technology). Since then, several projects have been released with source code for making fakes at home. The technology received widespread use, and with a variety of final results - from relatively innocent (that if you stick Mel Gibson's face in the movie Mad Max: Fury Road, in which he did not appear) to dubious and really dangerous (pornography and fakes of politicians' speeches).
Before the deepfake phenomenon, it could be assumed that any text on the Internet could be fake, while the video deserves a little more trust. Now this is not so, and it is not just about videos. On August 30, the Wall Street Journal reported the first documented case of smart fraud using a person’s voice. An unnamed energy company suffered: scammers managed to almost flawlessly reproduce the voice of its director, after which they called an organization employee and demanded 220 thousand euros to be transferred. The "task" was completed, the attackers got the money. This is not only an example of advanced telephone fraud, but also a scenario where technologies for creating fakes that are difficult to distinguish from reality get offline.
On the website of the Deepfake Detection Challenge project, the fight against fakes is compared to a game of chess: the development of intelligent systems of opponents needs to be answered with even more powerful fake recognition algorithms. This is an honorable task, but it seems that in the near future we will all have to apply even more stringent methods of filtering network content. In the new wondrous reality, one should not immediately trust not only e-mail messages allegedly from a large company, but also video messages from well-known people. And phone calls. Only face-to-face meeting is so far protected from digital interference. Hopefully this last bastion will last a long time.
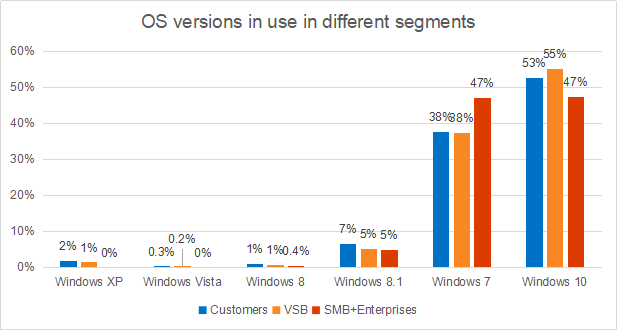
Traditional security issues, in particular the use of outdated software, do not go anywhere. Kaspersky Lab investigated which versions of Windows are used by medium and large companies, small businesses, and regular users. Consumer results are in line with recent data from other sources : Windows 10 only recently occupied a little more than half of the market. Most modern Windows is installed in 53% of end users, and the share among small companies is even slightly higher - 55%.
In second place is Windows 7, whose extended support ends January 14, 2020. The larger the company, the slower the migration to fresh OS versions; among medium and large businesses, the share of Windows 7 reaches 47%. In third place is the version of Windows 8.1 (7% of consumers, 5% of companies), whose support will continue until 2023. Unsupported and frankly unsafe Windows XP is installed in 2% of users, while larger companies are practically not used. Both consumers and companies may have different arguments against the upgrade, but from a security point of view, an upgrade will be necessary sooner or later. In the case of the still popular Windows 7, it will be needed very soon.
Disclaimer: The opinions expressed in this digest may not coincide with the official position of Kaspersky Lab. Dear editors generally recommend treating any opinions with healthy skepticism.
All Articles