Training Cisco 200-125 CCNA v3.0. Day 34. Advanced VLAN Concept
We have already examined VLANs in the video lessons Day 11, 12, and 13 and today we will continue to study them in accordance with ICND2. I recorded the previous video, which marked the end of preparation for the ICND1 exam, several months ago, and all this time until today has been very busy. I think many of you have successfully passed this exam, those who postponed testing can wait until the second part of the course is over and try to pass the CCNA 200-125 comprehensive exam.
Today’s video tutorial “Day 34”, we begin the topic of the ICND2 course. Many ask me why we did not consider OSPF and EIGRP. The fact is that these protocols are not included in the subject matter of the ICND1 course and are being studied in preparation for passing ICND2. Starting today, we will begin coverage of the second part of the course, and of course, we will study the OSPF and EIGRP punctures. Before starting today's topic, I want to talk about structuring our video tutorials. When presenting the topic of ICND1, I did not adhere to the accepted patterns, but simply logically explained the material, since I thought that this method was easier to understand. Now, while studying ICND2, at the request of students, I will begin to submit training material in accordance with the curriculum and curriculum of the Cisco course.
If you go to the company's website, you will see this plan and the fact that the entire course is divided into 5 main parts:
- Technologies for switching local networks (26% of the training material);
- Routing technologies (29%);
- Technologies of global networks (16%);
- Infrastructure services (14%);
- Maintenance of infrastructure (15%).
I will start with the first part. If you click on the drop-down menu on the right, you can see the detailed topics of this section. Today’s video tutorial will cover the topics of section 1.1: “Configuring, checking and troubleshooting VLANs (normal / extended range) covering several switches” and subsections 1.1a “Access ports (data and voice messages)” and 1.1.b “Default VLAN” .
Further, I will try to adhere to the same principle of presentation, that is, each video lesson will be devoted to one section with subsections, and if there is not enough material, I will combine the topics of several sections in one lesson, for example, 1.2 and 1.3. If there is a lot of section material, I will split it into two videos. In any case, we will follow the course program, and you can easily compare the compliance of your notes with the current Cisco curriculum.

You see my new desktop on the screen, it is Windows 10. If you want to improve your desktop with various widgets, you can watch my video called “Pimp Your Desktop”, where I tell you how to customize the desktop of your computer to suit your needs. I post videos of this kind on another channel, ExplainWorld, so you can use the link in the upper right corner and see its contents.
Before the start of the lesson, I’ll ask you not to forget to share my videos and like them. I also want to remind our contacts on social networks and links to my personal pages. You can write to me by e-mail, and as I have already said, the priority in receiving my personal response will be given to people who made a donation on our website.
If you don’t make a donation, it’s okay, you can leave your comments under the video tutorials on the YouTube channel, and I will respond to them whenever possible.
So, today, according to the Cisco schedule, we will consider 3 questions: compare the Default VLAN, or the default VLAN, with the Native VLAN, or the “native” VLAN, find out how the Normal VLAN (normal range of VLANs) differs from the extended range of Extended VLANs Consider the difference between a Data VLAN (Voice VLAN) and a Voice VLAN (Voice VLAN). As I said, we have already studied this issue in previous series, but rather superficially, so many students still have difficulty determining the difference between VLAN types. Today I will explain it so that everyone understands.
Consider the difference between Default VLAN and Native VLAN. If you take a brand new Cisco switch with factory settings, it will have 5 VLANs - VLAN1, VLAN1002, VLAN1003, VLAN1004 and VLAN1005.
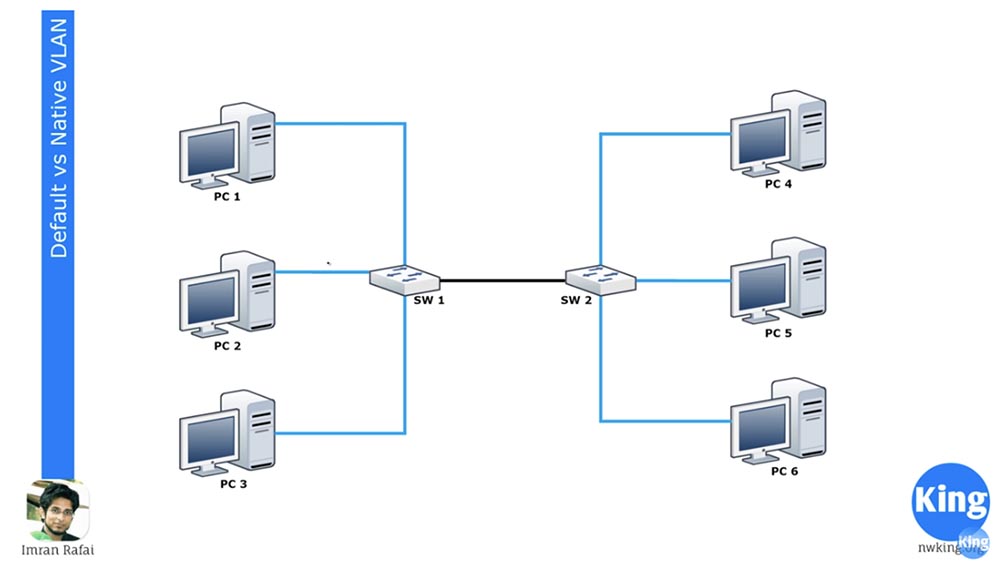
VLAN1 is the default VLAN for all Cisco devices, and VLAN 1002-1005 are reserved for Token Ring and FDDI. VLAN1 cannot be deleted or renamed, interfaces cannot be added to it, and all switch ports belong to this network by default until they are configured differently. By default, all switches can communicate with each other because they are all part of VLAN1. This is what “Default VLAN,” or Default VLAN, means.
If you go into the settings of switch SW1 and assign two interfaces to the VLAN20 network, they will become part of the VLAN20 network. Before starting this lesson today, I strongly advise you to review the 11.12 and 13 days series mentioned above, because I will not repeat what VLANs are and how they work.
I’ll just remind you that you cannot automatically assign interfaces to a VLAN20 network until you create it, so first you need to go into the global configuration mode of the switch and create VLAN20. You can look at the CLI settings console and understand what I mean. After you have assigned these 2 ports to work with VLAN20, PC1 and PC2 will be able to communicate with each other because they will both belong to the same VLAN20 network. But PC3 will still be part of VLAN1 and therefore will not be able to connect to computers on VLAN20.
We have a second switch SW2, one of the interfaces of which is assigned to work with VLAN20, and PC5 is connected to this port. With this connection scheme, PC5 cannot communicate with PC4 and PC6, but these two computers can communicate with each other because they belong to the same VLAN1 network.
Both switches are connected by trunk through appropriately configured ports. I won’t repeat myself, I’ll just say that all ports of the switch are configured by default for DTP trunking mode. If you connect a computer to some port, this port will use access mode. If you want to switch the port to which PC3 is connected to this mode, you must enter the switchport mode access command.
So, if you connect the two switches to each other, they form a trunk. The upper two ports of SW1 will only pass traffic on VLAN20, the lower port will only on VLAN1 traffic, but the trunk connection will pass through all the traffic passing through the switch. Thus, both VLAN1 and VLAN20 will receive traffic to SW2.
As you remember, VLANs have a local meaning. Therefore, SW2 knows that traffic arriving at port VLAN1 from PC4 can only be sent to PC6 through a port that also belongs to VLAN1. However, when one switch sends traffic to another switch on the trunk, it must use a mechanism to explain to the second switch what kind of traffic it is. As such a mechanism, the Native VLAN is used, which is connected to the trunk port and passes tagged traffic through itself.
 \
\
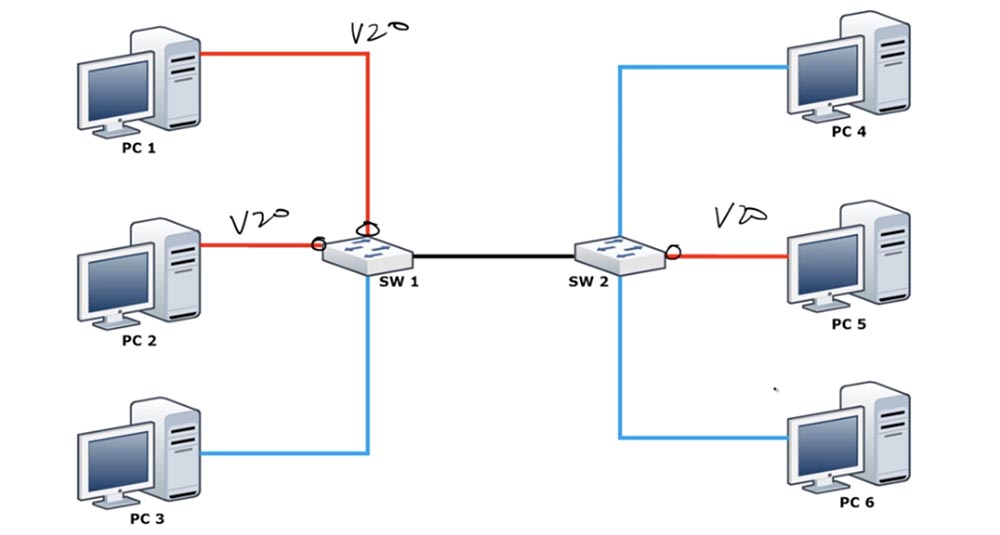
As I said, the switch has only one network that is not subject to change - this is the default network VLAN1. But by default, Native VLAN is VLAN1. What is a Native VLAN? This is a network that passes untagged traffic to VLAN1, but as soon as traffic from any other network comes to the trunk port, in our case VLAN20, it is necessarily tagged. Each frame has a DA destination address, an SA source address, and a VLAN tag that contains the VLAN ID. In our case, this identifier indicates that this traffic belongs to VLAN20, therefore it can only be sent through the VLAN20 port and destined for PC5. We can say that the Native VLAN decides whether the traffic should be tagged or not tagged.
Remember that VLAN1 is a Native VLAN by default, because by default all ports use VLAN1 as Native VLAN to transmit untagged traffic. However, in this case, the Default VLAN is only VLAN1, the only network that cannot be changed. If the switch receives untagged frames on the trunk port, it automatically assigns them to Native VLAN.
Simply put, in Cisco switches, any VLAN can be used as a Native VLAN, for example, VLAN20, and only VLAN1 can be used as Default VLAN.
In this case, we may have a problem. If we change for the trunk port of the first Native VLAN switch to VLAN20, the port will think: “since this is Native VLAN, then its traffic does not need to be tagged” and send untagged VLAN20 network traffic to the second switch on the trunk. The SW2 switch, having received this traffic, will say: “excellent, this traffic does not have a tag. According to my settings, my Native VLAN is VLAN1, so I have to send this untagged traffic over VLAN1. ” Thus, SW2 will forward the received traffic only to PC4 and PC-6, although it is designed by PC5. This will create a big security problem as it mixes VLAN traffic. That is why the same Native VLAN must always be configured on both trunk ports, that is, if the Native VLAN for the SW1 trunk port is VLAN20, then the same VLAN20 must be set as the Native VLAN on the SW2 trunk port.
This is the difference between the Native VLAN and the Default VLAN, and you need to remember that all Native VLANs in the trunk must match (translator's note: it’s better to use a network other than VLAN1 as the Native VLAN).
Let's look at it from the point of view of the switch. You can go into the switch and type the show vlan brief command, after which you will see that all ports of the switch are connected to Default VLAN1.

Below are shown 4 more VLANs: 1002,1003,1004 and 1005. This is also Default VLAN, you see this from their designation. They are the default networks because they are reserved for specific networks - Token Ring and FDDI. As you can see, they are in an active state, but are not supported, because networks of the mentioned standards are not connected to the switch.
The default designation for VLAN 1 cannot be changed because it is the default network. Since by default all switch ports belong to this network, all switches can communicate with each other by default, that is, without the need for additional port settings. If you want to connect the switch to another network, you enter the global settings mode and create this network, for example, VLAN20. Pressing “Enter”, you will go to the settings of the created network and you can give it a name, for example, Management, and then exit the settings.
If you use the show vlan brief command now, you will see that we have a new VLAN20 network that does not correspond to any of the switch ports. In order to assign a specific port to this network, you need to select an interface, for example, int e0 / 1, go into the settings of this port and enter the switchport mode access and switchport access vlan20 commands.
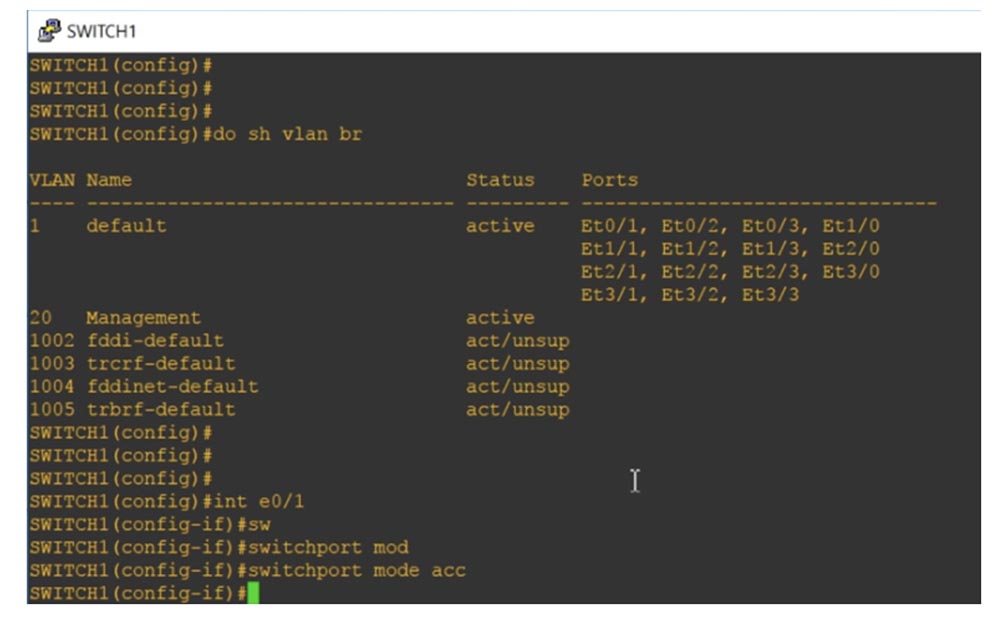
If we ask the system to show the status of the VLANs, we will see that now the Ethernet port 0/1 is destined for the Management network, that is, it was automatically moved here from the port area that is assigned by default for VLAN1.

Remember that each access port can have only one Data VLAN, so it cannot serve two VLANs at the same time.
Now take a look at the Native VLAN. I use the show int trunk command and see that the Ethernet0 / 0 port is dedicated to the trunk.

I did not need to do this on purpose, because the DTP protocol automatically assigned this interface for trunking. The port is in desirable mode, n-isl encapsulation, port state is trunking, network is Native VLAN1.
The following is a valid range of VLAN numbers 1–4094 for trunking and indicates that VLAN1 and VLAN20 are working for us. Now I will go into global configuration mode and type the command int e0 / 0, thanks to which I will go to the settings of this interface. I try to manually program this port to work in trunk mode with the switchport mode trunk command, however, the system does not accept the command, responding that: “an interface with an automatic trunk encapsulation mode cannot be switched to trunk mode.
Therefore, I must first configure the trunk encapsulation type, for which I use the switchport trunk encapsulation command. The system issued hints with possible parameters for this command:
dot1q — during trunking, the port uses 802.1q trunk encapsulation;
isl - during trunking, the port uses encapsulation of the trunking of only the proprietary Cisco ISL protocol;
negotiate - the device encapsulates the trunk with any device connected to this port.
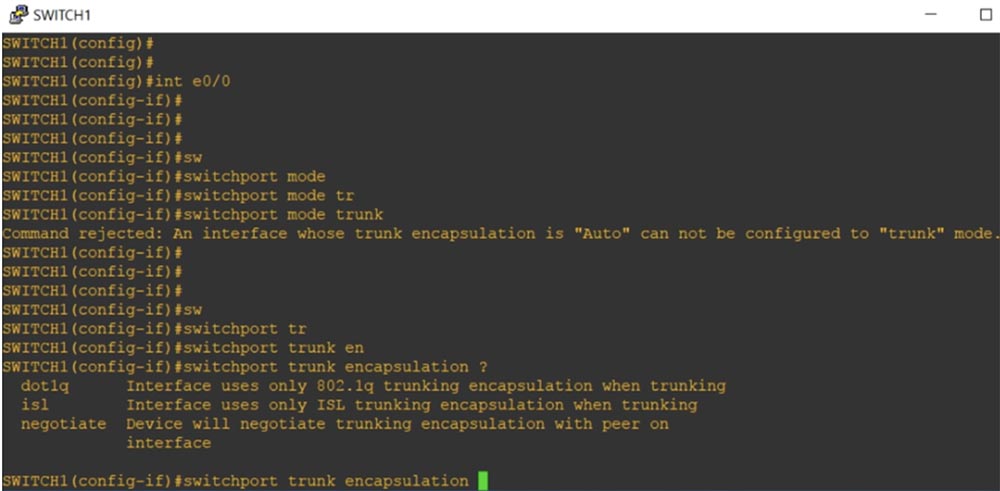
At each end of the trunk, the same type of encapsulation must be selected. By default, the out-of-box switch only supports dot1q trunking, since almost all network devices support this standard. I will program our interface to encapsulate trunking according to this standard with the switchport trunk encapsulation dot1q command, and then use the previously rejected switchport mode trunk command. Now our port is programmed to trunk mode.
If the trunk is formed by two Cisco switches, the proprietary ISL protocol will be used by default. If one switch supports dot1q and ISL, and the second only dot1q, the trunk will automatically be put into dot1q encapsulation mode. If we look again at the trunking parameters, we will see that now the encapsulation mode of the Et0 / 0 interface trunking has changed from n-isl to 802.1q.
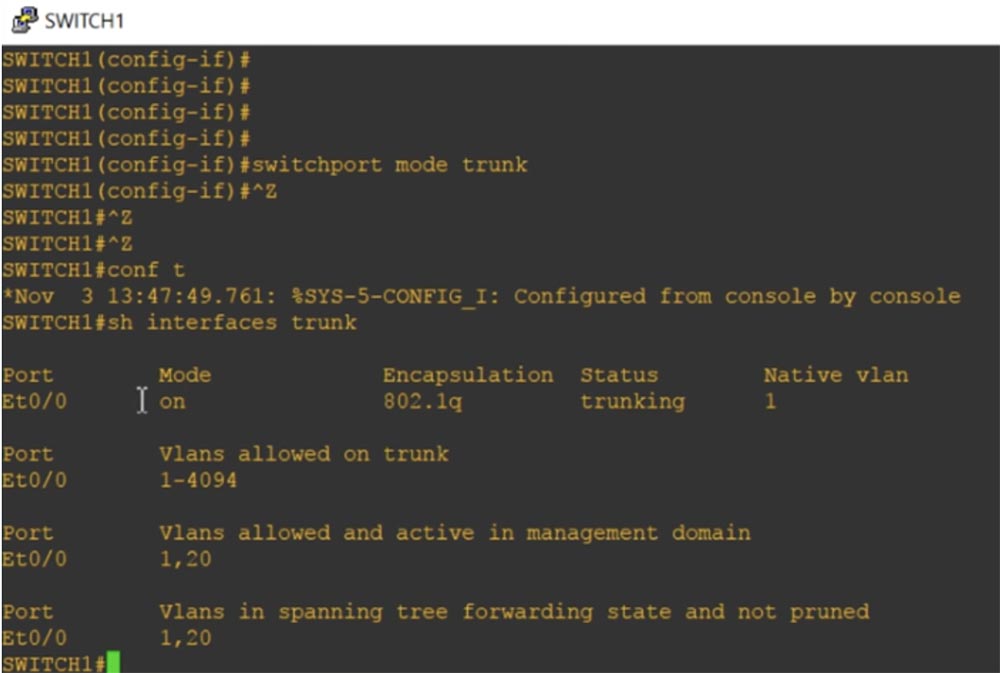
If we enter the show int e0 / 0 switchport command, we will see all the status parameters for this port.

You can see that by default VLAN1 is the Native VLAN for native trunking, and Native VLAN traffic tagging mode is possible. Next, I use the int e0 / 0 command, go to the settings of this interface and type switchport trunk, after which the system gives hints of possible parameters for this command.
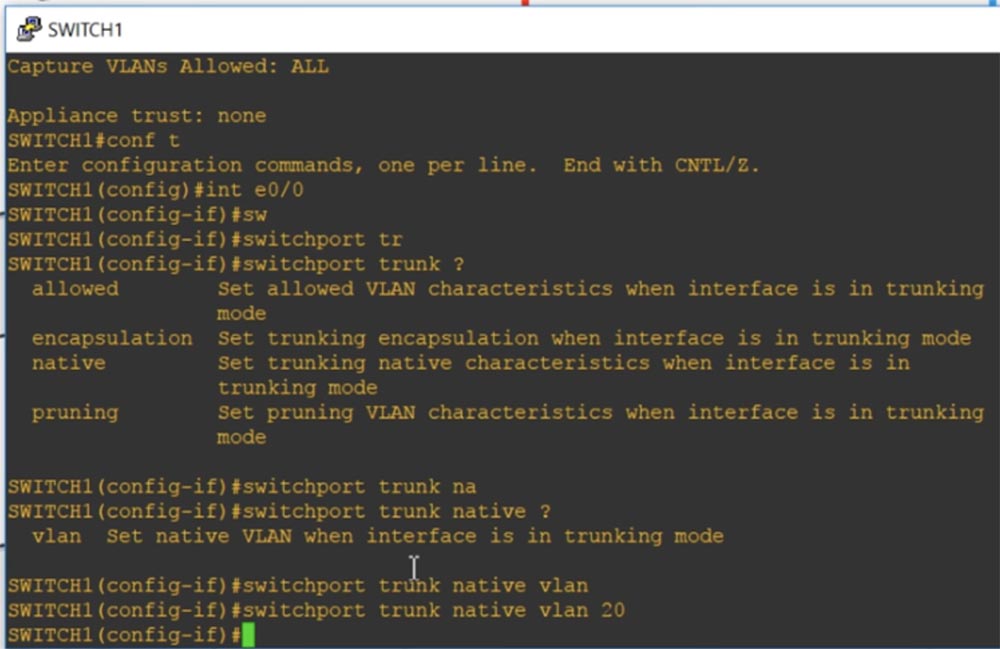
Allowed means that if the port is in trunk mode, then the permissible VLAN characteristics will be set. Encapsulation activates trunk encapsulation if the port is in trunk mode. I use the native parameter, which means that in trunk mode the native characteristics will be set for the port, and I enter the switchport trunk native VLAN20 command. Thus, in trunk mode VLAN20 will be the Native VLAN for this port of the first switch SW1.
We have another switch, SW2, which uses VLAN1 as its native port. Now you see that the CDP protocol displays a message that there is a mismatch between Native VLANs at both ends of the trunk: the trunk port of the first Ethernet0 / 0 switch uses Native VLAN20, and the trunk port of the second uses Native VLAN1. This illustrates the difference between Native VLAN and Default VLAN.
Let's get started with a basic and extended range of VLANs.

For a long time, Cisco only supported the range of VLAN numbers from 1 to 1005, while the range from 1002 to 1005 was reserved by default for Token Ring and FDDI VLAN. These networks were called regular VLANs. If you remember, the VLAN ID is a 12-bit tag that allows you to set the number to 4096, but for compatibility reasons, Cisco only used numbers up to 1005.
The extended VLAN range includes numbers 1006 through 4095. It can only be used on older devices if they support VTP v3. If you use VTP v3 and the extended VLAN range, you must disable VTP v1 and v2 support, because the first and second versions cannot work with VLANs if they have a number greater than 1005.
So if you use Extended VLAN for old switches, VTP must be in the “desable” state and you need to manually configure it for VLAN, otherwise the VLAN database will not be updated. If you intend to use Extended VLAN with VTP, you need the third version of VTP.
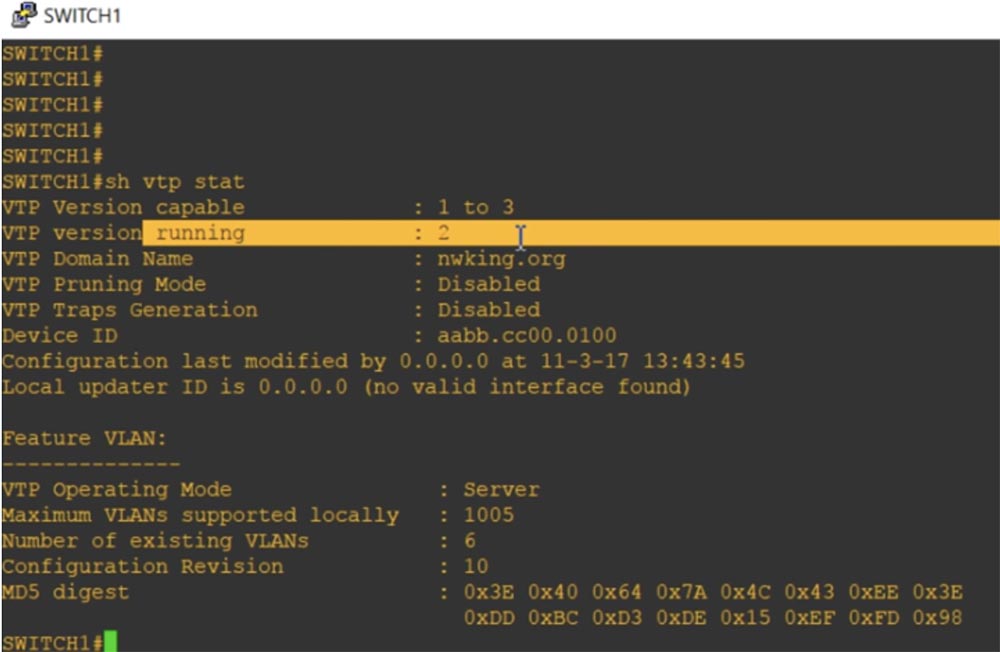
Let's look at the VTP status using the show vtp status command. You see that the switch works in VTP v2 mode, while it is possible to support versions 1 and 3. I assigned it the domain name nwking.org.
The VTP server management mode is important here. You can see that the maximum number of supported VLANs is 1005. Thus, you can understand that by default this switch only supports the normal VLAN range.
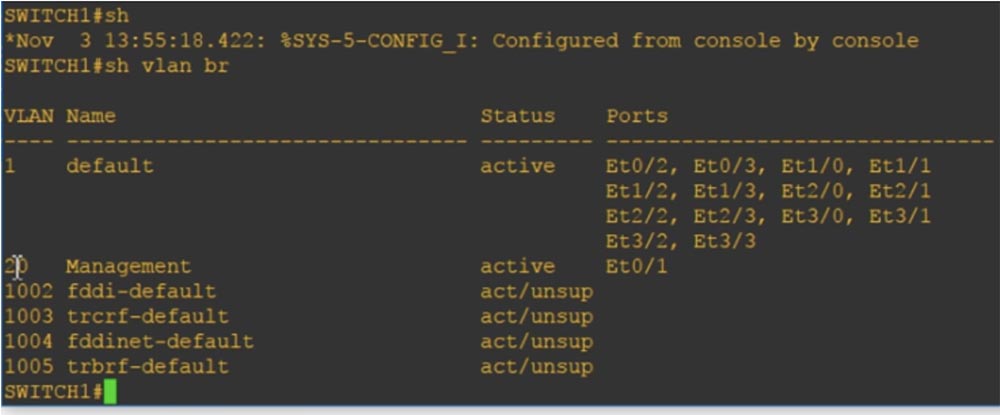
Now I type the show vlan brief command and you will see the VLAN20 Management, which is mentioned here because it is part of the VLAN database.
If I ask you now to show the current device configuration with the show run command, we will not see any mention of VLANs, because they are contained only in the VLAN database.
Next, I use the vtp mode command to configure the VTP mode of operation. The switches of the old models had only three parameters for this command: client, which switches the switch to client mode, server, which turns on server mode, and transparent, which switches the switch to "transparent" mode. Since it was impossible to completely disable VTP on old switches, in this mode the switch, remaining in the VTP domain, simply stopped accepting VLAN database updates arriving at its ports via VTP.
In new switches, the off parameter appeared, which allows you to completely disable VTP mode. Let's put the device into transparent mode with the vtp mode transparent command and look again at the current configuration. As you can see, now an entry about VLAN20 has been added to it. Thus, if we add some kind of VLAN whose number is in the usual VLAN range with numbers from 1 to 1005, and the VTP is in transparent or off mode, then in accordance with the internal VLAN policies, this network will be added to current configuration and into the database of virtual local area networks.
Let's try to add VLAN 3000, and you will see that in transparent mode it also appeared in the current configuration. Usually, if we want to add a network from the extended VLAN range, we should use the vtp version 3 command. As you can see, both VLAN20 and VLAN3000 are shown in the current configuration.
If you exit transparent mode and enable server mode using the vtp mode server command, and then look at the current configuration again, you can see that the VLAN entries have completely disappeared.This is because all VLAN information is stored only in the VLAN database and can only be viewed in transparent VTP mode. Since I turned on VTP v3 mode, after using the show vtp status command, you can see that the maximum number of supported VLANs has increased to 4096.
So, the VTP v1 and VTP v2 database supports only regular VLANs with numbers from 1 to 1005, and the VTP database v3 includes extended VLAN entries with numbers from 1 to 4096. If you use VTP transparent or VTP off, VLAN information will be added to the current configuration. If you want to use the extended VLAN range, the device must be in VTP v3 mode. This is the difference between regular and advanced VLANs.
VLAN VLAN . , , VLAN.

IP-. IP- Cisco , , - — . , , , VLAN. 11 12 , , , «» VLAN, , . VLAN .
VLAN. , PC1 PC2 VLAN20, PC3 – VLAN30, IP- VLAN50.
SW1 2 VLAN – .
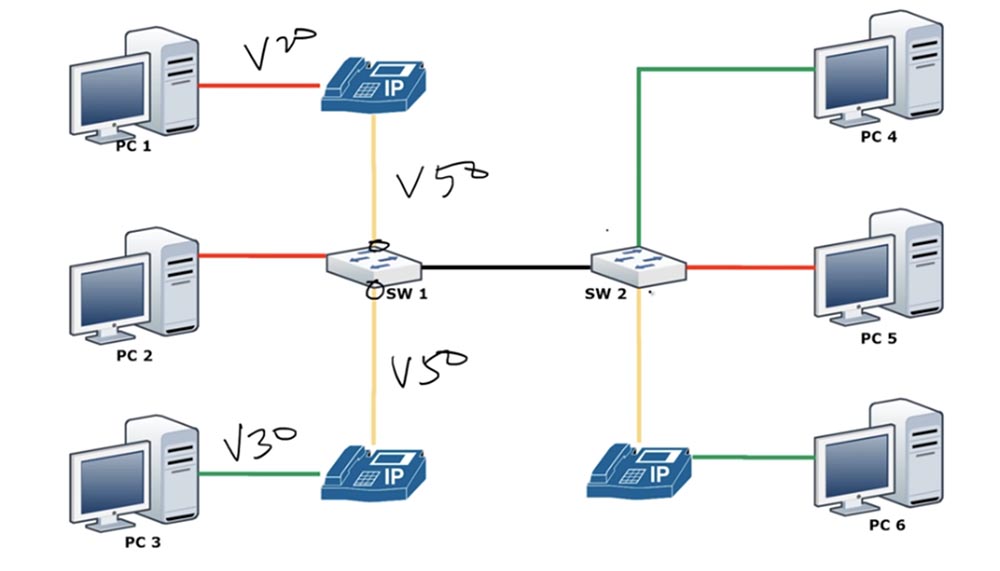
, access VLAN VLAN, VLAN . switchport access vlan 10, switchport access vlan 20 switchport access vlan 50. : switchport access vlan 10 switchport voice vlan 50. , IP- , VLAN50 switchport access VLAN20 SW1. , .
VLAN50, Ethernet 0/1 switchport mode access. switchport access vlan 10 switchport voice vlan 50.
VLAN , Ethernet 0/0 switchport trunk native vlan 1. VLAN, , Ethernet 0/1 – VLAN 50 VLAN20.
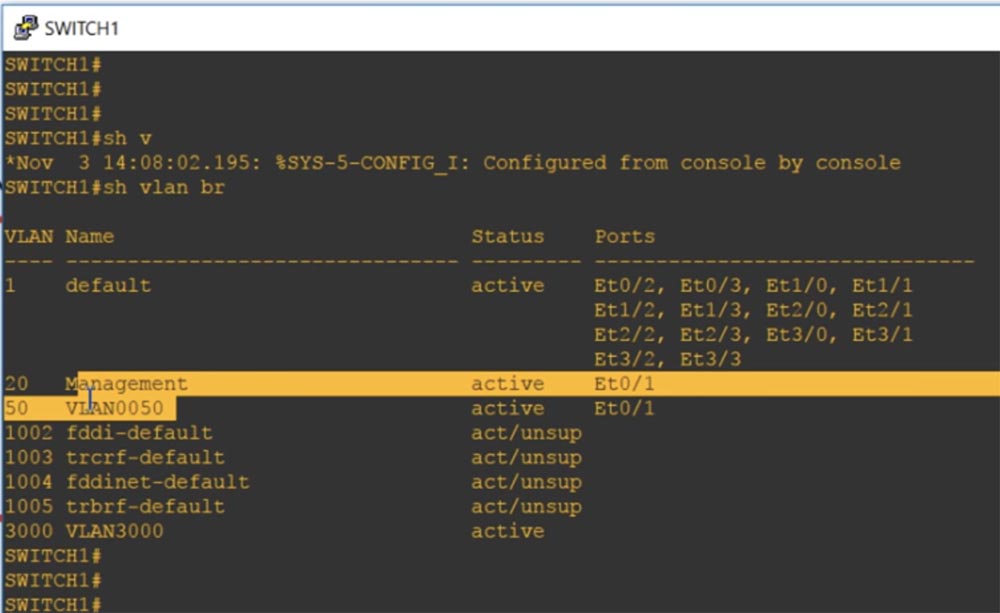
, , VLAN, , Voice VLAN. , show int trunk, , - VLAN, VLAN1.

, , , : , access –.
If you type the command show int e0 / 1 switchport, you can see that some of the characteristics correspond to two modes of operation: we have both static access and encapsulation of trunking. In this case, the access mode corresponds to the VLAN 20 Management data network and at the same time there is a VLAN 50 voice network.
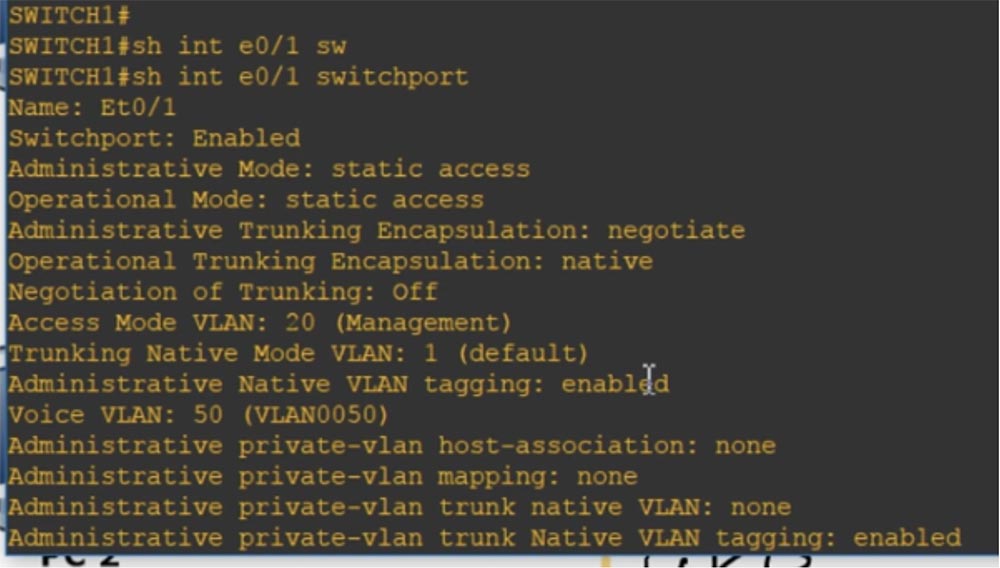
You can look at the current configuration, which will also show that there are access vlan 20 and voice vlan 50 networks on this port.
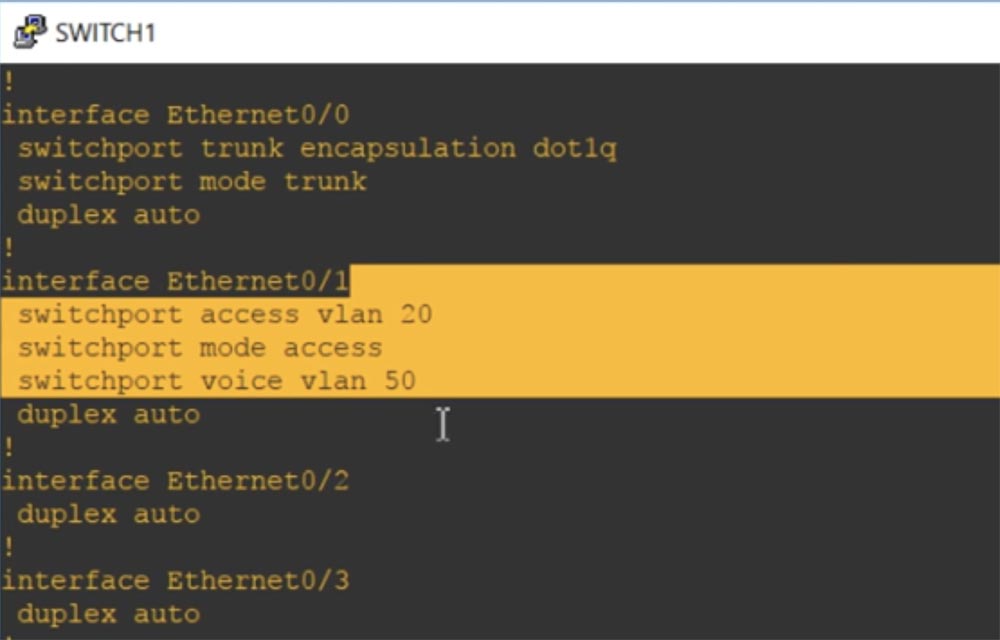
This is the difference between Data VLANs and Voice VLANs. I hope you understand everything that I talked about, if not - just review this video lesson again.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that was invented by us for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
Today’s video tutorial “Day 34”, we begin the topic of the ICND2 course. Many ask me why we did not consider OSPF and EIGRP. The fact is that these protocols are not included in the subject matter of the ICND1 course and are being studied in preparation for passing ICND2. Starting today, we will begin coverage of the second part of the course, and of course, we will study the OSPF and EIGRP punctures. Before starting today's topic, I want to talk about structuring our video tutorials. When presenting the topic of ICND1, I did not adhere to the accepted patterns, but simply logically explained the material, since I thought that this method was easier to understand. Now, while studying ICND2, at the request of students, I will begin to submit training material in accordance with the curriculum and curriculum of the Cisco course.
If you go to the company's website, you will see this plan and the fact that the entire course is divided into 5 main parts:
- Technologies for switching local networks (26% of the training material);
- Routing technologies (29%);
- Technologies of global networks (16%);
- Infrastructure services (14%);
- Maintenance of infrastructure (15%).
I will start with the first part. If you click on the drop-down menu on the right, you can see the detailed topics of this section. Today’s video tutorial will cover the topics of section 1.1: “Configuring, checking and troubleshooting VLANs (normal / extended range) covering several switches” and subsections 1.1a “Access ports (data and voice messages)” and 1.1.b “Default VLAN” .
Further, I will try to adhere to the same principle of presentation, that is, each video lesson will be devoted to one section with subsections, and if there is not enough material, I will combine the topics of several sections in one lesson, for example, 1.2 and 1.3. If there is a lot of section material, I will split it into two videos. In any case, we will follow the course program, and you can easily compare the compliance of your notes with the current Cisco curriculum.

You see my new desktop on the screen, it is Windows 10. If you want to improve your desktop with various widgets, you can watch my video called “Pimp Your Desktop”, where I tell you how to customize the desktop of your computer to suit your needs. I post videos of this kind on another channel, ExplainWorld, so you can use the link in the upper right corner and see its contents.
Before the start of the lesson, I’ll ask you not to forget to share my videos and like them. I also want to remind our contacts on social networks and links to my personal pages. You can write to me by e-mail, and as I have already said, the priority in receiving my personal response will be given to people who made a donation on our website.
If you don’t make a donation, it’s okay, you can leave your comments under the video tutorials on the YouTube channel, and I will respond to them whenever possible.
So, today, according to the Cisco schedule, we will consider 3 questions: compare the Default VLAN, or the default VLAN, with the Native VLAN, or the “native” VLAN, find out how the Normal VLAN (normal range of VLANs) differs from the extended range of Extended VLANs Consider the difference between a Data VLAN (Voice VLAN) and a Voice VLAN (Voice VLAN). As I said, we have already studied this issue in previous series, but rather superficially, so many students still have difficulty determining the difference between VLAN types. Today I will explain it so that everyone understands.
Consider the difference between Default VLAN and Native VLAN. If you take a brand new Cisco switch with factory settings, it will have 5 VLANs - VLAN1, VLAN1002, VLAN1003, VLAN1004 and VLAN1005.

VLAN1 is the default VLAN for all Cisco devices, and VLAN 1002-1005 are reserved for Token Ring and FDDI. VLAN1 cannot be deleted or renamed, interfaces cannot be added to it, and all switch ports belong to this network by default until they are configured differently. By default, all switches can communicate with each other because they are all part of VLAN1. This is what “Default VLAN,” or Default VLAN, means.
If you go into the settings of switch SW1 and assign two interfaces to the VLAN20 network, they will become part of the VLAN20 network. Before starting this lesson today, I strongly advise you to review the 11.12 and 13 days series mentioned above, because I will not repeat what VLANs are and how they work.

I’ll just remind you that you cannot automatically assign interfaces to a VLAN20 network until you create it, so first you need to go into the global configuration mode of the switch and create VLAN20. You can look at the CLI settings console and understand what I mean. After you have assigned these 2 ports to work with VLAN20, PC1 and PC2 will be able to communicate with each other because they will both belong to the same VLAN20 network. But PC3 will still be part of VLAN1 and therefore will not be able to connect to computers on VLAN20.
We have a second switch SW2, one of the interfaces of which is assigned to work with VLAN20, and PC5 is connected to this port. With this connection scheme, PC5 cannot communicate with PC4 and PC6, but these two computers can communicate with each other because they belong to the same VLAN1 network.
Both switches are connected by trunk through appropriately configured ports. I won’t repeat myself, I’ll just say that all ports of the switch are configured by default for DTP trunking mode. If you connect a computer to some port, this port will use access mode. If you want to switch the port to which PC3 is connected to this mode, you must enter the switchport mode access command.
So, if you connect the two switches to each other, they form a trunk. The upper two ports of SW1 will only pass traffic on VLAN20, the lower port will only on VLAN1 traffic, but the trunk connection will pass through all the traffic passing through the switch. Thus, both VLAN1 and VLAN20 will receive traffic to SW2.
As you remember, VLANs have a local meaning. Therefore, SW2 knows that traffic arriving at port VLAN1 from PC4 can only be sent to PC6 through a port that also belongs to VLAN1. However, when one switch sends traffic to another switch on the trunk, it must use a mechanism to explain to the second switch what kind of traffic it is. As such a mechanism, the Native VLAN is used, which is connected to the trunk port and passes tagged traffic through itself.
 \
\
As I said, the switch has only one network that is not subject to change - this is the default network VLAN1. But by default, Native VLAN is VLAN1. What is a Native VLAN? This is a network that passes untagged traffic to VLAN1, but as soon as traffic from any other network comes to the trunk port, in our case VLAN20, it is necessarily tagged. Each frame has a DA destination address, an SA source address, and a VLAN tag that contains the VLAN ID. In our case, this identifier indicates that this traffic belongs to VLAN20, therefore it can only be sent through the VLAN20 port and destined for PC5. We can say that the Native VLAN decides whether the traffic should be tagged or not tagged.
Remember that VLAN1 is a Native VLAN by default, because by default all ports use VLAN1 as Native VLAN to transmit untagged traffic. However, in this case, the Default VLAN is only VLAN1, the only network that cannot be changed. If the switch receives untagged frames on the trunk port, it automatically assigns them to Native VLAN.
Simply put, in Cisco switches, any VLAN can be used as a Native VLAN, for example, VLAN20, and only VLAN1 can be used as Default VLAN.
In this case, we may have a problem. If we change for the trunk port of the first Native VLAN switch to VLAN20, the port will think: “since this is Native VLAN, then its traffic does not need to be tagged” and send untagged VLAN20 network traffic to the second switch on the trunk. The SW2 switch, having received this traffic, will say: “excellent, this traffic does not have a tag. According to my settings, my Native VLAN is VLAN1, so I have to send this untagged traffic over VLAN1. ” Thus, SW2 will forward the received traffic only to PC4 and PC-6, although it is designed by PC5. This will create a big security problem as it mixes VLAN traffic. That is why the same Native VLAN must always be configured on both trunk ports, that is, if the Native VLAN for the SW1 trunk port is VLAN20, then the same VLAN20 must be set as the Native VLAN on the SW2 trunk port.
This is the difference between the Native VLAN and the Default VLAN, and you need to remember that all Native VLANs in the trunk must match (translator's note: it’s better to use a network other than VLAN1 as the Native VLAN).
Let's look at it from the point of view of the switch. You can go into the switch and type the show vlan brief command, after which you will see that all ports of the switch are connected to Default VLAN1.

Below are shown 4 more VLANs: 1002,1003,1004 and 1005. This is also Default VLAN, you see this from their designation. They are the default networks because they are reserved for specific networks - Token Ring and FDDI. As you can see, they are in an active state, but are not supported, because networks of the mentioned standards are not connected to the switch.
The default designation for VLAN 1 cannot be changed because it is the default network. Since by default all switch ports belong to this network, all switches can communicate with each other by default, that is, without the need for additional port settings. If you want to connect the switch to another network, you enter the global settings mode and create this network, for example, VLAN20. Pressing “Enter”, you will go to the settings of the created network and you can give it a name, for example, Management, and then exit the settings.
If you use the show vlan brief command now, you will see that we have a new VLAN20 network that does not correspond to any of the switch ports. In order to assign a specific port to this network, you need to select an interface, for example, int e0 / 1, go into the settings of this port and enter the switchport mode access and switchport access vlan20 commands.

If we ask the system to show the status of the VLANs, we will see that now the Ethernet port 0/1 is destined for the Management network, that is, it was automatically moved here from the port area that is assigned by default for VLAN1.

Remember that each access port can have only one Data VLAN, so it cannot serve two VLANs at the same time.
Now take a look at the Native VLAN. I use the show int trunk command and see that the Ethernet0 / 0 port is dedicated to the trunk.

I did not need to do this on purpose, because the DTP protocol automatically assigned this interface for trunking. The port is in desirable mode, n-isl encapsulation, port state is trunking, network is Native VLAN1.
The following is a valid range of VLAN numbers 1–4094 for trunking and indicates that VLAN1 and VLAN20 are working for us. Now I will go into global configuration mode and type the command int e0 / 0, thanks to which I will go to the settings of this interface. I try to manually program this port to work in trunk mode with the switchport mode trunk command, however, the system does not accept the command, responding that: “an interface with an automatic trunk encapsulation mode cannot be switched to trunk mode.
Therefore, I must first configure the trunk encapsulation type, for which I use the switchport trunk encapsulation command. The system issued hints with possible parameters for this command:
dot1q — during trunking, the port uses 802.1q trunk encapsulation;
isl - during trunking, the port uses encapsulation of the trunking of only the proprietary Cisco ISL protocol;
negotiate - the device encapsulates the trunk with any device connected to this port.

At each end of the trunk, the same type of encapsulation must be selected. By default, the out-of-box switch only supports dot1q trunking, since almost all network devices support this standard. I will program our interface to encapsulate trunking according to this standard with the switchport trunk encapsulation dot1q command, and then use the previously rejected switchport mode trunk command. Now our port is programmed to trunk mode.
If the trunk is formed by two Cisco switches, the proprietary ISL protocol will be used by default. If one switch supports dot1q and ISL, and the second only dot1q, the trunk will automatically be put into dot1q encapsulation mode. If we look again at the trunking parameters, we will see that now the encapsulation mode of the Et0 / 0 interface trunking has changed from n-isl to 802.1q.

If we enter the show int e0 / 0 switchport command, we will see all the status parameters for this port.

You can see that by default VLAN1 is the Native VLAN for native trunking, and Native VLAN traffic tagging mode is possible. Next, I use the int e0 / 0 command, go to the settings of this interface and type switchport trunk, after which the system gives hints of possible parameters for this command.

Allowed means that if the port is in trunk mode, then the permissible VLAN characteristics will be set. Encapsulation activates trunk encapsulation if the port is in trunk mode. I use the native parameter, which means that in trunk mode the native characteristics will be set for the port, and I enter the switchport trunk native VLAN20 command. Thus, in trunk mode VLAN20 will be the Native VLAN for this port of the first switch SW1.
We have another switch, SW2, which uses VLAN1 as its native port. Now you see that the CDP protocol displays a message that there is a mismatch between Native VLANs at both ends of the trunk: the trunk port of the first Ethernet0 / 0 switch uses Native VLAN20, and the trunk port of the second uses Native VLAN1. This illustrates the difference between Native VLAN and Default VLAN.
Let's get started with a basic and extended range of VLANs.

For a long time, Cisco only supported the range of VLAN numbers from 1 to 1005, while the range from 1002 to 1005 was reserved by default for Token Ring and FDDI VLAN. These networks were called regular VLANs. If you remember, the VLAN ID is a 12-bit tag that allows you to set the number to 4096, but for compatibility reasons, Cisco only used numbers up to 1005.
The extended VLAN range includes numbers 1006 through 4095. It can only be used on older devices if they support VTP v3. If you use VTP v3 and the extended VLAN range, you must disable VTP v1 and v2 support, because the first and second versions cannot work with VLANs if they have a number greater than 1005.
So if you use Extended VLAN for old switches, VTP must be in the “desable” state and you need to manually configure it for VLAN, otherwise the VLAN database will not be updated. If you intend to use Extended VLAN with VTP, you need the third version of VTP.
Let's look at the VTP status using the show vtp status command. You see that the switch works in VTP v2 mode, while it is possible to support versions 1 and 3. I assigned it the domain name nwking.org.
The VTP server management mode is important here. You can see that the maximum number of supported VLANs is 1005. Thus, you can understand that by default this switch only supports the normal VLAN range.

Now I type the show vlan brief command and you will see the VLAN20 Management, which is mentioned here because it is part of the VLAN database.

If I ask you now to show the current device configuration with the show run command, we will not see any mention of VLANs, because they are contained only in the VLAN database.
Next, I use the vtp mode command to configure the VTP mode of operation. The switches of the old models had only three parameters for this command: client, which switches the switch to client mode, server, which turns on server mode, and transparent, which switches the switch to "transparent" mode. Since it was impossible to completely disable VTP on old switches, in this mode the switch, remaining in the VTP domain, simply stopped accepting VLAN database updates arriving at its ports via VTP.
In new switches, the off parameter appeared, which allows you to completely disable VTP mode. Let's put the device into transparent mode with the vtp mode transparent command and look again at the current configuration. As you can see, now an entry about VLAN20 has been added to it. Thus, if we add some kind of VLAN whose number is in the usual VLAN range with numbers from 1 to 1005, and the VTP is in transparent or off mode, then in accordance with the internal VLAN policies, this network will be added to current configuration and into the database of virtual local area networks.
Let's try to add VLAN 3000, and you will see that in transparent mode it also appeared in the current configuration. Usually, if we want to add a network from the extended VLAN range, we should use the vtp version 3 command. As you can see, both VLAN20 and VLAN3000 are shown in the current configuration.
If you exit transparent mode and enable server mode using the vtp mode server command, and then look at the current configuration again, you can see that the VLAN entries have completely disappeared.This is because all VLAN information is stored only in the VLAN database and can only be viewed in transparent VTP mode. Since I turned on VTP v3 mode, after using the show vtp status command, you can see that the maximum number of supported VLANs has increased to 4096.
So, the VTP v1 and VTP v2 database supports only regular VLANs with numbers from 1 to 1005, and the VTP database v3 includes extended VLAN entries with numbers from 1 to 4096. If you use VTP transparent or VTP off, VLAN information will be added to the current configuration. If you want to use the extended VLAN range, the device must be in VTP v3 mode. This is the difference between regular and advanced VLANs.
VLAN VLAN . , , VLAN.

IP-. IP- Cisco , , - — . , , , VLAN. 11 12 , , , «» VLAN, , . VLAN .
VLAN. , PC1 PC2 VLAN20, PC3 – VLAN30, IP- VLAN50.
SW1 2 VLAN – .

, access VLAN VLAN, VLAN . switchport access vlan 10, switchport access vlan 20 switchport access vlan 50. : switchport access vlan 10 switchport voice vlan 50. , IP- , VLAN50 switchport access VLAN20 SW1. , .
VLAN50, Ethernet 0/1 switchport mode access. switchport access vlan 10 switchport voice vlan 50.
VLAN , Ethernet 0/0 switchport trunk native vlan 1. VLAN, , Ethernet 0/1 – VLAN 50 VLAN20.

, , VLAN, , Voice VLAN. , show int trunk, , - VLAN, VLAN1.

, , , : , access –.
If you type the command show int e0 / 1 switchport, you can see that some of the characteristics correspond to two modes of operation: we have both static access and encapsulation of trunking. In this case, the access mode corresponds to the VLAN 20 Management data network and at the same time there is a VLAN 50 voice network.

You can look at the current configuration, which will also show that there are access vlan 20 and voice vlan 50 networks on this port.

This is the difference between Data VLANs and Voice VLANs. I hope you understand everything that I talked about, if not - just review this video lesson again.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that was invented by us for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
All Articles