Confidential "cloud". We are looking for an alternative to open solutions
I am an engineer by training, but I communicate more with entrepreneurs and production directors. Some time ago, the owner of an industrial company asked for advice. Despite the fact that the company is large, and created in the 90s, management and accounting work the old fashioned way in the local network.
This is a consequence of concerns for their business and increased control by the state. Laws and regulations can be interpreted by inspection bodies very widely. An example is the amendments to the Tax Code, eliminating the statute of limitations for tax violations, the actual destruction of banking and audit secrets .
As a result, the owner of the enterprise began to look for solutions for the reliable storage of information and the safe transfer of documents. Virtual "safe".
We worked on the task with a full-time system administrator: we need a deep analysis of existing platforms.
I suggested removing the fourth point, because Russian applications have official certificates. The director explicitly said what should be done with such certificates.
I selected three solutions (the more choices, the more doubt):
The owner of the company is poorly versed in the technical subtleties, so I designed the report in the form of lists of the pros and cons of each option.
His first question is: what's the point of developing something for free? Syncthing was abandoned right away. Arguments did not work.
After a couple of days, the customer categorically dismissed Resilio Sync due to lack of support, as it is not clear where to turn in an emergency. Plus distrust of the American company registration.
For further analysis, the Pvtbox Electronic Safe remained. We conducted a full technical audit of this platform with emphasis on the possibility of interception, decryption of data and unauthorized entry into the information storage.
We did an analysis of the compounds at the start of the program, in the process of work and in a calm state. Traffic by modern standards is originally encrypted. Let's try to conduct a MITM attack and replace the certificate on the fly using Linux (Xubuntu Linux 18.04), Wireshark , Mitmproxy . To do this, we will implement an intermediary between the Pvtbox application and the pvtbox.net server (there is an exchange of data with the pvtbox.net server via an https connection).
We launch the application to make sure that the program and file synchronization work in it. In Linux, you can immediately observe the logging if you run the program from the terminal.

We turn off the application and replace the host address pvtbox.net in the file / etc / hosts with superuser privileges. The address is replaced with the address of our proxy server.
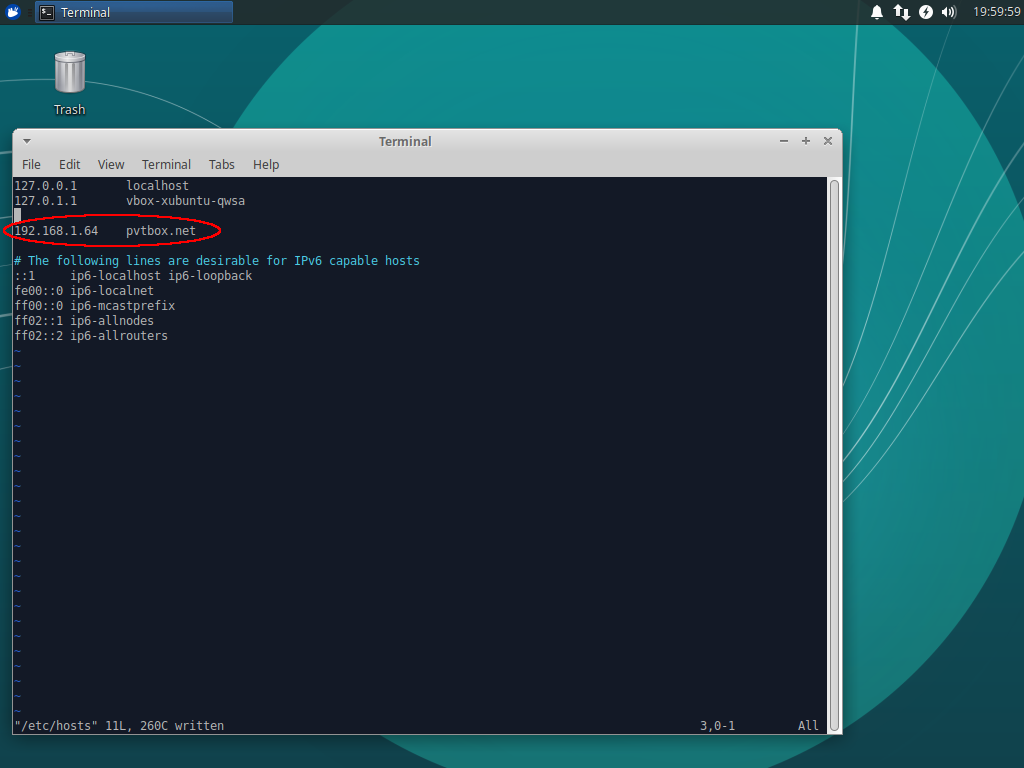
Now we will prepare our proxy server for the MITM attack on the computer with the address 192.168.1.64 in our local network. To do this, install the mitmproxy package version 4.0.4.
Launch the proxy server on port 443:
$ sudo mitmproxy -p 443
We start the Pvtbox program on the first computer, look at the output of mitmproxy and the application logs.
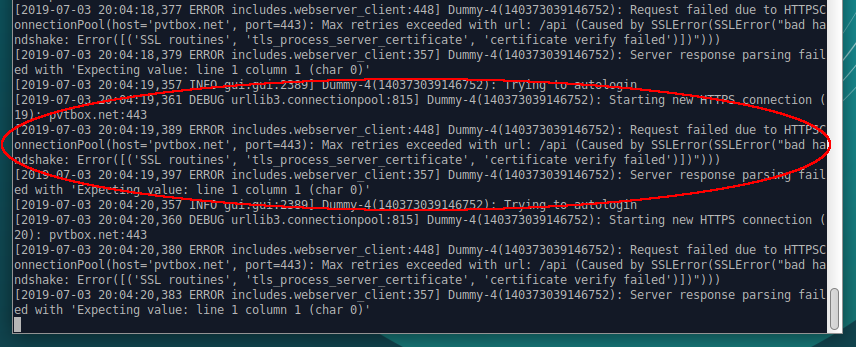
Mitmproxy reports that the client does not trust the spoof certificate from the proxy server. In the application logs, we also observe that the proxy server certificate does not pass the verification and the program refuses to work.
Install the mitmproxy proxy certificate on the computer with the Pvtbox application to make the certificate “trusted”. On the computer, install the ca-certificates package. Then copy the mitmproxy-ca-cert.pem certificate from the .mitmproxy directory of the proxy server to the computer with the Pvtbox application in the / usr / local / share / ca-certificates directory.
We execute the commands:
$ sudo openssl x509 -in mitmproxy-ca-cert.pem -inform PEM -out mitmproxy-ca-cert.crt
$ sudo update-ca-certificates

Launch the Pvtbox app. The certificate failed verification again, the program refuses to work. The application probably uses the certificate pinning security mechanism.
A similar attack was carried out on the signalserver.pvtbox.net host , as well as on the peer-2-peer connection between nodes. The developer indicates that the application for establishing peer-2-peer connections uses the open webrtc protocol which uses end-to-end encryption using the DTLSv1.2 protocol .
Keys are generated for each connection setup and transmitted over an encrypted channel through signalserver.pvtbox.net.
Theoretically, it would be possible to intercept offer and answer webrtc messages, replace encryption keys there and be able to decrypt all messages arriving via webrtc. But it was not possible to conduct a mitm attack on signalserver.pvtbox.net, therefore there is no possibility to intercept and replace messages sent through signalserver.pvtbox.net.
Accordingly, it is not possible to carry out this attack on a peer-2-peer connection.
A certificate file that came with the program was also detected. The file is located on the path /opt/pvtbox/certifi/cacert.pem. This file has been replaced with a file that contains a trusted certificate from our mitmproxy proxy server. The result has not changed - the program refused to connect to the system, the same error was observed in the log,
that the certificate does not pass verification.
I failed to intercept or replace traffic. File names, and even more so their contents are transmitted in encrypted form, end-to-end encryption is used. The application implements a number of security mechanisms that prevent wiretapping and implementation.
As a result, the company purchased two dedicated servers (physically in different places) for permanent access to information. The first server is used for receiving, processing and storing information, the second - for backup.
The director’s working terminal and an iOS mobile phone were connected to the received individual cloud. Other employees were connected by a regular system administrator and Pvtbox technical support.
Over the past time, there have been no complaints from a friend. I hope my review will help Habr's readers in a similar situation.
This is a consequence of concerns for their business and increased control by the state. Laws and regulations can be interpreted by inspection bodies very widely. An example is the amendments to the Tax Code, eliminating the statute of limitations for tax violations, the actual destruction of banking and audit secrets .
As a result, the owner of the enterprise began to look for solutions for the reliable storage of information and the safe transfer of documents. Virtual "safe".
We worked on the task with a full-time system administrator: we need a deep analysis of existing platforms.
- the service should not be cloudy, in the classical sense of the word, i.e. without saving at the facilities of a third-party organization. Only your server;
- strong encryption of transmitted and stored data is required;
- the ability to urgently delete content from any device at the click of a button is mandatory;
- The solution is developed abroad.
I suggested removing the fourth point, because Russian applications have official certificates. The director explicitly said what should be done with such certificates.
Choose options
I selected three solutions (the more choices, the more doubt):
- Open Source is a Syncthing.net project supported by development enthusiast Jacob Borg.
- Resilio.com , curated by American Resilio Inc. (previously called BitTorrent Sync).
- Pvtbox Project Electronic safe from pvtbox.net synchronization application. Cyprus registration.
The owner of the company is poorly versed in the technical subtleties, so I designed the report in the form of lists of the pros and cons of each option.
Analysis Summary
Syncthing
Pros :
- Open source
- Activity of the main developer;
- The project has existed for a very long time;
- Free.
Minuses:
- There is no client for the iOS shell;
- Slow Turn servers, (they are free, therefore they slow down). For those, who
not in the know, Turn is used when it is impossible to connect directly; - Complex interface configuration (many years of programming experience are needed);
- Lack of fast commercial support.
Resilio
Pros: support for all devices and nimble Turn servers.
Cons: One and very significant is the complete ignoring by the support service of any calls. Zero reaction, even if you write from different addresses.
Pvtbox
Pros:
- Support for all devices;
- Fast Turn Server;
- The ability to download a file without installing the application;
- Adequate support service, incl. by phone.
Cons :
- Young project (few reviews and good reviews);
- A very "techie" not always clear site interface;
- There is no thoroughly detailed documentation, many issues have to pull support.
What did the customer choose
His first question is: what's the point of developing something for free? Syncthing was abandoned right away. Arguments did not work.
After a couple of days, the customer categorically dismissed Resilio Sync due to lack of support, as it is not clear where to turn in an emergency. Plus distrust of the American company registration.
For further analysis, the Pvtbox Electronic Safe remained. We conducted a full technical audit of this platform with emphasis on the possibility of interception, decryption of data and unauthorized entry into the information storage.
Audit process
We did an analysis of the compounds at the start of the program, in the process of work and in a calm state. Traffic by modern standards is originally encrypted. Let's try to conduct a MITM attack and replace the certificate on the fly using Linux (Xubuntu Linux 18.04), Wireshark , Mitmproxy . To do this, we will implement an intermediary between the Pvtbox application and the pvtbox.net server (there is an exchange of data with the pvtbox.net server via an https connection).
We launch the application to make sure that the program and file synchronization work in it. In Linux, you can immediately observe the logging if you run the program from the terminal.

We turn off the application and replace the host address pvtbox.net in the file / etc / hosts with superuser privileges. The address is replaced with the address of our proxy server.

Now we will prepare our proxy server for the MITM attack on the computer with the address 192.168.1.64 in our local network. To do this, install the mitmproxy package version 4.0.4.
Launch the proxy server on port 443:
$ sudo mitmproxy -p 443
We start the Pvtbox program on the first computer, look at the output of mitmproxy and the application logs.

Mitmproxy reports that the client does not trust the spoof certificate from the proxy server. In the application logs, we also observe that the proxy server certificate does not pass the verification and the program refuses to work.
Install the mitmproxy proxy certificate on the computer with the Pvtbox application to make the certificate “trusted”. On the computer, install the ca-certificates package. Then copy the mitmproxy-ca-cert.pem certificate from the .mitmproxy directory of the proxy server to the computer with the Pvtbox application in the / usr / local / share / ca-certificates directory.
We execute the commands:
$ sudo openssl x509 -in mitmproxy-ca-cert.pem -inform PEM -out mitmproxy-ca-cert.crt
$ sudo update-ca-certificates

Launch the Pvtbox app. The certificate failed verification again, the program refuses to work. The application probably uses the certificate pinning security mechanism.
A similar attack was carried out on the signalserver.pvtbox.net host , as well as on the peer-2-peer connection between nodes. The developer indicates that the application for establishing peer-2-peer connections uses the open webrtc protocol which uses end-to-end encryption using the DTLSv1.2 protocol .
Keys are generated for each connection setup and transmitted over an encrypted channel through signalserver.pvtbox.net.
Theoretically, it would be possible to intercept offer and answer webrtc messages, replace encryption keys there and be able to decrypt all messages arriving via webrtc. But it was not possible to conduct a mitm attack on signalserver.pvtbox.net, therefore there is no possibility to intercept and replace messages sent through signalserver.pvtbox.net.
Accordingly, it is not possible to carry out this attack on a peer-2-peer connection.
A certificate file that came with the program was also detected. The file is located on the path /opt/pvtbox/certifi/cacert.pem. This file has been replaced with a file that contains a trusted certificate from our mitmproxy proxy server. The result has not changed - the program refused to connect to the system, the same error was observed in the log,
that the certificate does not pass verification.
Audit Results
I failed to intercept or replace traffic. File names, and even more so their contents are transmitted in encrypted form, end-to-end encryption is used. The application implements a number of security mechanisms that prevent wiretapping and implementation.
As a result, the company purchased two dedicated servers (physically in different places) for permanent access to information. The first server is used for receiving, processing and storing information, the second - for backup.
The director’s working terminal and an iOS mobile phone were connected to the received individual cloud. Other employees were connected by a regular system administrator and Pvtbox technical support.
Over the past time, there have been no complaints from a friend. I hope my review will help Habr's readers in a similar situation.
All Articles