Tracking the life cycle of users without pliers and electrical tape

Good day! You are worried about Valentina Ostroukhova from accounting. Sergey Sergeevich goes on vacation for two weeks and I will replace him. Could you give me access for this time to his folders in the // fs-buh / black_cashier / corruption directory? Thank you in advance!
Valentina Ostroukhova, partner accountant
Hello! This is Kolya from technical support. We have created a new group in AD specifically for the new head of the security department. There is access to specific servers. Can you add me there temporarily so that I can check the correctness of access? Thank you
Nikolay Zubatov, technical support engineer
What if this company does not follow the terms of the granted rights, and Valentina and Nikolai still have access to resources unnecessary for their work? The more users in the organization, the more such potential threats. In the article we will tell you what the life cycle of users consists of and about a tool to control it.
A user’s life cycle is provisioning, managing, and de-provisioning a user. At each of these stages, the user is assigned or disabled specific attributes: group membership, mailbox, access to file storage, etc. If you want to know more about the process, we recommend this document . And we will consider control over user attributes and the formation of detailed reporting.
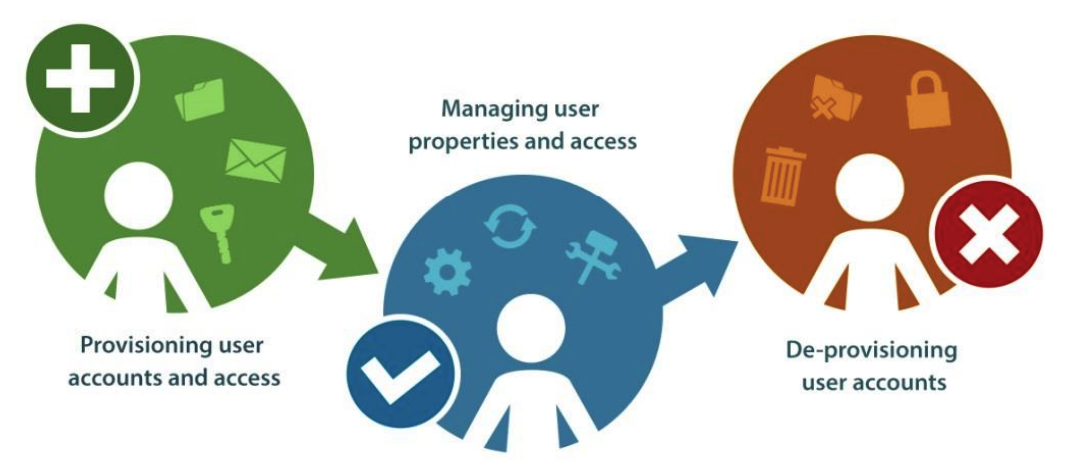
The first step works best in organizations - creating users and granting them rights. Managing and disabling users sometimes goes by the wayside and a mess begins. Two stories at the beginning of the article are a graphic illustration.
These stories are real cases of two of our customers. At the third customer, we found users who did not change their passwords for 2 or more years (no, the policy for the validity period was configured there, but not for everyone). It turned out that now no one knows why those users need such privileges. In one of the banks there was a case of unblocked non-personalized user accounts of remote users who were once in car dealerships and issued loans. The bank closed this area as early as two years, but active accounts remained. In another company, all users had access to a color laser printer, where employees were happy to print personal documents, photographs and other things unrelated to work. There was also a case with nested AD groups, in which users with administrative rights in the domain have not been identified for years.
Tell us in the comments about similar situations and how they were identified. The feeling that you can expect very amazing stories.
Self-written scripts and internal capabilities of AD (and other Microsoft products) do not always provide an opportunity to look in detail at the true extent of the discrepancy with the elementary security requirements. Plus, support for such decisions is usually performed by a specific person, without whom it is not clear how it works under the hood. Using a commercial solution for reporting on user rights is to identify hidden threats and reduce dependence on specific people.
Quest Enterprise Reporter is an access control and security reporting tool for Microsoft environments: Active Directory / Azure AD, Exchange / Exchange Online, Office 365, Windows Servers, OneDrive for Business, SQL Server, Azure infrastructure (VMs, disks, network security groups and rest). Several hundred predefined reports for the listed infrastructure, the ability to perform control actions on access rights (add a user to the group, cancel access to the directory, etc.) by directly navigating from the report and generating your own reports based on the data available in the infrastructure.
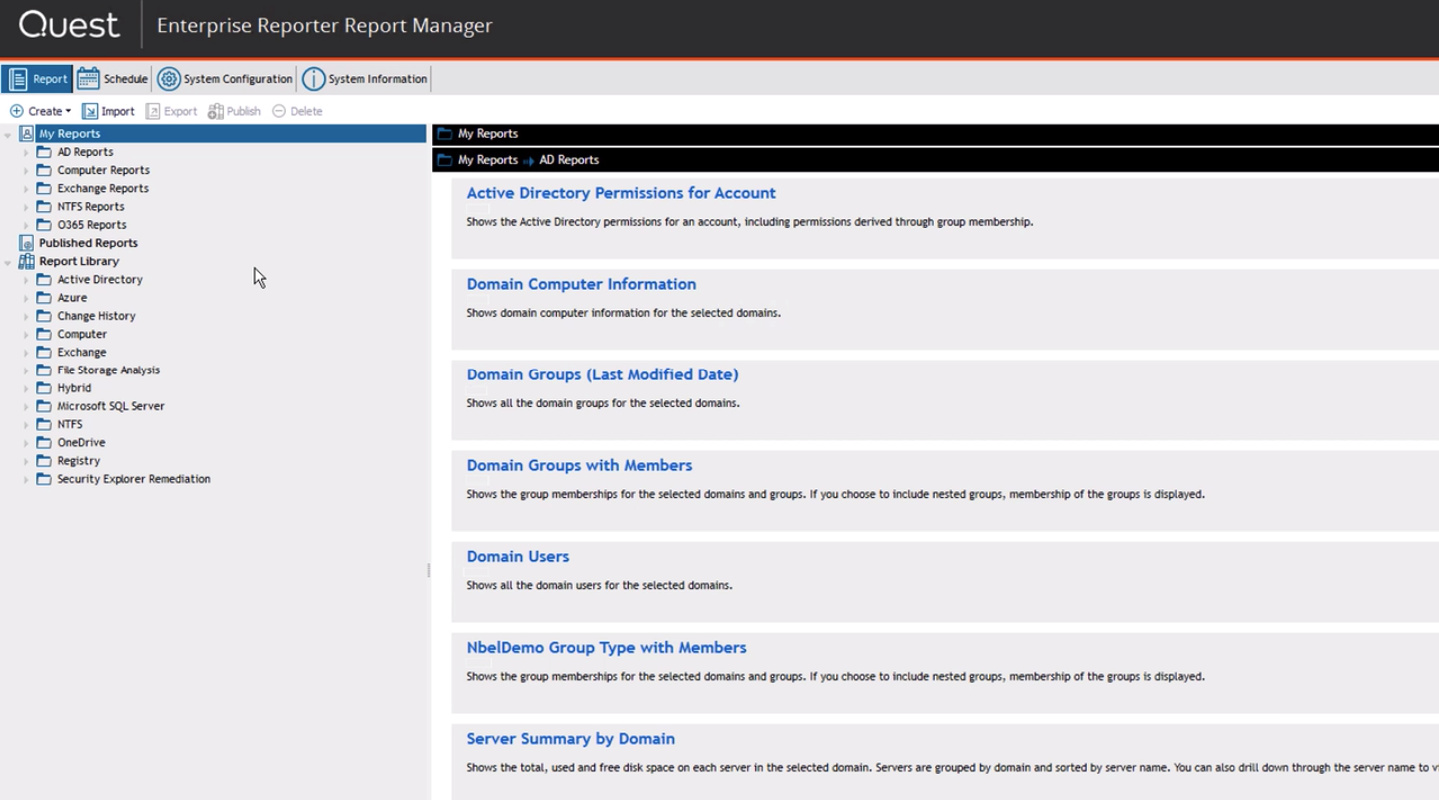
Each report can be generated on a schedule and checked, for example, if the objects are at the correct level if you use the “Red forest” or ESAE approach .
We highlighted the most revealing Quest Enterprise Reporter reports:
- Administrative users who have not logged in for the last 30 days. In the same report, you can see users from nested groups.
- Users with an infinite password.
- Services launched not from the system account. One type of attack is logging on to the server through a service (log on as a service), launched from a specific account.
- Groups in AD with a single user.
- Hotfixes installed on the computer.
- Software installed on domain controllers (or any other computers).
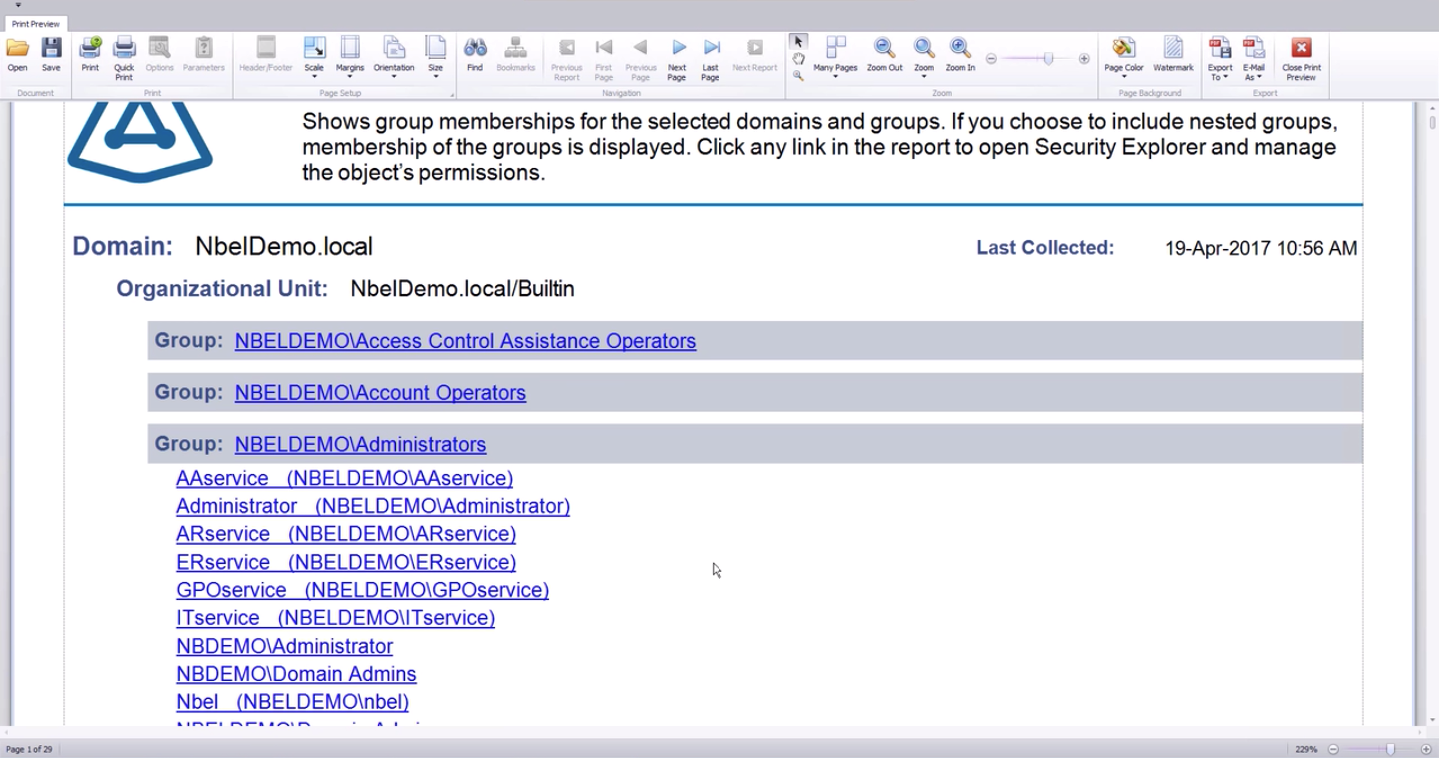
- Access to shared folders for an account or access to a folder of various accounts. These two related reports will allow us to identify situations from the history at the beginning of this article.
- Files older than N days, files created in the last 30 days, open files in the last 30 days.
- Delegated mailboxes and their properties.
- Access rights for accounts to the schema in the MSSQL database.
Directly from the link report, you can go to Security Explorer, through which typical actions are performed: adding to the AD group, assigning access rights to the folder, etc. This is how a specialized report looks.
Security Explorer module to determine which files a user has access to.
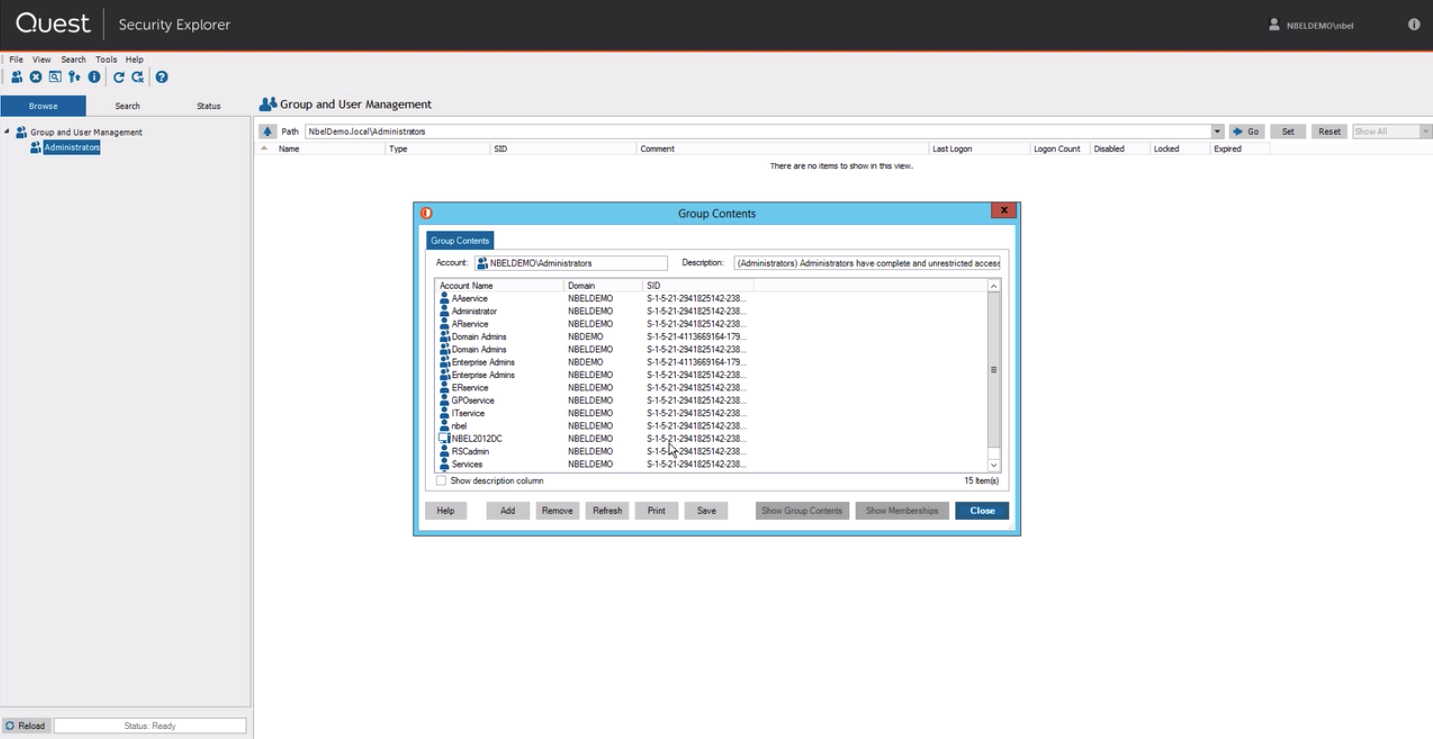
From the same interface, you can assign rights accurate to the file.

If your company has special requirements for the format of reports, you can easily insert a logo and make it up as needed.
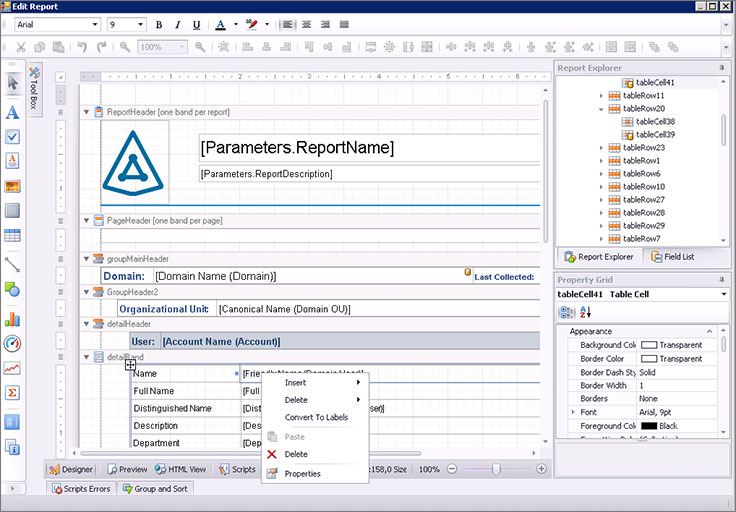
Fields in the report can also be arbitrary (from available).
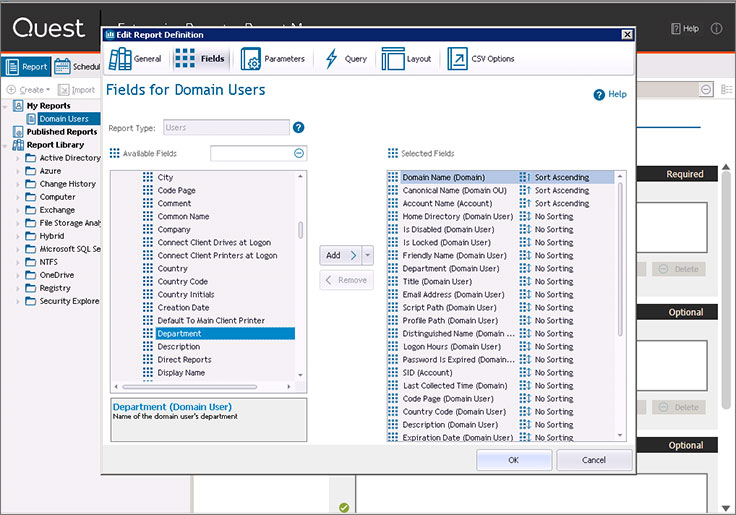
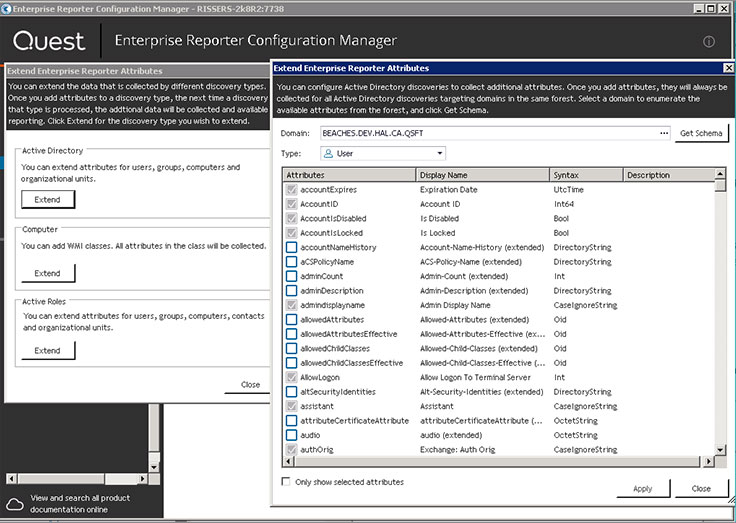
Unloading reports in various formats is available from the interface.
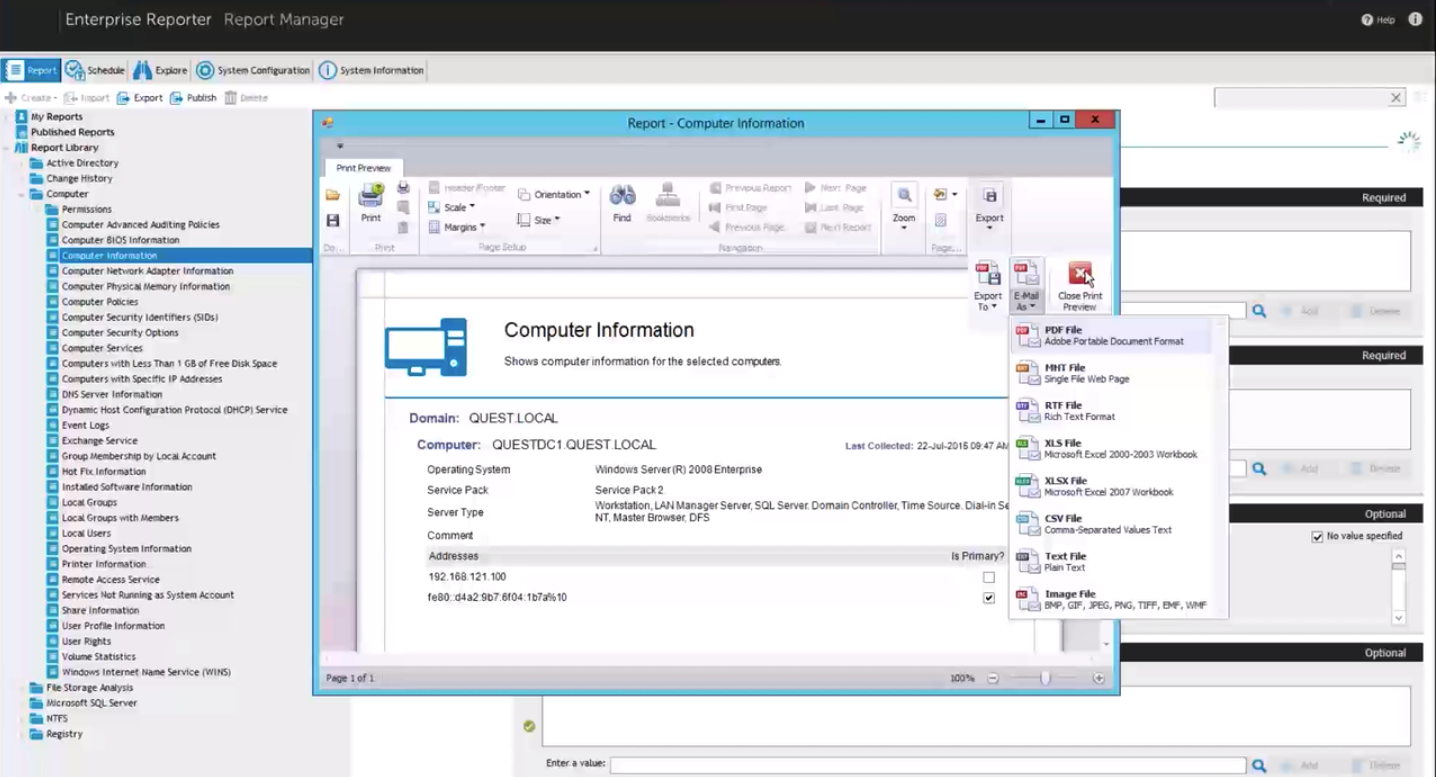
Quest Enterprise Reporter is a simple but functional solution that is installed and it works. This product is part of the Quest group of solutions for managing Microsoft infrastructure. We wrote about this in detail in the article on automation of information security audit . If you are interested in testing the product on your infrastructure or would like to learn more about the product - leave contacts and write briefly about the existing Microsoft infrastructure in the feedback form on our website .
All Articles