7 Key Active Directory Risk Indicators in Varonis Dashboard

All an attacker needs is time and motivation to penetrate your network. But our work with you is to prevent him from doing this, or at least to complicate this task as much as possible. You need to start by identifying weaknesses in Active Directory (hereinafter referred to as AD) that an attacker can use to gain access and move around the network, undetected. Today in this article we will look at risk indicators that reflect the existing vulnerabilities in the cyber defense of your organization, using the AD Varonis dashboard as an example.
Attackers use specific configurations in the domain
Attackers use many tricks and vulnerabilities to penetrate the corporate network and increase privileges. Some of these vulnerabilities are domain configuration parameters that can be easily changed after they are identified.
The AD dashboard will notify you immediately if you (or your system administrators) did not change the KRBTGT password last month, or if someone authenticated with the built-in default administrator account (Administrator). These two accounts provide unlimited access to your network: attackers will try to gain access to them in order to freely bypass any distinctions in privileges and access permissions. And, as a result, to get access to any data that interests them.
Of course, you can detect these vulnerabilities yourself: for example, set a reminder in the calendar for verification or run a PowerShell script to collect this information.
The Varonis dashboard is automatically updated to quickly view and analyze key metrics that highlight potential vulnerabilities so you can take immediate action.
3 key risk indicators at the domain level
Below are a number of widgets available on the Varonis dashboard, the use of which will significantly enhance the protection of the corporate network and IT infrastructure as a whole.
1. The number of domains for which the Kerberos account password has not changed significantly
The KRBTGT account is a special account in AD that signs all Kerberos tickets . Attackers who gain access to a domain controller (DC) can use this account to create a Golden ticket , which will give them unlimited access to almost any system on the corporate network. We were faced with a situation where, after successfully receiving the Golden Ticket, the attacker had access to the organization’s network for two years. If the password of the KRBTGT account in your company has not changed for the past forty days, the widget will notify you of this.
Forty days is more than enough time for an attacker to gain access to the network. However, if you provide and standardize the process of changing this password on a regular basis, this will greatly complicate the task for an attacker to penetrate the corporate network.
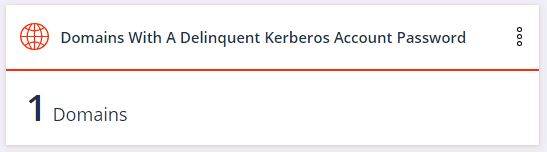
Remember that in accordance with the implementation of the Kerberos protocol by Microsoft, you need to change the KRBTGT password twice.
In the future, this AD widget will remind you when it is time to change the KRBTGT password again for all domains on your network.
2. Number of domains recently using the built-in Administrator account
According to the principle of least privileges , two accounts are provided to system administrators: the first is an account for everyday use, and the second is for planned administrative work. This means that no one should use the default administrator account.
A built-in administrator account is often used to simplify the system administration process. This can be a bad habit, resulting in a hack. If this happens in your organization, then it will be difficult for you to distinguish the proper use of this account from potentially malicious access.
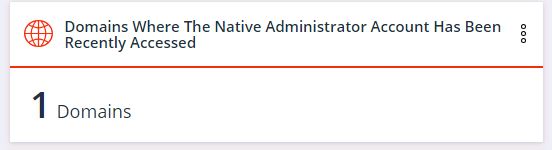
If the widget shows anything other than zero, it means that someone is not working correctly with administrative accounts. In this case, you must take measures to correct and restrict access to the built-in administrator account.
After you have reached the zero value of the widget and system administrators no longer use this account for their work, then in the future, any change in it will indicate a potential cyber attack.
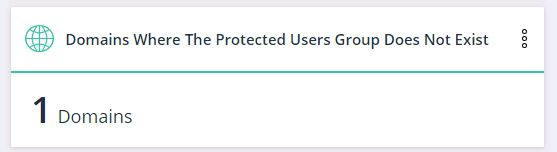
3. The number of domains in which there is no group of protected Users (Protected Users)
Old versions of AD supported a weak type of encryption - RC4. Hackers cracked RC4 many years ago, and now for an attacker to crack an account that still uses RC4 is a very trivial task. The version of Active Directory introduced in Windows Server 2012 introduced a group of users of a new type called the Protected Users Group. It provides additional security tools and prevents user authentication using RC4 encryption.
This widget will demonstrate if there is no such group in any domain of the organization so that you can fix it, i.e. enable a group of protected users, and use it to protect the infrastructure.
Light targets for attackers
User accounts are the number one target for attackers - from the first attempts to penetrate to the ongoing escalation of privileges and hiding their actions. Attackers look for simple targets on your network using basic PowerShell commands, which are often difficult to detect. Remove as many of these light targets from AD as possible.
Attackers look for users with unlimited passwords (or who do not need passwords), technology accounts that are administrators, and accounts that use old RC4 encryption.
Any of these accounts is either trivial to access, or, as a rule, is not monitored. Attackers can hijack these accounts and move seamlessly inside your infrastructure.
Once attackers penetrate the security perimeter, they are likely to gain access to at least one account. Can you stop them from gaining access to sensitive data before they detect and eliminate the attack?
The Varonis AD dashboard will point to vulnerable user accounts so that you can fix problems in advance. The more difficult it is to get inside your network, the higher your chances of neutralizing an attacker before he does serious damage.
4 key risk indicators for user accounts
The following are examples of widgets in the Varonis AD dashboard that indicate the most vulnerable user accounts.
1. The number of active users with passwords that never expire
For any attacker, access to such an account is always a great success. Since the password never expires, the attacker obtains a permanent foothold within the network, which can then be used to elevate privileges or move within the infrastructure.
Attackers have lists with millions of user-password combinations that they use in credential-substitution attacks, and the likelihood
that the combination for the user with the "eternal" password is in one of these lists, much more than zero.
Accounts with non-expiring passwords are easy to manage, but they are not secure. Use this widget to find all accounts that have these passwords. Change this setting and update the password.
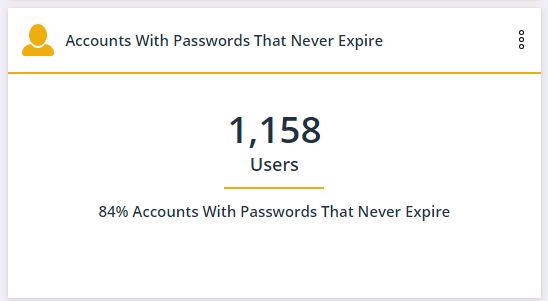
As soon as the value of this widget becomes zero, any new accounts created with this password will appear on the dashboard.
2. The number of administrative accounts with SPN
SPN (Service Principal Name) is a unique identifier for an instance of a service. This widget shows how many service accounts have full administrator rights. The value on the widget must be zero. An SPN with administrator rights occurs because granting such rights is convenient for software providers and application administrators, but this poses a security risk.
Giving a service account administrator privileges allows an attacker to gain full access to an account that is not used. This means that attackers with access to SPN accounts can freely act inside the infrastructure and at the same time avoid monitoring their actions.
You can fix this problem by changing the permissions for service accounts. Such accounts must obey the principle of least privilege and have only the access that is really necessary for their work.
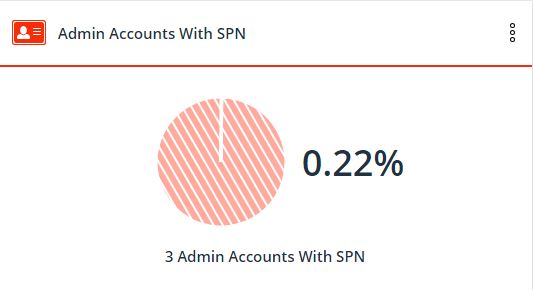
Using this widget, you can find all SPNs that have administrator rights, eliminate such privileges, and further control the SPN, guided by the same principle of access with the least privileges.
The newly appearing SPN will be displayed on the dashboard, and you can control this process.
3. Number of users who do not need Kerberos pre-authentication
Ideally, Kerberos encrypts an authentication ticket using AES-256 encryption, which remains unbroken to date.
However, older versions of Kerberos used RC4 encryption, which can now be cracked in minutes. This widget shows which user accounts still use RC4. Microsoft still supports RC4 for backward compatibility, but that doesn't mean you should use it in your AD.
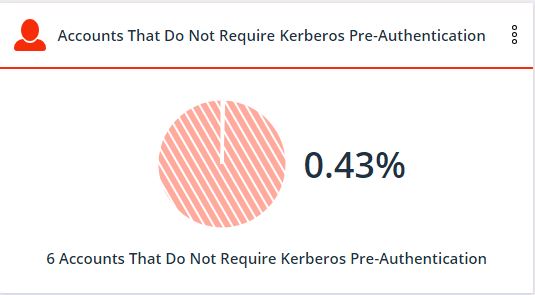
After you find such accounts, you need to clear the “do not require Kerberos pre-authorization” checkbox in AD so that the accounts use more complex encryption.
Self-discovery of these accounts, without the Varonis AD dashboard, is time consuming. In reality, being timely informed of all accounts that are edited to use RC4 encryption is an even more difficult task.
If the value on the widget changes, this may indicate illegal actions.
4. The number of users without a password
Attackers use the basic PowerShell commands to read the “PASSWD_NOTREQD” flag from the AD properties in the account properties. Using this flag means that there is no requirement for the presence or complexity of a password.
How easy is it to steal an account with a simple or blank password? Now imagine that one of these accounts is an administrator.
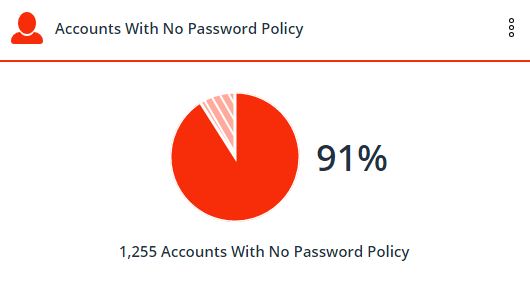
What if one of the thousands of confidential files open to everyone is an upcoming financial report?
Ignoring the mandatory password entry requirement is another shortcut to system administration, which has often been used in the past, but today it is unacceptable and unsafe.
Fix this problem by updating the passwords for these accounts.
Monitoring this widget in the future will help you avoid the appearance of accounts without a password.
Varonis equalizes the odds
In the past, the work of collecting and analyzing the metrics in the article took many hours and required in-depth knowledge of PowerShell: security specialists had to allocate resources for such tasks every week or month. But manual collection and processing of this information gives attackers a head start for penetration and data theft.
With Varonis, you will spend one day to deploy the AD dashboard and additional components, to collect all the considered and many other vulnerabilities. Later, during operation, the dashboard will be automatically updated as the state of the infrastructure changes.
Conducting cyber attacks is always a race between attackers and defenders, an attacker’s desire to steal data before security experts can block access to them. Early detection of cybercriminals and their illegal actions, combined with strong cyber defense, is the key to ensuring the security of your data.
All Articles