Training Cisco 200-125 CCNA v3.0. Day 19. Getting started with routers
Today's lesson is an introduction to Cisco routers. Before starting to study the material, I want to congratulate everyone who is watching my course, because almost a million people have watched the Day 1 video tutorial today. I thank all the users who contributed to the CCNA video course.
Today we will explore three topics: a router as a physical device, a small introduction to Cisco routers, and initial router setup. This slide shows what a typical Cisco Model 1921 router looks like.

Unlike a switch that has many ports, a typical router has only 2 ports for connection, in this case these are Gigabit Ethernet ports GE0 / 0 and GE / 1 and a USB connector. The router also has slots for expansion modules and 2 console ports, including 1 USB port. A distinctive feature of Cisco routers is the presence of a switch - Cisco switches do not have switches. Typically, the front of the router looks like the one shown at the bottom left of the slide. On the back of the router are jacks for connecting cables. In this case, the cable from the GE0 / 0 or GE / 1 slot is connected to the switch.
The bottom right shows the NME-X 23-ES-1GP expansion module, which can be inserted into the router by removing the dummy panels. Using these modules, you can expand the capabilities of a conventional Cisco router to meet your needs. As you know, due to its complexity and wide functionality, Cisco products are quite expensive, so the user has the opportunity not to overpay for a device with more features than he needs. Having bought a simple router for 2 ports, you can buy the necessary expansion modules as the network develops. In general, Cisco devices are capable of many functions. The routers were not invented by Cisco, but it was the routers that made Cisco the company that we know today. Cisco began mass production of routers with the highest quality, which ensured these products a leading position in the market of network devices.
Cisco calls itself a software company, that is, a software company. Hardware similar to Cisco hardware can be manufactured by any manufacturer, for example, China, by purchasing the appropriate hardware. But it is the Cisco IOS software that makes the devices of this company what they really are. The company is truly proud of this operating system, which runs on all Cisco devices - both switches and routers.
Cisco’s most important invention is CEF Enhanced, or Cisco Express Forwarding. It provides very fast packet transmission, almost at the maximum speed that the technical capabilities of the network allow. This is made possible thanks to Cisco ASIC's special-purpose integrated circuits - Application Specific Iintegrated Circuitry, which force the switch to transmit packets at almost network speed.
As I said, the router is more of a software device, so routing decisions are made by the Cisco IOS operating system.
You know that there are expensive graphics cards for computer games. So, if you do not have such a card, all the cumbersome calculations, 3D-animation and complex graphics processing are performed by your operating system, loading the computer processor. If you have a powerful graphics card with its own GPU processor and its own memory, the performance in games increases many times over, since the separate hardware deals with the graphic part.
The switch works in a similar way, because all decisions on packet switching are made by a separate hardware, without loading the router in which the software should make these decisions. Cisco uses CEF semi-software, semi-hardware technology, which forces the router to make faster routing decisions. This feature is unique to Cisco routers.
We have already considered how to perform the initial configuration of the switch parameters, and since the router is configured in the same way, I will tell you about it very quickly. I will open the Cisco Packet Tracer program and select the model 1921 router, then open the IOS console window in which you can see how the operating system of this router boots.
You see that we have downloaded version 15.1, this is the latest version of IOS, the memory capacity is 512 MB, the CISCO 2911 platform, then the other parameters of the operating system, the IOS image test are located, and of course, there is a license agreement and other similar things.
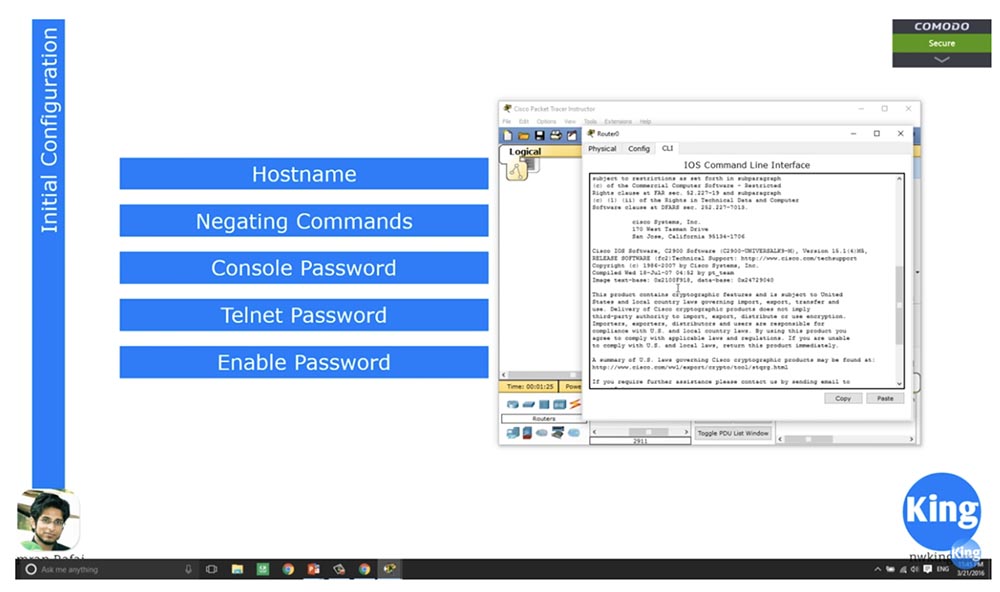
I will make a separate video devoted exclusively to Cisco IOS, or just talk about the various services of this operating system. I can only say that by the version number you can determine what features and functions this OS has. Starting from 15.1, all versions of iOS are universal, that is, depending on the license that the user acquires, he can take advantage of various functions of the system. For example, if you need to provide increased network security, you buy a security service license, if you need the voice service features - a voice service license, etc.
Prior to version 15.1, routers had OS with different versions - Basic, Security, Enterprise, Voice Enable, and so on. Suppose my friend’s router had an Enterprise IOS version, and I had a Basic IOS version, but there was nothing stopping me from taking a friend’s version and installing it on my router because Cisco did not use the OS license concept.
Starting from version 15.1, the company began to apply the concept of license options, and until you have purchased the corresponding key, you cannot use any additional service of the operating system. A little later, when we look at the licensing policy of Cisco, I will tell you about different versions of IOS. In the meantime, you can not pay any attention to this and go directly to the download log.
At the end of the log you see a description of the hardware on which the system was launched: processor brand, 3 gigabit interfaces, 64-bit DRAM, 256 Kb non-volatile memory. This amount of memory seems too small, but for a router that makes routing decisions, this is quite enough. This memory should not be compared with the memory of your computer, as these are completely different things.
The Cisco IOS boot log ends with the question: “Continue with the configuration dialog? Well no". If you answer “Yes”, the system will guide you through a series of questions, answering which you will perform the initial configuration of the device.
When learning a CCNA course, you should not do this, so always answer “No” to this question. Of course, you can choose the answer “Yes” and scroll through the configuration settings, but since you do not know how to perform it, it is better to choose the answer “No”.
Selecting “No” and pressing RETURN, we will move on to the prompts on the command line, where you can type various commands. As in the case of the switch, at the beginning we type the command Router> enable to switch to the privileged settings mode. Then I type config t (configure terminal) and get into global configuration mode.
Let's quickly go over the teams. I want to change the host name, so I use the hostname R1 command, then the negation commands follow, so I first ask you to show me the router interfaces using the do show ip interface brief command. We see that the Gigabit Ethernet port 0/0 is in administratively down mode, so I use the int gigabitEthernet 0/0 and no shutdown commands. After that, the state of the port changes to up. If you again look at the status of the router’s interfaces, you can see that now this port has the status “on”. The state of the protocol remains in the down position, because nothing is connected to our router, and in the absence of traffic, it is in the off state. But as soon as traffic arrives at the router port, the protocol will change the status to up.
Next, you need to set a password on the console. To do this, I print the commands line con 0, password console and do show run to make sure that the password for the console has been set. Password verification will be performed only after I enter the login command. Now the console port of the router is password protected.
I already told you about password encryption. Imagine that someone has accessed the current configuration of this device. Since the password is clearly visible in it, this person can easily steal it, so that at any time you can go into the settings of the router and hack the system.
One way to enable password encryption is to use the service password-encryption command. Since by default this command is used with the negation command no and has the form no service password-encryption, password encryption is not performed. Let's go into global configuration mode, type the service password-encryption command and press Enter. This command means that the system takes the text password that I set and encrypts it.
Now, if you look at the current configuration using the do show run command and go to the password line, you can see that the seventh type password took the form of a random sequence of digits. Now, if one of your colleagues can look over your shoulder and see this password, it will be very difficult for him to remember this sequence. Thus, we created the first line of defense of the access security system.

But even if he manages to copy this password, go into the settings and try to paste it into the password string, the system will not give access to the settings, because this set of numbers is not the password itself, but its encrypted value. The correct password is the word console, and when I enter it, I will get access to the console port. Thus, even if someone copies these numbers, they still will not be able to access the device.
However, in fact, we are mistaken, because all an attacker needs is to go to a site that makes it easy to decrypt Cisco passwords of the seventh type. Just go to the page of the site, enter the copied numbers, and you will get a decrypted password, in our case the word console. Now the hacker just needs to copy this word, return to the iOS settings and paste it into the password prompt.

In this case, the simple Enable Password function does not provide the necessary security. The best way to provide security is to use the enable secret cisco command. If after that we look at the current configuration, it can be seen that the password value now is a set of a variety of characters. In this case, the fifth type of Cisco password is used.
It is impossible to decrypt this type of password online, so now the console of your device is completely safe.
Next, you need to set a password on Telnet. To do this, I type the line vty 0 4 command, which will allow 5 people to use this router, and enter the password telnet command. Now, if someone wants to connect to the router using the Telnet protocol, he will need to enter this password - the word telnet.
Next, for the switch, we configured the Management IP IP address, because the switch belongs to OSI Level 2. However, the router is a level 3 device, and this means that each port on the router has its own IP address.
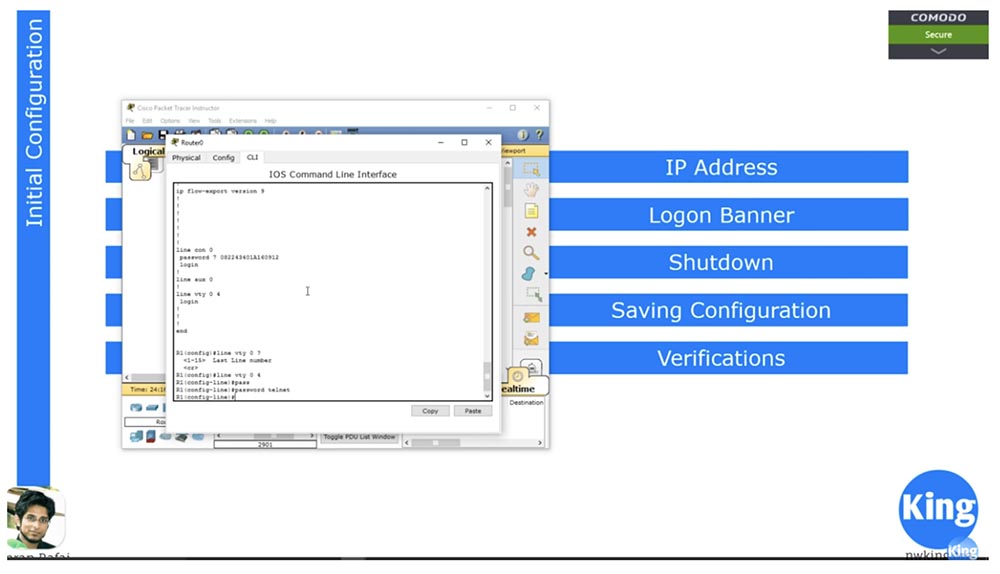
In the switch, we went to the settings of VLAN1 or to the settings of any other network in which it was necessary to register an IP address. We created virtual interfaces and assigned them IP addresses. But in the case of a router, these addresses must be assigned to physical ports, so I enter the config t and int g0 / 0 commands. Next, I use the command to assign an IP address in the same way as I did in the case of VLAN, that is, I enter the ip address 10.1.1.1 255.255.255.0 command and then type no shutdown.
If we now look at the state of the ports using the do show int brief command, we see that the address 10.1.1.1 is assigned to the Gigabit Ethernet 0/0 interface. So we configured the IP address.
Next, we move on to setting up the Logon Banner. In the same way as for the switch, I use the banner motd & command and then I can enter any text I want, for example, Welcome to NetworKing Router, underline the text with “asterisks” and close it with ampersand &.
Further, if you want to disable the port, then use the Shutdown command. To save the settings, use the copy running-config startup-config command. The current configuration can be viewed using the show running conf command, and the show startup conf command is used to view the boot configuration. Since we used the new device “out of the box” and the boot with the default settings, in response to a request to show the boot configuration, the system replies that it does not exist yet.
After entering the copy running-config startup-config command, the system asks to confirm that the rewritable file is the startup-config boot parameters file. After overwriting the boot configuration file, I look through it with the show startup conf command and see that now it completely repeats the file of the current state of the device. Now, if I turn off the router and turn it on again, it will boot using the saved settings.
Router status verification is best done using the show int brief command; you can also use the show int command, which will show the status of all ports. If you want to look at the status of a specific port, you can use the show interface g0 / 0 command, after which the system will show full statistics on this interface.
As I said, the most important part of the router is the routing table. You can view it using the show ip route command.
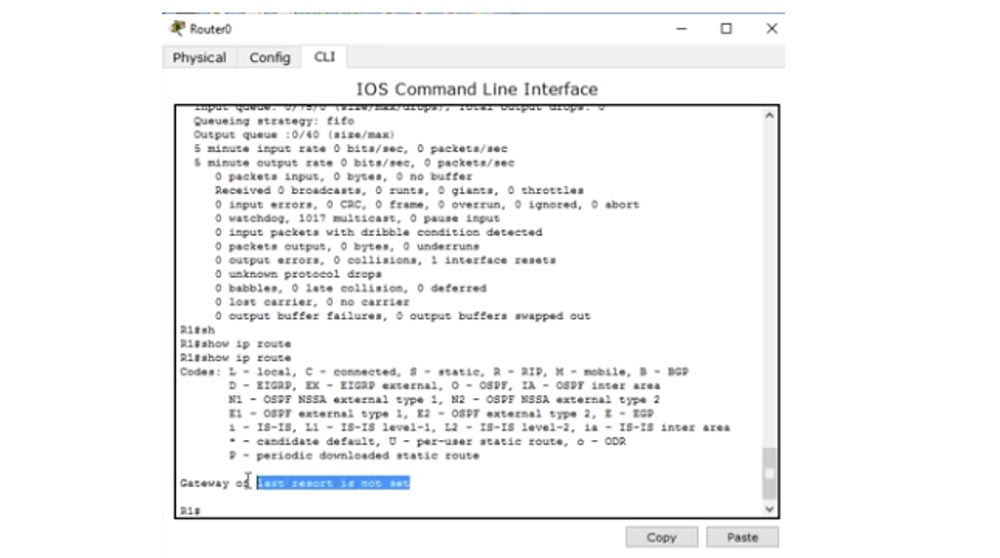
At the moment, the table is empty, because no devices are connected to our router. In the next video tutorial, we will look at how a routing table is created using various protocols, how it is populated when new devices are connected using static routing or dynamic protocols. In the world of routers, the show ip route command is the most popular because usually all routing problems start with a routing table.
This is where I finish our video tutorial, as I talked about everything that was planned for today. Many users ask what my interest is when I record and post these video tutorials. I do this in my free time for free. Of course, you can send me money if you want. Many sites use my video tutorials and ask for money for it, but I don’t want to do this with my students and promise that my lessons will never be paid.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
Today we will explore three topics: a router as a physical device, a small introduction to Cisco routers, and initial router setup. This slide shows what a typical Cisco Model 1921 router looks like.

Unlike a switch that has many ports, a typical router has only 2 ports for connection, in this case these are Gigabit Ethernet ports GE0 / 0 and GE / 1 and a USB connector. The router also has slots for expansion modules and 2 console ports, including 1 USB port. A distinctive feature of Cisco routers is the presence of a switch - Cisco switches do not have switches. Typically, the front of the router looks like the one shown at the bottom left of the slide. On the back of the router are jacks for connecting cables. In this case, the cable from the GE0 / 0 or GE / 1 slot is connected to the switch.
The bottom right shows the NME-X 23-ES-1GP expansion module, which can be inserted into the router by removing the dummy panels. Using these modules, you can expand the capabilities of a conventional Cisco router to meet your needs. As you know, due to its complexity and wide functionality, Cisco products are quite expensive, so the user has the opportunity not to overpay for a device with more features than he needs. Having bought a simple router for 2 ports, you can buy the necessary expansion modules as the network develops. In general, Cisco devices are capable of many functions. The routers were not invented by Cisco, but it was the routers that made Cisco the company that we know today. Cisco began mass production of routers with the highest quality, which ensured these products a leading position in the market of network devices.
Cisco calls itself a software company, that is, a software company. Hardware similar to Cisco hardware can be manufactured by any manufacturer, for example, China, by purchasing the appropriate hardware. But it is the Cisco IOS software that makes the devices of this company what they really are. The company is truly proud of this operating system, which runs on all Cisco devices - both switches and routers.
Cisco’s most important invention is CEF Enhanced, or Cisco Express Forwarding. It provides very fast packet transmission, almost at the maximum speed that the technical capabilities of the network allow. This is made possible thanks to Cisco ASIC's special-purpose integrated circuits - Application Specific Iintegrated Circuitry, which force the switch to transmit packets at almost network speed.
As I said, the router is more of a software device, so routing decisions are made by the Cisco IOS operating system.
You know that there are expensive graphics cards for computer games. So, if you do not have such a card, all the cumbersome calculations, 3D-animation and complex graphics processing are performed by your operating system, loading the computer processor. If you have a powerful graphics card with its own GPU processor and its own memory, the performance in games increases many times over, since the separate hardware deals with the graphic part.
The switch works in a similar way, because all decisions on packet switching are made by a separate hardware, without loading the router in which the software should make these decisions. Cisco uses CEF semi-software, semi-hardware technology, which forces the router to make faster routing decisions. This feature is unique to Cisco routers.
We have already considered how to perform the initial configuration of the switch parameters, and since the router is configured in the same way, I will tell you about it very quickly. I will open the Cisco Packet Tracer program and select the model 1921 router, then open the IOS console window in which you can see how the operating system of this router boots.
You see that we have downloaded version 15.1, this is the latest version of IOS, the memory capacity is 512 MB, the CISCO 2911 platform, then the other parameters of the operating system, the IOS image test are located, and of course, there is a license agreement and other similar things.

I will make a separate video devoted exclusively to Cisco IOS, or just talk about the various services of this operating system. I can only say that by the version number you can determine what features and functions this OS has. Starting from 15.1, all versions of iOS are universal, that is, depending on the license that the user acquires, he can take advantage of various functions of the system. For example, if you need to provide increased network security, you buy a security service license, if you need the voice service features - a voice service license, etc.
Prior to version 15.1, routers had OS with different versions - Basic, Security, Enterprise, Voice Enable, and so on. Suppose my friend’s router had an Enterprise IOS version, and I had a Basic IOS version, but there was nothing stopping me from taking a friend’s version and installing it on my router because Cisco did not use the OS license concept.
Starting from version 15.1, the company began to apply the concept of license options, and until you have purchased the corresponding key, you cannot use any additional service of the operating system. A little later, when we look at the licensing policy of Cisco, I will tell you about different versions of IOS. In the meantime, you can not pay any attention to this and go directly to the download log.
At the end of the log you see a description of the hardware on which the system was launched: processor brand, 3 gigabit interfaces, 64-bit DRAM, 256 Kb non-volatile memory. This amount of memory seems too small, but for a router that makes routing decisions, this is quite enough. This memory should not be compared with the memory of your computer, as these are completely different things.
The Cisco IOS boot log ends with the question: “Continue with the configuration dialog? Well no". If you answer “Yes”, the system will guide you through a series of questions, answering which you will perform the initial configuration of the device.
When learning a CCNA course, you should not do this, so always answer “No” to this question. Of course, you can choose the answer “Yes” and scroll through the configuration settings, but since you do not know how to perform it, it is better to choose the answer “No”.
Selecting “No” and pressing RETURN, we will move on to the prompts on the command line, where you can type various commands. As in the case of the switch, at the beginning we type the command Router> enable to switch to the privileged settings mode. Then I type config t (configure terminal) and get into global configuration mode.
Let's quickly go over the teams. I want to change the host name, so I use the hostname R1 command, then the negation commands follow, so I first ask you to show me the router interfaces using the do show ip interface brief command. We see that the Gigabit Ethernet port 0/0 is in administratively down mode, so I use the int gigabitEthernet 0/0 and no shutdown commands. After that, the state of the port changes to up. If you again look at the status of the router’s interfaces, you can see that now this port has the status “on”. The state of the protocol remains in the down position, because nothing is connected to our router, and in the absence of traffic, it is in the off state. But as soon as traffic arrives at the router port, the protocol will change the status to up.
Next, you need to set a password on the console. To do this, I print the commands line con 0, password console and do show run to make sure that the password for the console has been set. Password verification will be performed only after I enter the login command. Now the console port of the router is password protected.
I already told you about password encryption. Imagine that someone has accessed the current configuration of this device. Since the password is clearly visible in it, this person can easily steal it, so that at any time you can go into the settings of the router and hack the system.
One way to enable password encryption is to use the service password-encryption command. Since by default this command is used with the negation command no and has the form no service password-encryption, password encryption is not performed. Let's go into global configuration mode, type the service password-encryption command and press Enter. This command means that the system takes the text password that I set and encrypts it.
Now, if you look at the current configuration using the do show run command and go to the password line, you can see that the seventh type password took the form of a random sequence of digits. Now, if one of your colleagues can look over your shoulder and see this password, it will be very difficult for him to remember this sequence. Thus, we created the first line of defense of the access security system.

But even if he manages to copy this password, go into the settings and try to paste it into the password string, the system will not give access to the settings, because this set of numbers is not the password itself, but its encrypted value. The correct password is the word console, and when I enter it, I will get access to the console port. Thus, even if someone copies these numbers, they still will not be able to access the device.
However, in fact, we are mistaken, because all an attacker needs is to go to a site that makes it easy to decrypt Cisco passwords of the seventh type. Just go to the page of the site, enter the copied numbers, and you will get a decrypted password, in our case the word console. Now the hacker just needs to copy this word, return to the iOS settings and paste it into the password prompt.

In this case, the simple Enable Password function does not provide the necessary security. The best way to provide security is to use the enable secret cisco command. If after that we look at the current configuration, it can be seen that the password value now is a set of a variety of characters. In this case, the fifth type of Cisco password is used.
It is impossible to decrypt this type of password online, so now the console of your device is completely safe.
Next, you need to set a password on Telnet. To do this, I type the line vty 0 4 command, which will allow 5 people to use this router, and enter the password telnet command. Now, if someone wants to connect to the router using the Telnet protocol, he will need to enter this password - the word telnet.
Next, for the switch, we configured the Management IP IP address, because the switch belongs to OSI Level 2. However, the router is a level 3 device, and this means that each port on the router has its own IP address.

In the switch, we went to the settings of VLAN1 or to the settings of any other network in which it was necessary to register an IP address. We created virtual interfaces and assigned them IP addresses. But in the case of a router, these addresses must be assigned to physical ports, so I enter the config t and int g0 / 0 commands. Next, I use the command to assign an IP address in the same way as I did in the case of VLAN, that is, I enter the ip address 10.1.1.1 255.255.255.0 command and then type no shutdown.
If we now look at the state of the ports using the do show int brief command, we see that the address 10.1.1.1 is assigned to the Gigabit Ethernet 0/0 interface. So we configured the IP address.
Next, we move on to setting up the Logon Banner. In the same way as for the switch, I use the banner motd & command and then I can enter any text I want, for example, Welcome to NetworKing Router, underline the text with “asterisks” and close it with ampersand &.
Further, if you want to disable the port, then use the Shutdown command. To save the settings, use the copy running-config startup-config command. The current configuration can be viewed using the show running conf command, and the show startup conf command is used to view the boot configuration. Since we used the new device “out of the box” and the boot with the default settings, in response to a request to show the boot configuration, the system replies that it does not exist yet.
After entering the copy running-config startup-config command, the system asks to confirm that the rewritable file is the startup-config boot parameters file. After overwriting the boot configuration file, I look through it with the show startup conf command and see that now it completely repeats the file of the current state of the device. Now, if I turn off the router and turn it on again, it will boot using the saved settings.
Router status verification is best done using the show int brief command; you can also use the show int command, which will show the status of all ports. If you want to look at the status of a specific port, you can use the show interface g0 / 0 command, after which the system will show full statistics on this interface.
As I said, the most important part of the router is the routing table. You can view it using the show ip route command.

At the moment, the table is empty, because no devices are connected to our router. In the next video tutorial, we will look at how a routing table is created using various protocols, how it is populated when new devices are connected using static routing or dynamic protocols. In the world of routers, the show ip route command is the most popular because usually all routing problems start with a routing table.
This is where I finish our video tutorial, as I talked about everything that was planned for today. Many users ask what my interest is when I record and post these video tutorials. I do this in my free time for free. Of course, you can send me money if you want. Many sites use my video tutorials and ask for money for it, but I don’t want to do this with my students and promise that my lessons will never be paid.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
All Articles