Our service is both dangerous and difficult, or Zyxel ATP500
Introduction
We wrote, we wrote, our fingers are tired. Why did we suddenly decide to start with this children's couplet? Everything is very simple. In this article, we wanted to introduce readers to the capabilities of our most advanced network security solution - the Zyxel ATP line of firewalls. As an example, the middle model of the line was chosen - ATP500. Based on it, we planned not only to make a high-quality description of the functionality of the entire line of firewalls, but also to share test results by measuring the performance of the device when performing most typical user filtering operations. Having looked at the volume of the resulting material, we decided to divide the text into two or even three articles: today we will describe the main security features, as well as get acquainted with the device settings, and postpone all measurements and design until the next publications.
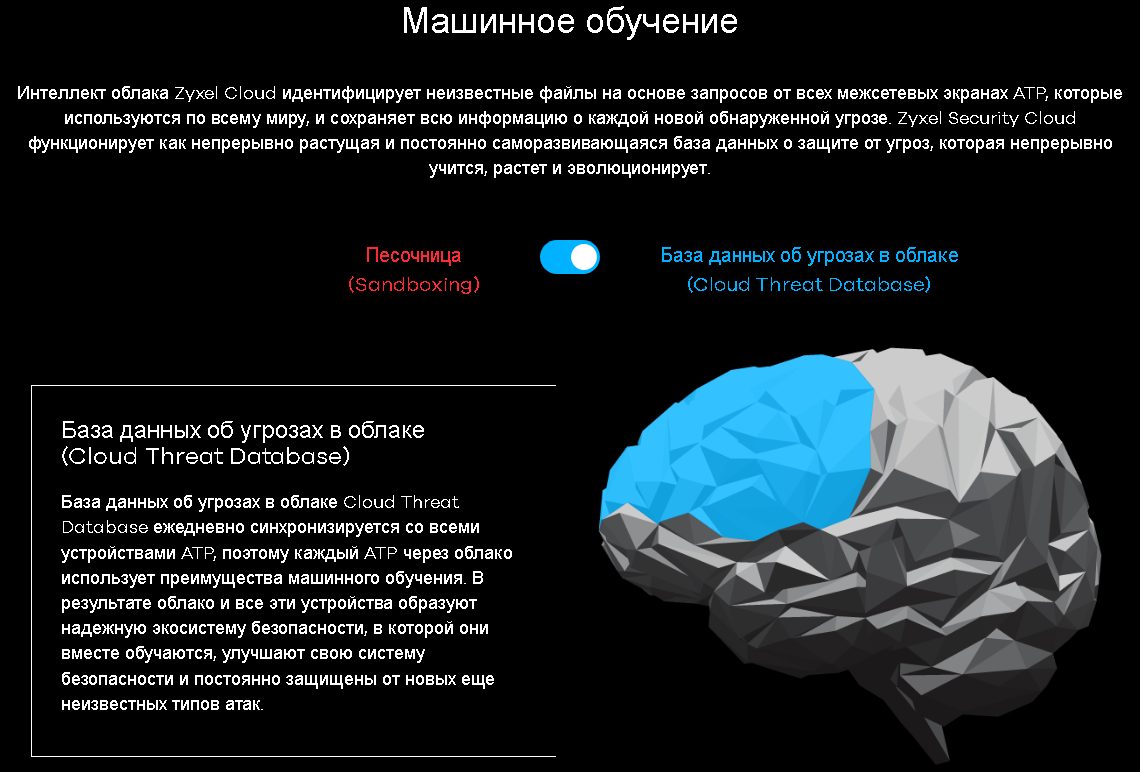
The volume of material is related to the number of multilevel protection features that Zyxel firewalls offer: sandboxed code execution, machine learning, the use of a cloud of current threats, an intrusion prevention system, a security system for applications and the web, and much more -much more.

So let's get started!
Update
Before starting a discussion of issues related to the functionality of the device, we would like to once again remind readers of the need to timely update not only the anti-virus signature databases, but also the firmware of the device itself. For security devices, this is extremely important, since new versions of firmware not only fix potential vulnerabilities in the firmware code, but also expand the functionality and increase the number and quality of user traffic checks. The firmware version is changed using the “Firmware Management” tab of the “File Manager” item of the “SERVICE” menu.
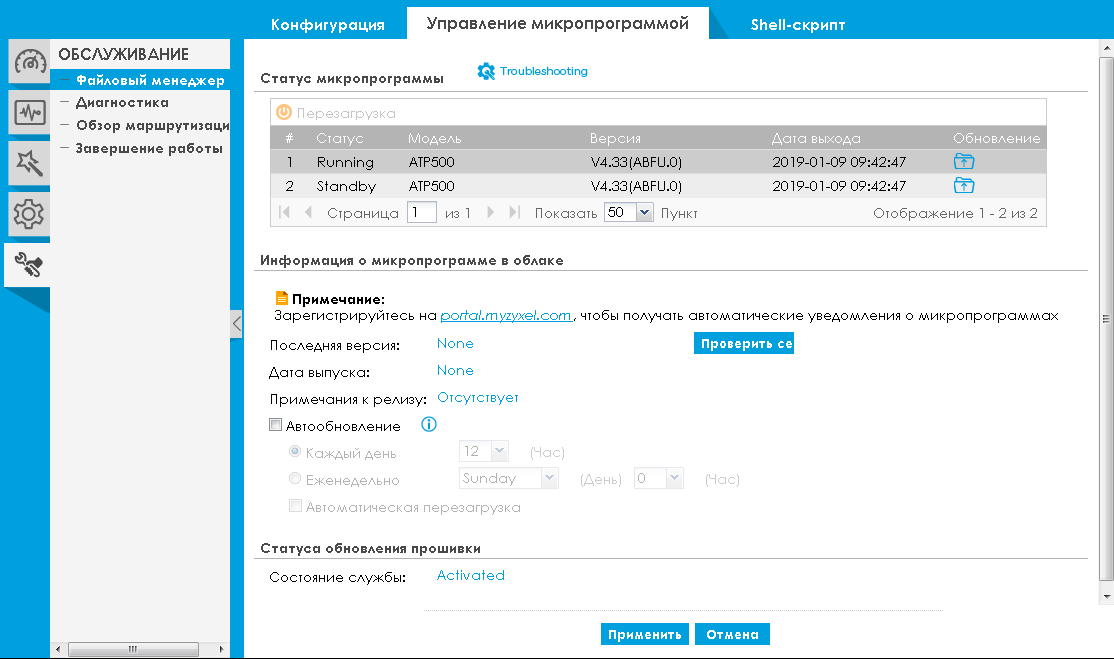
There are two firmware on the device at once: the current and the backup. If problems arise during the firmware update, the administrator can easily return to the previous (obviously working) version of the firmware. We did not invent a wheel here, two firmwares - a standard approach for most devices of this level.
The update itself can be done manually, semi-automatically and fully automatically. Each administrator can choose the update mode that suits him best. For example, the firewalls of remote offices can be updated automatically according to the schedule during the hours of the least load on the network (for example, at night or on weekends), while for updating firewalls in critical network segments you can resort to the manual method of replacing the firmware.
During the firmware upgrade process, the device needs to reboot. This is a very standard way to replace microcode. During a reboot, it is obvious that the firewall cannot forward user traffic. Does this mean that during the reboot users will be left without access to the network? When using a single firewall, yes, the duration of the service outage will approximately correspond to the ATP reboot time. Obviously, the time required to reboot the device depends on many factors, such as the version of the operating system, the number of services included, the hardware platform, and so on. We measured the boot time of the ATP500 model with the default configuration and the latest firmware version at the time of writing.
The load time was 138 seconds, that is, approximately two and a quarter minutes. All-all, as we promised at the beginning, there are no more measurements in this article!
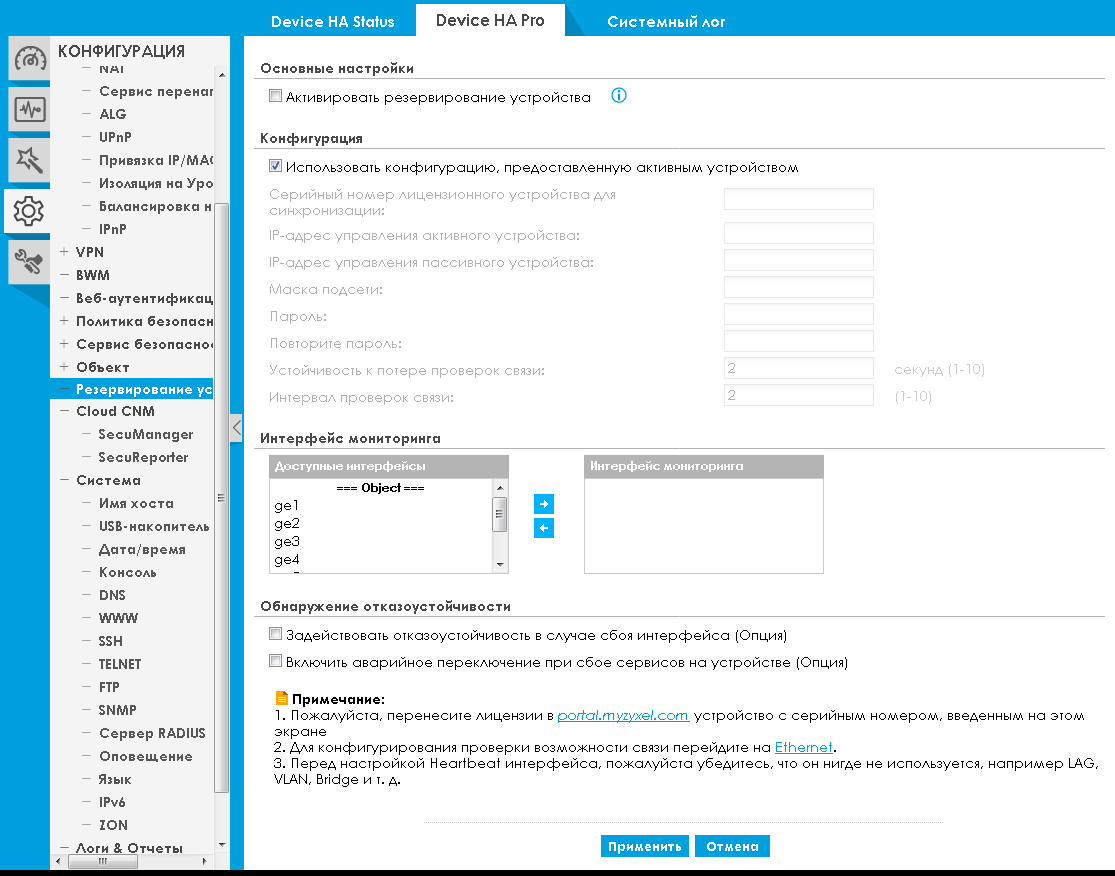
It is worth noting that if the network is built using high availability tools, then the service interruption will be much shorter. The corresponding settings are available in the “Device backup” item of the “CONFIGURATION” menu.
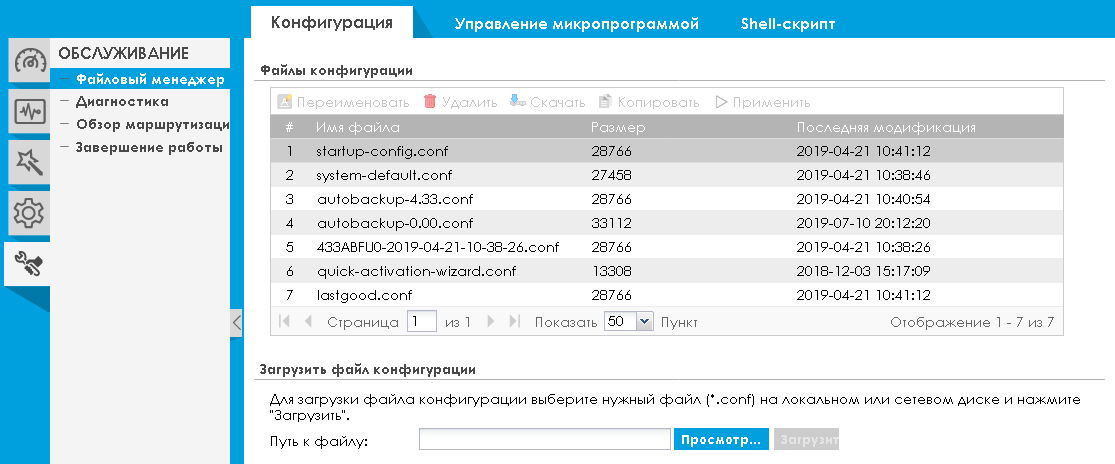
Zyxel ATP series firewalls support not only two copies of the firmware, but also several configuration files. Yes, of course, this does not apply directly to the procedure for updating firmware and signatures, but we cannot but say so. The administrator can always roll back to the previous version of the settings.
For the functioning of a number of services, such as anti-virus scanning, application monitoring, a filter of botnet networks and intrusion prevention systems, it is necessary to have up-to-date signature databases containing information about malware. You can perform a semi-automatic update or set a schedule for automatic updating using the “Signature Update” item in the “Licensing” group of the “CONFIGURATION” menu.

In conclusion of this section, we would like to draw the attention of readers to the item “Date / Time” of the “System” group of the “CONFIGURATION” menu. Using this item, the administrator can set the time synchronization parameters. It is difficult to overestimate the importance of such synchronization. And here we are not talking about the convenience of working with journal information (logs). Firstly, the date and time is used in all schedules configured on the device.
We believe that no administrator would like to unexpectedly reboot the device in the middle of the day due to a firmware update for the firewall. But what can be even more important is checking the time of validity of HTTPS certificates of those servers accessed by users from the protected network.

We now turn to the consideration of specific network security features.
Anomalies
Zyxel ATP series firewalls allow you to detect anomalies in the transmitted data and block such traffic. But what kind of anomalies can ATP detect ?! Here are just a few examples. Perhaps, any network administrator will agree that port scanning of a certain node cannot be attributed to typical traffic, of course, with rare exceptions. The appearance of a variety of spurious (flood) traffic also belongs to this type of anomaly. Each network and transport (TCP / UDP / ICMP) protocols has its own set of anomalies. So, for example, among the anomalies of the IP protocol, fragment overlap can be noted, and for TCP there are reserved (unused) values for the Header Length field - the minimum value of this field is 5.
You can enable or disable checking traffic from a specific security zone for anomalies using the “Basic Settings” tab of the “ADP” item of the “Security Policy” group of the “CONFIGURATION” menu. Here, the anomaly detection profile is linked to the zone.
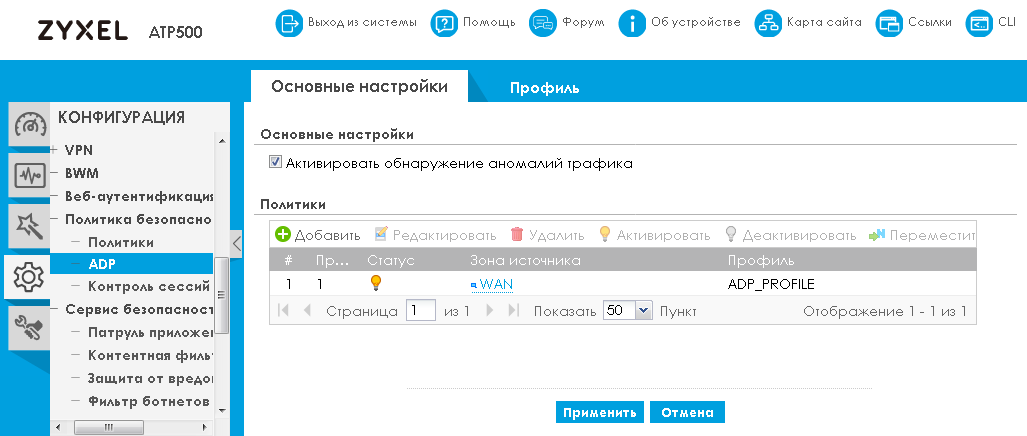
The profiles themselves are managed on the “Profile” tab of the same menu item.
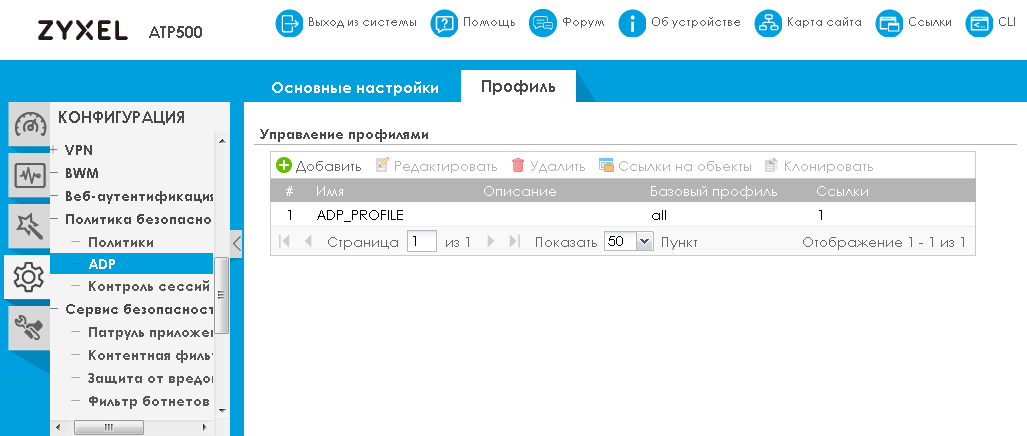
For each of the profiles, you can choose which traffic anomalies to detect, as well as what actions to take after detection.
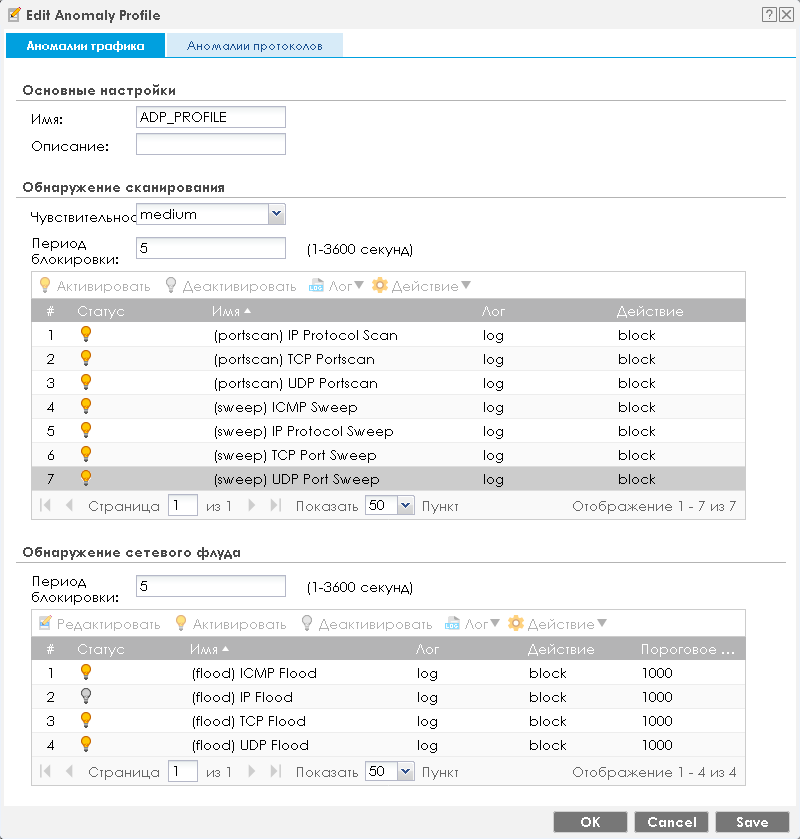

From finding the simplest anomalies, let's move on to a more in-depth study of traffic.
Politicians
The Policies item of the Security Policy group of the CONFIGURATION menu provides administrators with the ability to manage traffic filtering policies that apply to user data passing through the firewall.

It should be noted that there is support for asymmetric routes. Such support may be in demand for large and complex networks. However, the quite standard recommendation is applicable here that asymmetric routing should be avoided whenever possible.
To apply the policy, traffic can be selected according to the following criteria: zones of the sender and recipient of data, IP addresses of the sender and recipient, schedule, authenticated user, as well as traffic of a certain service. You can create multiple policies at the same time. Checking traffic for compliance with the terms of the policy is applied sequentially. The first matching policy is applied.
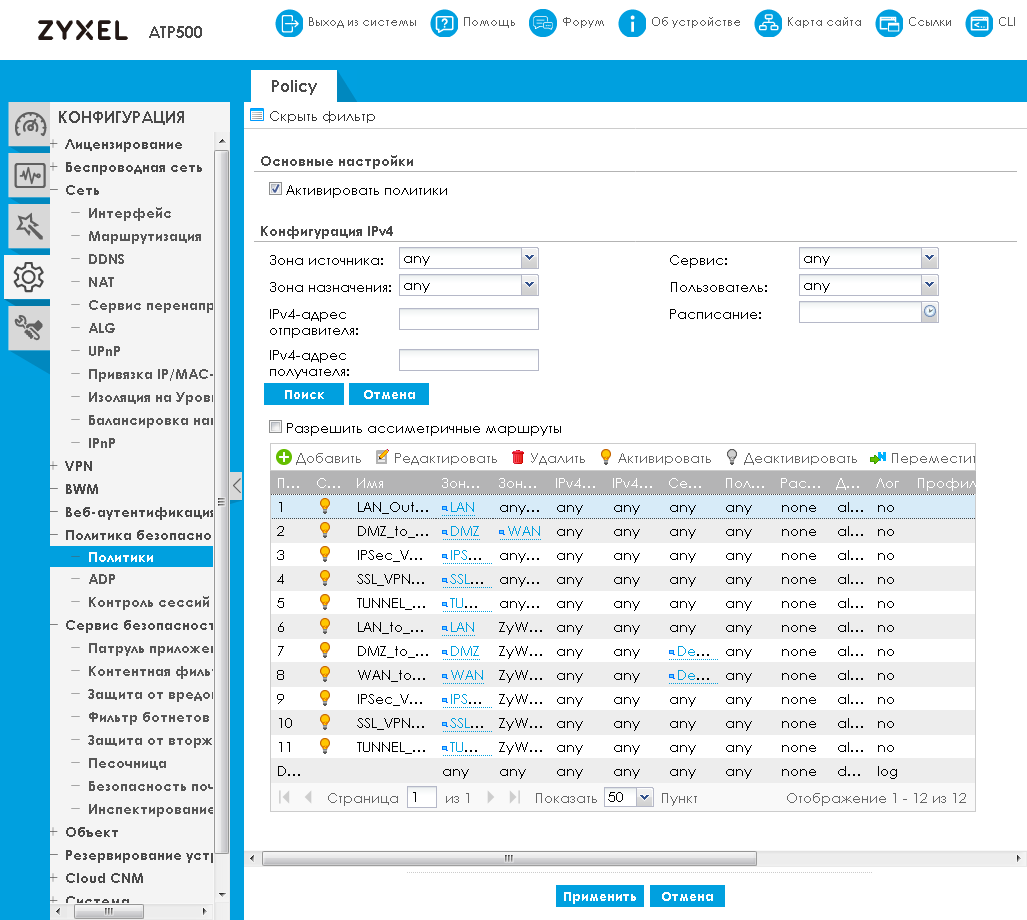
Traffic that is subject to a specific processing policy can be transferred to the following mechanisms for processing: application patrol, content filtering and SSL inspection. In more detail about each of the listed mechanisms we will tell further.
Session Control
The ability to limit the number of sessions, of course, is not directly related to protecting the network from infections by various malware. However, it can be useful in case of excessive load on the firewall, for example, when a DDoS attack occurs. In general, the sharply increased number of simultaneous open connections from one or several hosts (baseline relative to the initial level) may indirectly indicate the appearance of a new dangerous code in the active phase. Limiting the number of allowed sessions will slightly reduce the rate of spread of the infection, for example, if the device has become part of the botnet network; or reduce her damage.
General restrictions are configured in the “Session Control” item of the “Security Policy” group of the “CONFIGURATION” menu. For IPv4 and IPv6 traffic restrictions are imposed independently.
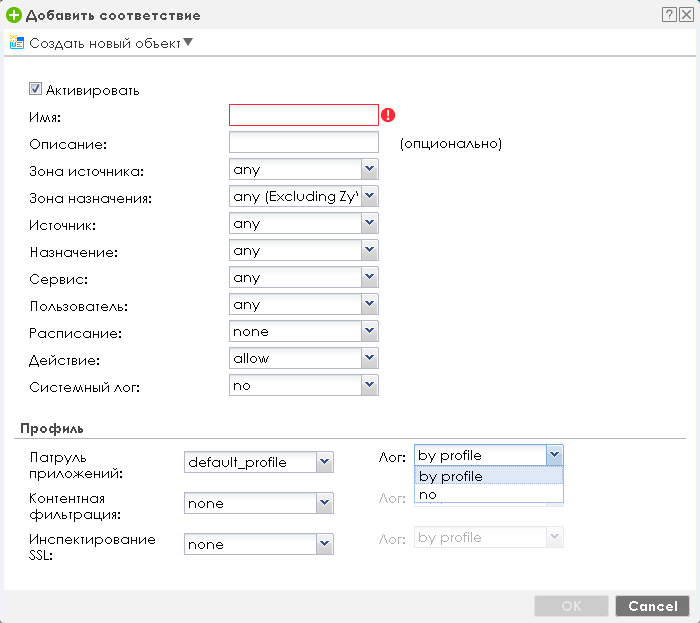
The maximum number of sessions can be set individually for each user or device with a specific IP address.
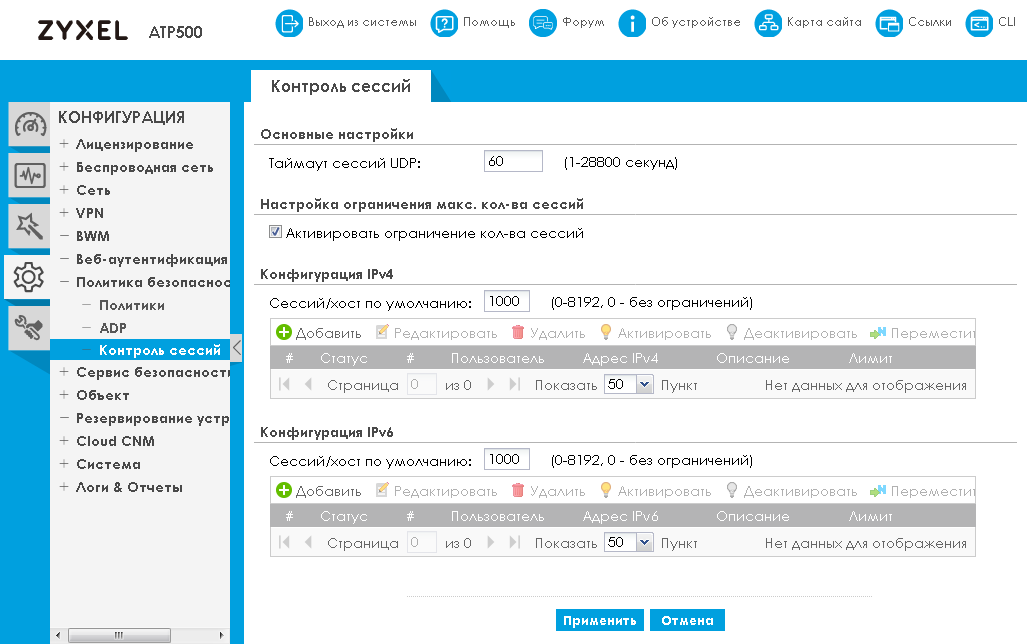
And although limiting the maximum number of active sessions can have a positive effect on the whole situation with an infection or an attack as a whole, we would recommend using specialized tools for each specific case.
Application Patrol
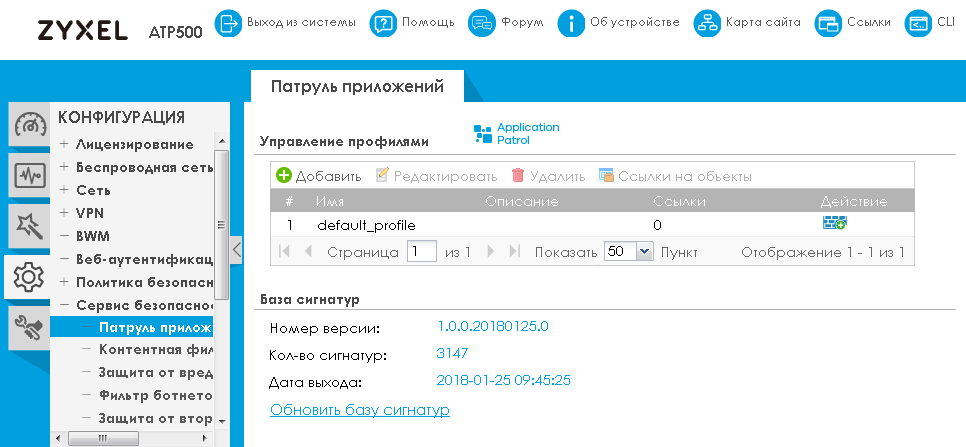
The signature database of this service contains information about several thousand diverse applications and online services. Moreover, the application signature database is regularly updated, giving the administrator the ability to filter traffic for an increasing number of services.
Traffic control of well-known applications is performed by configuring the corresponding profiles in the “Application patrol” item of the “Security Service” group of the “CONFIGURATION” menu.

Each profile contains a list of applications and the actions that need to be performed on it. Perhaps it’s worth explaining the difference between the drop and reject actions. If you select the drop option, packets will be discarded without sending any notification, while the reject option will also send a message about dropping packets.
Now consider the possibilities of content filtering.
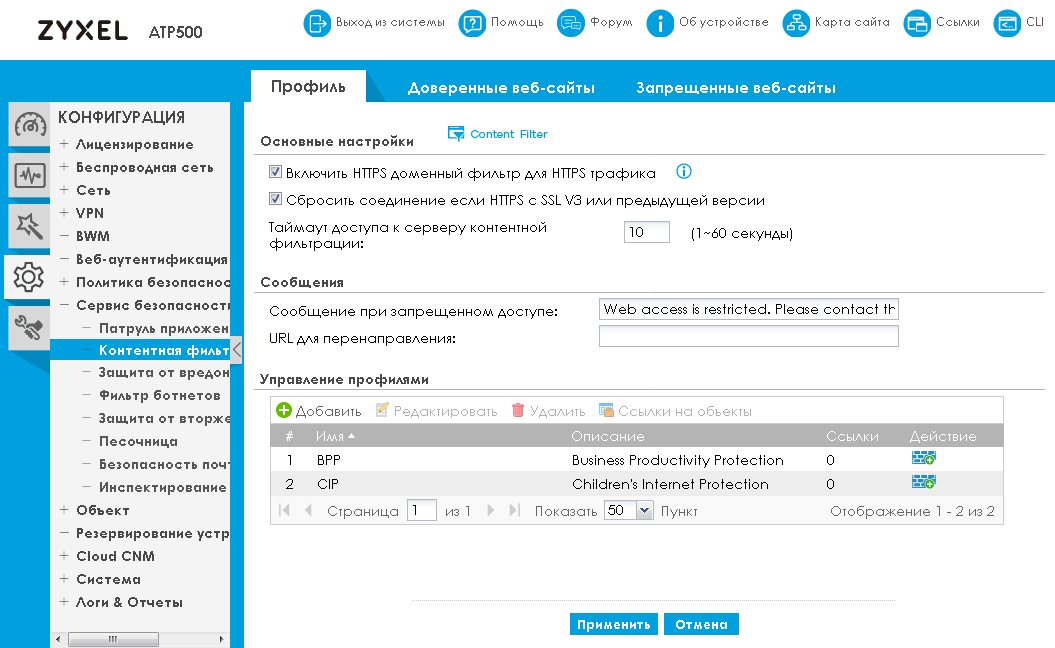
Content filtering
Content filtering allows the administrator to control access to certain websites or to resources containing certain data. Content filtering policies can be time-bound, which is why it’s even more important to pre-configure time synchronization with NTP servers. The schedule for applying policies allows you to block employee access to certain resources (for example, social networks) during working hours and vice versa to allow it after the end of a business day, or during lunch.
Of course, different employees require access to different types of information. For example, human resources employees must have access to the same social networks all the time, since they use these websites to carry out their immediate duties.
Content filtering is configured on the page of the same group "Security Service" of the "CONFIGURATION" menu.

When creating or modifying a content filtering profile, you can immediately check which categories a particular resource belongs to.
It is worth noting that the filtering profile not only determines the sites to which users are allowed or blocked access, but also allows which elements of web pages are allowed (Active X, Java, Cookies, web proxies). In addition, access blocking can be done by keywords.
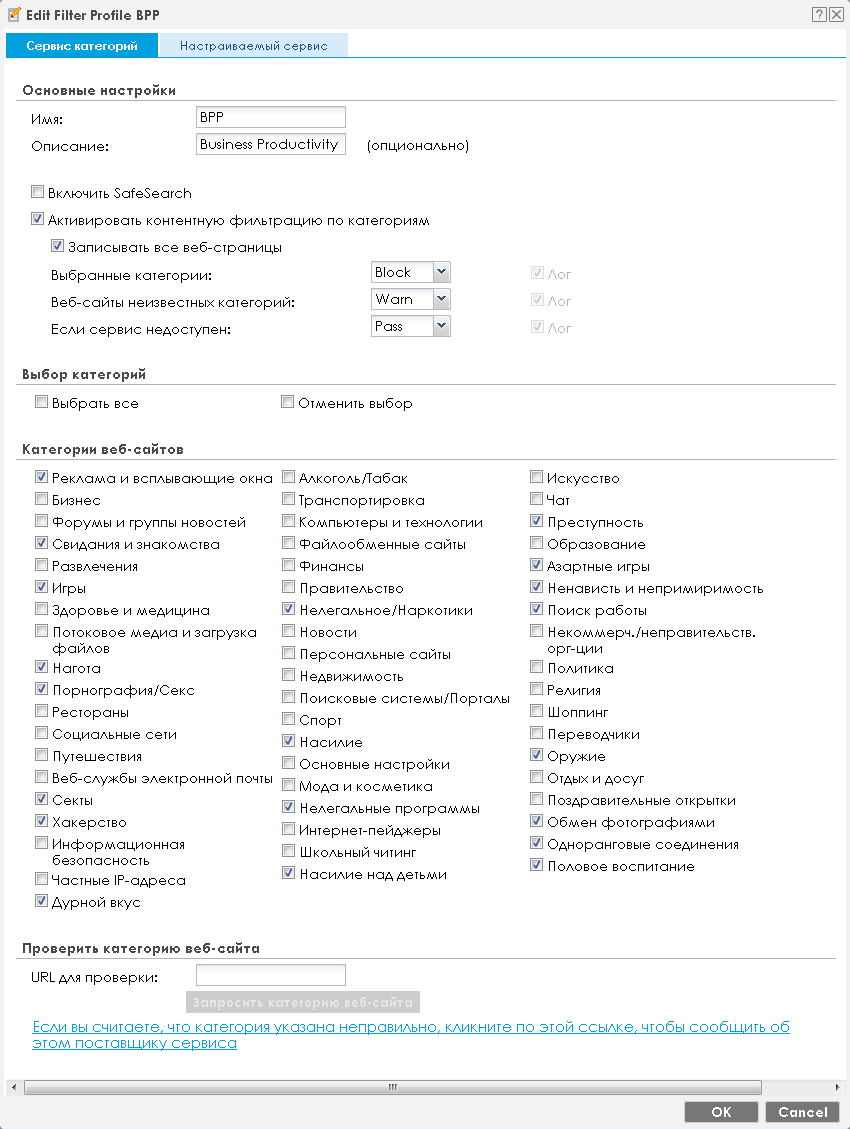
Naturally, the administrator has the ability to explicitly allow or deny access to certain resources, regardless of what category they belong to. The corresponding setting is available on the Trusted Web Sites and Prohibited Web Sites tabs.
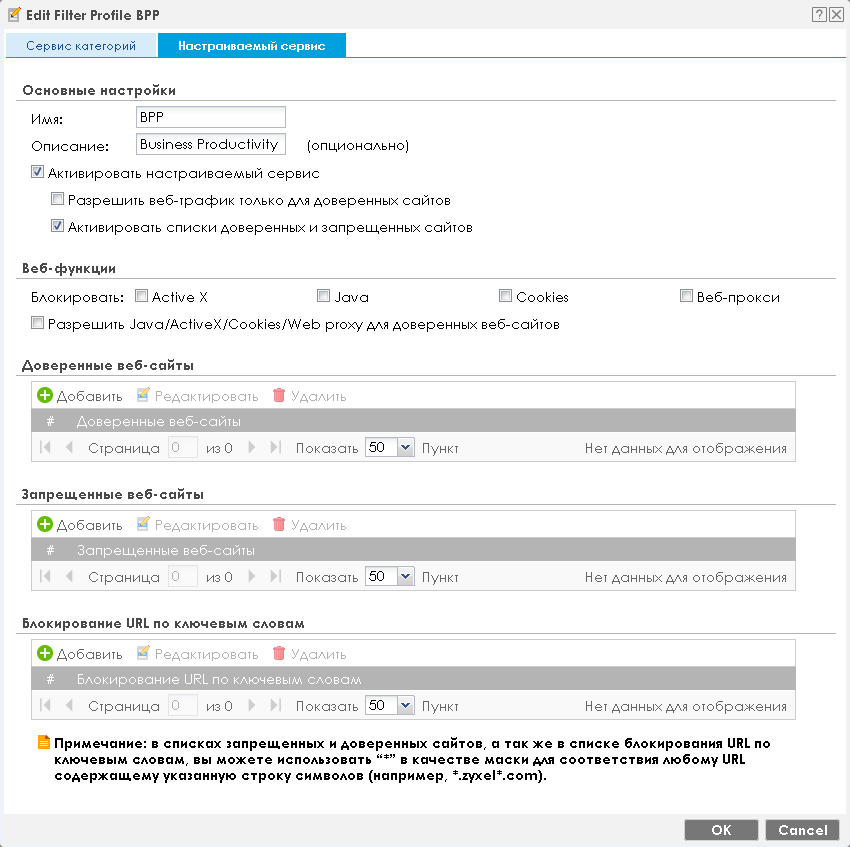
Limiting employee access to certain categories of sites is one of the preventive measures to protect the local network from malicious software.
Malware protection
Anti-virus traffic scanning is perhaps one of the most interesting and popular options offered by Zyxel ATP series firewalls. Immediately it is worth mentioning that we are talking about checking the following protocols: HTTP, FTP, POP3 and SMTP, working on standard ports. Will HTTPS traffic be checked? Yes, it will, if you activate the SSL inspection option, which we will talk about later.
So what types of malware can be detected? Viruses are malicious code designed to disrupt or alter the functioning of other software products and / or the operating system. Worms are self-spreading viruses that exploit vulnerabilities in installed software or the operating system. Spyware is designed to track the user, they intercept correspondence, entered commands, passwords, and so on.
Regardless of the type of malware, the anti-virus scan module calculates the hash sum of the file or its part and compares it with the database located on the firewall. That is why it is so important to be able to regularly update the database of known virus signatures. At the moment, hash calculation is performed using the MD5 algorithm. It is worth noting that the built-in antivirus module allows you to detect even polymorphic viruses.
You can change the anti-virus protection settings using the “Anti-malware protection” item in the “Security Service” group of the “CONFIGURATION” menu.

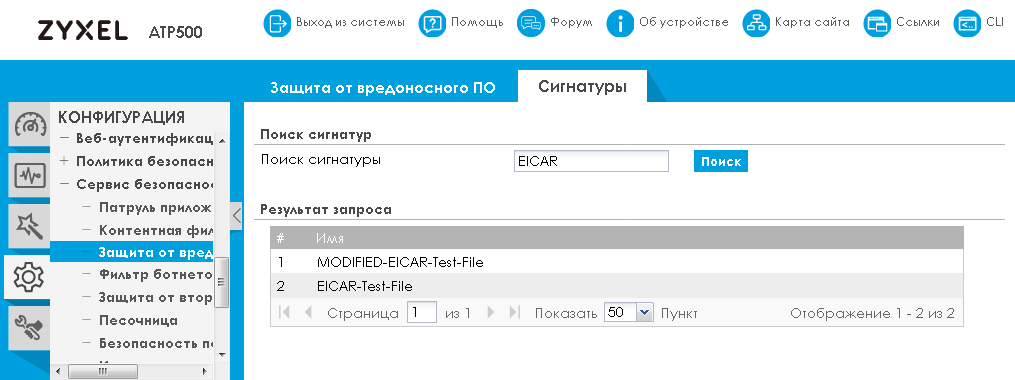
Perhaps a few words should be said about the available settings. If the administrator needs to check the functionality of the anti-virus module, you can use the test "virus" EICAR, which is a regular text string of ASCII characters. This line is shown in the picture below. We specifically publish it in a non-text format in order to avoid false positives for anti-virus protection from Zyxel ATP users.
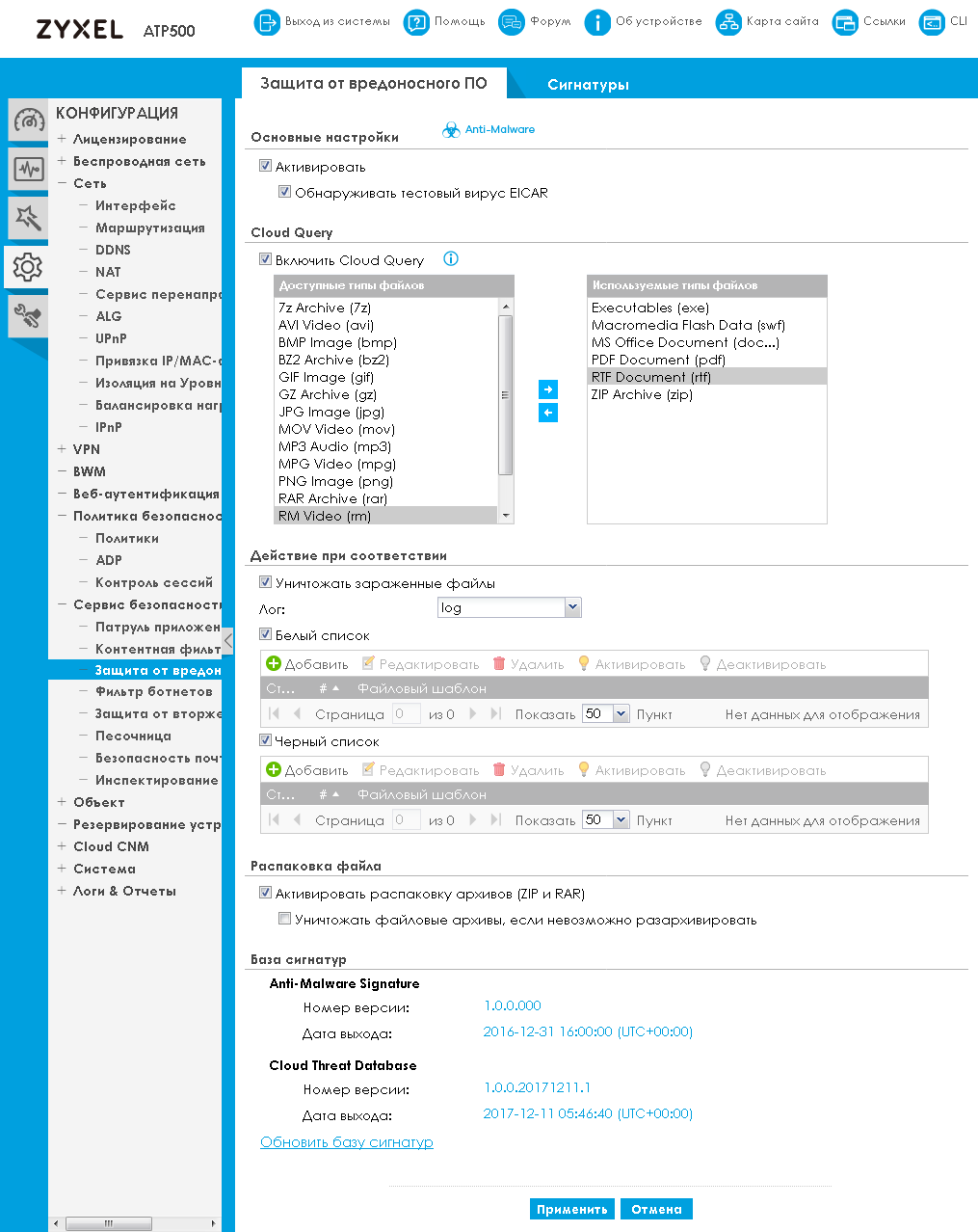
All transferred files are subjected to anti-virus scan even if they are archived. The administrator can enable or disable the verification of ZIP and RAR archives.
Also, using the Cloud Query option, the firewall can send a hash amount to the cloud for comparison with a cloud database. Such a check will be performed only in a situation if the local database does not contain information about the file being scanned.
Probably, our inquisitive reader in this place may have a reasonable question about why access to the cloud is required when there are local signature databases. I must say, the question is very reasonable. And the answer is extremely simple: the local firewall databases are updated, although quite often, but still not in real time. There is some likelihood that any new virus modification may not yet be contained in the local signature databases of the firewall at the time of sending the body of the updated malware to the protected network. In this case, a cloud service will come to the rescue, containing the most complete set of constantly updated set of signatures. Cloud signatures can be added not only by anti-virus experts manually, but also using a mechanism called the sandbox, which we will talk about in one of the following sections.

But what time intervals are we talking about? Virus signature databases are updated up to once per hour. An analysis of a new unknown malware requires no more than 15 minutes of time. Thus, connecting the ability to access the cloud anti-virus database allows you to win from a dozen minutes to several hours of precious time.
The administrator has the ability to manually specify black and white lists of files that are allowed or prohibited to transfer.
Our story about the antivirus module would not be complete if we had not mentioned the possibility of searching for information on the signature database, performed using the Signatures tab of the same menu item.
With this, we conclude our discussion of the capabilities of Zyxel ATP in anti-virus scanning of transmitted files and move on to blocking botnet networks.
Botnet filter
We begin this section with the classic definition: a botnet is a network of infected computers that are managed remotely. This definition has long been outdated. In the modern world, it needs to be expanded significantly, since not only personal computers, servers and laptops, but also tablets and mobile phones, webcams, routers, coffee makers, refrigerators, robotic vacuum cleaners and a great many different gadgets can be infected and managed. whom we voluntarily let into our house. How does it feel to be attacked by a light bulb or air conditioning ?! Unfortunately, many network administrators are rather frivolous in botnets consisting of household appliances and similar devices. They say that a washing machine can against my ultra-modern laptop or server. One is nothing. However, do not forget that, as a rule, the vulnerability is detected and exploited not in one single light bulb taken, but in whole series, which makes such botnets extremely numerous. And even if you are not particularly afraid of a remote attack on your network, nobody wants to be a member of the attacking group.
But let's return to the essence of the section. All infected devices will connect to the botnet control centers (C&C servers) and wait for commands to be executed. Another way to distribute commands is to transmit them via p2p connections between participants in the botnet network, that is, without the participation of dedicated servers.
Zyxel's botnet filtering service allows you to block all connections between the protected network and the management servers, or with known IP addresses of botnet networks. If necessary, the administrator can independently choose which locks should be used. The corresponding settings are collected in the “Botnet filter” item of the “Security Service” group of the “CONFIGURATION” menu.
It is worth noting one subtle point: although the botnet filtering service itself, perhaps, will not protect you from malware infection, it will prevent the possible subsequent participation of your nodes in the botnet network.
Perhaps it is worth noting another subtle point. With the help of botnet networks, DDoS attacks are usually carried out - a distributed attack aimed at denial of service. Although using the option to filter botnet networks, the administrator has the opportunity to protect user workstations and other devices from participating in geo-distributed botnets, this will not completely protect the protected network from DDoS attacks from outside. That is, although the nodes themselves will not take part in DDoS attacks, when conducting an external DDoS attack against public resources of the company, completely different protective equipment and support from the provider may be required. For example, a large-scale volumetric attack cannot be defeated without the involvement of a superior provider with excellent connectivity and wide uplinks. But this is a completely different story.
Intrusion protection
Zyxel ATP firewalls allow you to protect your local network from intruders from the outside by analyzing incoming traffic and comparing it with a database of known attack signatures. The corresponding settings are presented in the “Intrusion protection” item of the same menu group.

It is worth noting that Zyxel firewalls not only allow you to use the signature database supplied by the manufacturer, but also create your own database by adding definitions of new signatures to it.
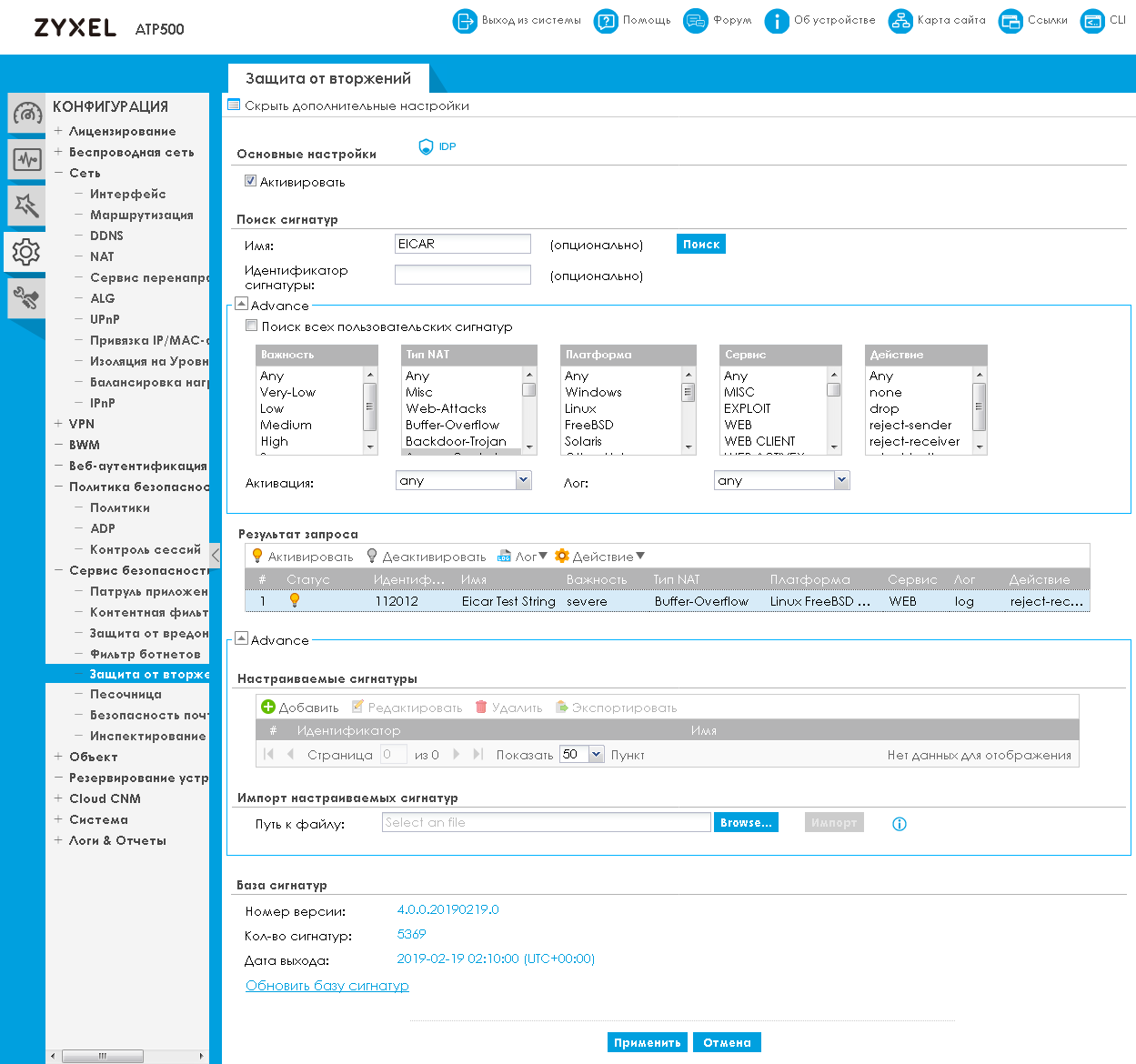
When using multiple Zyxel ATP firewalls on a network, there is no need to manually create your own signatures on each device. Custom signatures can be exported and imported, which greatly simplifies the process of their distribution on the corporate network.
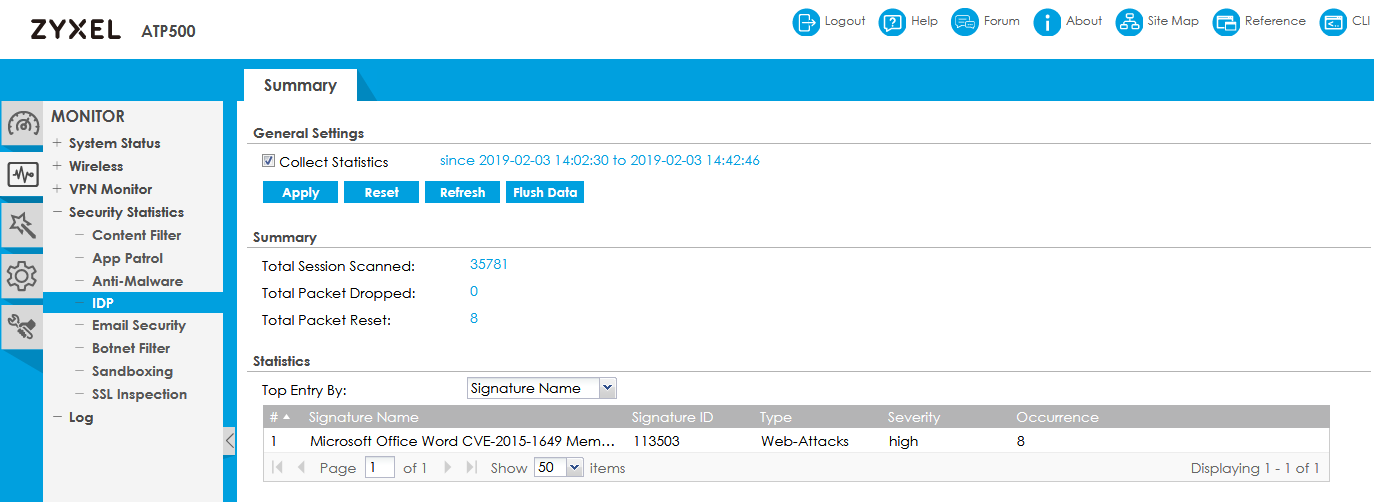
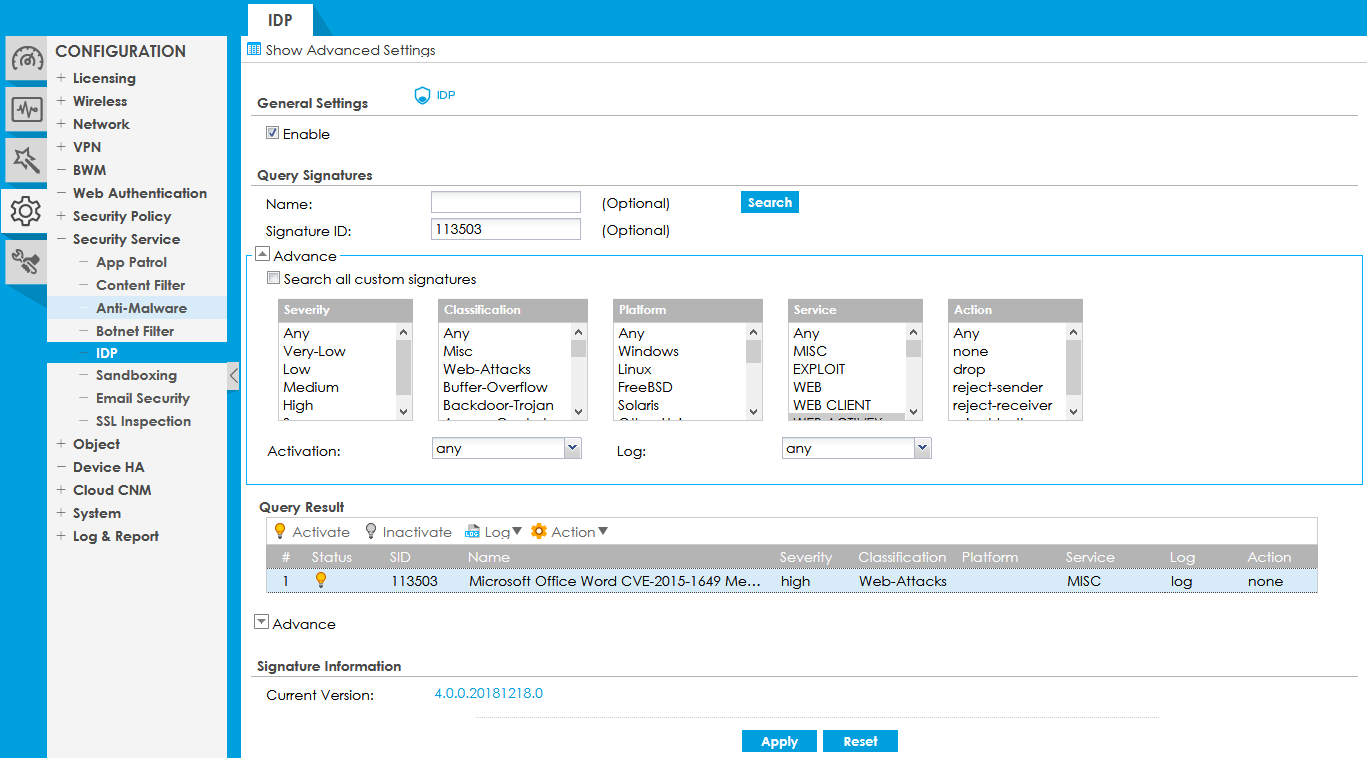
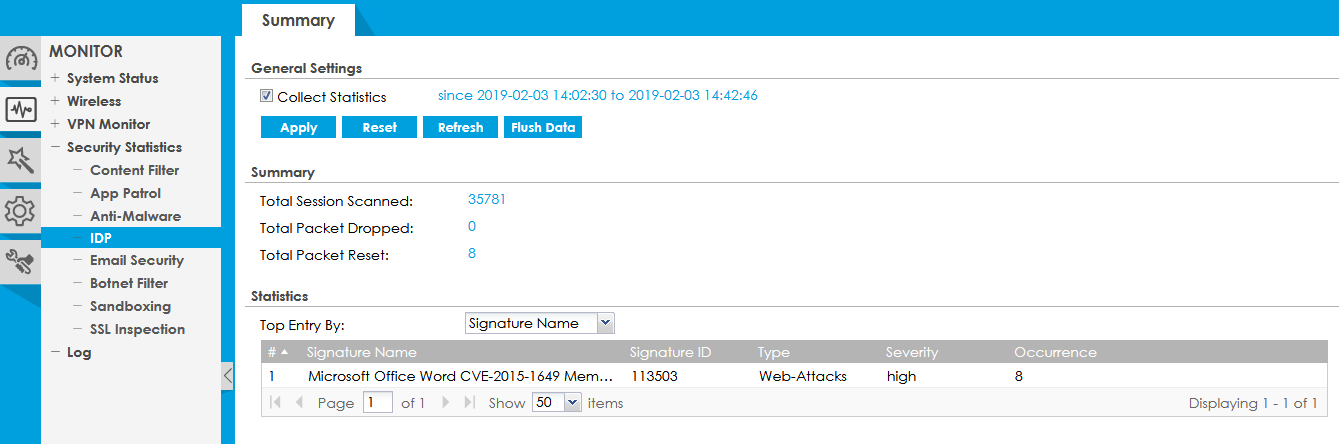
We decided to check how the local network protects this module, for which we simulated a small attack. After some time, we turned to the tested ATP500 for statistics.
Our simulation of the attack did not go unnoticed, as seen in the screenshot above, a web attack with a signature of 113503 was detected. We decided to find out in more detail what the firewall reacted to, for which we launched a search in the database by the signature number.
We also started scanning open TCP and UDP ports from the WAN interface. Information about such a scan necessarily appears in the firewall logs.
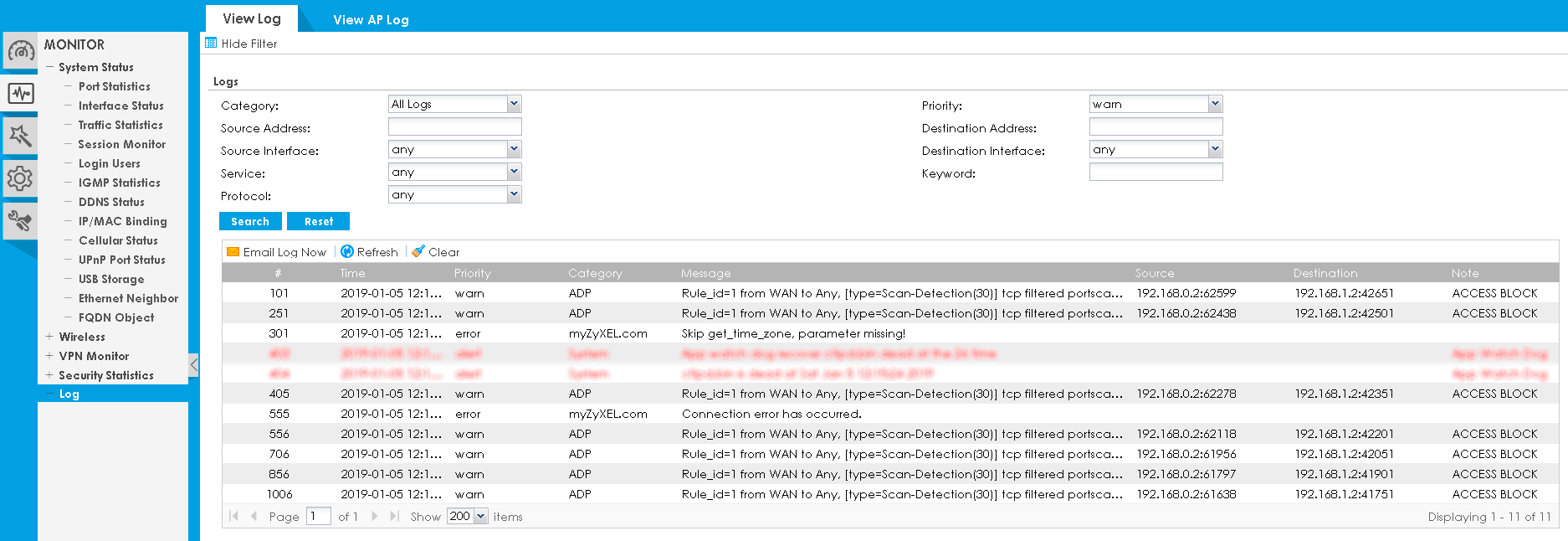
It seems that we got a little carried away, as we promised at the beginning of the article that this time we would not share any test results. All-all, back to the description of the possibilities.
Sandbox
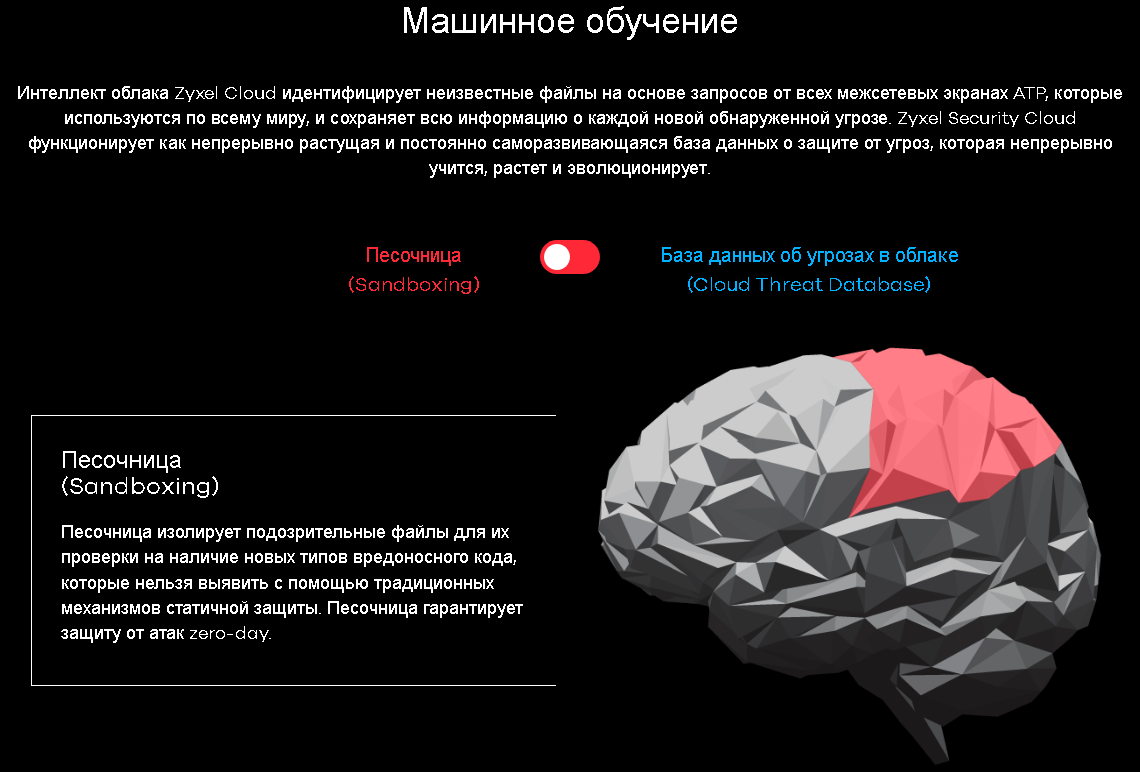
Minimum settings, maximum benefits. Something like this can describe our new service - sandboxing (sandbox). What is the meaning of the service? - Detect new (0-day, zero day) threats, block their spread at the very beginning, crushing the infection in the bud. Sandbox operation parameters are configured using the menu item of the same name.

Sometimes it happens that a particular file contains a new (not yet studied) version of the malware, or a completely new virus. Due to its novelty and obscurity for antivirus products, infection can initially spread with staggering speed. When information about this threat enters the anti-virus database, it may be too late - a lot of devices will be infected. Obviously, the easiest way to deal with the epidemic is at the very beginning, while the consequences of its impact are not so widespread. It is these goals that the sandbox service pursues - to reduce the time when the virus remains unrecognizable.
But how can one discover an unexplored malware? The answer to this question is extremely simple - to launch and observe the actions. No, of course, this is definitely not worth doing at your workstation; therefore, Zyxel software launches a suspicious file in an isolated environment: the ATP series firewall analyzes the transferred files and, if any suspicious code is detected, sends this file to the manufacturer’s cloud lab for further analysis. It is there, in the cloud, that the file is isolated, launched, and further automatically investigated. The results of the study are reported to the sending device and, if necessary, are entered into the database of known virus signatures. This approach allows to minimize detection time and protect the attacked network.
Infected, dangerous, suspicious objects can be transmitted in files of completely different types. It can be ordinary executable files, archives, office documents, or PDF files ... Zyxel ATP firewalls allow the administrator to choose which types of files to search for suspicious code and to specify what actions to take. For automated behavior studies, files ranging in size from 32 bytes to 8 megabytes are sent. The cloud service takes up to 15 minutes to complete and comprehensively analyze the suspicious data received from the firewall.
Email Security
Another traditional channel of information for corporate users is e-mail. Some people read it using a browser, but most use specialized email clients. Zyxel ATP firewalls only support the following mail protocols: POP3 and SMTP. This imposes certain restrictions on the supported topologies.
, , , Zyxel ATP ( HTTP/HTTPS ), ( POP3/SMTP ).
, HTTP/HTTPS . , ATP .
IMAP, , SMTP.
The settings for filtering mail traffic are collected in the “Mail Security” item of the “Security Service” group of the “CONFIGURATION” menu. Here you can activate white and black list blocking, check the contents of letters and their attachments, configure the response to spam, and also enable reputation checks.

Black and white lists allow you to take into account the various fields of the message header, mail addresses and server addresses.


The ideal solution would be to host the mail server in the DMZ, which is accessed using the POP3 and SMTP protocols. In this case, Zyxel ATP firewalls will check mail traffic both between the server and the Internet, and between users and the server. In this case, it will be possible to prevent the spread of malicious messages within the company and to use the maximum capabilities of the firewall.
SSL
. , «» – . Let's Encrypt HTTPS 80% (https://letsencrypt.org/stats/#percent-pageloads) HTTP . , Firefox.

Encryption makes a significant part of the checks described above pointless, simply because all defense mechanisms do not see what real data is being transmitted. However, the Zyxel ATP series firewalls provide the administrator with the ability to decrypt the transmitted data for verification purposes. Using the Profile tab of the SSL Inspection item of the Security Service group of the CONFIGURATION menu, the administrator can manage the inspection profiles of encrypted traffic.
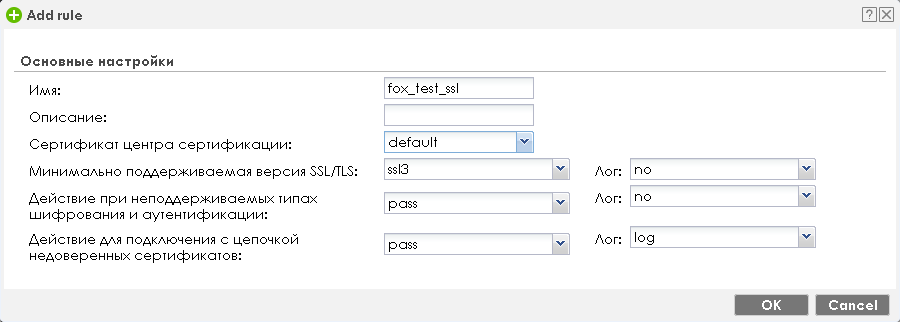
In essence, the Zyxel ATP firewall will act as a proxy server, intercepting encrypted data, decrypting it, checking for malicious code, and then encrypting traffic back.
Recall that the profiles created in the "SSL Inspection" section will not be used by default to verify traffic. They must be explicitly applied when creating policies in the "Policies" clause of the "Security Policy" group.

Naturally, it may be necessary to pass traffic from certain resources without inspection. The “Exclusion List” tab of the same menu item will come to the rescue.

All the magic described in this section would not have been possible without the trust of the certificate used by the firewall on the part of users. The certificate can be renewed by the administrator manually or in automatic mode.
Access to the certificate itself is done using the “Certificate” item in the “Object” group of the “CONFIGURATION” menu. This item will be useful, for example, in a situation when the administrator wants to connect Zyxel ATP to an existing corporate certification authority.


We now turn to the statistics collection service.
Statistics
Event logging and statistics collection require additional processor resources. And although in networks where there is an acute shortage of network equipment resources, disabling the collection of statistics will slightly increase the available bandwidth; in this situation, the administrator will be left without adequate monitoring tools and will not be able to find out what exactly is happening on the network. Therefore, we would highly recommend that without urgent need to disable statistics on the security tools used.
Statistics are managed and viewed using the items in the "Security System Statistics" group of the "MONITORING" menu.
And although we promised not to talk about testing today, we cannot help but share with our readers an example of the Zyxel ATP500 protecting a small local network.
, , Zyxel; - - ? - : , - . , – – Zyxel SecuReporter. , , . .

.
Conclusion
In this article, we tried to describe in sufficient detail the capabilities of the Zyxel ATP series of firewalls. Of course, the description did not concern all device functions, but only those that are somehow related to network protection and checking user traffic for dangerous instructions.
The material turned out to be quite voluminous, which is due to a large number of various functions that provide comprehensive protection of the network perimeter. Of course, Zyxel ATP firewalls can also be used to filter intranet traffic, but, as we promised at the beginning, we put all the topological issues in a separate article.
. , Zyxel Nebula Zyxel ATP. . . Zyxel , Cloud CNM, . Zyxel Nebula .
, Zyxel ATP , . , .
Zyxel, — - : @zyxelru
All Articles