3.2異常検出の問題における画像分類
次のステップは、結果の画像の分類問題を解決することです。 一般に、画像内のクラス(オブジェクト)を検出する問題の解決策は、機械学習アルゴリズムを使用してクラスモデルを構築し、アルゴリズムを使用して画像内のクラス(オブジェクト)を検索することです。

モデルの構築は、2つの段階で構成されます。
a)クラスの特徴抽出:クラスメンバーの特徴ベクトルをプロットします。
図 1
b)後続の認識タスクのために、取得したモデル機能のトレーニング。
クラスオブジェクトは、特徴ベクトルを使用して記述されます。 ベクトルは以下から形成されます:
a)色情報(指向性勾配ヒストグラム);
b)コンテキスト情報。
c)オブジェクトの部分の幾何学的配置に関するデータ。
分類(予測)アルゴリズムは、2つの段階に分けることができます。
a)画像から特徴を抽出します。 この段階で、2つのタスクが実行されます。
- 画像には多くのクラスのオブジェクトが含まれている可能性があるため、すべての代表を見つける必要があります。 これを行うには、左上から右下に画像を通過するスライドウィンドウを使用できます。
- 画像内のオブジェクトのスケールが変更される可能性があるため、画像はスケーリングされます。
b)画像を特定のクラスに関連付ける。 クラスの正式な説明、つまりテストイメージで強調表示されている一連の機能が入力として使用されます。 この情報に基づいて、分類器は画像がクラスに属しているかどうかを判断し、結論の確実性の度合いを評価します。
分類方法。 分類方法は、主にヒューリスティックなアプローチから、数学的統計の方法に基づく正式な手順にまで及びます。 一般的に受け入れられている分類はありませんが、画像分類に対するいくつかのアプローチを区別できます。
- 詳細に基づくオブジェクトモデリングの方法。
- 「言葉の袋」のメソッド;
- 空間ピラミッドを一致させる方法。
この記事で紹介する実装では、次の理由により、著者は「ワードバッグ」アルゴリズムを選択しました。
- 詳細に基づいたモデリングと空間ピラミッドのマッチングのためのアルゴリズムは、空間内の記述子の位置とそれらの相対位置に敏感です。 これらのクラスのメソッドは、画像内のオブジェクトを検出するタスクで効果的です。 ただし、入力データの特性のため、画像分類の問題にはあまり適用できません。
- 「ワードオブワード」アルゴリズムは、他の知識分野で広くテストされており、良好な結果を示し、実装が非常に簡単です。
トラフィックから投影されたビデオストリームを分析するために、単純ベイズ分類器を使用しました[25]。 多くの場合、ワードバッグモデルを使用してテキストを分類するために使用されます。 この場合、アプローチはテキスト分析に似ており、単語だけでなく記述子のみが使用されます。 この分類子の作業は、トレーニング段階と予測段階の2つの部分に分けることができます。
学習フェーズ 。 各フレーム(画像)は、記述子検索アルゴリズムの入力、この場合はスケール不変特徴変換(SIFT)[26]に入力されます。 その後、フレーム間の特異点の相関のタスクが実行されます。 オブジェクトの画像内の特定のポイントは、このオブジェクトの他の画像に表示される可能性が高いポイントです。
異なる画像内のオブジェクトの特別なポイントを比較する問題を解決するために、記述子が使用されます。 記述子はデータ構造であり、他と区別する特異点の識別子です。 オブジェクトの画像の変換に関して不変である場合と不変である場合があります。 私たちの場合、記述子は透視変換、つまりスケーリングに関して不変です。 ハンドルを使用すると、ある画像のオブジェクトの特徴点を、このオブジェクトの別の画像の同じ特徴点と比較できます。
次に、すべての画像から得られた記述子のセットは、k-meansクラスタリング法[26、27]を使用して、類似性によってグループに分類されます。 これは分類器を訓練するために行われ、画像が異常な動作を表しているかどうかについて結論を出します。
以下は、画像記述子分類子をトレーニングするための段階的なアルゴリズムです。
ステップ1 攻撃の有無にかかわらずセットからすべての記述子を抽出します。
ステップ2 n個のクラスターでk-means法を使用してすべての記述子をクラスター化します。
ステップ3 マトリックスA(m、k)の計算。ここで、mは画像の数、kはクラスターの数です。 要素(i; j)は、j番目のクラスターの記述子がi番目の画像に表示される頻度の値を格納します。 このようなマトリックスは、発生頻度のマトリックスと呼ばれます。
ステップ4 式tf idf [28]を使用した記述子の重みの計算:
ここで、tf(「用語頻度」)はこの画像の記述子の出現頻度であり、次のように定義されます。
ここで、tは記述子、kは画像内の記述子の数、ntは画像内の記述子tの数です。 さらに、idf(「ドキュメント逆周波数」)は、サンプル内の特定の記述子を持つ逆画像周波数であり、次のように定義されます。
ここで、Dはサンプル内の特定の記述子を持つ画像の数、{di∈D、t∈di}はDの画像の数です。ここで、tはntです。 = 0。
ステップ5 マトリックスAの記述子の代わりに対応する重みを代入します。
ステップ6 分類。 単純ベイズ分類器の増幅(adaboost)を使用します。
ステップ7 トレーニング済みモデルをファイルに保存します。
ステップ8 これでトレーニングフェーズは終了です。
予測フェーズ 。 トレーニングフェーズと予測フェーズの違いはわずかです。記述子は画像から抽出され、既存のグループと関連付けられます。 この比率に基づいて、ベクトルが構築されます。 このベクトルの各要素は、画像内のこのグループの記述子の出現頻度です。 このベクトルを分析することにより、分類器は特定の確率で攻撃予測を行うことができます。
分類器のペアに基づく一般的な予測アルゴリズムを以下に示します。
ステップ1 画像からすべての記述子を抽出します。
ステップ2 記述子の結果セットをクラスタリングします。
ステップ3 ベクトル[1、k]の計算。
ステップ4 上記の式tf idfによる各記述子の重みの計算。
ステップ5 ベクトルの出現頻度をその重みで置き換える。
ステップ6 以前に訓練された分類器による結果ベクトルの分類。
ステップ7 分類子の予測に基づく、観測されたネットワーク内の異常の存在に関する結論。
4.検出効率の評価
提案された方法の有効性を評価するタスクは、実験的に解決されました。 実験では、実験的に確立された多くのパラメーターが使用されました。 クラスタリングには、1000個のクラスターが使用されました。 生成された画像は1000 x 1000ピクセルでした。
4.1実験データセット
実験のために、インストールが組み立てられました。 これは、通信チャネルで接続された3つのデバイスで構成されています。 インストールのブロック図を図2に示します。
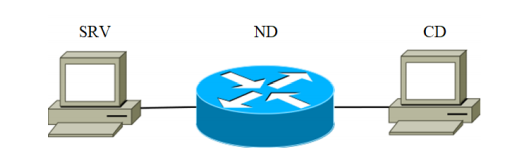
図1
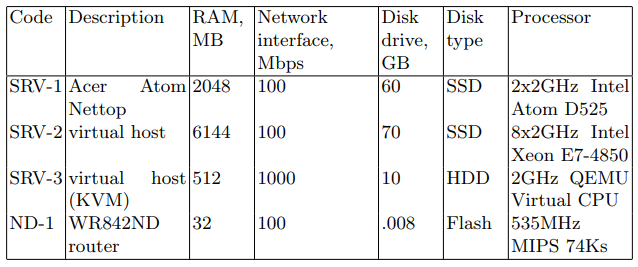
SRVデバイスは攻撃サーバーとして機能します(以降、ターゲットサーバーと呼びます)。 SRVコードとともに表1にリストされているデバイスは、ターゲットサーバーとして順次使用されました。 2番目は、ネットワークパケットを送信するように設計されたネットワークデバイスです。 デバイスの特性は、コードND-1で表1に示されています。
表1.ネットワークデバイスの仕様
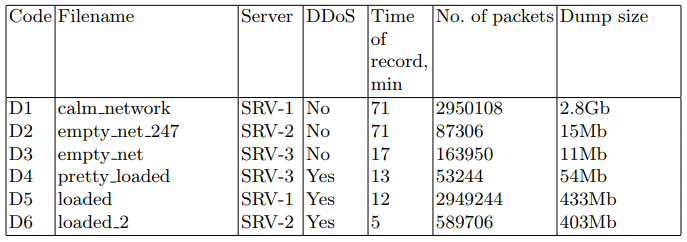
ターゲットサーバーでは、後で発見アルゴリズムで使用するために、ネットワークパケットがPCAPファイルに書き込まれました。 このタスクにはtcpdumpユーティリティが使用されました。 データセットについては、表2で説明しています。
表2.傍受されたネットワークパケットのセット
次のソフトウェアがターゲットサーバーで使用されました:Linuxディストリビューション、nginx 1.10.3 Webサーバー、postgresql 9.6 DBMS。 システムの起動をエミュレートするための特別なWebアプリケーションが作成されました。 アプリケーションは、大量のデータを含むデータベースを要求します。 要求は、さまざまなキャッシュの使用を最小限に抑えるように設計されています。 実験中に、このWebアプリケーションに対する要求が生成されました。
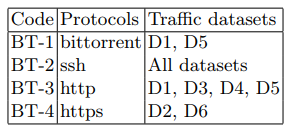
攻撃は、Apache Benchmarkユーティリティを使用して3番目のクライアントデバイス(表1)から行われました。 攻撃中およびその他の期間のバックグラウンドトラフィックの構造を表3に示します。
表3.バックグラウンドトラフィック関数
攻撃として、HTTP GET Floodの分散DoSバージョンを実装します。 実際、このような攻撃は、GETリクエストの一定のストリームの生成であり、この場合はCD-1デバイスからのものです。 それを生成するために、apache-utilsパッケージのabユーティリティを使用しました。 その結果、ネットワークのステータスに関する情報を含むファイルが受信されました。 これらのファイルの主な特徴を表2に示します。攻撃シナリオの主なパラメーターを表4に示します。
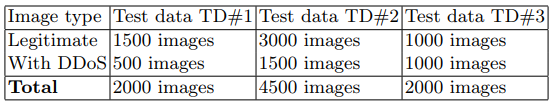
取得されたネットワークトラフィックダンプから、生成された画像のセットTD#1およびTD#2が取得され、トレーニング段階で使用されました。 サンプルTD#3が予測フェーズに使用されました。 テストデータセットの概要を表5に示します。
4.2性能基準
この調査中に評価された主なパラメーターは次のとおりです。
表4. DDoS攻撃の機能
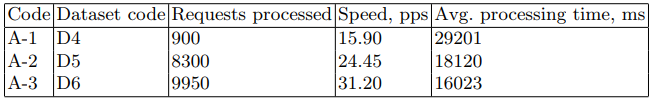
表5.テストイメージセット
a)DR(検出率)-攻撃の総数に対する検出された攻撃の数。 このパラメーターが高いほど、ADSの効率と品質が高くなります。
b)FPR(False Positive Rate)-「正常な」オブジェクトの総数に対する、攻撃として誤って分類された「正常な」オブジェクトの数。 このパラメータが低いほど、異常検出システムの効率と品質が高くなります。
c)CR(複合レート)は、DRおよびFPRパラメーターの組み合わせを考慮した複雑な指標です。 研究ではパラメーターDRとFPRの重要性が等しくなっているため、CR =(DR + FPR)/ 2。
「異常」とマークされた1000個の画像が分類器に送信されました。 認識結果に基づいて、トレーニングサンプルのサイズに応じてDRが計算されました。 次の値が得られました:TD#1の場合DR = 9.5%、TD#2の場合DR = 98.4%。 さらに、画像の後半(「正常」)が分類されました。 結果に基づいて、FPRが計算されました(TD#1 FPR = 3.2%、TD#2 FPR = 4.3%)。 したがって、次の包括的なパフォーマンス指標が得られました:TD#1 CR = 53.15%、TD#2 CR = 97.05%。
5.結論と今後の研究
実験結果から、異常を検出するために提案された方法は、攻撃の検出において高い結果を示すことがわかります。 たとえば、大規模なサンプルでは、包括的なパフォーマンスインジケーターの値は97%に達します。 ただし、この方法にはアプリケーションにいくつかの制限があります。
1. DRとFPRの値は、トレーニングセットのサイズに対するアルゴリズムの感度を示しています。これは、機械学習アルゴリズムの概念的な問題です。 サンプルを増やすと、検出パフォーマンスが向上します。 ただし、特定のネットワークに対して十分に大きなトレーニングセットを実装できるとは限りません。
2.開発されたアルゴリズムは決定論的であり、同じ画像が毎回同じ結果で分類されます。
3.アプローチの有効性指標は、コンセプトを確認するのに十分ですが、誤検知の数も多く、実際の実装が困難になる可能性があります。
上記の制限(ポイント3)を克服するために、ナイーブベイジアン分類器を畳み込みニューラルネットワークに変更することが想定されており、著者によれば、異常検出アルゴリズムの精度を高める必要があります。
参照資料
1. Mohiuddin A.、Abdun NM、Jiankun H .:ネットワーク異常検出技術の調査。 In:Journal of Network and Computer Applications。 巻 60、p。 21(2016)
2. Afontsev E。:ネットワーク異常、2006 nag.ru/articles/reviews/15588 setevyie-anomalii.html
3. Berestov AA:インターネット上のウイルス攻撃から保護するための実動システムに基づくインテリジェントエージェントのアーキテクチャ。 In:XV全ロシア科学会議高等学校システムにおける情報セキュリティの問題」、pp。 180?276(2008)
4. Galtsev AV:異常なネットワーク状態を特定するためのトラフィックのシステム分析:技術科学候補の論文。 サマーラ(2013)
5. Kornienko AA、Slyusarenko IM:侵入検知システムおよび方法:現状と改善の方向、2008 citforum.ru/security internet / ids overview /
6. Kussul N.、Sokolov A。:可変順序のマルコフ連鎖を使用したコンピューターシステムユーザーの行動における適応異常検出。 パート2:異常の検出方法と実験結果。 In:情報と制御の問題。 問題4、ページ。 83?88(2003)
7. Mirkes EM:ニューロコンピューター:ドラフト標準。 科学、ノボシビルスク、pp。 150-176(1999)
8. Tsvirko DA生産モデル手法を使用したネットワーク攻撃ルートの予測、2012 academy.kaspersky.com/downloads/academycup参加者/ cvirko d。 ppt
9. Somayaji A。:システムコール遅延を使用した自動応答。 In:USENIX Security Symposium 2000、pp。 185-197、2000
10. Ilgun K。:USTAT:UNIX用のリアルタイム侵入検知システム。 で:セキュリティとプライバシーの研究に関するIEEEシンポジウム、カリフォルニア大学(1992)
11. Eskin E.、Lee W.、およびStolfo SJ:モデリングシステムは、動的なウィンドウサイズでの侵入検知を要求します。 In:DARPA Information Survivability Conference and Exposition(DISCEX II)、2001年6月
12. Ye N.、Xu M.、およびEmran SM:異常検出のための無向リンクを備えた確率的ネットワーク。 In:2000 IEEE Workshop on Information Assurance and Security、West Point、NY(2000)
13. Michael CCとGhosh A。:プログラムベースの異常検出に対する2つの状態ベースのアプローチ。 In:情報とシステムセキュリティに関するACMトランザクション。 いや 5(2)、2002
14. Garvey TD、Lunt TF:モデルベースの侵入検知。 で:第14回国家コンピューターセキュリティ会議、メリーランド州ボルチモア(1991)
15. Theus M.およびSchonlau M。:構造ゼロに基づく侵入検知。 In:統計コンピューティングおよびグラフィックニュースレター。 いや 9(1)、pp。 12?17(1998)
16. Tan K。:Unixコンピュータセキュリティへのニューラルネットワークの適用。 In:ニューラルネットワークに関するIEEE国際会議。 巻 1、pp。 476?481、パース、オーストラリア(1995)
17. Ilgun K.、Kemmerer RA、Porras PA:状態遷移分析:ルールベースの侵入検知システム。 In:IEEE Trans。 ソフトウェア工学 巻 21、いいえ。 3、(1995)
18. Eskin E。:学習した確率分布を使用したノイズの多いデータに対する異常検出。 で:17th International Conf。 機械学習について、pp。 255?262。 モーガン・カウフマン、サンフランシスコ、カリフォルニア(2000)
19. Ghosh K.、Schwartzbard A.、およびSchatz M。:侵入検知のためのプログラム動作プロファイルの学習。 In:侵入検知とネットワーク監視に関する第1回USENIXワークショップ、pp。 51?62、サンタクララ、カリフォルニア(1999)
20. Ye N。:異常検出の時間的挙動のマルコフ連鎖モデル。 で:2000 IEEE Systems、Man、and Cybernetics、Information Assurance and Security Workshop(2000)
21. Axelsson S。:侵入検知の難しさに対する基本レートの誤acyとその意味。 In:ACM Conference on Computer and Communications Security、pp。 1?7(1999)
22. Chikalov I、Moshkov M、Zielosko B。:動的計画法に基づく決定ルールの最適化。 ニジニ・ノヴゴロドのロバチェフスキー州立大学のヴェストニクで、いいえ。 6、pp。 195-200
23. Chen CH:パターン認識とコンピュータービジョンのハンドブック。 マサチューセッツ大学ダートマス、アメリカ(2015)
24. Gantmacher FR:行列の理論、p。 227.科学、モスクワ(1968)
25. Murty MN、Devi VS:パターン認識:アルゴリズム。 Pp。 93-94(2011)
2. Afontsev E。:ネットワーク異常、2006 nag.ru/articles/reviews/15588 setevyie-anomalii.html
3. Berestov AA:インターネット上のウイルス攻撃から保護するための実動システムに基づくインテリジェントエージェントのアーキテクチャ。 In:XV全ロシア科学会議高等学校システムにおける情報セキュリティの問題」、pp。 180?276(2008)
4. Galtsev AV:異常なネットワーク状態を特定するためのトラフィックのシステム分析:技術科学候補の論文。 サマーラ(2013)
5. Kornienko AA、Slyusarenko IM:侵入検知システムおよび方法:現状と改善の方向、2008 citforum.ru/security internet / ids overview /
6. Kussul N.、Sokolov A。:可変順序のマルコフ連鎖を使用したコンピューターシステムユーザーの行動における適応異常検出。 パート2:異常の検出方法と実験結果。 In:情報と制御の問題。 問題4、ページ。 83?88(2003)
7. Mirkes EM:ニューロコンピューター:ドラフト標準。 科学、ノボシビルスク、pp。 150-176(1999)
8. Tsvirko DA生産モデル手法を使用したネットワーク攻撃ルートの予測、2012 academy.kaspersky.com/downloads/academycup参加者/ cvirko d。 ppt
9. Somayaji A。:システムコール遅延を使用した自動応答。 In:USENIX Security Symposium 2000、pp。 185-197、2000
10. Ilgun K。:USTAT:UNIX用のリアルタイム侵入検知システム。 で:セキュリティとプライバシーの研究に関するIEEEシンポジウム、カリフォルニア大学(1992)
11. Eskin E.、Lee W.、およびStolfo SJ:モデリングシステムは、動的なウィンドウサイズでの侵入検知を要求します。 In:DARPA Information Survivability Conference and Exposition(DISCEX II)、2001年6月
12. Ye N.、Xu M.、およびEmran SM:異常検出のための無向リンクを備えた確率的ネットワーク。 In:2000 IEEE Workshop on Information Assurance and Security、West Point、NY(2000)
13. Michael CCとGhosh A。:プログラムベースの異常検出に対する2つの状態ベースのアプローチ。 In:情報とシステムセキュリティに関するACMトランザクション。 いや 5(2)、2002
14. Garvey TD、Lunt TF:モデルベースの侵入検知。 で:第14回国家コンピューターセキュリティ会議、メリーランド州ボルチモア(1991)
15. Theus M.およびSchonlau M。:構造ゼロに基づく侵入検知。 In:統計コンピューティングおよびグラフィックニュースレター。 いや 9(1)、pp。 12?17(1998)
16. Tan K。:Unixコンピュータセキュリティへのニューラルネットワークの適用。 In:ニューラルネットワークに関するIEEE国際会議。 巻 1、pp。 476?481、パース、オーストラリア(1995)
17. Ilgun K.、Kemmerer RA、Porras PA:状態遷移分析:ルールベースの侵入検知システム。 In:IEEE Trans。 ソフトウェア工学 巻 21、いいえ。 3、(1995)
18. Eskin E。:学習した確率分布を使用したノイズの多いデータに対する異常検出。 で:17th International Conf。 機械学習について、pp。 255?262。 モーガン・カウフマン、サンフランシスコ、カリフォルニア(2000)
19. Ghosh K.、Schwartzbard A.、およびSchatz M。:侵入検知のためのプログラム動作プロファイルの学習。 In:侵入検知とネットワーク監視に関する第1回USENIXワークショップ、pp。 51?62、サンタクララ、カリフォルニア(1999)
20. Ye N。:異常検出の時間的挙動のマルコフ連鎖モデル。 で:2000 IEEE Systems、Man、and Cybernetics、Information Assurance and Security Workshop(2000)
21. Axelsson S。:侵入検知の難しさに対する基本レートの誤acyとその意味。 In:ACM Conference on Computer and Communications Security、pp。 1?7(1999)
22. Chikalov I、Moshkov M、Zielosko B。:動的計画法に基づく決定ルールの最適化。 ニジニ・ノヴゴロドのロバチェフスキー州立大学のヴェストニクで、いいえ。 6、pp。 195-200
23. Chen CH:パターン認識とコンピュータービジョンのハンドブック。 マサチューセッツ大学ダートマス、アメリカ(2015)
24. Gantmacher FR:行列の理論、p。 227.科学、モスクワ(1968)
25. Murty MN、Devi VS:パターン認識:アルゴリズム。 Pp。 93-94(2011)
伝統的に、私たちはあなたのコメントを待っており、来週の月曜日に開催されるオープンデーに皆さんを招待します。