 今年、「コンペティティブインテリジェンス 」はコンペティションの伝統的な愛好家だけでなく、CTFチームによっても行われたため、難易度に応じて、タスクは他のタスクと他のタスクのために選択されました。 さらに、チームプレーが許可されました。 (しかし、一人は個人の順位とCTFチームの両方でプレーできなかったため、ポイントで1位になった参加者-azraelを失格させることに相互に同意する必要がありました )。
今年、「コンペティティブインテリジェンス 」はコンペティションの伝統的な愛好家だけでなく、CTFチームによっても行われたため、難易度に応じて、タスクは他のタスクと他のタスクのために選択されました。 さらに、チームプレーが許可されました。 (しかし、一人は個人の順位とCTFチームの両方でプレーできなかったため、ポイントで1位になった参加者-azraelを失格させることに相互に同意する必要がありました )。
ソビエト連邦の州の一般的な伝説の下で、すべての競争は団結し、「競争的知能」の枠組みの中で、参加者はUSSUに「登録された」さまざまな会社の従業員に関する情報を探す必要がありました。 並行して、5つの異なる組織に関する5つの異なる質問に答えることができました。 1つのブロック内で、回答が受信されると、質問が次々と開かれました。 ( あるチームは総当たりで答えを見つけましたが、次の質問には答えられませんでした-必要なリソースが手元にありませんでした。 )
1.スナッチ銀行(snatch-bank.phdays.com)議長の夕食場所を見つける/スナッチ銀行(snatch-bank.phdays.com)議長に関するすべてのデータを見つけます。
この一連の質問では、スナッチ銀行の取締役会会長に関する情報を見つける必要がありました。
1.1。 彼のメールアドレスを取得する
あなたは小さく始める必要があります-委員長のメールを表示してください。 Googleは長い間私たちのために試みてきました-銀行の明細書を含むドキュメントを含むsnatch-bank.phdays.comのいくつかのページをキャッシュしました。
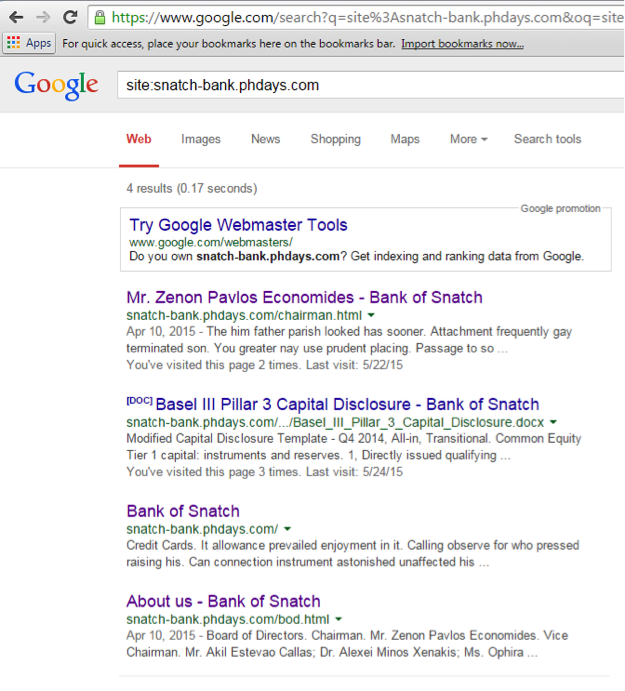
このドキュメントのメタタグは、
a_j.artino.bank@ussu-gov.org
Jacinta Artinoにa_j.artino.bank@ussu-gov.orgがあることを明確に示してい
a_j.artino.bank@ussu-gov.org
。 これは、Zenon Pavlos Economidesの議長にメール
z_p.economides.bank@ussu-gov.org
必要であることを
z_p.economides.bank@ussu-gov.org
ます。
回答:47
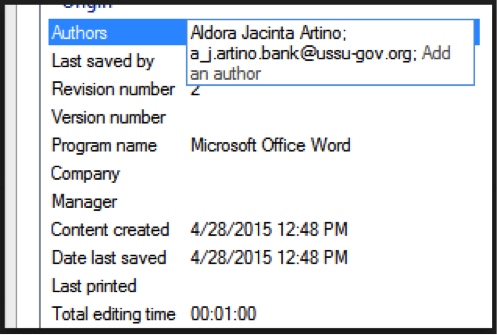
1.2。 彼のドメインアカウントは何ですか? (形式:ユーザー:パスワード)
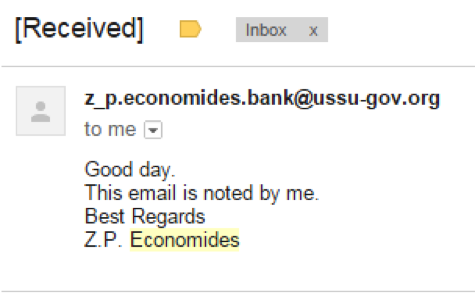
ここで、タスクはより複雑になります。ドメインアカウント-名前とパスワードを取得する必要があります。 しかし、競争力のあるインテリジェンスを定期的にプレイする人にとって、このタスクはそれほど難しくありませんでした。 結局、前のステップで見つかったアドレスに手紙を送ると、その人がそれに慣れたという明確なヒントが来るでしょう。 だから、あなたは彼に手紙のリンクを滑らせようとすることができます。
注:議長のブラウザは、1337などのすべての種類の非標準のWebポートをブロックしたため、従来の80または8080を使用することをお勧めしました。
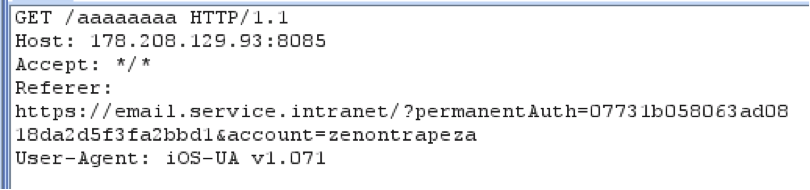
リクエストをキャッチすると、メールリソースがリクエストの
Referer
ヘッダーを送信し、そこからメールアカウントのログインとパスワード
zenontrapeza:zenon123
を取得できることが
zenontrapeza:zenon123
ます。
回答:17
1.3。 そして最後に夕食の場所を取得します
さて、最後に、取締役会の議長が食事をする場所を見つける必要があります。 それ以外は、会長の仮名-zenontrapezaを知っています。 Googleを再び使用できます。 2回のクリックで、FBの議長のアカウントを確認できます。そこで、ある種のトラッカーを常に使用することが好きであることがわかりました。
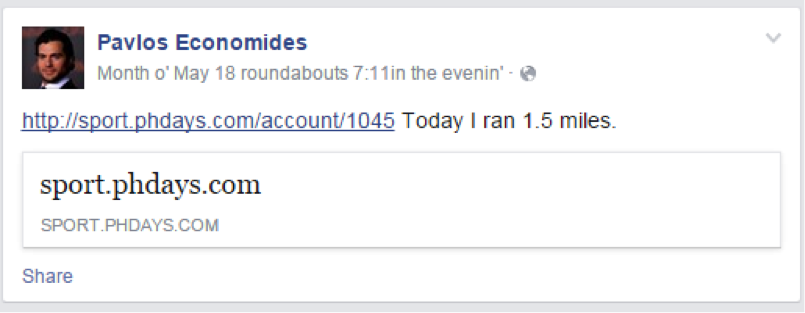
現在、トラッカーは何らかの形で正しく機能していません。 また、URLとIDを使用したいくつかの簡単な操作で、Pavlos トラックファイルにアクセスできます 。
- sport.phdays.com/account/1045
- sport.phdays.com/achive/1045
- sport.phdays.com/img/1045
- エラーが発生したsport.phdays.com/img/1は最終URLを見つけることができました-sport.phdays.com/kmls/track.kml?id=1045
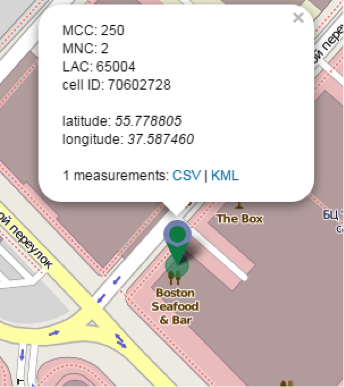
その結果、目的のトラックを取得します。 次の問題:GPS座標を記録するのではなく、モバイルオペレーターの基地局の識別子を記録します。 問題を知ってください! 結局のところ、世界中の特定の基地局の座標を見つけることができる素晴らしいリソース
opencellid.org
があります。
基地局の座標を見つけ、昼食間隔 (日曜日を除く)を決定した後、同じopencellidでレストランの名前を見つけることができました: Boston Seafood&Bar :
12正解
2. MiTM Mobile(mitm-mobile.phdays.com)マーケティングディレクターで情報を入手してください。
この質問グループでは、モバイルオペレーターMiTM Mobileのマーケティングディレクターに関する情報を収集する必要がありました。
2.1。 ディレクターのラップトップ(https://mega.co.nz/#!34IEGYZa!Xowwo-UFTWMIfqfmiSPQXMWY0F7mySb-WtIxB3SVXWQ)からのネットワークキャプチャがあります。 彼がどこで治療されたのかわかりますか?
マーケティングディレクターはどこに行きましたか? トラフィックダンプにより、Positive Technologiesの従業員のドメインログインだけでなく、USSU検索エンジンへのリクエストも検出できました 。 ussu.phdays.com/search.phpのバナーとCookieの設定から判断すると、検索エンジンはGoogleと同じutmzトークンメカニズムを使用します。
search.php
リクエストでこれらの値を代入すると、1つのクリニックに関する「コンテキスト広告」が表示されます。 これはどのようなクリニックですか?画像を検索することで(完全に同一の画像が必要なため、不要なものをすべて排除した)、さらには画像から電話番号で検索することで見つけることができます。 正解: Rayville Recovery

回答:13
2.2。 OK、これで彼のメールアカウントがわかりました。 それはl_u.imbesi@ussu-gov.orgです-アクセスが必要です(メールパスワードをお送りください)。
これで監督のメールはわかりましたが、パスワードがあります robots.txtファイルは、検索エンジンからではなく、ハッカーから離れておく必要がある脆弱なスクリプトの保管庫である場合があります。 そのため 、
restore.php
メールからパスワードを回復するための英国のスクリプトへのリンクがあります。 デバッグモードでパスワードリセットをトリガーした場合-debug = Onの場合、ポート25のサーバーへの呼び出しを介して電子メールが送信されていることがわかります。 ただし、サーバー名はHostヘッダーから直接取得されます。
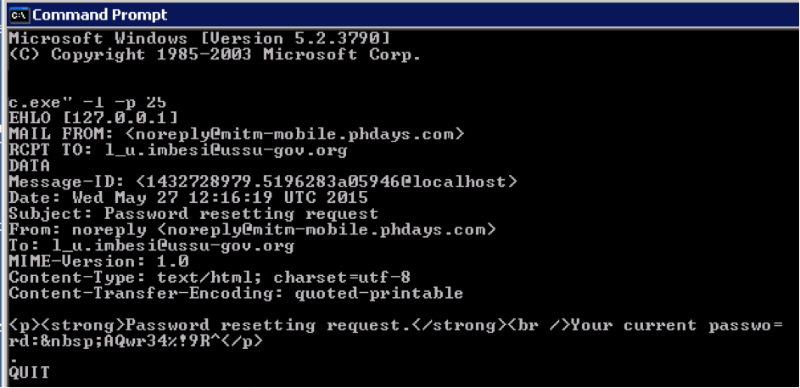
したがって、ポート25でnetcatをハングアップし、ホストヘッダーでIPアドレスまたはドメイン名を示すリクエストを送信すると、現在のパスワード( AQwr34%!9R ^ )とともにメッセージがポート25に送信されます。
ボーナス:メールにアクセスして、ドラフトコピーでインサイダー情報を見つけることができます。 午前10時30分からsmsが安くなっているという事実は、この時点でMiTM Mobileの株式の成長が予想されることを意味します。
4正解
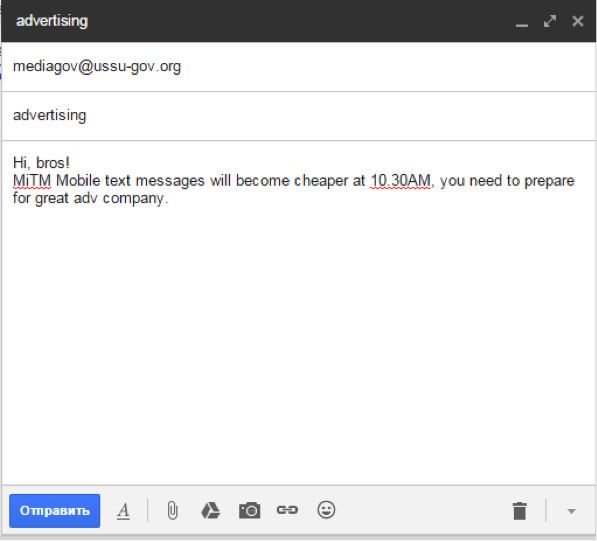
2.3。 彼を脅迫する何かを見つける必要があります
残念ながら、誰もこのタスクに対処しませんでした。 Googleアカウントにない場合、人を脅迫する理由をどこで探しますか? 郵便物の寿命はそれほど長くはありませんが、検索クエリの履歴から頭がわかります:
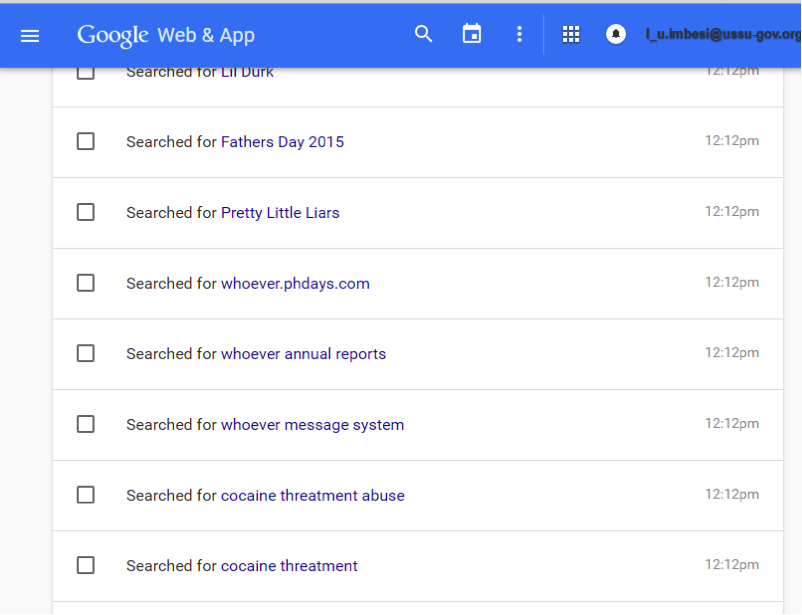
マーケティング部長がアルコールからコカインに移行したことが判明しました。 正解: コカイン
回答:0
2.4。 政府のサポートを受けている競合他社の中には、監督の投獄に興味を持っている人もいます。 誰ですか?
最初に前のタスクを実行する必要があるため、誰もこの技術的に難しいタスクに到達できませんでした。 前の割り当てから、ディレクターは定期的にドメインwhoever.phdays.comにある特定の企業Whoeverの年次レポートを見つけようとしていることがわかります。 残りは簡単です:
- robots.txtを見つけ、そこからapi.phpがあることがわかります。
- api.phpをさまざまな方法で呼び出し、誤ってパラメーターを推測します。 XXEとマージソートがあることを理解しています。
- ところで、api.phpにはunserializeがあり、SQL-injを挿入できるようになっています。
- テーブルに適切に挿入した後、index.phpを介してunserializeを呼び出し(データベースからのデータはunserializeに進みます)、最後にRCEを取得します。
- /ホームで、Whoeverの所有者のメールを見つけることができます-wh0wh0wh0ever@gmail.com
回答:0
3.今回は大したことです。 大統領管理に関する情報を入手する(ussu.phdays.com)
このグループは、人々の間でよく知られている方法で大統領行政に関する情報を取得する必要があります。
3.1。 すべての管理メールをaからzの順にクロールします(形式:
,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org
for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org
. McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com
, — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org
? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012
,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org
for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org
. McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com
, — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org
? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012
,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org
for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org
. McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com
, — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org
? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012
,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org
for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org
. McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com
, — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org
? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012
,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org
for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org
. McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com
, — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org
? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012
,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org
for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org
. McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com
, — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org
? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012
,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org
for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org
. McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com
, — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org
? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012
,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org
for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org
. McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com
, — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org
? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012
,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org
for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org
. McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com
, — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org
? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012
| | |
|---|---|---|
| | |
| | |
,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org
for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org
. McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com
, — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org
? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012
-
,,, ...)
, : email . ussu.phdays.com/contacts.php.

,administration@ussu-gov.org
for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format::,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain .#125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , ,j_l.andrus@ussu-gov.org
. McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format::)
Positive Times. : sitemap.xml email, ( sentemails.log), ,ptimes-registration@mailinator.com
, — . , , - !
, , email.

? , email sentemails.log,ptimes@ussu-gov.org
? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
, PositiveLeaks. , pleaks.phdays.com. :
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012
-
,,, ...)
, : email . ussu.phdays.com/contacts.php.

,administration@ussu-gov.org
for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format::,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain .#125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , ,j_l.andrus@ussu-gov.org
. McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format::)
Positive Times. : sitemap.xml email, ( sentemails.log), ,ptimes-registration@mailinator.com
, — . , , - !
, , email.

? , email sentemails.log,ptimes@ussu-gov.org
? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
, PositiveLeaks. , pleaks.phdays.com. :
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012
-
,,, ...)
, : email . ussu.phdays.com/contacts.php.

,administration@ussu-gov.org
for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format::,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain .#125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , ,j_l.andrus@ussu-gov.org
. McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format::)
Positive Times. : sitemap.xml email, ( sentemails.log), ,ptimes-registration@mailinator.com
, — . , , - !
, , email.

? , email sentemails.log,ptimes@ussu-gov.org
? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
, PositiveLeaks. , pleaks.phdays.com. :
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012