
Are there any “viruses” for Mac? In short, yes rather than no. Want to know why such a slightly strange answer?
A large number of people call viruses all malware. If you approach formally, then only programs that can spread independently can be called viruses .
But there is a nuance - the current malware is often complex and can consist of several components - some are responsible for infection, others for distribution, and others for the load that is useful for attackers. Viruses can also be grouped according to various characteristics, for example, by the distribution method or the harmful load.
Therefore, I propose not to go into polemic about whether it is a virus or not a virus, but to try to understand whether malware threatens our poppies and if it does, what kind and how it infects systems.
Story
Surely many are tormented by the question of when the first virus appeared for Apple computers. Virus 1,2,3 and ElkCloner are considered to be one of the very first. They were written back in 1981 .
The virus with the simple name of Virus was created as a concept check. The main idea was to write a program that could be distributed independently, but did not affect other applications. The first two versions were distributed independently, but affected the operation of the system or other software. Therefore, there are three versions.
A few years after 1981, other viruses appeared . In the late 80s and 90s, several dozens of malware were created.
As you know, then Apple computers have not yet used Intel processors. And in general, the world of computers was very different from the present - personal computers, and even more so, not everyone had access to the Internet, and computer threats were treated in a completely different way. Compared to mainframes, which were accessed physically alternately, personal computers have a completely different threat model. For example, one computer on a network may try to attack another.
The early wreckers did more out of curiosity or thirst for fame. Subsequently, it became a means of profit (to call it a language does not turn to earnings). Let's see how things are today.
Our time (2016 -...)
Cryptographer (ransomware)
Keranger - 2016
It was distributed along with the Transmission torrent client, the site of which was hacked and malicious code was introduced into the official installer. The modified application was signed, so the protection in the form of GateKeeper could not work. This was probably the first crypto encryptor for macOS.
Backdoor
Eleanor - 2016
This virus spread under the guise of the usual EasyDoc Converter.app application outside the AppStore. An application should convert documents from one format to another, but it does anything, but not that. In particular, it installs a backdoor on the user's computer, which works through the Tor network. The name of the new Tor service is posted on pastebin.com, from where the attacker gets it.
Keydnap - 2016
Another interesting backdoor was distributed as a zip archive. Inside was the “screenshot.jpg“ file (with a space at the end of the extension). In fact, this file was not an image, but an executable file. Another interesting point - this backdoor had a second distribution method. Namely, through the torrent client Transmission. Yes, there is no mistake. The same application was previously used to distribute the Keranger ransomware.
Mokes - 2016
The backdoor Mokes is notable for the fact that although it was discovered, it was not possible to find the exact vector of infection. There was only speculation that it was distributed via phishing emails.
Komplex - 2016
Distributed by email as an application disguised as a pdf file. When “opening” this application, a malicious load was launched, but a pdf document was also opened for disguise. The main functionality comes down to loading other files and executing commands. Thus, this malware was most likely used to spread other malicious programs. The first part of the backdoor was discovered in 2016, and the second, more functional part, in 2017.
Advertising (adware)
FakeFileOpener - 2016
The infection method is quite old. When you get to a specialized site, the user receives a message stating that his computer is infected and you need to download an application that will clean it up.
In fact, the MacFileOpener application was downloaded, which registered itself as a handler for a large number of file types. As a result, the application did not have to create any demons or invent anything else. When a user tried to open any file for which the malware registered itself, the operating system launched the malware.
Applications showing ads are dangerous not only and not so much by the advertisement itself. They often install root certificates on the system so that they can view encrypted traffic. And the traffic may contain passwords, credit card information, session cookies and other secrets.
Statistics
To dig into news archives and search for all malware is a dubious pleasure, therefore I will limit myself to the statistics of the portal av-test.org. According to intelligence, thousands of malware are created for poppies.
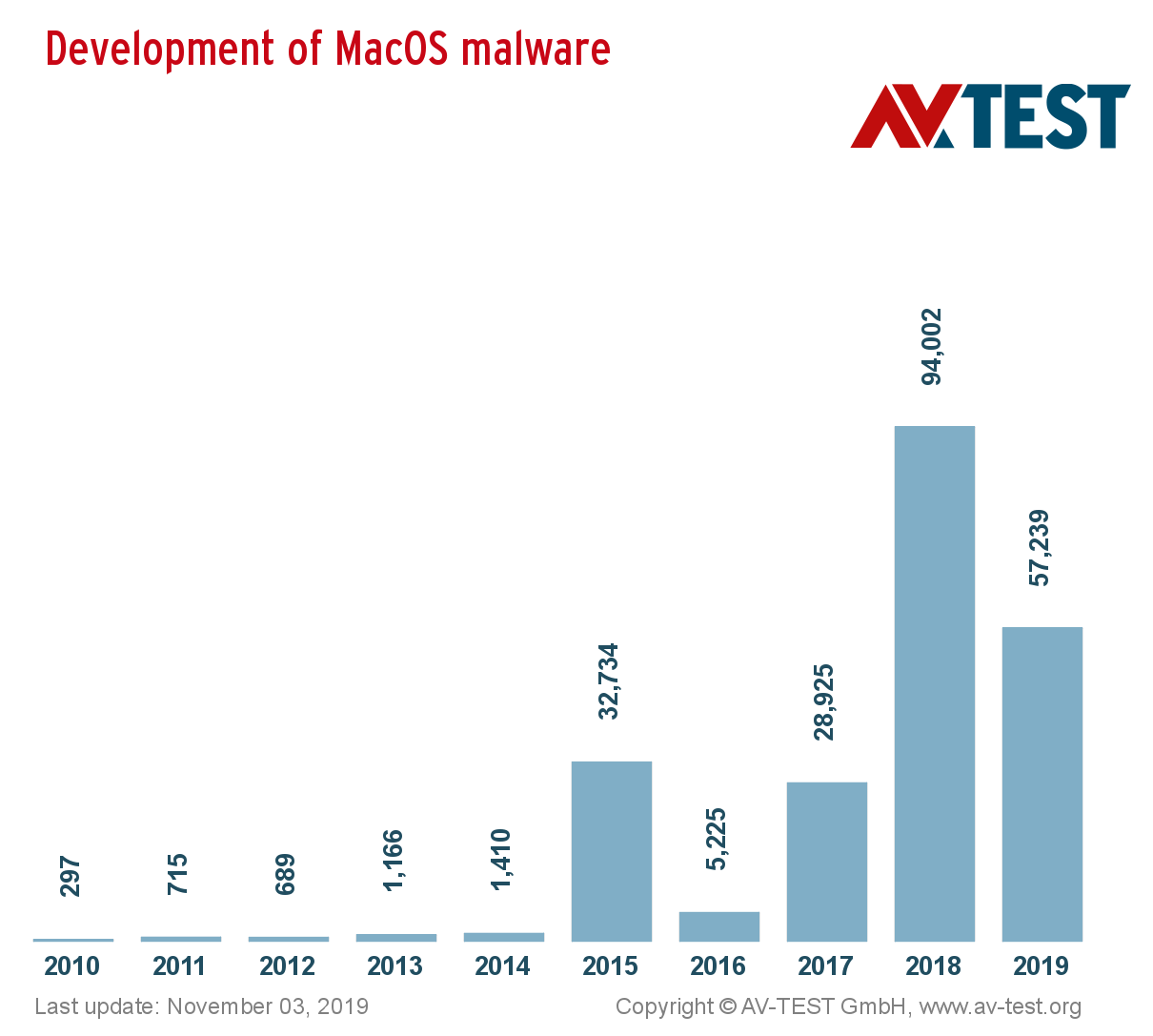
Bad news
For the first half of 2019, new malware appeared and some old ones were reanimated.
Dok - 2017 -> 2019
Like the original version, it was distributed as a zip archive by e-mail. The archive contained the installation .pkg file. When starting up, the user received a fake message saying that the package was damaged and could not be started. Thus dulling vigilance. The malware intercepts traffic and sends data to attackers through the tor network.
Cookieminer
At the very beginning of 2019, CookieMiner appeared. He stole cryptocurrency cookies and passwords from Google Chrome. In addition to this, the cryptocurrency miner and backdoor are also installed in the system.
Experts say that CookieMiner is either based or written based on DarthMiner, which appeared in December 2018. DarthMiner was distributed under the guise of a crack for Adobe products.
Lazarus malware
The next malware is associated with the Lazarus organized group (APT), which has been aimed at cryptocurrency exchangers since 2018. Their backdoor was distributed using a special prepared Word document. Inside was a VBA script that could run on Windows or macOS. And this document was far from the only one. Judging by the names of the methods, the document was part of a long-running malicious campaign called Operation Troy.
OSX.Siggen - fake WhatsApp with a trojan
In April, the OSX.Siggen malware was detected, which was distributed under the guise of a WhatsApp application for computers. Users downloaded it from the domain message-whatsapp.com. The malicious application has been running on macOS since 10.8, which was released in 2012. To hide from the user's eyes, the application uses the standard mechanism for disabling the icon in the Dock. Being running OSX.Siggen gives attackers remote access to the victim’s computer. Probably the infected computer becomes part of the botnet.
OSX.Loudminer - cross-platform miner
Another example of how to download cracked software is not safe. This malware is approximately 2.5 GB in size. Because it is distributed along with the cracked version of the popular audio program Ableton Live. In this malicious application, there are attempts to hide “from prosecution” - if Activity Monitor is running on the computer (shows running processes and their activity), then the script suspends its activity for 15 minutes. For the mistake of installing a malicious user, the user will pay with the resources of his hardware, which will work for the benefit of the attackers.
KeyStealDaemon - password theft through vulnerability
I did not find information about how this malware was distributed (or maybe I didn’t look for it). But this is not particularly important. Importantly, this malware exploited vulnerability CVE-2019-8526, which was found in February and fixed in March . The vulnerability allows an unprivileged process to read secure password stores (KeyChain).
The malware appeared on virustotal in June and, apparently, was active at that time. But he could do his dirty work only on systems without updates or using the no longer supported macOS versions for which there was no fix (and probably will not). Yes, Apple systems also have security flaws and the company fixes them regularly. Therefore, you need to install updates not only on Windows.
OSX / Linker - zero day vulnerability in action
At the end of May, one researcher described an unpatched vulnerability that circumvented Gatekeeper, a component of the system that validates applications and prevents unsigned ones from starting. He reported the vulnerability to Apple in February, but the company did not manage to fix the error within 90 days (a de facto standard, although, for example, the Zero Day Initiative gives the development company 120 days ).
In mid-June, attackers took up the vulnerability. To activate the malware, the user only needs to mount the .dmg file. One of the first lures is the fake installer of the Adobe Flash Player plugin (I don’t know who still uses the flash and for what. If you know, share in the comments :)) Adobe Flash for some reason is very popular with distributors of advertising malware.
OSX / CrescentCore - Adware changes its tricks
The developers of this malware were trying to protect it from exposure. To do this, the malware contains two files inside the bundle: one with a list of software for virtualization, the other with a list of antiviruses. The idea was simple - if an antivirus was detected from the list or the application was launched inside a virtual machine, then take measures (for example, do not continue to work) so as not to be detected.
Malicious activity - launching unnecessary tasks that are open in the browser of windows with advertisements or fake warnings about virus infections.
Medical history
If you analyze the malware, you can identify the main trends in infection, the survival of malware and their goals.
Infection
Most often, infection of poppies occurs with the direct participation of users. For cheating apply
- fake pop-ups
- pirated software (it can be both the programs themselves and the cracks for them)
- infected websites (most often well-known programs infected with them are placed on them)
Survival
Some malware programs use unique methods to launch themselves, for example, associating with file extensions to be called when a user opens files. But most often, three methods are used.
- Launchd daemons or services (they start at system startup)
- browser extensions
- applications loading at user login (Startup Item)
Goals
There are only two main goals for malware - money or data. You can get all this in a direct way:
- (money) advertising, clicks, buyback
- (data) files, correspondence
either go the other way:
- (general) logins, passwords, code execution
Conclusion
Very often malicious users require the user to be active in order to run. According to Patrick Wardle (Patrick Wardle), this is a consequence of the fact that the malware for mac is not yet sufficiently developed. Regardless of how the malware for poppies develops, I would give users the following recommendations:
- Be careful, drop the stereotype about the security of apple devices.
- Periodically update the software - and the operating system, and installed applications. Updating is always the risk of breaking something, but the risk of losing time, money and data is also present. Alternatively, update after a few weeks, when other users step on the rake. But do not delay, otherwise it may be too late.
- Do not install software unnecessarily. Extra software is an additional opportunity for attack, an additional way to catch the infection.
Thanks for attention. All health and good luck! Welcome to the comments.