
Today we will describe the real workflow that the Varonis Incident Response Team uses to investigate brute force attack attacks (hereinafter referred to as brute force attacks) through NTLM. These attacks are quite common, and our team often encounters them with customers around the world.
Detection
If you see any of these alerts in the Varonis dashboard, you might be exposed to a brute force attack via NTLM:
- Password spraying from a single source
- Account enumeration via NTLM
- Multiple account lockouts

You can also search for all failed authentication attempts in the Varonis dashboard to find suspicious activities that need to be investigated.
1. Initial investigation at the Varonis interface
Click Analytics in the Varonis dashboard.
In the Servers drop-down list, select DirectoryServices.
For the filter type by Event Type, select “Account Authentication”. As a result, you will get a selection of events related to login attempts for a given time period.
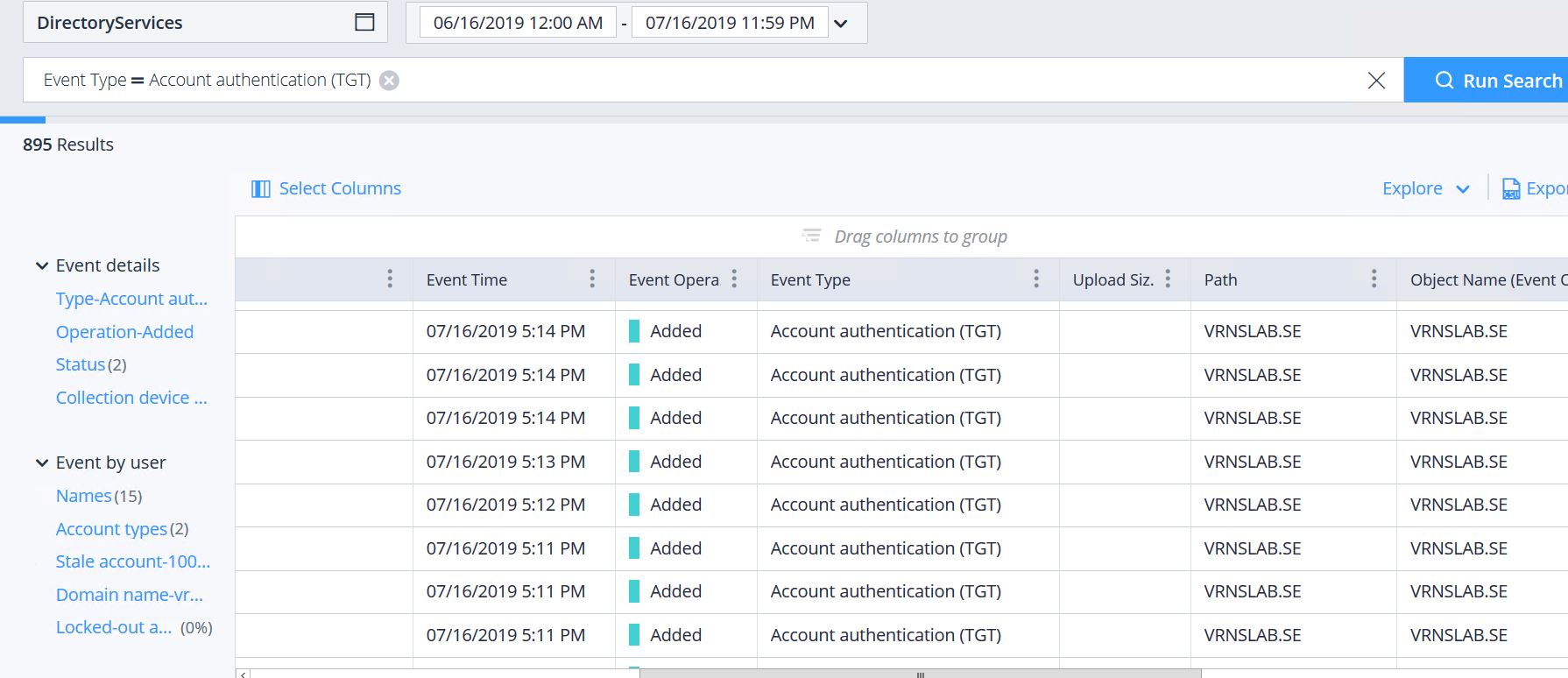
Look for unsuccessful login attempts for unknown users that may indicate a dictionary attack by common account names such as “administrator” or “service”. Varonis displays accounts such as “Abstract / Nobody” (in the highlighted field User Name (Event By)) because they do not exist in Active Directory and cannot be matched.
In the “Device Name” column, you will most likely see the disguised name of the machine used for authentication requests. You probably won’t know this machine, and its name will not comply with the corporate device naming policy. Attackers often use device names such as “workstation” or “mstsc” in the hope of hiding their activity. Sometimes they leave the device name completely blank.

If you determine that a brute force attack through NTLM really has a place to be, you need to delve deeper into the logs.
Search for all failed login attempts through NTLM using the following filters:
- event description 'contains' NTLM
- event Status = Fail
- event Type = TGT Authentication
Look for all successful authentications by device names used by cybercriminals to verify that at the moment there are no direct signs of successful account compromise. Record the value of the “Collection Device Hostname” field for the events being analyzed. This is the name of the domain controller from which to start the next phase of the investigation.
2. Preparing an NTLM Audit
Highlight Default Domain Policy so that we can later receive events from all domain controllers.
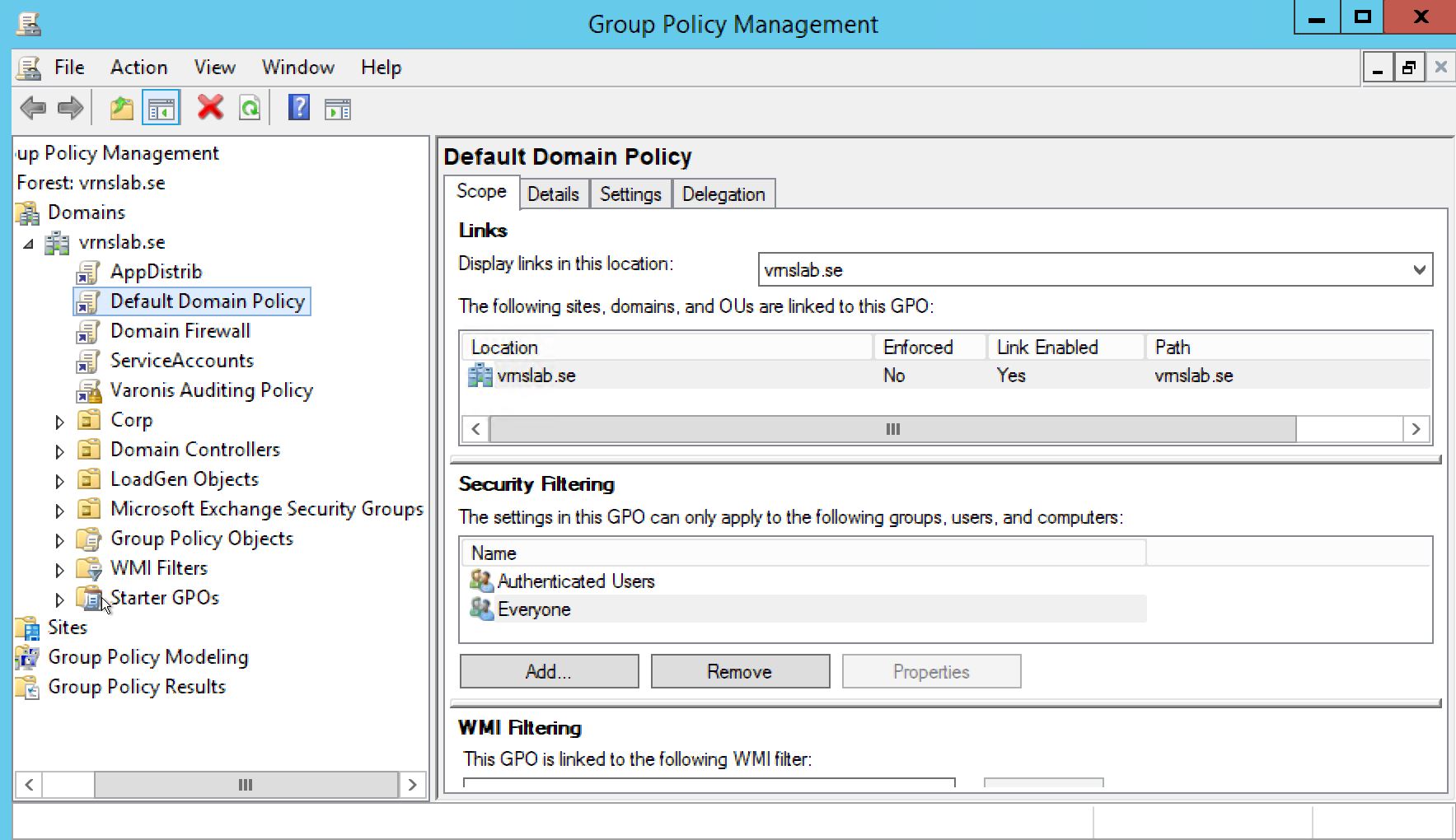
Right-click on Default Domain Policy and select Edit.
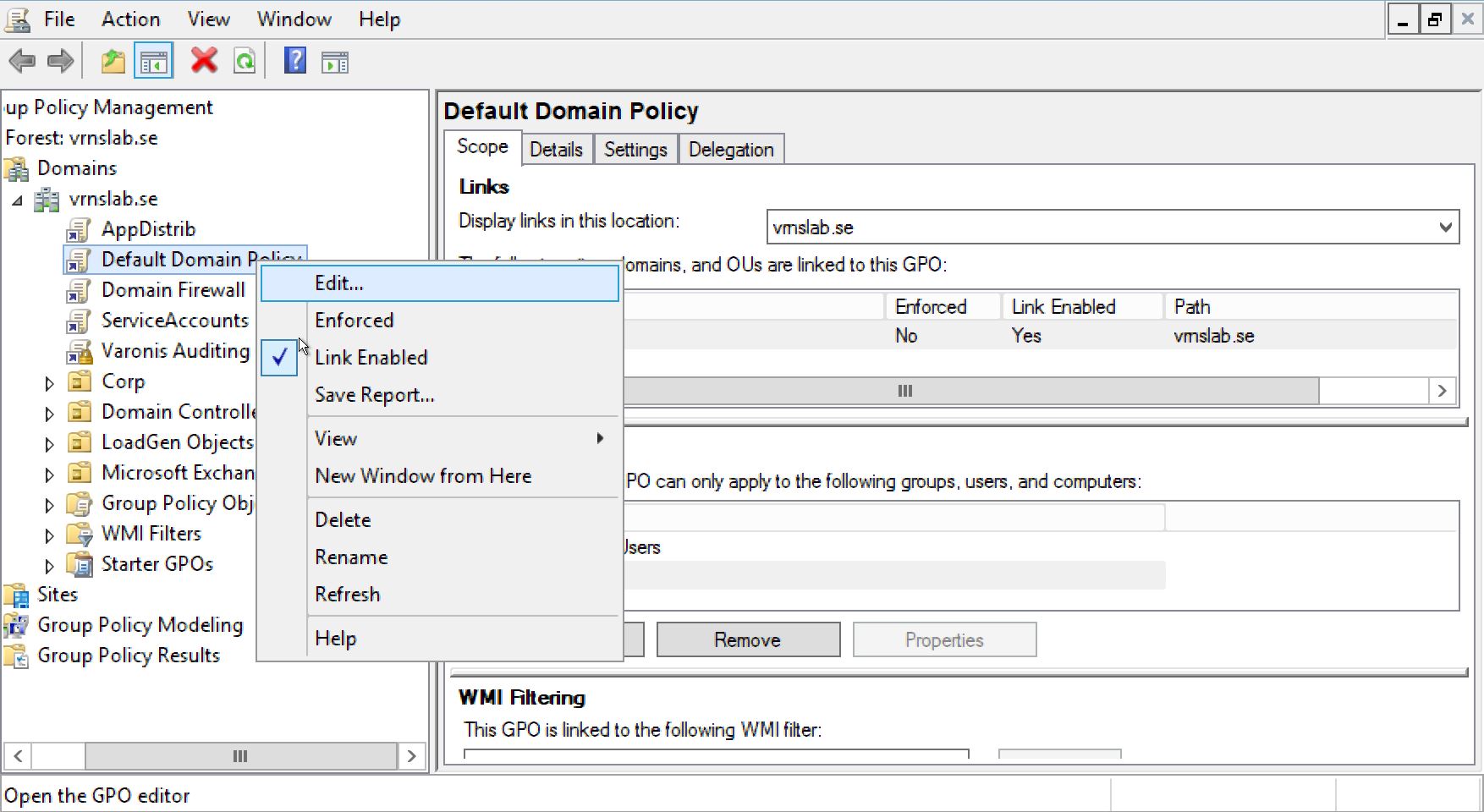
The Group Policy Management Editor window opens. Expanding the hierarchy, select Security Options.
Change the following values:
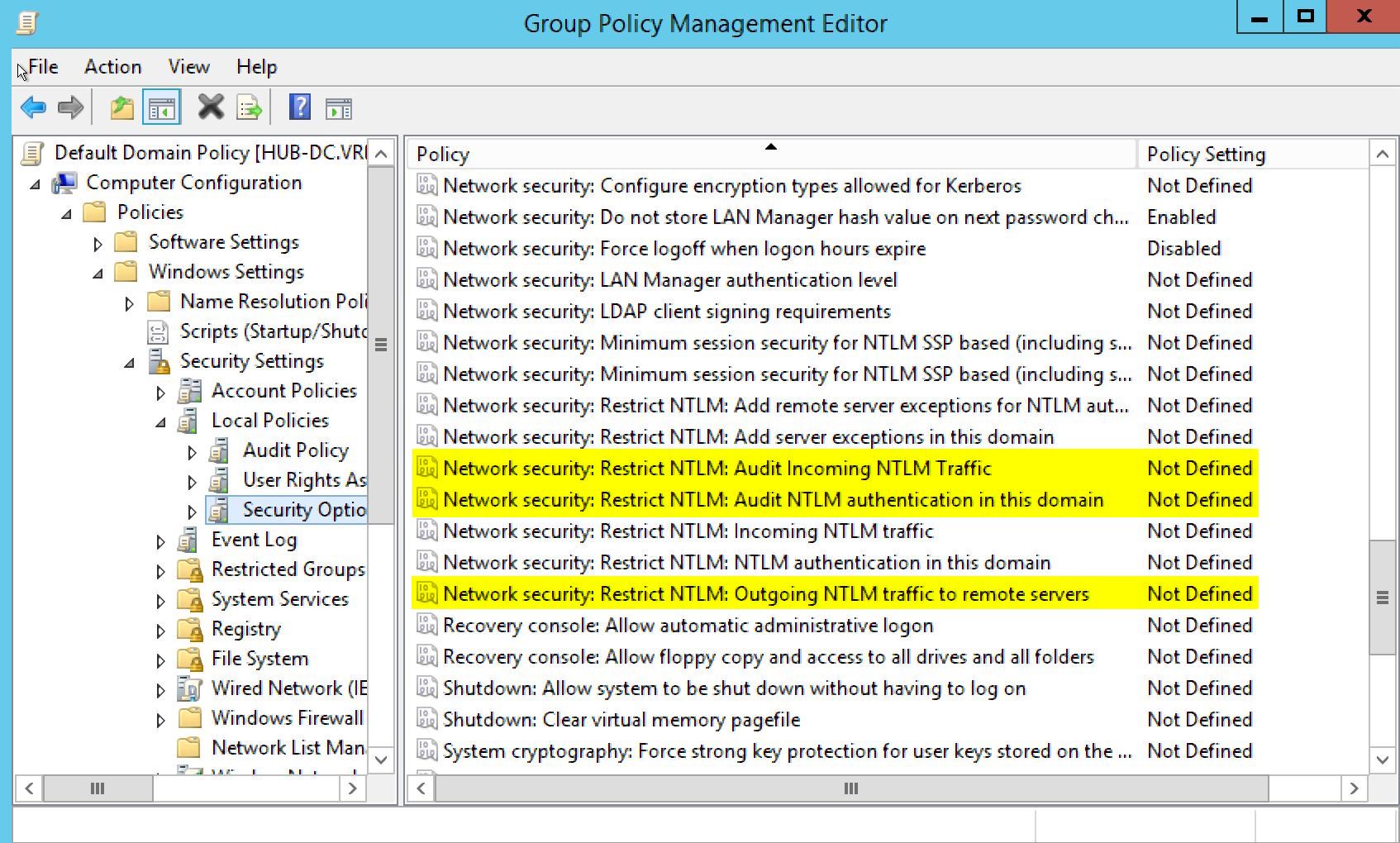
- Network security: Restrict NTLM: Audit Incoming Traffic = Enable auditing for all accounts
- Network security: Restrict NTLM: Audit NTLM authentication in this domain = Enable all
- Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers = Audit all
Run the gpupdate / force command to apply the changes.
3. NTLM Log Investigation
Go to the domain controller identified through the “Collection Device Hostname” column in step 1.
Run the Event Viewer (eventvwr command in cmd) and expand the hierarchy to the Application and Services Logs> Microsoft> Windows> NTLM> Operational log. Right-click on the specified log, select Properties and increase the log size to at least 20 MB (default size is 1 MB).
Events with Event ID = 8004 will mostly be associated with malicious authentication attempts.
Look in the log using the names of devices or users that we saw in step 1. In the events found, pay attention to the “Secure Channel Name” field. This is the name of the device under attack.
Important Notice
In the NTLM event log, you will see only new events that began to arrive since the inclusion of audit in paragraph 2
4. Remedy
Once we have identified the name of the attacked device, we can find out how the attacker sends these authentication attempts. In the firewall logs, check for connections during malicious authentication attempts. On the device under attack, you can use the netstat command or the Wireshark utility. Thus, we look for the IP address and port that the attacker uses to send authentication requests.
As soon as we receive this information, we can take measures to prevent hostile activity - block the IP address or close the port.
Important Notice
There is a chance of infection of the attacked device. Be careful!
Finally, in order to complete the investigation, we need to check all the actions for authenticating user accounts on the attacked device, as well as activity on the observed data sources from the attacked device and any other notifications coming from the attacked device. We need to look at the Varonis and NTLM logs to make sure authentication attempts are stopped, and continue to monitor new activity.
The Varonis team in Russia conducts a free cybersecurity analysis and risk audit of IT infrastructure. To do this, leave a request on the website or contact us in a convenient way.