Foreword
This text will be one of the rewritten chapters for the training manual on information protection of the Department of Radio Engineering and Control Systems, as well as, from this training code, the Department of Information Protection of the MIPT (GU). The full tutorial is available on github (see also draft releases ). On Habrir I plan to upload new "big" pieces, firstly, to collect useful comments and observations, and secondly, to give the community more overview material on useful and interesting topics. Previous sections of the Cryptographic Protocols chapter: 1 , 2 , 3 , 4
Key distribution schemes with a trusted center consist of three steps.
- At the first stage, the trusted center creates a secret known only to him. This may be some secret matrix with special properties, as in the Blom scheme, or a pair of private and public keys, as in the Giraud scheme.
- For each new legal member of the network, the trusted center, using its secret information, produces a fingerprint or certificate that allows the new member to generate session keys with other legal participants.
- Finally, at the third stage, when the protocol of communication between the two legal participants begins, they present identifiers and / or additional information from the trusted center to each other. Using it, without additional access to the center, they can generate a secret session key for communication with each other.
Giro scheme
In the Giraud scheme ( French: Marc Girault ), reliability is built on the strength of the RSA cryptosystem (the difficulty of factorizing large numbers and computing a discrete root).
Preliminary:
- Trust Center (Trent, ):
- selects a common module where and - large prime numbers;
- selects a pair of private and public keys and ;
- selects an item fields maximum order;
- publishes schema parameters in a public place , and .
- Each of the legal participants:
- chooses a private key and id ;
- computes and sends to a trusted center ;
- Using the parties authentication protocol (see below), the legal participant proves to the trusted center that he owns the private key without disclosing its meaning;
- receives its public key from the trusted center:
As a result, for each participant, for example, Alice, who owns The statement will be executed:
The authentication protocol of the parties in the general case is as follows.
- Alice picks a random .
- Bob picks random .
- Bob is calculating ;
Bob checks that .
The protocol for generating a session key, or just a Giraud scheme , like other schemes, consists of passes for exchanging open information and calculating a key.
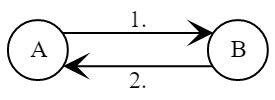
- Bob is calculating .
- Alice calculates .
As a result of the operation of the circuit, the parties generated the same common session key.
The scheme provides key authentication (target G7), since only legitimate users can calculate the correct value for the shared session key.
Blom's scheme
The Rolf Blom scheme is used in the HDCP protocol ( English High-bandwidth Digital Content Protection ) to prevent copying of high-quality video signal. It is assumed that some trusted center will distribute the keys in such a way that legal manufacturers of video cards, high-resolution monitors and other components will transmit video content through a secure channel, and pirated devices will not be able to intercept this data, and, for example, write to another medium.
At the initialization stage, the trusted center selects a symmetric matrix over the final field . To join the key distribution network, a new participant either independently or through a trusted center selects a new public key (identifier) representing a length vector above . The trusted center calculates the private key for the new member :
The symmetry of the matrix Trusted Center allows any two network participants to create a shared session key. Let Alice and Bob be legal network users, that is, they have public keys and respectively, and their private keys and were calculated by the same trusted center using the formula above. Then the protocol for generating a shared secret key is as follows.
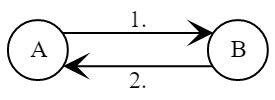
- Bob is calculating .
- Alice calculates .
From the symmetry of the matrix it follows that the values and coincide, they will be the common secret key for Alice and Bob. This secret key will be unique for each pair of legal network users.
The accession of new participants to the scheme is strictly controlled by a trusted center, which allows you to protect the network from illegal users. The reliability of this scheme is based on the inability to restore the original matrix. However, to restore the matrix of the trusted center of size necessary and enough pairs of linearly independent public and private keys. In 2010, Intel, which is the “trusted center” for users of the HDCP security system, confirmed that cryptanalysts managed to find a secret matrix (more precisely, similar to it) used to generate keys in the mentioned system to prevent copying of high-quality video signal.
Afterword
The author will be grateful for factual and other comments on the text.