BLACK HAT USA Conference. Get rich or die: make money on the Internet using Black Hat. Part 2
They went so far as to discuss the possibility of bringing UPS drivers to a confrontation with a suspect. Let's check now if what is quoted on this slide is legal.

Here is what the FTC Federal Trade Commission answers to the question: “Do I have to return or pay for the product that I never ordered?” - “No. If you received a product that you didn’t order, you have the legal right to accept it as a free gift. ” Does this sound ethical? I wash my hands because I'm not smart enough to discuss such issues.
But interestingly, we see a trend in which the less technology we use, the more money we get.
Affiliate Internet Fraud
Jeremy Grossman: It is really very difficult to understand, but in this way you can get a six-figure amount of money. So, for all the stories that you heard, there are real links, and you can read in detail about all this. One of the most interesting types of online fraud is affiliate fraud. Online stores and advertisers, through affiliate networks, drive traffic and users to their sites in exchange for a portion of the profit generated from this.
I'm going to talk about what a lot of people have known for many years, but I could not find a single public link that would indicate how many losses this type of fraud caused. As far as I know, there were no lawsuits, no criminal investigations. I spoke with entrepreneurs engaged in production, I spoke with guys from affiliate networks, I spoke with Black Cats - all of them are sure that scammers made a huge amount of money from the partnership.
I ask you to take my word for it and get acquainted with the result of the “homework” that I completed on these specific problems. On them, scammers “weld” 5-6-digit, and sometimes seven-figure amounts monthly, using special techniques. There are people in this room who can verify this if they are not bound by a confidentiality agreement. So, I'm going to show you how it works. Several players are involved in this scheme. You will see what a new generation of partner games is.

A merchant who has a website or product participates in the game and pays partners a commission for user clicks, created accounts, purchases, and so on. You pay a partner that someone visits his website, clicks a link, goes to your seller’s website and buys something there.
The next player is a partner who receives money in the form of payment for each click (CPC) or in the form of a commission (CPA) for redirecting buyers to the seller’s website.
Commissions imply that as a result of the partner’s activities, the customer made a purchase on the seller’s website.
A buyer is a person who makes purchases or subscribes to a seller’s stock.
Affiliate networks provide technologies that integrate and track the activities of the seller, partner and buyer. They "glue" all the players together and provide their interaction.
You may need a few days or a couple of weeks to understand how this all works, but there are no complicated technologies. Affiliate networks and affiliate programs cover all types of trade and all markets. Google, EBay, Amazon have them, their interests of commissioners intersect, they are everywhere and do not lack income. I’m sure that you know that even the traffic from your blog is capable of generating several hundred dollars in monthly profits, so this scheme will be easy for you to understand.
Here's how the system works. You affiliate a small site, or an electronic bulletin board, it does not matter, sign an affiliate program and get a special link that you place on your web page. She looks like this:
<a href=”http://AffiliateNetwork/p? program=50&affiliate_id=100/”>really cool product!</a>
Here is a specific affiliate program, your affiliate ID, in this case it is 100, and the name of the product being sold. And if someone clicks on this link, the browser sends it to the affiliate network, sets up special tracking cookies, linking it to the affiliate ID = 100.
Set-Cookie: AffiliateID=100
And redirects to the seller’s page. If later the buyer purchases some product during the period of time X, which can be day, hour, three weeks, any agreed time, and all this time cookies continue to exist, then the partner receives his commission.
This is what the scheme is, thanks to which affiliate companies earn billions of dollars using effective SEO tactics. I will give an example. The next slide shows the check, now I’ll increase it to show you the amount. This is a check from Google for 132 thousand dollars. The name of this gentleman is Schumann, he owns a network of advertising websites. This is not all the money, Google pays such amounts once a month or once every 2 months.

Another check from Google, I will increase it, and you will see that it is issued in the amount of 901 thousand dollars.

Should I ask someone about the ethics of such ways of earning? Silence in the hall ... This check is a 2-month payment because the previous check was rejected by the beneficiary's bank due to too much payment.
So, we made sure that such money can be made, and this money is paid. How can you beat this scheme? We can use a technique called Cookie-Stuffing, or “Stuffing for Cookies.” This is a very simple concept that appeared in 2001-2002, and this slide shows how it looked in 2002. I will tell you the story of its appearance.
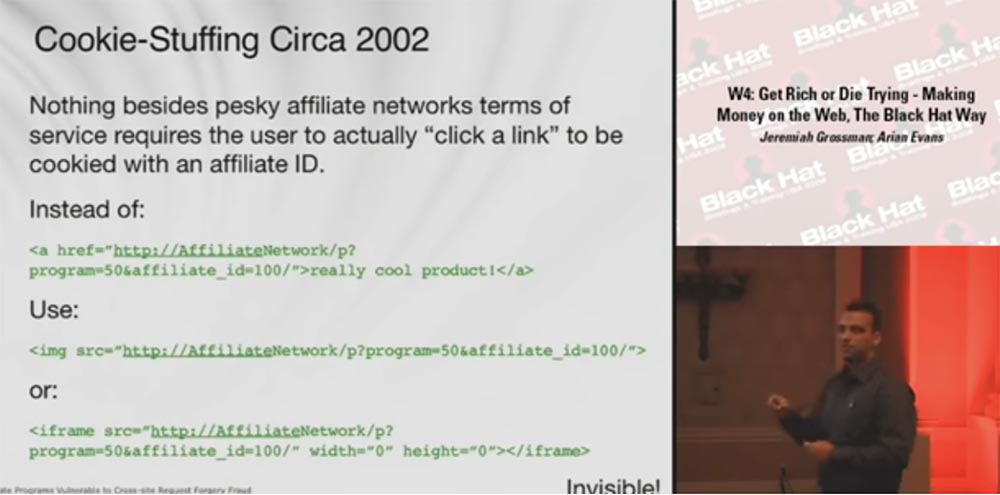
Nothing but the annoying service conditions of affiliate networks requires that the user really clicks the link in order for his browser to pick up cookies with the affiliate ID.
You can automatically download this URL, which the user usually clicks on, into the image source or in the iframe tag. Moreover, instead of the link:
<a href=”http://AffiliateNetwork/p? program=50&affiliate_id=100/”>really cool product!</a>
You load this:
<img src=”http://AffiliateNetwork/p?program=50&affiliate_id=100/”>
Or that:
<iframe src=”http://AffiliateNetwork/p?program=50&affiliate_id=100/” width=”0” height=”0”></iframe>
And when the user gets to your page, he will automatically pick up affiliate cookies. At the same time, regardless of whether he will buy something in the future, you will receive your commission, you redirected traffic or not - it does not matter.
Over the past few years, this has become the entertainment of SEO guys who post similar material on bulletin boards and develop all kinds of scripts, where else to post their links. Aggressive partners realized that they can post their code anywhere on the Internet, and not just on their own sites.
On this slide, you see that they have their own Cookie-Stuffing programs that help users make their “cookies filled." And this is not one cookie, you can download 20-30 identifiers of affiliate networks at the same time, and as soon as someone buys something, you get paid for it.
Soon, these guys realized that they might not post this code on their pages. They refused cross-site scripting and simply began to post their small snippets with HTML code on message boards, guest books, and social networks.

By about 2005, merchants and affiliate networks figured out what was going on, started tracking referrers and clickthrough rates, and began to kick out suspicious partners. For example, they noticed that the user clicks on the MySpace site, but this site belongs to a completely different affiliate network than the one that receives legitimate benefits.
These guys got a little wiser, and in 2007 a new kind of cookie-stuffing appeared. Partners began to place their code on SSL-pages. According to the Hypertext Transfer Protocol RFC 2616, clients should not include the Referer header field in an insecure HTTP request if the referring page was migrated from a secure protocol. This is because you do not want to leak this information from your domain.
From this it is clear that no Referer sent to the partner can be tracked, so the main partners will see an empty link and will not be able to kick you out for this. Now the scammers have the opportunity to make their “stuffed cookies" with impunity. True, not every browser allows you to do this, but there are many other ways to do the same, using automatic updating of the current browser page meta-refresh, meta tags or JavaScript.
In 2008, they began to use more powerful hacker tools, such as re-binding attacks - DNS rebinding, Gifar and malicious Flash content, which could completely destroy existing protection models. It takes some time to figure out how you can use them, because the guys involved in cookie-stuffing are not very advanced hackers, they are just aggressive marketers who are poorly versed in writing codes.
Sale of semi-available information
So, we looked at how to earn 6-digit amounts, and now let's move on to seven-digit ones. We need big money to get rich or die. We will look at how you can make money by selling semi-available information. Business Wire was very popular a couple of years ago, and it still remains important, we see its presence on many sites. For those who do not know - Business Wire provides a service consisting in the fact that registered users of the site receive a stream of relevant press releases from thousands of companies. Press releases are sent to this company by various organizations, which are sometimes temporarily prohibited or embargoed, so the information in these press releases may affect the value of the shares.
Press release files are uploaded to the Business Wire web server, but do not link until the embargo is lifted. All this time, press release web pages are linked to the main website, and users are notified of them by URLs of this kind:
http://website/press_release/08/29/2007/00001.html http://website/press_release/08/29/2007/00002.html http://website/press_release/08/29/2007/00003.htm
Thus, while you are under the embargo, you post interesting data on the site so that as soon as the embargo is lifted, users immediately familiarize themselves with them. These links are dated and emailed to users. As soon as the ban expires, the link will work and will direct the user to the site where the corresponding press release is posted. Before providing access to the press release web page, the system must make sure that the user has logged into the system legally.
They do not check whether you have the right to familiarize yourself with this information before the deadline for the embargo, you only need to log in to the system. It seems harmless for now, but if you don’t see something, it doesn’t mean that he is not there.

Lohmus Haavel & Viisemann, an Estonian financial company, not hackers at all, discovered that the press release web pages were named in a predictable way and began to guess these URLs. While links may not yet exist because the embargo is in effect, this does not mean that the hacker cannot guess the file name and thus get access to it prematurely. This method worked because the only Business Wire security check was that the user logged in legally, and nothing more.
Thus, Estonians received information before the market closed, and sold this data. Until the SEC tracked them down and froze their accounts, they managed to earn $ 8 million from trading semi-available information. Think about the fact that these guys just looked at how the links looked, tried to guess the URLs and made 8 million on it. Usually at this point I ask the audience whether it is considered legal or illegal, whether it refers to the concepts of trade or not. But now I just want to draw your attention to who did it.
Before you try to answer these questions, I will show you the next slide. This is not directly related to online fraud. A Ukrainian hacker hacked Thomson Financial, a provider of business intelligence, and stole IMS Health’s financial distress a few hours before it was supposed to enter the financial market. The fact that he is guilty of hacking is beyond doubt.
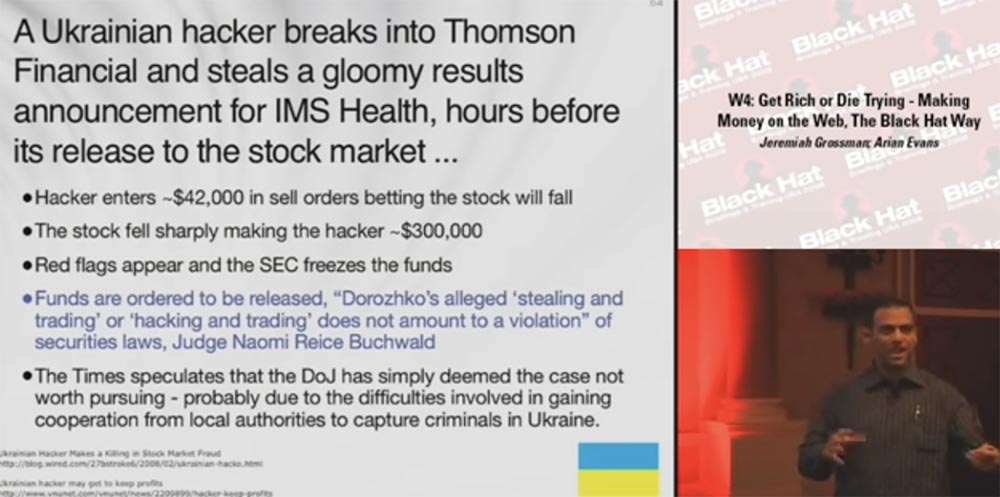
The hacker placed sell orders in the amount of 42 thousand dollars, playing before falling bets. For Ukraine, this is a huge amount, so the hacker knew well what he was doing. A sudden drop in stock prices brought him for several hours about 300 thousand dollars in profit. The exchange posted a Red Flag, the SEC froze funds, noting that something was going wrong, and the investigation began. However, Judge Naomi Reis Buchwald stated that the funds should be unfrozen, as “theft and trade” and “hacking and trade” attributed to Dorozhko do not violate securities laws. The hacker was not an employee of this company, so he did not violate any laws on the disclosure of confidential financial information.
The Times suggested that the US Department of Justice simply considered the case unpromising because of the difficulties involved in obtaining the consent of the Ukrainian authorities to cooperate in the capture of the criminal. So this hacker got 300 thousand dollars very easily.
Now compare this to the previous case when people made money simply by changing the URLs of the links in their browser and selling commercial information. These are quite interesting, but not the only ways to make money on the stock exchange.
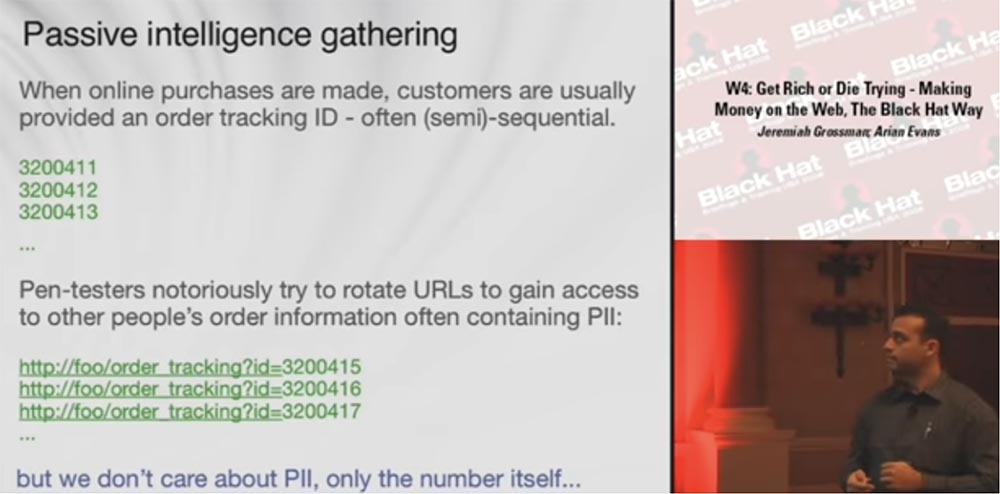
Consider passive information gathering. Usually, after making an online purchase, the buyer receives a track code for the order, which can be sequential or pseudo-serial and looks something like this:
3200411
3200412
3200413
With it, you can track your order. Pentesters or hackers try to “scroll” the URLs to access the data of the order, usually containing personal information (PII):
http://foo/order_tracking?id=3200415 http://foo/order_tracking?id=3200416 http://foo/order_tracking?id=3200417
Scrolling through the numbers, they get access to credit card numbers, addresses, names and other personal information of the buyer. However, we are not interested in the personal information of the client, but the track code of the order itself, we are interested in passive intelligence.
The art of drawing conclusions
Consider the "Art of drawing conclusions." If you can accurately estimate how many “orders” the company processes at the end of the quarter, then, based on historical data, you can conclude whether its financial affairs are good and in which direction the value of its shares will fluctuate. For example, you ordered or bought something at the beginning of the quarter, it does not matter, and then made a new order at the end of the quarter. According to the difference in numbers, we can conclude how many orders were processed by the company during this period of time. If we are talking about a thousand orders against a hundred thousand over the same past period, you can assume that the company's affairs are bad.
However, the fact is that often these serial numbers can be obtained without actually fulfilling the order or the order, which was subsequently canceled. I hope that these numbers will not be displayed in any case and the sequence will continue from the numbers:
3200418
3200419
3200420
Thus, you know that you have the opportunity to track orders, and you can begin to passively collect information from the site that they provide to us. We do not know whether this is legal or not, we only know that it can be done.
So, we have examined the various flaws of the business logic.
Trey Ford: the attackers are businessmen. They are counting on the return on their investment. The more technology, the more and more complex the code, the more work you need to do and the more likely it is to be caught. But there are many very beneficial ways to carry out attacks without any effort. Business logic is a gigantic business, and there is tremendous motivation for criminals to break it. The disadvantages of business logic are the main goal of criminals and this is something that cannot be detected by simply running a scan or conducting standard testing in the quality assurance process. There is a psychological problem in QA quality assurance, which is called the “propensity to confirm one’s point of view”, because, like any other people, we want to know that we are right. Therefore, it is necessary to conduct testing in real conditions.

It is necessary to test everything and everything, because not all vulnerabilities can be detected at the development stage by analyzing the code, or even during QA. So you need to go through the entire business process and develop all measures to protect it. Much can be learned from history because some types of attacks are repeated over time. If you are woken up one night due to a peak load on the processor, then you can assume that some hacker is again trying to find valid discount coupons. The real way to recognize the type of attack is to observe the active attack, because recognizing it based on the log history will be an extremely difficult task.
Jeremy Grossman: So that's what we learned today.

Guessing the captcha can bring you a four-digit amount in dollars. Manipulating online payment systems will bring a five-figure profit to the hacker. Hacking banks can bring you more than five-digit profit, especially if you do this more than once.
E-commerce fraud will give you a six-figure sum of money, and using affiliate networks will give you a 5-6-digit or even seven-digit profit. If you are brave enough, you can try to fool the stock market and get more than seven-figure profit. And using the RSnake method in competitions for the best chihuahua is simply priceless!
Most likely, the new slides of this presentation did not appear on the CD, so you can download them later from my blog page. The OPSEC conference is due to take place in September, in which I am going to participate, and I think that we will be able to create some really cool things together with them. And now, if you have any questions, we are ready to answer them.
A bit of advertising :)
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, cloud VPS for developers from $ 4.99 , a 30% discount for Habr users on the unique entry-level server analog that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share a server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?