There is a site called Hire2Hack, which also accepts applications for the "recovery" of passwords. Here, the cost of the service starts at $ 150. I do not know about the rest, but you must provide them with information about yourself, because you are going to pay them. To register, you must specify a username, email, password, and so on. The funny thing is that they accept even Western Union transfers.
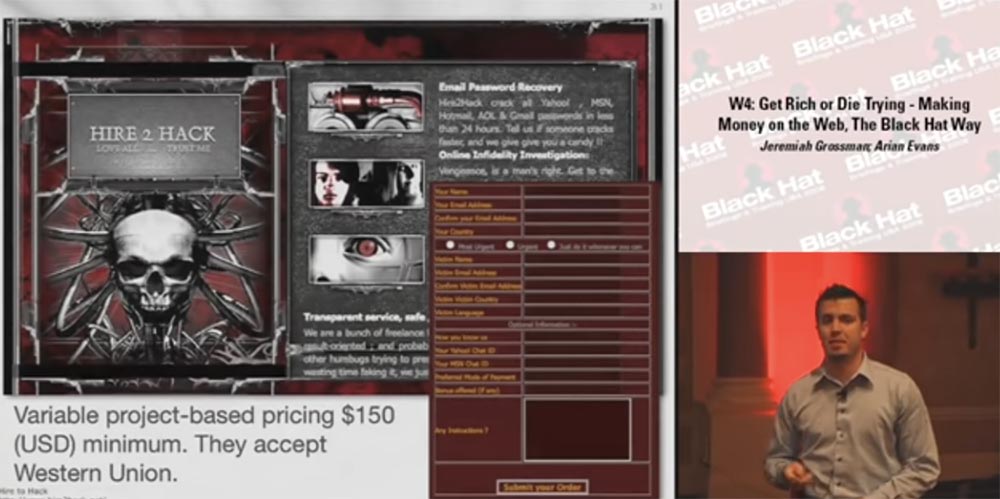
It is worth noting that usernames are very valuable information, especially when they are tied to an email address. Tell me, which of you indicates your real name when registering a mailbox? Nobody, this is fun!
So, email addresses are valuable information, especially if you shop online or want to track the affair of a spouse hanging on a dating site. If you are a seller, you can use email addresses to check which of your customers or your subscribers currently use the services of any of your competitors.
Therefore, phishing attackers pay a lot of money for real user addresses. In addition, they use windows to recover passwords and logins to mine valid email addresses using temporary attacks. Many large e-commerce and social media portals see the theft of valid email addresses as a problem that can do a lot of damage since interesting research has been published. So we must fight on two fronts - against timing attacks and against information leaks of this kind.
Turning electronic coupons into money
Jeremy Grossman: So, we looked at three methods of online fraud and are now raising rates. The next way is monetizing eCoupons electronic coupons. These coupons are used for online purchases. The customer enters his unique ID, and a discount is applied to his purchase. Large online merchants offer customers a discount program that has been supported by AmEx.
Many of you know that coupons offer a discount of a few to a couple hundred dollars and are equipped with a 16-digit ID. These numbers are very static and usually go in order. At first, only one coupon was allowed to be applied to one order, but then, as the program grew in popularity, these restrictions were removed, and now more than 3 coupons can be used with one order.
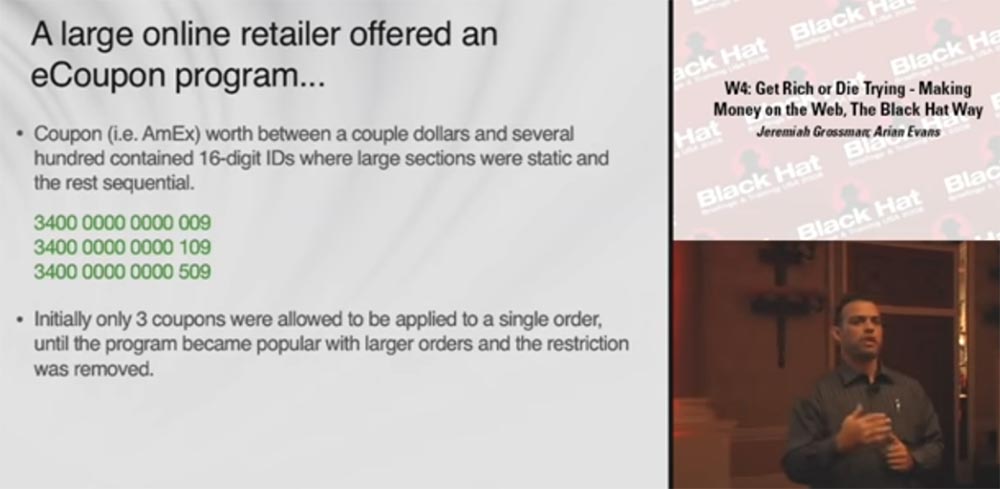
Someone has developed a script that tries to determine the thousands of possible valid discount coupons. Sellers are known for orders worth more than 50 thousand dollars, which instead of money were paid with 200 or more coupons. Agree, this is a good Christmas present!
The problem went unnoticed for a long time, because the program worked perfectly, everyone used coupons and everyone was happy. This continued until the program load planning system detected a 90% increase in processor load at a time when people “scrolled” the ID numbers, choosing the ones that offered a discount.
Merchants asked the FBI to investigate this case, as they suspected something was amiss. But the problem was that the goods were sent to a non-existent address, and this confused them. It turned out that the attacker entered into a conspiracy with the delivery service, which “intercepted” the goods in advance.
In this case, the interesting thing is that coupons are not currency, they are only marketing tools. However, errors in business logic led to the need to attract the Secret Service, which also faced with fraud by the delivery service that used the system to its advantage.
Earnings on fake accounts
Trey Ford: This is one of my favorite stories. “Real Life: Hacking the Office Space.” I think you saw a movie about hackers, "Office Space." Let's figure this out. How many of you have used online banking?

Well, everyone admitted that they used. There is one interesting thing - the ability to pay bills online via ACH. The ACH Automated Settlement Chamber works like this. Suppose I want to buy a car from Jeremy and am going to transfer money directly from my account to his account. Before I make the main payment, my financial institution must make sure that everything is fine with us. Therefore, at first the system transfers a tiny amount, from a few cents to $ 2, to check that the financial accounts and routing addresses of the parties are in order and the client received this money. After they are convinced that this transfer has been completed normally, they are ready to forward the full payment. You can talk about whether this is legal, whether it is consistent with the terms of the user agreement, but tell me which of you has a PayPal account? How many people have multiple PayPal IDs? This is probably quite legal and complies with Terms & Conditions.
Now imagine that this mechanism can be used to make a lot of money. We are talking about using the effect of creating, say, 80 thousand such accounts by setting up a simple script. The only thing you need to pay attention to is that we started our story with the use of a local proxy, RSnake script, another hacker tool that should help us make money, but now we are going to come back and show how to make hacking a lot easier so that you could use only a browser to earn money.
This particular attack is individual. California-based 22-year-old Michael Largent used a simple script to create 58,000 fake brokerage accounts. He opened them in the systems of Schwab, eTrade and some others, assigning the names of cartoon characters to the fake users of these accounts.

For each of these accounts, he used only a test translation using the ACH system, without making a full transfer of funds. But he owned a general account on which all these verification tools flocked, and then transferred them to himself. It sounds good - it’s not a lot of money, but in total they brought him a very substantial income. That's how he made money, following the idea of the film "Office Space". The most interesting thing is that there is nothing illegal - he simply collected all these tiny amounts, but did it very quickly.
He earned $ 8,225 on Google Checkout, another $ 50,225 on eTrade and Schwab. Then he withdrew this money to a credit card and appropriated it. When the bank discovered that all these thousands of accounts belong to one person, the bank employees called him and asked why he did this, does he not understand that he is stealing money? To which Michael replied that he did not understand and did not know that he was committing something illegal.
This is a very good way to build new relationships with people from the Secret Service who follow you everywhere and want to learn more about you. I repeat once again - the funniest thing about this scheme is that there was nothing illegal here. He was detained on the basis of the Patriot Act, the "Patriotic Act." Who knows what the Patriotic Act is?
That's right, this is a law expanding the powers of special services in the field of countering terrorism. This guy used cartoon and comic names, so they were able to detain him for using fake user names. So those present who use fictitious names for their mailboxes should be careful - this can be declared illegal!
The Secret Service accusation was based on four points: computer fraud, Internet fraud and mail fraud, but the act of receiving money was recognized as completely legal, since he used a real account. I can’t say whether it was done correctly or not, ethically or not ethically, but basically everything that Michael did was in accordance with the Terms & Conditions given on the websites, so maybe it was just such an additional function.
Hacking banks through ASP
Jeremy Grossman: you know, I travel a lot, and I meet people who are technically savvy or vice versa, not at all versed in technology. And when we talk about life, they ask where I work. When I answer that I am engaged in information security, they ask what it is. I explain, and then they say: "Oh, so you can crack the bank!"
So, when you start explaining how you can really hack a bank, you mean hacking through ASP financial application providers. Application Service Providers are companies that rent their own software and hardware to their customers - banks, credit unions, and other financial companies.

Their services are used by small banks and similar companies that are not financially profitable to have their own “software” and “hardware”. Therefore, they rent ASP facilities, paying them monthly or every year.
ASPs enjoy the increased attention of hackers, because instead of hacking one bank, they can immediately crack 600 or a thousand banks. So ASPs are a very interesting goal for bad guys.
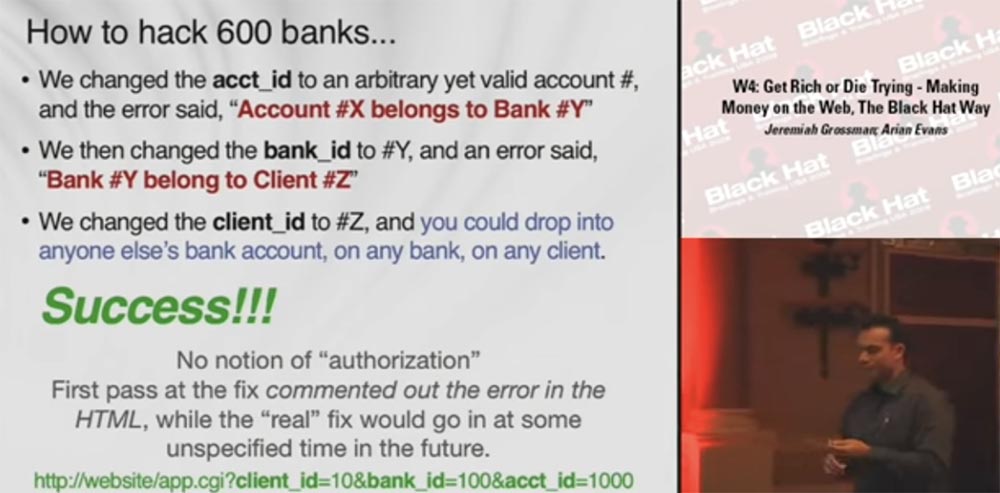
So, ASP companies serve a whole bunch of banks on the basis of three most important URL parameters: client identifier client_ID, bank identifier bank_ID and account identifier acct_ID. Each ASP client has its own unique identifier that can potentially be used on several banking sites. Each bank can have any number of user accounts for each financial application - a savings system, an account verification system, a payment system, and so on, and each financial application has its own ID. Moreover, each client account in this application system also has its own ID. Thus, we have three account systems.
So, how do we hack 600 banks at the same time? First of all, we look at the end of a line of a URL of this type: website / app.cgi? Client_id = 10 & bank_id = 100 & acct_id = 1000 and try to replace acct_id with an arbitrary value #X, after which we get a large, highlighted in red error message with the following content: “ Account #X belongs to Bank #Y ”(account #X belongs to bank #Y). Next, we take bank_id, change it in the browser to #Y and get the message: “Bank #Y belong to Client #Z” (bank #Y belongs to client #Z).
Finally, we take client_id, assign it #Z - and you're done, we get into the account we originally wanted to get into. After we have successfully cracked the system, we can get into any other bank account, or bank, or client account in the same way. We can get to every account in the system. There is no sign of authorization at all. The only thing they check is that you are logged in under your ID, and now you can freely withdraw money, make a transfer, and so on.
One day, one of our clients, not ASP, forwarded our information about this vulnerability to another client who used ASP and informed them that there was a problem that needed to be fixed. We told them that it would probably be necessary to rewrite the entire application in order to enter authorization and the system would check if the client has the right to make financial transactions and that it will take some time.
Two days later, they sent us an answer in which they reported that they had already fixed everything themselves - they corrected the URL so that the error message no longer appears. Of course, it was cool, and we decided to look at the source code to see what they did using their "great" hacker technique. So, all that was done was to stop displaying the error message in HTML format. In general, we had a very interesting conversation with this client. They said that since they were unable to solve this problem quickly, they decided to do so for now, hoping to completely fix the vulnerability in the distant future.
Reverse money transfer
Another method of fraud, which I will talk about very briefly, is a reverse money transfer. This operation is performed in many banking applications. When transferring $ 10,000 from account A to account B, the operation formula should logically work like this:
A = A - ($ 10,000)
B = B + ($ 10,000)
That is, $ 10,000 is withdrawn from account A and added to account B.
Interestingly, the bank does not check whether you enter the correct transfer amount. For example, you can replace a positive number with a negative one, that is, transfer _10000 $ from account A to account B. In this case, the transaction formula will look like this:
A = A - (- $ 10,000)
B = B + (- $ 10,000)
That is, instead of debiting funds from account A, they will be debited from account B and credited to account A. This happens from time to time and brings interesting results. At the bottom of this slide, you see a link to a Breaking the Bank (Vulnerabilities in Numeric Processing within Financial Applications) research article.
It describes similar things that happen with rounding errors. This Corsaire article has a lot of interesting things that have served us as material for some of our own solutions.
But back to the previous problem. We contacted ASP security and received the following response: “Internal business control will prevent such problems.” We said, “ok, look at their website.” A few weeks later, when we continued to work with our client, we received this check from them by mail:

It’s stated here that this is a $ 2 test fee for our company WH. That's how we make money!
This check is still on my desk. For two such tests, we can get as much as 4 bucks!
But a few months later we heard from a specific customer that $ 70,000 was illegally transferred to one of the East European countries. The money could not be returned, because it was too late, and the ASP lost their client. These things happen, but what we never learned, because we are not forensic investigators, is how many other clients have suffered from this vulnerability. Because everything in this scheme looks completely legal again - you just change the look of the URL.
Shopping from TV Stores
Trey Ford: Now I will tell you about a truly technical hack, so listen carefully. We all know a small television station called QVC, I'm sure you sometimes buy something at this telemarket.

Know that when you buy something online, regardless of the site, do not click anywhere, because your order will immediately begin to be processed! Perhaps you will immediately change your mind and stop the transaction. But in a few days you will receive in the mail a bunch of all kinds of junk, for which you must immediately pay.
Here's Quintina Moore Perry, a 33-year-old certified hacker from Greensboro, North Carolina. I don’t know how she made a living earlier, but I can tell you how she started making money after a random transaction that she allegedly made, although she canceled the deal on the site almost immediately.
All these “ordered” things began to come to her mailing address from QVC - women’s handbags, household appliances, jewelry, electronics. What would you do if you didn’t order by mail? That's right, nothing! You can see right away, our people ...
However, you get free shipping, and free shipping is a benefit! After all, the parcels are already in the mail, you do not need to send them anywhere. If this is a standard business process, then how can it be used? What to do with 1800 parcels that arrived at her mailing address from May to November? So, this woman put all these things up for auction on eBay, and as a result of selling all this junk, her profit was $ 412,000! How did she do it - very simple! She said in the mail that someone ordered all these packages with QVC to her address, but it is very difficult for her to repack them and send them to the recipients, so let them be sent in the original packaging of QVC!
As you can see, this is a very technical solution! However, QVC was worried about this problem after 2 people who bought the product on eBay received it in a QVC package. A federal court found this woman guilty of mail fraud.

Thus, a simple technical hitch with the cancellation of the orders made allowed this woman to earn a huge amount of money.
37:40 min
BLACK HAT USA Conference. Get rich or die: make money on the Internet using Black Hat. Part 3
A bit of advertising :)
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, cloud VPS for developers from $ 4.99 , a 30% discount for Habr users on the unique entry-level server analog that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share a server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?