Today I’ll talk about other ways of multi-factor authentication and the tasks that they help companies solve. I will talk about the example of the Gemalto Safenet Authentication Service (SAS) solution, which exists in the format of a cloud service and on-premise version certified by the FSTEC.
Everyone roughly understands what multifactor authentication is: this is when in addition to the password (knowledge factor), you need to enter an additional confirming factor. There are two of them:
- ownership factor (what I have): codes from SMS, email, mobile applications, USB keys and more.
- property factor (what I am): fingerprints, iris.

Typically, inside a company, multi-factor authentication is used to protect against unauthorized access VDI, web portals (OWA, various ServiceDesk, Confluence, Microsoft IIS), VPN, cloud applications (Office 365, Salesforce).
Below are some examples of what tasks can be accomplished using the SafeNet Authentication Service.
Challenge: Compliance with PCI DSS
Multifactor authentication is one of the requirements of the PCI DSS standard (clause 8.3.). Moreover, the standard requires multi-factor authentication to be one-step: the password and the second factor must be entered in the same field. If an attacker tries to take over the account and makes a mistake when entering, he will not understand where the error was made - in the password or token.
Solution: One-Step Multi-Factor PIN + OTP Authentication
This SafeNet-based authentication scheme is implemented in our IaaS platform that complies with PCI DSS and 152- requirements - Cloud-152 . Administrators of the Cloud-152 platform pass it to access the management segment. For authorization, you need to enter the PIN and OTP in one field, which comes with a push notification in the Mobile Pass mobile application.
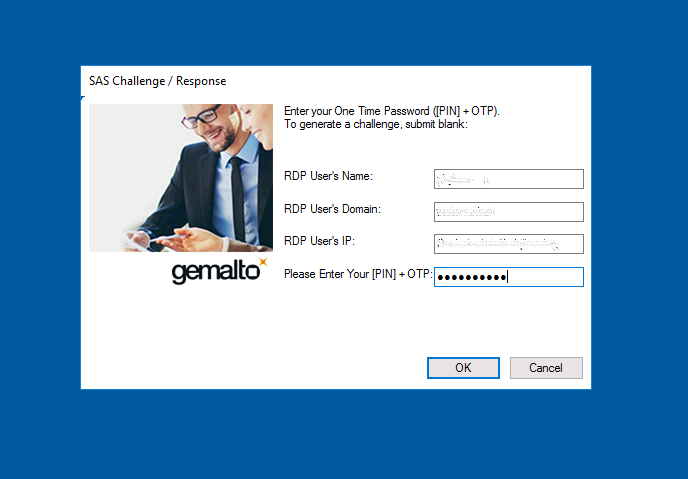
This is how the authentication for Cloud-152 administrators on the DataLine side looks.
* There should have been a screenshot from the SafeNet Mobile Pass, but the application blocks the screenshots.
Challenge: two-factor authentication for employees without a smartphone and mobile Internet
The company intends to implement two-factor authentication for entering workstations. The company has a distributed network of offices throughout Russia, many employees have unstable mobile Internet or no smartphone at all. It turns out that Push notifications from mobile applications as a second factor will not work. SMS and physical tokens disappear due to high cost.
Solution: use GrIDSure as a second factor
GrIDSure is a one-time password (OTP). It consists of a table with characters and a pattern that the user sets himself when setting up authentication. For authorization, the user selects characters from the table according to this pattern and enters as the second factor.
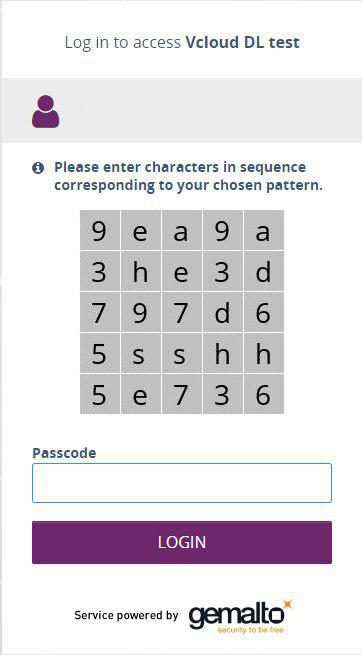
The table with characters that the user receives when authorizing to workstations.

Next, the user simply follows the selected pattern. For example, like this.
As characters, you can use numbers, letters, and special characters. The size of the table is customizable: it can be a table of 5 by 5 or more.
With each authentication attempt, the table is updated, so this password cannot be brushed.
Gridsure also does not need a mobile application, and therefore a smartphone with mobile Internet. GrIDSure is displayed on the same interface and device as the protected service.
Objective: protect the web service from brute force attack
SafeNet-based multi-factor authentication can be used to protect web services published on the Internet, such as Outlook Web App (OWA). Safenet supports RADIUS and SAML protocols, so it easily integrates with Microsoft Outlook, Office 365, Saleforce, Dropbox, Apache, etc.
If the attacker knows emails, then he will be able to attack such services by means of password cracking. The purpose of such an attack may not always be to capture the account, but to block it. In theory, you can block the entire company mail.
Solution: using OTP as a second factor
Here you can use GrIDSure or Mobile Pass as a second factor.
Task: automation of the issuance and maintenance of tokens
A company with a distributed network of branches for 20 thousand employees already uses two-factor authentication with GrIDSure as the second factor.
The problem is that administrators have to spend a lot of time servicing tokens: issuing new ones, dropping patterns, etc.
Solution: use the self-service portal
SafeNet has a self-service portal that helps automate routine operations and reduce the burden on administrators.
On the self-service portal, the user can leave all the information necessary to issue a token. The administrator can only confirm it and send a link to the formation of the token. If the user has forgotten which path he chose for GrIDSure, then again he can independently reset it here and set a new one.

Tasks: Regulation of access to workstations
The call center has 200 shift workers. To save resources, two employees have one workstation. You need to configure accesses so that there are no competitive sessions.
Solution: Implement Token Login and Access Policies
SafeNet can be installed on each workstation and through it set access policies by time and IP addresses. If the change of employee has not yet begun, then he will not be able to go to his workstation. The administrator will be able to track when an employee logged in and from which IP address in the log.
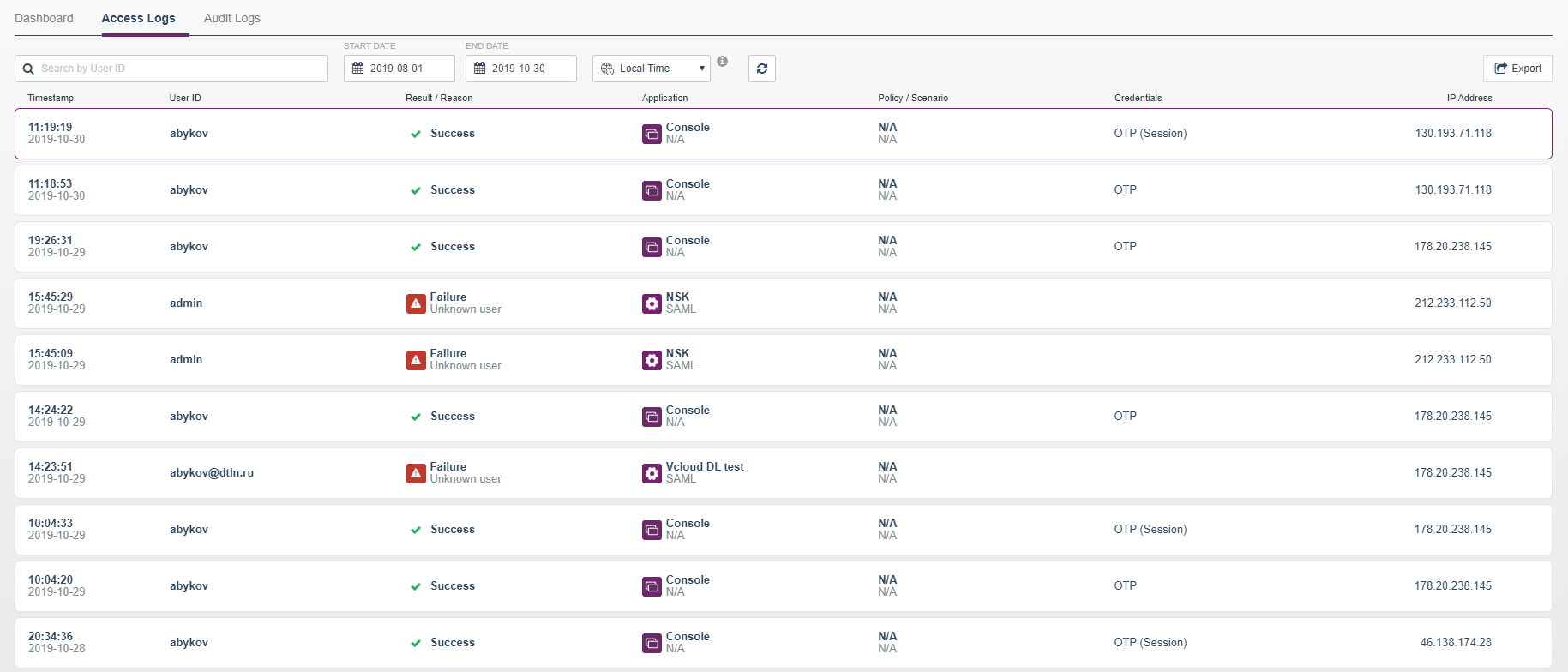
Multi-factor authentication is becoming more and more important, since a static password even with a large number of characters is no longer a difficult obstacle to an attacker.
Another of the trends in this direction is the use of a token to access several company systems or applications at once (SSO input). Such a scenario can also be implemented using SafeNet. If interested, I’ll tell you about him in a separate post.