Introduction
Mobile devices - smartphones, tablets and other mobile devices - are becoming an integral part of people's lives. Nearly 67% of the world's people have at least one smartphone; 5.8 billion active mobile devices are projected by 2025 [1].
According to IDC [2], of all mobile devices sold in the third quarter of 2018, 86.8% were equipped with Android OS. The number of users using the Android OS is more than 1.4 billion. According to Securelist [3], in 2018, 5.3 million malicious software packages for the Android family of OS were detected. Therefore, a specialist in the field of computer forensics has to use different methods for extracting a copy of memory for each device.
Currently, there is no way to uniformly obtain a copy of memory from devices running Android OS. In this regard, the specialist in computer forensics has to use many different methods, where he is faced with technical problems. First of all, problems are associated with the lack of a driver or with a malfunction of the USB connector used in traditional methods for data extraction. However, wireless communication channels can be used to receive and transmit a copy of the memory [4].
Section 1 will describe the architecture of Android OS, scenarios for using RAM, data structures contained in RAM, software for obtaining a copy of memory, and software for transferring data.
Section 2 will describe the architecture of the system for obtaining a copy of RAM, the connection between subsystems and modules.
Section 3 will describe the implementation of a system for obtaining a copy of RAM.
Section 1: Exploring ways to get a copy of memory in devices running Android OS via wireless channels
This section discusses software for obtaining a copy of memory and their comparison, network protocols for transferring a copy of RAM, ways to run executable files via wireless connections for Android OS, RAM structure, and scenarios for using a copy of RAM.
Scenarios for using a copy of RAM
Today, the Android operating system is present on different devices thanks to the Linux kernel and the Dalvik virtual machine. This paper discusses devices running on the most common hardware platform ARM and x86.
A copy of memory is unstructured binary data that is difficult to analyze without appropriate specialized tools. At the time of this writing, devices have a RAM size of not more than ten gigabytes, which significantly increases the analysis time of a copy of RAM of this size. At the moment, there is no single means of analyzing all the structures of RAM. For a complete analysis of RAM requires the use of several software tools.
There are no guarantees for a successful analysis of a copy of RAM, even if you have all the necessary tools due to problems at the stage of obtaining a copy of the memory. If there is no possibility to connect to the device or there is a huge risk of data corruption, then the wireless way to get a copy of the memory remains the only and safe. Unfortunately, at the moment there are no software tools for automatically receiving a copy of memory via wireless communication.
A copy can be used in computer forensics. For example, if the data on the device under study is encrypted, a copy of the memory can help to decrypt the data which contains passwords and cryptographic keys [5]. Each application that processes personal data uses data encryption. Having the image of a copy of RAM and some skill in working with it, there is a chance to restore the latest messages or temporary files that can help in a forensic investigation.
In the case of an attack on a device, analysis of a copy of the device’s RAM allows you to find out how the attack was carried out, which communication channels, malware and vulnerabilities were used by the attacker to prevent such attacks in the future.
Periodically copying critical data to detect malicious software. This approach is used to detect malware that uses methods to hide its presence in the system.
Also, a copy of the memory (or the part that contains only the context of the application or process under study) can be used to identify vulnerabilities and undocumented features of the software. Existing specialized software tools use a copy of RAM to detect rootkits [6]. A copy of the memory of the entire system can be used to monitor changes in the entire system in order to identify illegal actions.
To analyze the operational copy, the Volatility Framework [7] is used. Volatility Framework is a set of tools for obtaining and analyzing a copy of RAM of various operating systems, including Android. Using these tools, you can get the necessary information contained in the image of RAM. To obtain a copy of the RAM, the Volatility Framework uses the LiME kernel module. To extract a copy of RAM via LiME, the source code of the Linux kernel of the device under study is required.
Analysis of tools and methods for executing executable files via wireless connections for Android OS
To install applications, as in any UNIX-like operating systems, packages are used. On Android, these packages have the .apk extension. Such packages are stored in the device’s memory even after installation and are deleted only when the application is uninstalled. The .apk package contains compiled Java code, as well as an AndroidManifest.xml file that declares the permissions necessary for the application to work.
There are two types of applications: system and user. System applications, unlike user applications, have more privileges, so changing or deleting them is possible only if you have superuser rights. User application packages are located in the “/ data / app” directory. System application packages are located in the “/ system / app” directory.
Starting from Android 5.0, instead of the Dalvik virtual machine, the Android Runtime virtual machine is used. Unlike Dalvik, Android Runtime does not compile the application during startup, but during installation. This increases the speed of launching the program and increases the battery life. To ensure backward compatibility, Android Runtime uses the same bytecode as Dalvik.
Unlike a system process, a user process has fewer privileges on the system. To obtain privileges like a system process, a user process requires superuser rights or “root” rights. The superuser is a user of the operating system that has unlimited rights in the system.
Superuser rights are of two types: permanent and temporary. Permanent superuser rights are maintained even after a reboot, and temporary rights are valid until the device is rebooted.
Typically, superuser rights on devices are not available. Due to the wide variety of devices, there is no monotonous way to obtain superuser rights. Therefore, to obtain superuser rights, different tools are used. Obtaining superuser rights is necessary to obtain a copy of the memory from Android devices.
To run executable files, some privileges are required on the system, as well as a set of Unix commands. Initially, Android has some minimal set of commands, which are usually not enough to get a copy of the memory. Therefore, they use BusyBox, which includes an extended set of commands. The utilities included with BusyBox allow you to work in the file system, launch applications, display system information and much more. It is also possible to create shell scripts.
Shell scripts are executable files that contain a script to execute a set of commands. Unlike applications, shell scripts do not require installation and compilation. If you need to fix something, then just make changes to the shell script file.
Since executable files are launched via wireless communication, we will consider two ways to launch executable files using ADB and SSH.
For the first method, it is enough to run the “setprop service.adb.tcp.port 5555; stop adbd; start adbd ”. Next, run the command line on the computer and connect to the device using the “adb connect X” command, where “X” is the IP address of the device on the network and the port value is 5555. To run the executable file, use the command “adb shell am start -n com. package.name/com.package.name.ActivityName ”if this is an application. If the executable file is a shell script, then it is launched using the “adb shell ./name” command, where name is the name of the script.
For the second method, the SSH protocol is used. Unlike the previous method, this method requires an SSH client on the computer, and an SSH server on the device. On Windows, you can use PuTTY, and on Linux, Openssh. After connecting the device to the computer, we gain access to the Shell command shell. The commands to run the executable files are the same as in the first method.
Thus, it can be seen that both methods differ only in the connection method. Both methods use the Shell command shell to run executable files. From this it follows that when gaining access to the command shell, you can execute any command and also run any executable file, whether it be an application or a shell script.
Software tools for obtaining a copy of RAM
Existing software methods can be divided into two categories:
- getting a copy of memory from user space and the kernel;
- receiving a copy of memory only from user space.
Software tools for retrieving a copy of user space and kernel space include AMExtractor and LiME. Mem and Memfetch tools can only get a copy of memory from user space only.
Consider the above-mentioned software tools for obtaining a copy of RAM from devices under the control of the Android operating system:
- Mem: an open source utility used to obtain process RAM data [8];
- Memfetch: an open source utility for obtaining the address space of the process RAM using the devices / proc / $ pid / map and / proc / $ pid / mem [9];
- LiME: a module for the Linux kernel with open source code for retrieving data stored in RAM in user space and kernel [10];
- AMExtractor: an open source utility that uses the / dev / kmem pseudo-device to load into kernel memory [11].
Mem and Memfetch programs can be used without preliminary configuration, but they are not able to get data from the kernel memory area and require superuser rights for their work.
Despite its widespread use and versatility, the LiME module requires the correct configuration and the source code of the Linux kernel for each individual device.
For AMExtractor to work, information is required on the type of virtual memory addressing model used by the kernel and superuser rights.
The software tools considered in this work, the source code of which is publicly available, are used only to obtain a copy of the RAM.
Software tools such as Oxygen, UFED, and MSAB XRY are expensive and are available for commercial use only. Programs of this level are capable of: receiving a copy of memory from a locked device, obtaining superuser rights, generating forensic reports, and much more.
The ANDROPHSY tool is the first open source tool that supports all stages of the forensic investigation of Android devices [12]. The ANDROPHSY architecture consists of four main modules: a processing module, a collection module, an analysis module, and a reporting module. Data acquisition is performed using the dd tool and the ADB service. A USB cable is used to connect between the computer and the device under investigation, and data is transmitted via the TCP protocol.
Confirmation of the relevance of this work is the presence of flaws in ANDROPHSY. These include performance only in the Linux environment, the lack of functions for obtaining and analyzing a copy of the device’s RAM and the lack of connection to the device via Wi-Fi or Bluetooth to extract data.
Based on the analysis, a comparative table was built (see Figure 1). In table 1, the symbol “+” denotes funds that meet the requirements, and the symbol “-” indicates the opposite.
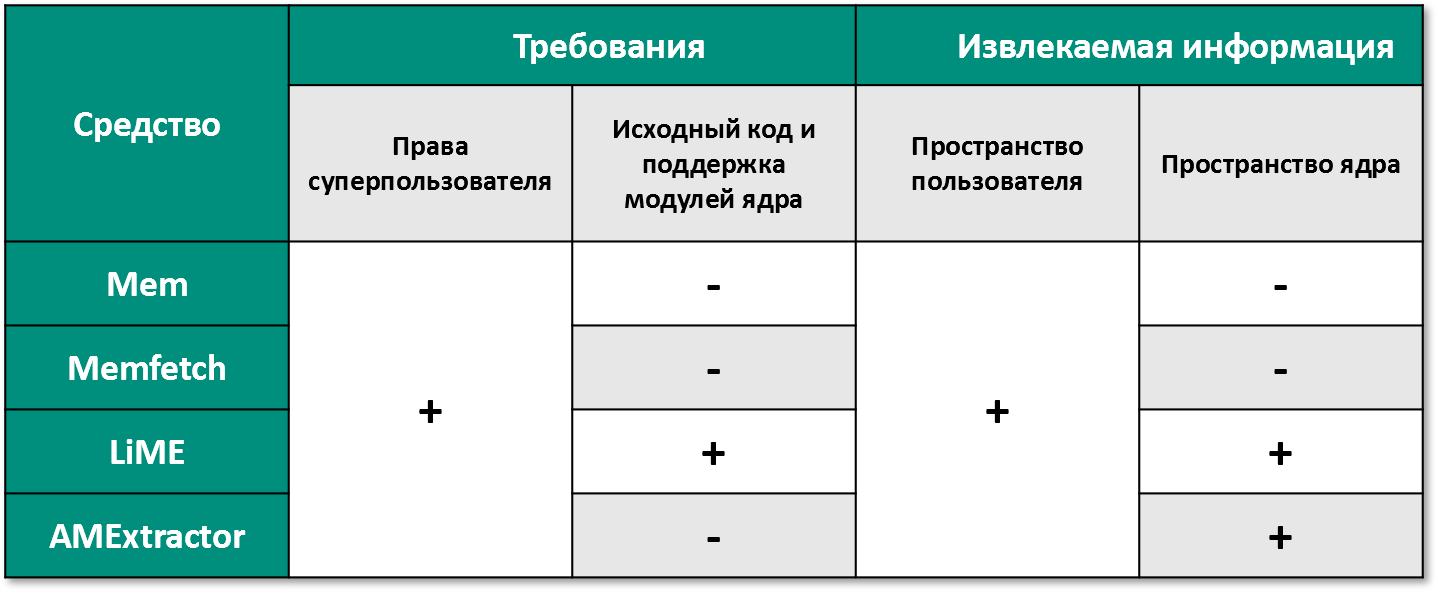
Figure 1 - Software for obtaining a copy of RAM
Based on the results of the comparison, it was decided to use AMExtractor to take the image of RAM, due to the receipt of a full copy of RAM, as well as the lack of the need for the source code of the kernel and support for loading modules.
Data Transfer Software
A USB cable is used to retrieve data from devices running the Android operating system. Most Android devices can be connected to a personal computer using a USB cable.
However, when conducting an investigation of an Android device, it may happen that it is impossible to extract data from it using a USB connection. The reasons for this may be a faulty cable or a damaged connector. In these cases, only an external memory card, which is not found on all devices, will be available to the expert for research. Sometimes a device contains only internal memory. The contents of this memory, as well as RAM, can be safely removed via a USB connection. An alternative to a wired connection is wireless. Of all the wireless protocols, the Android operating system supports the most popular: Wi-Fi and Bluetooth.
Wi-Fi in modern Android devices is used to access the Internet or to transfer data. An-droid-based mobile devices support most Wi-Fi standards up to 802.11ac. The data transfer speed between devices via Wi-Fi exceeds the data transfer speed via Bluetooth [13].
To connect devices via Wi-Fi, just connect to a shared access point. Since other devices can connect to the shared access point, it is important to limit their access to the network. The availability of support in Android, Wi-Fi Hotspot, allows you to use the device as an access point.
The Bluetooth wireless protocol, available on An-droid devices, was designed to transfer data between devices that have a small battery. Compared to Wi-Fi, the file transfer speed via Bluetooth is much slower. The protocol is based on a piconet consisting of a main node and several subordinate nodes [14]. Profiles are used to transfer different types of data. A Bluetooth profile defines the commands and functionality that devices can exchange among themselves. There are at least 27 Bluetooth profiles.
A PAN profile is used to create a WPAN between two devices. The HID profile allows you to connect a mouse, keyboard, and other peripheral devices that support this profile [14].
In this paper, based on the features of the Android operating system, we consider the following software data transfer:
- SSHFS: a FUSE-based file system client for mounting remote directories via an SSH connection [15];
- Rsync: an open source utility that provides fast step-by-step data transfer [16];
- SCP: utility and protocol for transmitting data via the SSH protocol [17];
- SFTP: in comparison with SCP, which allows you to only copy files, SFTP has the ability to perform file operations: for example, resume file transfer after disconnecting, delete files on the server, and many other operations [18];
- NetCat: UNIX utility that reads and writes data through network connections using the TCP or UDP protocol [19].
The rsync utility is used in most cases to synchronize files or directories. During synchronization, only changes are sent using an efficient checksum search algorithm. Rsync functionality allows you to transfer via SSH protocol, compress files, as well as copy links, device files, owner attributes, groups and rights.
Most means of obtaining a copy of the memory use the TCP protocol for data transfer to exclude the possibility of writing data to the memory of the device under study.
For secure data transfer it is important that the software uses the SSH protocol. Secure Shell Protocol (SSH) is a protocol for secure remote login and other secure network services over an insecure network [20].
Data compression can significantly increase the transmission speed at low channel bandwidth. The transfer of files, as well as their attributes, is of great importance for subsequent forensic analysis.
To copy a physical copy of memory, the dd utility is used. Another dd utility can be used to convert files, but usually this utility is used to back up files, directories or the entire operating system.
Based on the analysis, a table was built (see Figure 2). In the table, the symbol “+” indicates the means that satisfy the requirements, and the symbol “-” indicates the opposite.
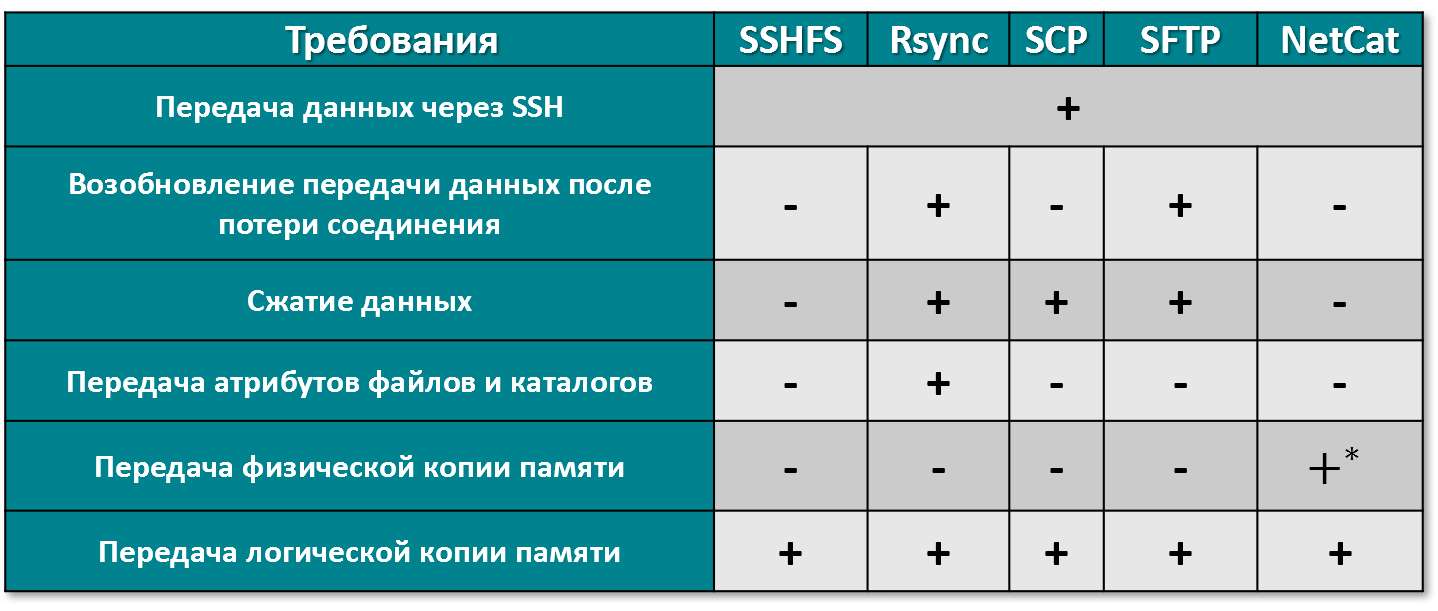
Figure 2 - Existing software for transferring a copy of RAM.
As a result of the analysis, it was decided to use NetCat to transfer a physical copy of the memory, and Rsync to transfer ordinary files and directories needed for forensic analysis
- GSMA Global Mobile Economy Report 2018 [Electronic resource]. // GSMA. - Resource access mode: http://www.gsma.com/mobileeconomy/ (accessed: 04/15/2019).
- International Data Corporation, Worldwide Quarterly Mobile Phone Tracker [Electronic resource]. // International Data Corporation - Resource access mode: http://www.idc.com/prodserv/smartphone-os-market-share.jsp (accessed: 04/15/2019).
- Securelist, Mobile malware evolution 2018 [Electronic resource]. // Kaspersky Lab - Access mode to the resource: https://securelist.ru/mobile-malware-evolution-2018/93451/ (accessed: 04/15/2019).
- Oleg Davydov. Mobile Phone Forensics Challenges [Electronic resource] // Eforensics magazine. - Access mode to the resource: http://www.tverlingua.by.ru/archive/005/5_3_1.htm (accessed date: 08/22/2018).
- Christian Hilgers. Post-Mortem Memory Analysis of Cold-Booted Android Devices. // IEEE Xplore Digital Library - Resource Access Mode: http://ieeexplore.ieee.org/stamp/stamp.jsp?arnumber=6824082 (accessed date September 15, 2018)
- Haiyu Yang. A Tool for Volatile Memory Acquisition from Android Devices [Electronic Resource]. // ResearchGate - Resource access mode: https://www.researchgate.net/publication/308300539_A_Tool_for_Volatile_Memory_Acquisition_from_Android_Devices (accessed September 16, 2018).
- About Volatility Framework [Electronic resource]. // Volatility Foundation - Resource access mode: https://www.volatilityfoundation.org/about (accessed September 16, 2018).
- Description of utility Mem [Electronic resource]. // GitHub - Resource access mode: https://github.com/MobileForensicsResearch/mem (accessed: 10/23/2018).
- Description of utility LiME [Electronic resource]. // GitHub - Resource access mode: https://github.com/volatilityfoundation/volatility/wiki/Android (accessed: 10.23.2018).
- Description of the utility Memfetch [Electronic resource]. // GitHub - Resource Access: https://github.com/citypw/lcamtuf-memfetch (reference date: 10.23.2018).
- Description of the utility AMExtractor [Electronic resource]. // GitHub - Resource access mode: https://github.com/ir193/AMExtractor (accessed: 10/23/2018).
- Description of ANDROPHSY utility [Electronic resource]. // GitHub - Resource access mode: https://github.com/scorelab/ANDROPHSY (accessed: 10/23/2018).
- Android Developer [Electronic resource]. // Google Developers - Resource access mode: https://developer.android.com/guide/topics/connectivity/wifip2p.html (accessed: 11/18/2018).
- Bluetooth overview [Electronic resource]. // Google Developers. - Resource access mode: https://developer.android.com/guide/topics/connectivity/bluetooth (accessed: 11/23/2018).
- SSHFS [Electronic resource]. // ArchLinux - Resource access mode: https://wiki.archlinux.org/index.php/SSHFS (accessed: 11/08/2018).
- Description of the utility Rsync [Electronic resource]. // Rsync - Resource access mode: https://rsync.samba.org/ (accessed: 11/23/2018).
- Description of the utility SCP [Electronic resource]. // Die.net - Resource access mode: https://linux.die.net/man/1/scp (accessed date: 12/08/2018).
- Description of SFTP utility [Electronic resource]. // SSH Communications Security - Resource access mode: https://www.ssh.com/ssh/sftp/#sec-SCP-Command-on-Linux/ (accessed: 12/08/2018).
- Useful Unix Utilities. Netcat [Electronic resource]. // Notes at hand - Resource access mode: https://handynotes.ru/2010/01/unix-utility-netcat.html (accessed date: 12/08/2018).
- The Secure Shell (SSH) Connection Protocol. // IETF - Resource Access: https://tools.ietf.org/html/rfc4254 (reference date: 12.13.2018).
PS To be continued ...