Introduction to Skydive
Skydive is a real-time, open-source network topology and protocol analyzer. It aims to provide an exhaustive way to understand what is happening in the network infrastructure.
Screenshot of objects (pods, interfaces) in kubernetes
Official project page: https://github.com/skydive-project/skydive
Kubernetes will be lower.
Now let's see a simpler example.
To demonstrate, install the Etcd cluster on 3 servers. For this we will use the galaxy role frank6866.etcd.
ansible-galaxy install frank6866.etcd
Yaml below
- hosts: etcd become: yes roles: - frank6866.etcd
Ansible.cfg file below
[defaults] inventory = inventory remote_user = user host_key_checking = False stdout_callback=debug
inventory file
frank6866-etcd-1 ansible_ssh_host=172.26.9.78 etcd_public_ip=172.26.9.78 frank6866-etcd-2 ansible_ssh_host=172.26.9.79 etcd_public_ip=172.26.9.79 frank6866-etcd-3 ansible_ssh_host=172.26.9.80 etcd_public_ip=172.26.9.80 [cluster1] frank6866-etcd-[1:3] [etcd:children] cluster1 [etcd:vars] etcd_tls_enabled='false'
We start installation
ansible-playbook -i hosts.multiple etcd-cluster.yaml
After downloading the skydive repository
git clone https://github.com/skydive-project/skydive.git
Go to the contrib / ansible / inventory folder
cd contrib/ansible/inventory
Edit IP in hosts.multiple file
[analyzers] IP [agents] IP etcd # skydive-flow-matrix # For skydive-flow-matrix add skydive_extra_config: [agents:vars] skydive_extra_config={'agent.topology.probes': ['socketinfo',]}
We start the installation of skydive agents and the analyzer
ansible-playbook -i inventory/hosts.multiple playbook.yml.sample
After that, from your computer, go to IP :8082
And we see something like this

Skydive shows objects: interfaces.
The topology that you see when you go to Skydive is formed in the file /etc/skydive/skydive.yml
If you install skydive in kubernetes, then it will show you the pods.
If you comment out the topology in the analyzer’s config, we’ll just get separate objects without links.

Config with commented topology:
analyzer: auth: cluster: backend: cluster password: secret username: skydive listen: 0.0.0.0:8082 # topology: # fabric: # - TOR1[Name=tor1] -> TOR1_PORT1[Name=port1, MTU=1500] # - TOR1_PORT1 -> *[Type=host,Name=skydive-rpm-apatsev-2]/eth0 # - TOR1[Name=tor1] -> TOR1_PORT2[Name=port2, MTU=1500] # - TOR1_PORT2 -> *[Type=host,Name=skydive-rpm-apatsev-3]/eth0 # - TOR1[Name=tor1] -> TOR1_PORT3[Name=port3, MTU=1500] # - TOR1_PORT3 -> *[Type=host,Name=skydive-rpm-apatsev-4]/eth0 analyzers: - 172.26.9.21:8082 auth: cluster: type: basic users: skydive: secret etcd: embedded: true listen: 0.0.0.0:12379 name: skydive-rpm-apatsev-1 flow: protocol: udp host_id: skydive-rpm-apatsev-1
And now, with the help of skydive-flow-matrix, let's see the active connections between the servers.
First install skydive-flow-matrix on your work computer.
git clone https://github.com/skydive-project/skydive-flow-matrix.git cd skydive-flow-matrix/ apt install graphviz sudo pip install virtualenv virtualenv .venv source .venv/bin/activate pip install -r requirements.txt pip install .
We get the active connectivity in text form.
skydive-flow-matrix --analyzer IP :8082 --username admin --password password protocol,server,server_ip,port,server_proc,server_procname,client,client_ip,client_proc,client_procname TCP,skydive-apatsev-2,127.0.0.1,2379,/usr/bin/etcd,etcd,skydive-apatsev-2,127.0.0.1,/usr/bin/etcd,etcd TCP,skydive-apatsev-2,127.0.0.1,4001,/usr/bin/etcd,etcd,skydive-apatsev-2,127.0.0.1,/usr/bin/etcd,etcd TCP,skydive-apatsev-4,172.26.9.80,2380,/usr/bin/etcd,etcd,skydive-apatsev-2,172.26.9.78,/usr/bin/etcd,etcd TCP,skydive-apatsev-2,172.26.9.78,2380,/usr/bin/etcd,etcd,skydive-apatsev-3,172.26.9.79,/usr/bin/etcd,etcd TCP,skydive-apatsev-4,127.0.0.1,4001,/usr/bin/etcd,etcd,skydive-apatsev-4,127.0.0.1,/usr/bin/etcd,etcd TCP,skydive-apatsev-3,127.0.0.1,4001,/usr/bin/etcd,etcd,skydive-apatsev-3,127.0.0.1,/usr/bin/etcd,etcd TCP,skydive-apatsev-3,172.26.9.79,2380,/usr/bin/etcd,etcd,skydive-apatsev-2,172.26.9.78,/usr/bin/etcd,etcd TCP,skydive-apatsev-3,172.26.9.79,2380,/usr/bin/etcd,etcd,skydive-apatsev-4,172.26.9.80,/usr/bin/etcd,etcd TCP,skydive-apatsev-2,172.26.9.78,2380,/usr/bin/etcd,etcd,skydive-apatsev-4,172.26.9.80,/usr/bin/etcd,etcd TCP,skydive-apatsev-4,127.0.0.1,2379,/usr/bin/etcd,etcd,skydive-apatsev-4,127.0.0.1,/usr/bin/etcd,etcd TCP,skydive-apatsev-3,127.0.0.1,2379,/usr/bin/etcd,etcd,skydive-apatsev-3,127.0.0.1,/usr/bin/etcd,etcd TCP,skydive-apatsev-4,172.26.9.80,2380,/usr/bin/etcd,etcd,skydive-apatsev-3,172.26.9.79,/usr/bin/etcd,etcd
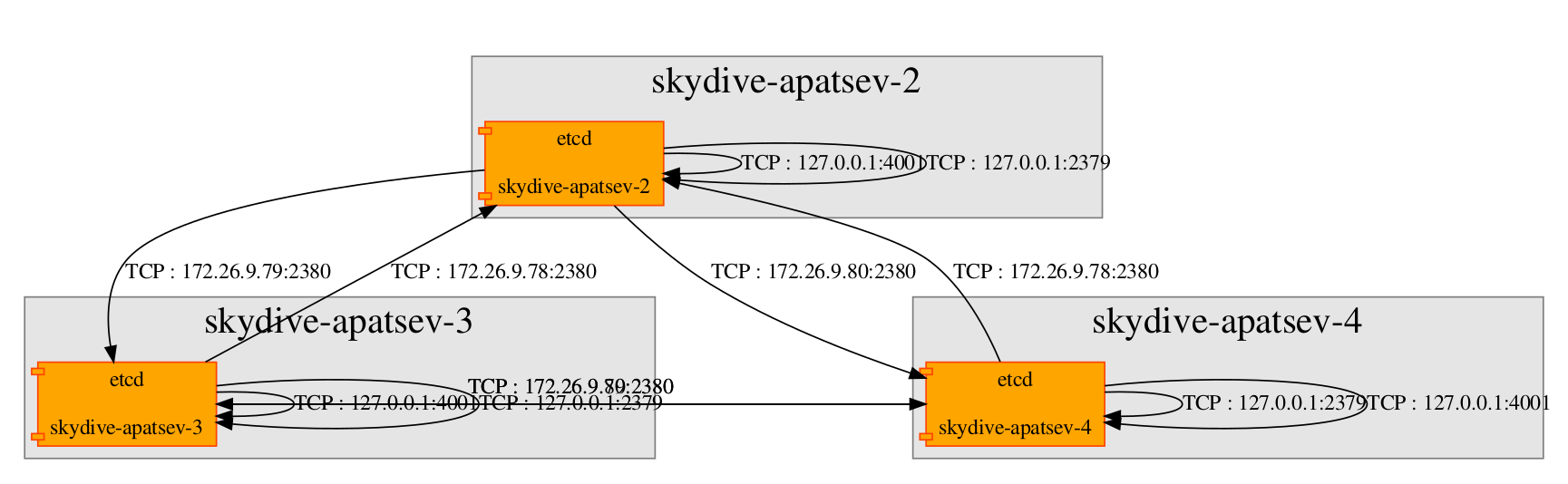
We also get active connections in graphical form.
skydive-flow-matrix --analyzer IP :8082 --username admin --password password --format render
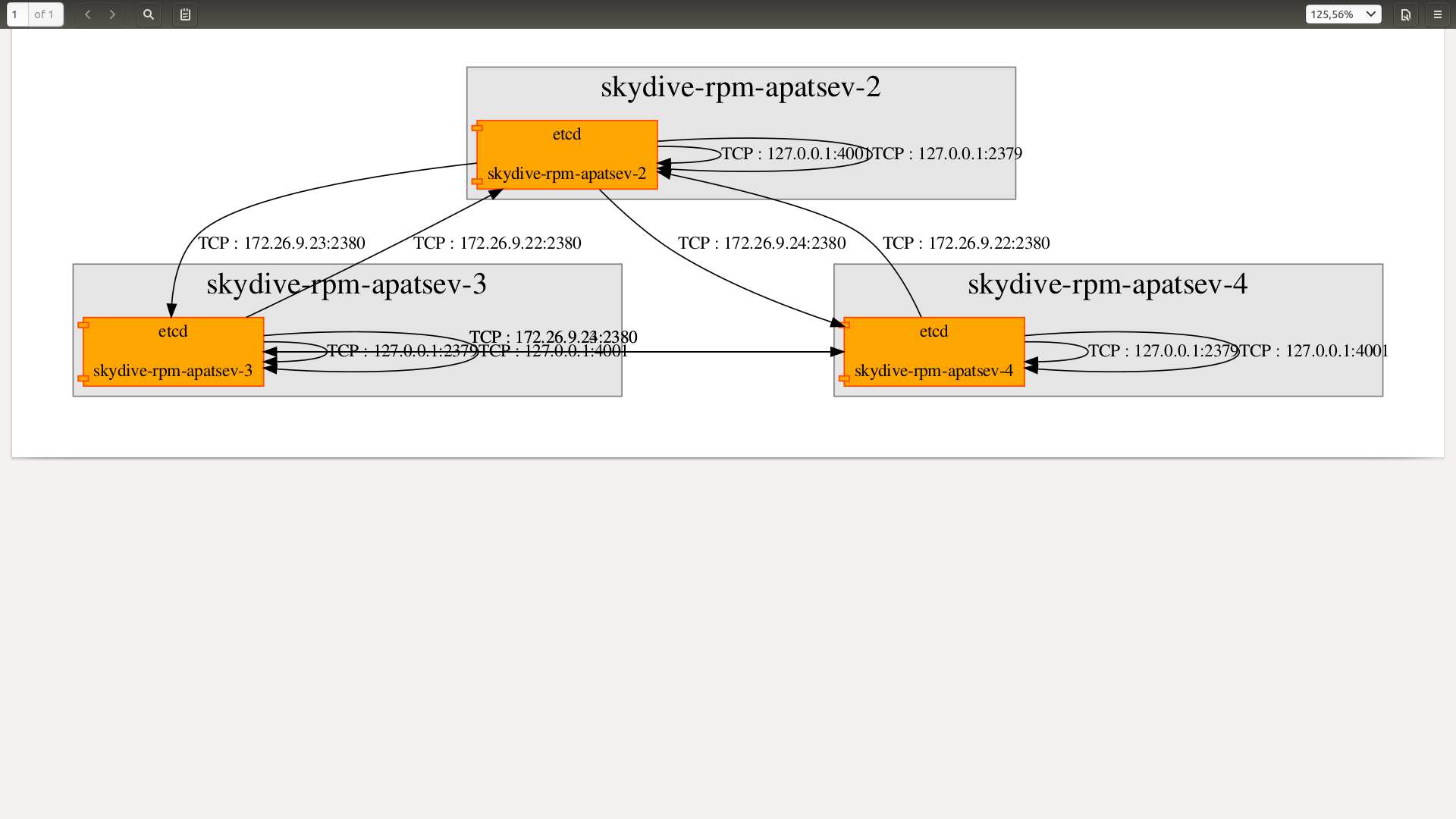
If you comment out the topology in the analyzer’s config and start the topology analysis, we will still get active connections in graphical form.
That is, the topology does not affect skydive-flow-matrix
Output:
The topology in the main skydive window shows the nodes where the agent is installed, the interfaces that are installed on this node.
In topology, nodes can be interconnected via interfaces. To do this, fix the file /etc/skydive/skydive.yml
Now install skydive in Kubernetes
Skydive needs to be installed in Kubernetes version no more than 1.16.
You can use kubespray for installation.
Next, run the installation of skydive:
git clone https://github.com/skydive-project/skydive.git cd skydive/contrib/kubernetes/ kubectl apply -f skydive.yaml
After installing skydive in kubernetes, we start port 8082 forwarding to your workstation.
This command must be run from your workstation.
Before that, you need to create a config file in the .kube directory in the home directory.
kubectl port-forward service/skydive-analyzer 8082:8082
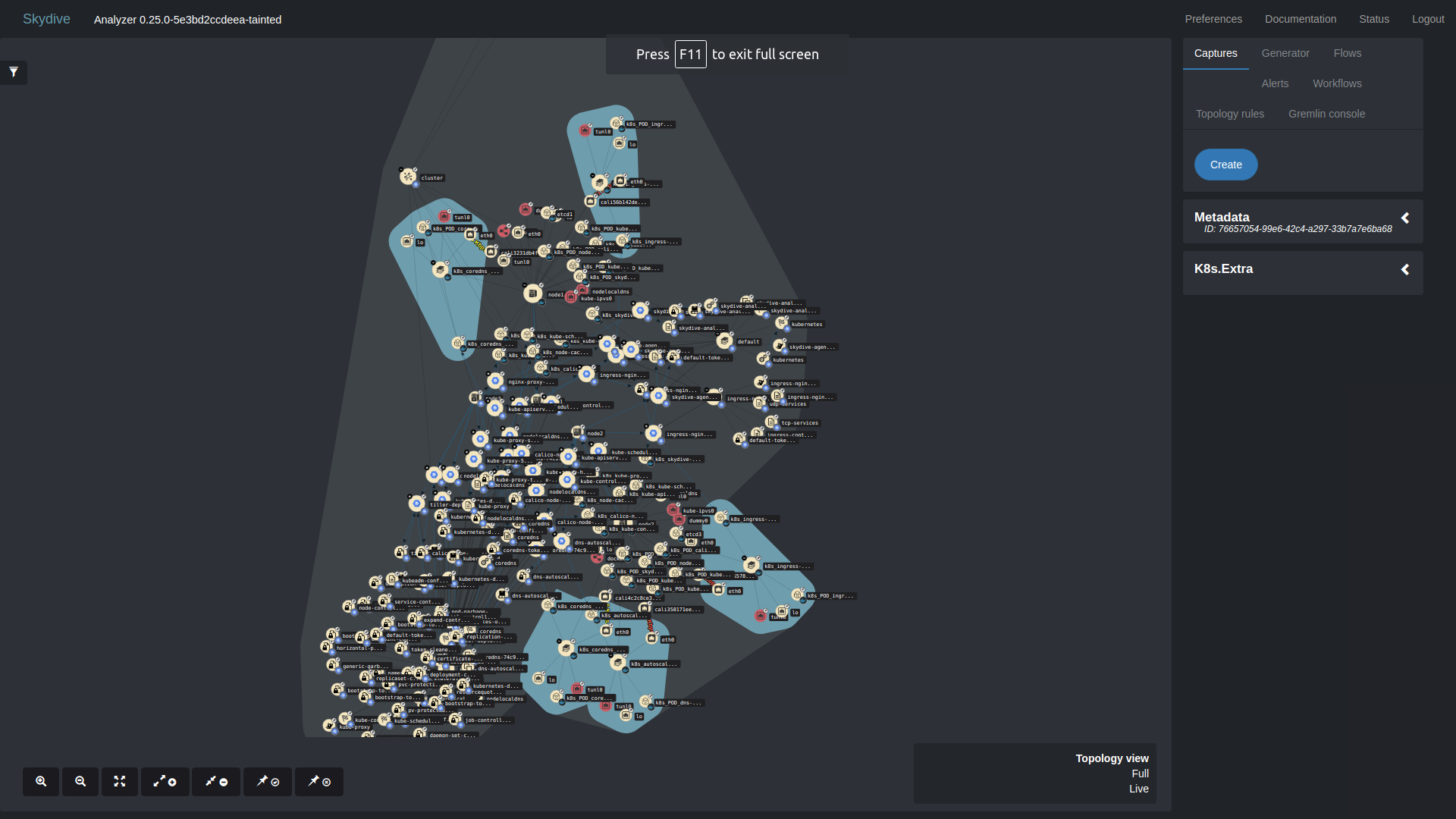
A few screenshots and video objects (pods, interfaces) in kubernetes
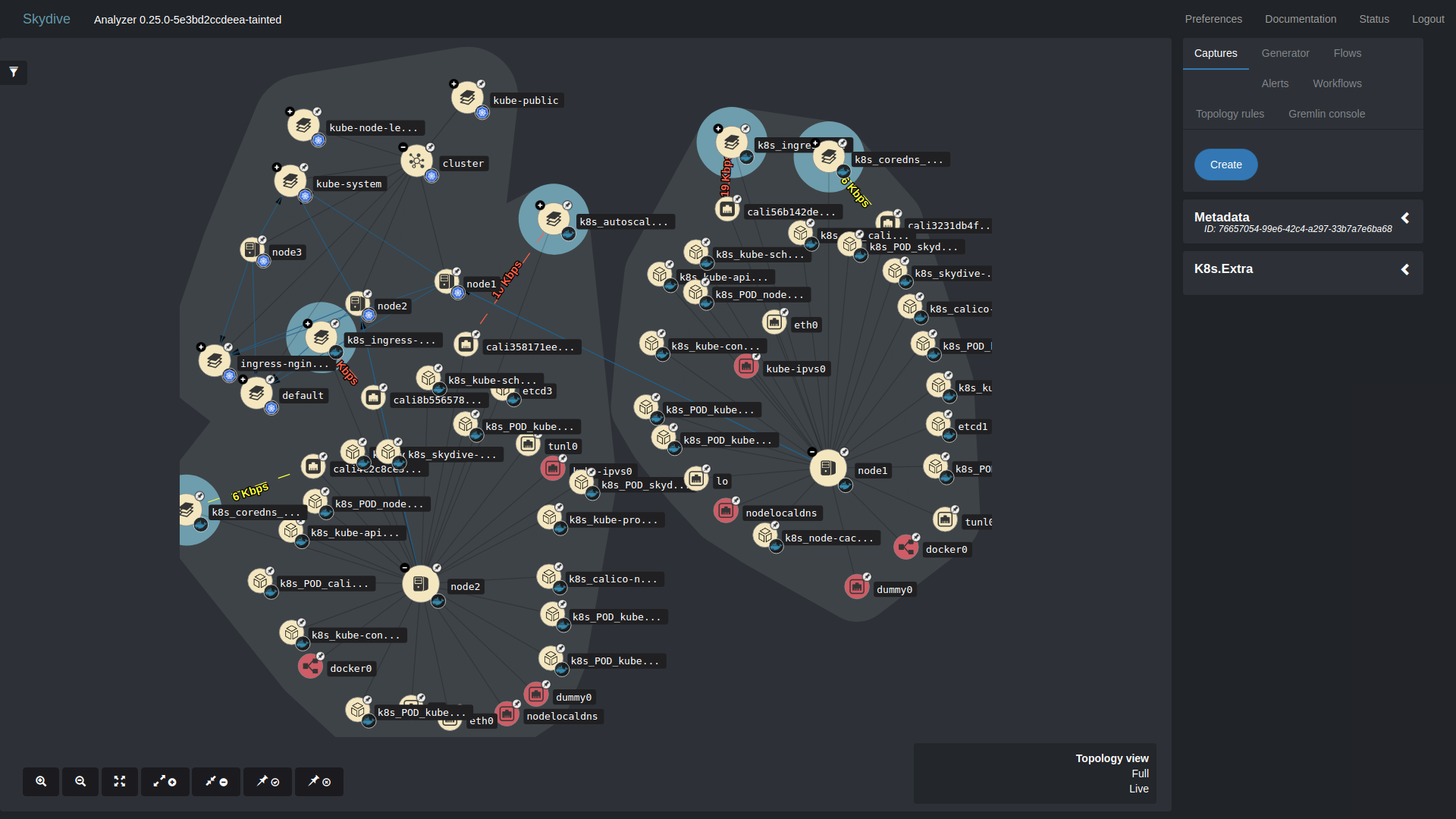
If we click plus, then there will be even more objects.

Video:
And in the end I quote from where agents can take information
- Docker (docker)
- Ethtool (ethtool)
- Libvirt (libvirt)
- LLDP (lldp)
- Lxd (lxd)
- NetLINK (netlink)
- NetNS (netns)
- Neutron (neutron)
- OVSDB (ovsdb)
- Opencontrail (opencontrail)
- runC (runc)
- Socket Information (socketinfo)
- VPP (vpp)
Where the analyzer can get the topology from:
- Isstio (istio)
- Kubernetes (k8s)
- OVN (ovn)
Wide support for K8s
Building a graph of nodes:
- general: cluster, namespace
- compute: node, pod, container
- storage: persistentvolumeclaim (pvc), persistentvolume (pv), storageclass
- network: networkpolicy, service, endpoints, ingress
- deployment: deployment, statefulset, replicaset, replicationcontroller, cronjob, job
- configuration: configmap, secret
Building a graph of terminal objects:
- k8s-k8s ownership (eg k8s.namespace - k8s.pod)
- k8s-k8s relationship (eg k8s.service - k8s.pod)
- k8s-physical relationship (eg k8s.node - host)
Display metadata nodes:
- indexed fields: standard fields such as
Type
,Name
plus k8s specific such asK8s.Namespace
- stored-only fields: the entire content of k8s resource stored under
K8s.Extra
Building node metadata:
- the
Status
node metadata field - with values Up (white) / Down (red)
- currently implemented for resources: pod, persistentvolumeclaim (pvc) and persistentvolume (pv)
Support for various types of Flow
- sFlow
- Afpacket
- PCAP
- PCAP socket
- DPDK
- eBPF
- Openvswitch port mirroring
Ansible's network search for Skydive is described in 2 posts.
We are looking for people who could write posts about other Skydive features.
Telegram chat on skydive.network: https://t.me/skydive_network_en