
Image: Unsplash
Proxies are usually used as a “strip” between the client and the website or online services. Directing traffic through a proxy helps users hide their real location and IP address. At the same time, companies also use proxies (see reverse proxies) to solve many problems, from increasing the level of information security to performing anonymous tasks and controlling the use of the Internet by employees.
Today we’ll talk about how proxy technology is actually used by different companies to increase the level of security of their infrastructure.
Hiding information from crackers
For example, often such proxies are used as an SSL gateway. In this case, the company can respond to external HTTP requests without fear of revealing the structure of its network. Acting as a mediator between external clients and the backend of the internal network, proxies can hide the real device of the company's infrastructure. Without a proxy, requests would be sent directly to the servers, and those would respond to them - this could give attackers information about the network device and possible weak points in its protection.
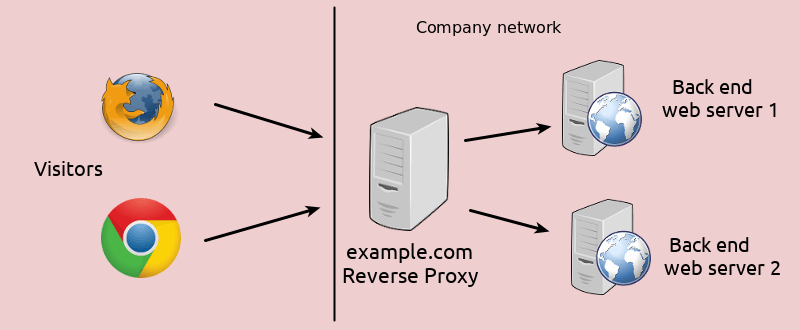
Image: linuxbabe.com
Another type of proxy useful for security tasks is resident proxies. In fact, these are addresses given to users by a real Internet provider from a certain city, region or state. Typically, these addresses are given to homeowners, they are noted in the database of regional Internet registers (RIR). When used correctly, requests from such addresses cannot be distinguished from calls from a real user.
Resident proxies are often used for competitive intelligence, scraping data from sites and bypassing antibot systems. In turn, companies can use rotated resident proxies to increase the security of the corporate network or site. If servers from different countries and regions respond to requests from potential attackers, information about the real network device will be impossible to obtain.
We at Infatica provide just such a service of rotated resident proxies - and many of our customers use it precisely to ensure the security of their infrastructure.
Encryption and decryption of traffic
Most often, companies use the so-called reverse proxies - usually this is the proxy server behind the corporate network firewall. It redirects external client requests to servers within the network. Reverse proxies can also be used to solve tasks such as encryption of traffic passing through.
In addition, proxies are useful for working with already encrypted traffic. Using reverse proxies for incoming HTTPS connections allows you to decrypt content upon receipt and send its decrypted version within the network.
This has a number of advantages. For example, you will not need to install security certificates on backend servers. In addition, you will have only one point where you need to configure SSL / TLS. In addition, since servers within the network do not need to perform resource-intensive operations of decrypting content, the load on them is significantly reduced.
Monitoring and optimizing protection costs
The use of reverse proxies also helps to increase the level of security, giving the company a point at which all traffic flows - and here it is easiest to monitor and log.
In addition, if all the servers behind the firewall first send traffic to the proxy server on the perimeter, then by protecting it, the overall level of security will increase (otherwise it would be necessary to allocate resources to protect all servers).
Access control
Proxies are not only useful for balancing and distributing traffic and load on the network, but can be used to limit access to certain resources on the network. A proxy server can act as a gateway for access to individual network segments, servers or services, both for external users and for company employees.
Conclusion
Companies actively use different types of proxies to solve problems related to increasing the level of security of their infrastructure. Proxies can be used as a tool for access control, logging, traffic encryption and even hiding the real device of the internal infrastructure.