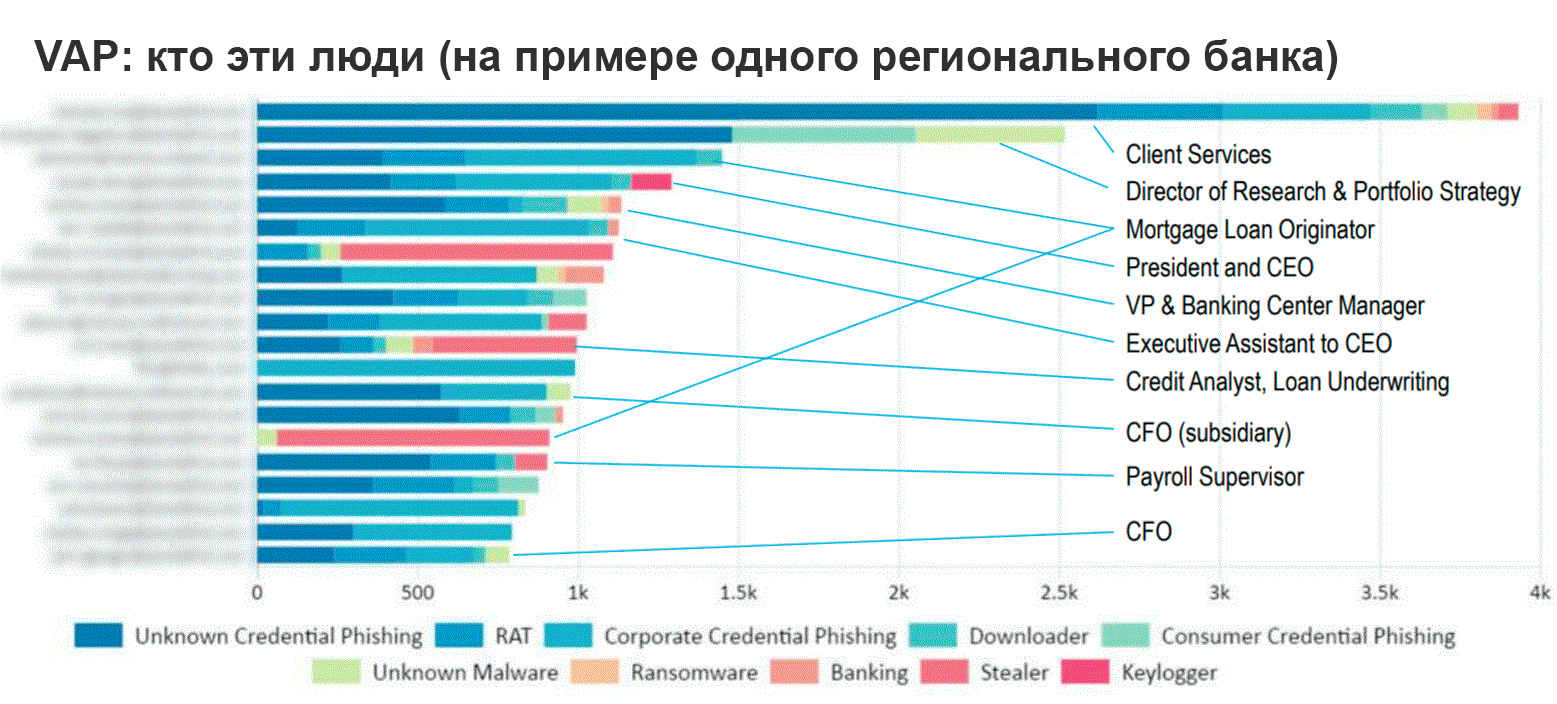
Source: Proofpoint
Exploit kits and known software vulnerabilities are rarely used for cyber attacks. In fact, more than 99% of successful attacks are carried out with the participation of the victim . The goal is to open the file with your own hands, run the macro, click on the link or perform some other action. This is the statistics from the latest report from Proofpoint.
Modern attacks do not focus on infrastructure, but on specific people. Specialists even identify a special type of users that pose the greatest threat to any organization - the so-called VAP-users (Very Attacked People), by analogy with VIPs. Hackers really appreciate them.
Human factor
Instead of attacking computer systems and infrastructure, the threat subjects focused on people, taking into account the victim's position, its role in the organization, access to data - and the likelihood that the user clicks on the link.
Thus, the system entry point before conducting a targeted attack is chosen not among servers and vulnerable software, but among company personnel.
In addition to targeted attacks, there are mass mailings of phishing emails. Attackers hope that there will be at least one VAP person among the recipients: “Over the past 18 months, social engineering has become more common and effective in hunting people,” the Proofpoint report says. - Attackers send messages on behalf of an unauthorized person or allegedly from a trusted colleague, or install more and more advanced malicious programs that secretly profile employees, steal confidential and credentials to make future attacks more effective. Regardless of the attack vectors - email, cloud applications, websites, social networks or other vectors - victims repeatedly demonstrate the effectiveness of social engineering, which convinces them to click on malicious links, download insecure files, install malware, transfer funds and disclose confidential information ".
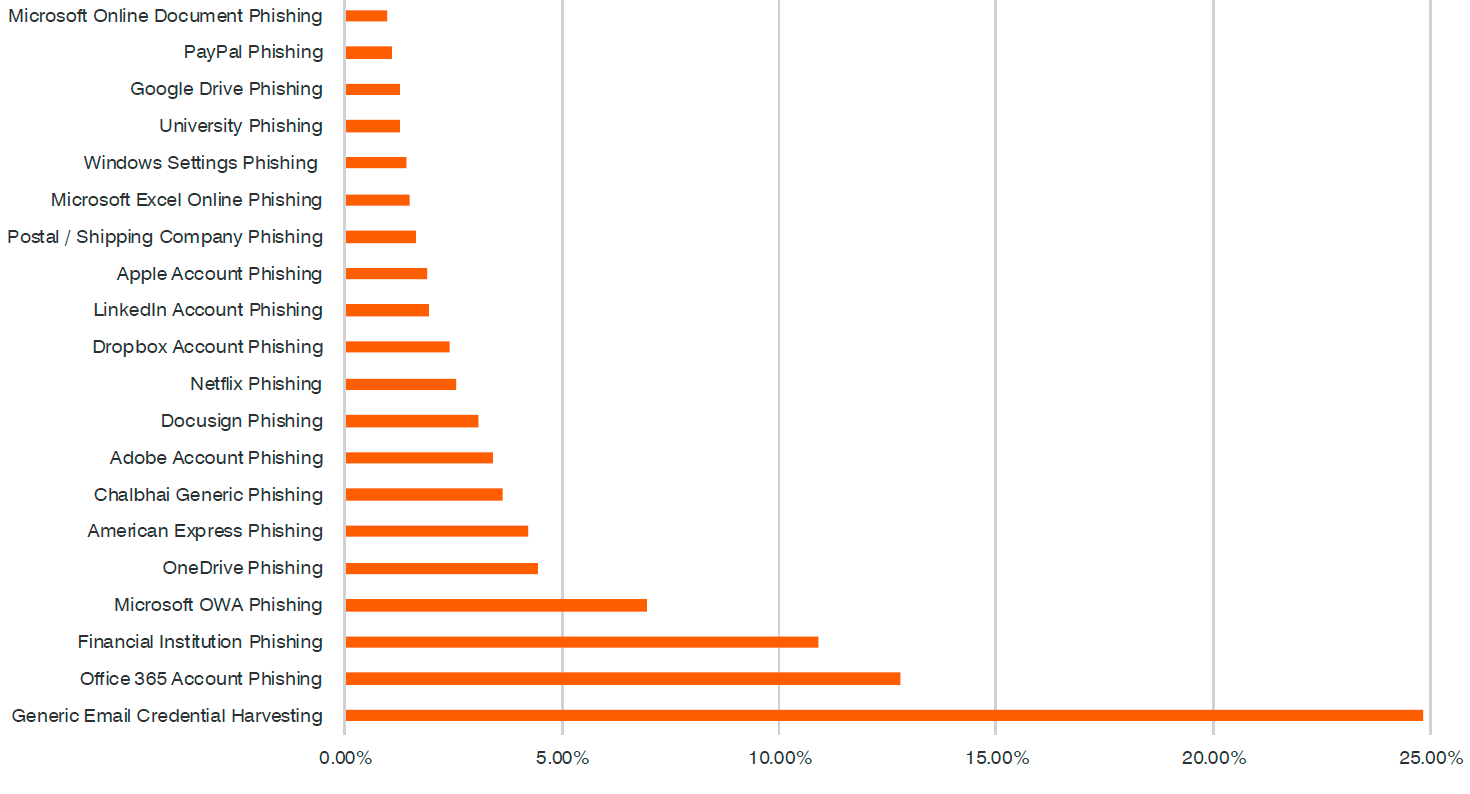
The most popular phishing baits in 2018, as a percentage of the total
Social engineering and phishing are now applied on a very wide scale. This is a very cheap and easy way to attack. But most importantly, it really works.

Average CTR on the most effective phishing "baits" in 2018
The problem seems to be in people. It's easy to blame users for believing a letter from a dubious source, clicking on a link, or opening a file. But in reality, attacks are becoming more sophisticated. It is often difficult to distinguish a malicious email from a regular email because attackers adapt their mailing lists. For example, they send letters as if from a reliable source, such as a cloud service provider, Microsoft or Google, on behalf of a colleague or even from a boss .
Attackers even try to imitate business processes within the company in order to increase the chances of success. For example, a user may be suspicious of a letter allegedly from a colleague if it arrived in the middle of the night. Therefore, such letters are specially sent out in the middle of the working day: so the chances are that the victim will click on the link.
“Cybercriminals are aggressively using social engineering because sending out fraudulent emails, stealing credentials, and downloading malicious attachments to cloud applications is easier and much more profitable than creating a costly, time-consuming exploit that is highly likely to fail,” says Kevin Epstein, vice President of Threat Operations for Proofpoint. - More than 99% of cyber attacks rely on human interaction, making individual users the last line of defense. To significantly reduce risk, organizations need a holistic approach to cybersecurity, taking into account the human factor, including effective security training and multi-level protection. ”
Phishing protection
Although phishing attacks are well camouflaged, there are ways to automatically determine what the threat might be. It is also necessary to inform employees that cloud service providers such as Microsoft and Google will not ask users to click on unexpected links to enter credentials and other information. If the user sees a suspicious URL, then it’s better not to click on the link, but directly in the browser to go to the company’s site and use the site navigation.
Organizations should also ensure that software and security patches are regularly updated. This increases the chance that in the event of an accidental launch, malware on known vulnerabilities will not work.
For example, unexpected emails that require something urgently needed can be considered suspicious. If the user is in doubt, it is best to contact the prospective sender and find out if he is really making such an urgent request. Better yet, implement an authentication system with digital signatures, which completely protects letters from falsification.
For example, GlobalSign recently signed an agreement with Sanmina , a leading provider of integrated manufacturing solutions, to digitally sign all outgoing e-mail. With GlobalSign certificates, businesses can sign and encrypt email using S / MIME technology. So Sanmina will do for 25,000 of its employees. At the same time, she will continue to use the Gmail mail provider as part of the GSuite corporate package, but the provider does not have automatic access to the contents of the letters, because only the recipient can read the message with S / MIME encryption (theoretically).
“The integration of GlobalSign enables us to implement the industry's best email security solution, strengthening our ability to block phishing and social engineering attacks,” said Matt Ramberg, vice president of information security at Sanmina. “The recent introduction of S / MIME in the GSuite package has enabled these enhancements with GlobalSign to provide even more secure communications for our employees, customers and suppliers.”
GlobalSign is a leader in S / MIME encrypted email protection, protecting tens of thousands of companies worldwide from phishing and other security issues.