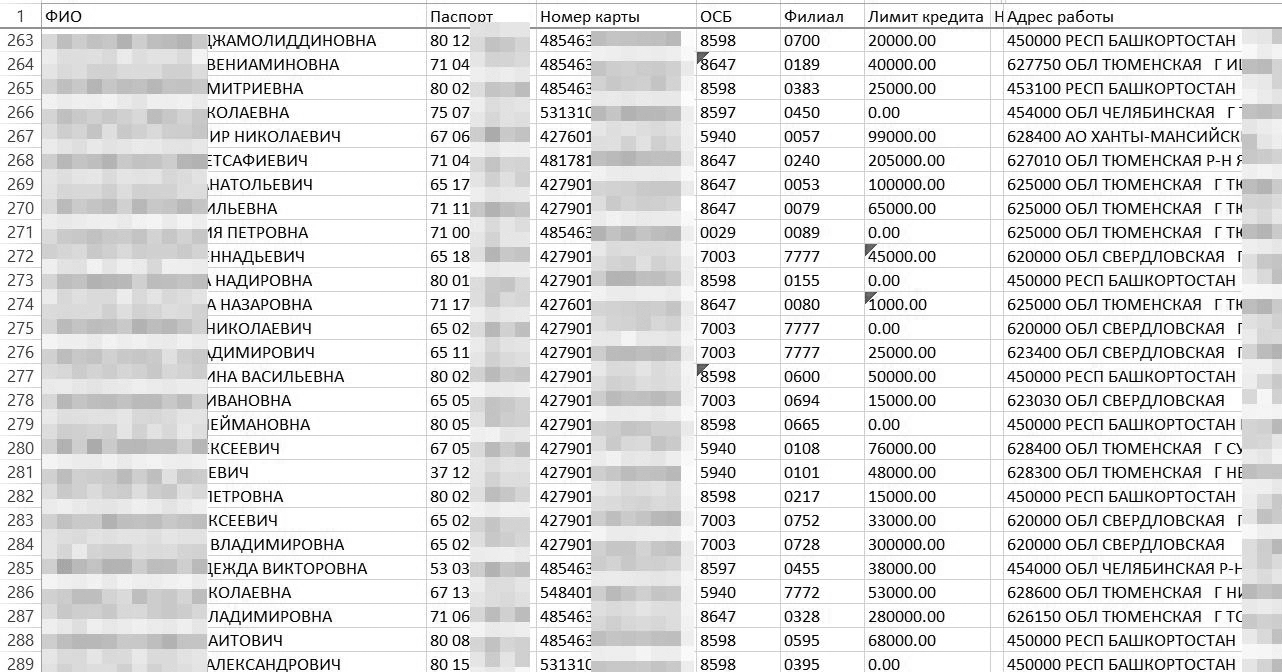
At the beginning of October on Habr the leak of data from "Sberbank" was discussed . One of the bank's employees sold information on thousands or millions of customers: name, passport number, card number, date of birth, address, etc.
The news itself is ordinary: employees of almost all Russian banks, telecom operators and state-owned companies sell such private information about customers. But here the base fell into open access, which does not happen often. The employee has already been calculated (and probably punished). But who framed the informant and Sberbank by launching information in the mass media is a separate topic .
But what should companies do, how to avoid such leaks? Probably, you need to raise staff salaries (so that they do not earn extra money in this way) and strengthen control over them. Sberbank uses the InfoWatch DLP system. Then she did not help. There are other systems that complement DLP. For example, Microsoft offers the Intune employee smartphone management platform.
Intune is a component of the Microsoft Enterprise Mobility + Security (EMS) suite that manages mobile devices and applications. It integrates tightly with other EMS components, such as Azure Active Directory (Azure AD) for access rights management and Azure Information Protection for data protection.
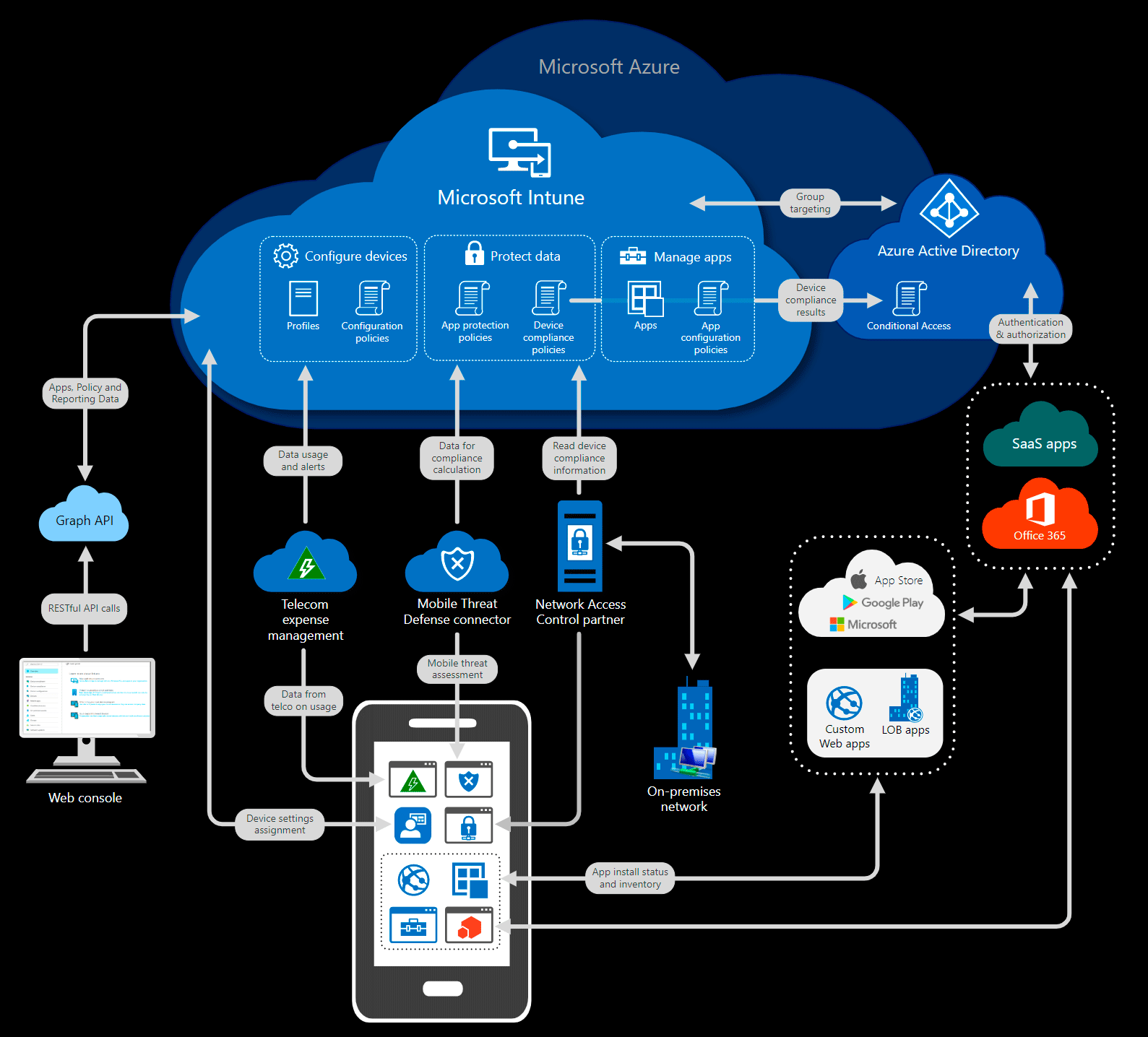
Here are some of the features of Intune:
- Manage mobile devices and computers that are used to access company data.
- Manage the mobile apps that employees launch.
- Protecting corporate information by controlling how employees access and share it.
- Ensure that all devices and applications comply with security requirements.
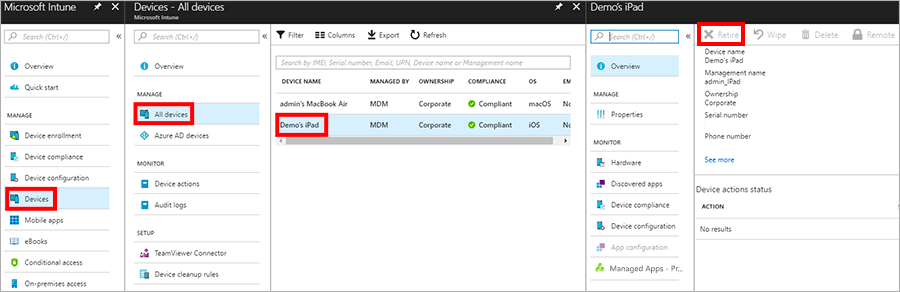
On the basis of Intune, it is convenient to launch the so-called "corporate phones" for distribution to staff. For example, that on the territory of the office it is allowed to use only their or their own devices with the same connection to Intune and the corresponding restrictions. This immediately eliminates several channels of information leakage described above.
Intune allows you to remotely prohibit the use of the camera on a mobile phone and limit the list of allowed applications for installation and launch.
Of course, the same restrictions should be set on tablets, laptops, desktop computers and any other devices used by the employee.
What methods does he have left to copy information from a database, like that of Sberbank? Writing to flash drives is prohibited or monitored.
He can dictate information by phone or skype voice. This problem is covered by speech recognition DLP.
You can copy information to an authorized application and send it through open channels. For example, encrypt it, then archive it to a file like dogovor.zip and send it to the counterparty under the guise of an application to the contract. Insert the pdf or jpg file into the metadata, hide it in a sound, graphic or video file using the steganography method and put it on an open hosting. Tracking such options is the work of the security service, which has a record of activity on the monitor of each employee through the DLP
Of course, the story of Edward Snowden shows that secret information can be taken out of the most protected organization if you really want to, but for this you need to have special clearance. Edward Snowden used an old computer from the archive allegedly under the guise of a repair (probably there were no ports on the other computers for recording a flash drive) and Rubik's cube, where he hid the microSD card.
Intune's employee device management system uses protocols or APIs available on mobile OSs. It includes tasks such as:
- Register devices in the system, so that they are all visible to the IT department
- Configure devices to meet safety standards
- Providing Wi-Fi / VPN certificates and profiles to access corporate services
- Reporting and verifying compliance with corporate standards
- Deleting corporate data from managed devices
The certificate provider for devices is Azure Active Directory (Azure AD). Intune integrates with Azure AD for a wide range of access control scenarios.
Mobile application management (MAM system) includes assigning specific mobile applications to specific employees, setting up applications; management of the use and sharing of corporate data in mobile applications; removal of corporate data from mobile applications; update etc.
What gives integration with GlobalSign
Since February 2019, GlobalSign has been supporting integration with Intune and Microsoft Active Directory . This means that devices can log in to the corporate network using GlobalSign PKI certificates. This is more convenient for both users and system administrators, who can automatically assign certificates to certain groups of users, depending on their access rights. Each group has its own set of allowed resources.
Automatic management of certificates and rights for each group reduces the risk of such leaks, as in the case of Sberbank. Although they say that there the information was sold by the director of the branch, which by default had maximum rights. Well, if ordinary employees can still be monitored using systems like Intune and DLP, then even the most advanced security department, which itself submits to this bosses, will not save from abuse by the bosses.