5+ Ways to Connect to a DataLine Cloud

In the DataLine cloud, our client receives not just separate virtual machines, but a virtual data center with the ability to organize complex network connectivity. And it is often required on client projects. For example, in one case, the virtual machine needs to be made publicly accessible from the Internet, in the other, for individual employees to have access to a group of virtual machines via VPN, in the third, to combine the cloud with physical equipment on our site or in another data center. Today we’ll talk about various ways to connect to our cloud and when to use which one.
How does the internet work in your home? The Internet is fed to the edge device, the router, it is the firewall behind which is your home network. About the same in the cloud. In 90% of cases, a virtual NSX Edge router is used as such an edge device in the VMware DataLine cloud. Here are ways to organize resource connectivity in the DataLine cloud with it:
NAT If you want the virtual machine to be visible from the Internet, we create NAT rules for publishing ports, and on the firewall we restrict access to them: https for all, ssh / rdp for a limited pool of admins IP addresses.
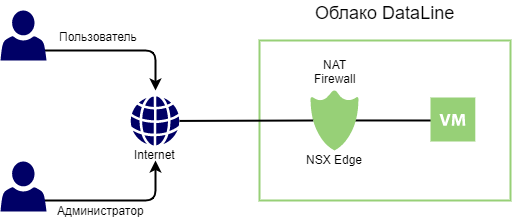
VPN If you need to connect virtual machines in the DataLine cloud with an office or other data center via a secure channel, then this is solved using a site-to-site VPN . If access to an encrypted channel is needed for a specific user from anywhere in the world, then we configure user-to-site VPN .

Butt network. It happens that a client needs to organize network connectivity between virtual machines in the DataLine cloud and physical equipment or virtual machines in a private cloud on our site. In this case, we forward the crossover and VLAN from our network equipment to the client, configure the routing between the NSX Edge from the DataLine cloud side and the network equipment (or other virtual appliance) from the client side.
All the same can be done if the client equipment is located outside the DataLine data centers. We have our own fiber optic network , so we just finish building the channel from the point of our closest presence to the client site.

Instead of NSX Edge, you can use third-party solutions - ASAv or CSR from Cisco, FortiGate, virtual Check Point, MicroTik and others. The applications hosted in the DataLine cloud will be connected via direct-internet . The Internet channel connects directly to the client organization in the cloud.

It is extremely rare that customers use this scheme without appliance to directly connect virtual machines to the Internet. Virtual machines in this case receive white IP addresses.

Direct-LAN (L2 to the cloud). This method is used when the internal network is terminated on the client side - on physical equipment or on virtual appliance. For example, a client installs a physical firewall in a rack on our site and connects our Internet channel to it. Further, the scheme is similar to a butt network, only here virtual machines are connected to the internal network directly, and not through compliance.

Direct-LAN (L2 from the cloud). This option is for cases when the client, for example, keeps databases on physical servers, and the application is in the cloud. They need to remain on the same network. To do this, the internal network from the cloud is forwarded to the physical equipment of the client.

In real projects, a combination of all these options is often used. Here are a couple of examples.
Example 1
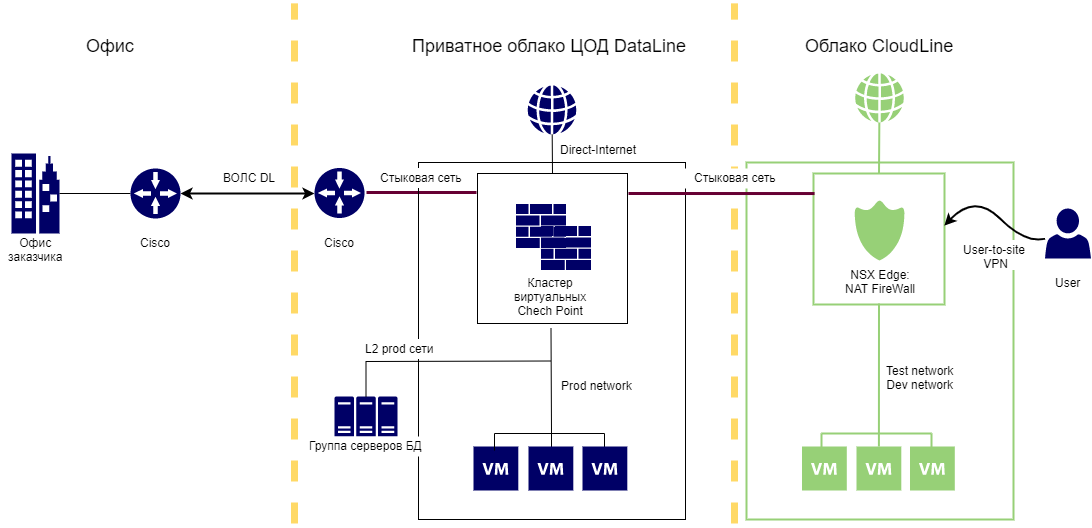
The client’s infrastructure is distributed between:
- office
- private cloud and physical servers on the DataLine site - this segment hosts the productive;
- resources in the public DataLine cloud, in which test and dev stands work.
From the client’s office to the Data Line, our optics are laid.
Between the NSX Edge in the public cloud, virtual Check Points in the private segment and the Cisco physical router on the channel to the client site, a docking network is configured. Thus, the client from the office has access to his prod-, test- and dev-stands.
In a private cloud, virtual Check Points are connected using the direct-Internet scheme. NAT rules are configured on Check Point, and through them virtual machines are published on the Internet. To connect virtual machines with physical servers, a joint is organized at the L2 level .
The public cloud uses NSX Edge, which also has NAT rules configured. For test and dev stands, a user-to-site VPN for developers is additionally configured.
Example 2
All client infrastructure is located in a public cloud. An external firewall is connected via direct-internet . On the firewall itself, NAT rules are set in the direction of the Web Application Firewall. From it, requests are sent to the balancer, which scatters them across the web servers. A site-to-site VPN is configured to access the infrastructure from the office.

All Articles