Veeam PN solution and its new features in version 2.0
What is Veeam Powered Network
The Veeam Powered Network (Veeam PN) is the technology used when running Veeam Recovery to Microsoft Azure (restoring a virtual machine to the Microsoft Azure cloud). Using Veeam PN, a VPN connection is established between the on-premises network and the Microsoft Azure network.
The technologies used are WireGuard and OpenVPN. VPN configuration and management is done through the web interface.
Veeam PN can be useful, for example, in such scenarios:
- Providing access to the corporate network through the Microsoft Azure network for remote users.
- Creating a site-to-site VPN connection between the company’s offices and the Microsoft Azure network, to which virtual machines restored to the Microsoft Azure cloud are connected.
- Create a point-to-site VPN connection between remote computers and the Microsoft Azure network, to which virtual machines restored to the Microsoft Azure cloud are connected.
For details, welcome to cat.
Usage example
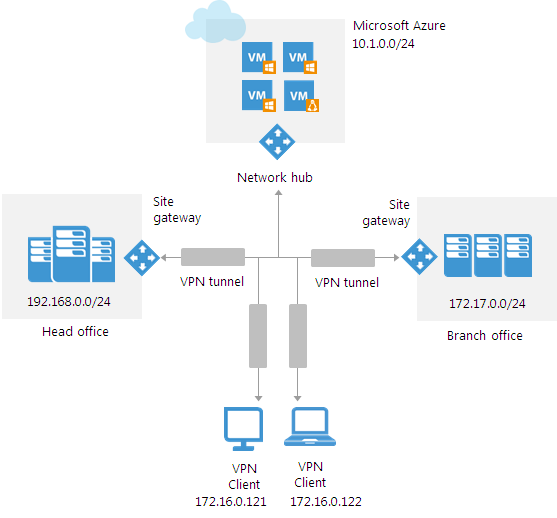
In one of the above scenarios ( site-to-site ), all VPN traffic is controlled using the Veeam components: network hub (network hub) and site gateways (gateways on sites).
A VPN that is built in this way (via Veeam PN) has a star topology. All traffic in the VPN network is always routed through the network hub.
With all this, you do not need to painstakingly configure a VPN on many machines running on remote sites - just install and set up Veeam PN. Profit!
Suppose you want to add 3 remote networks to a VPN network: 2 on-premises networks and one cloud network in Microsoft Azure. For this configuration, you need to deploy a network hub in the Microsoft Azure cloud and one gateway in each of the on-premises networks. All traffic will be routed through a network hub in the cloud.
Another example
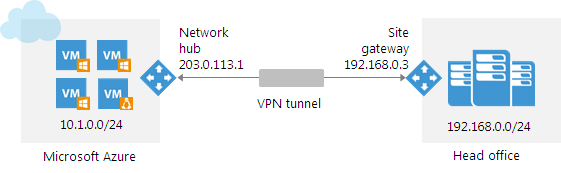
In another scenario ( site-to-site ), the network hub is configured on the network where you want to provide user access (this can be either a cloud network or an on-premises network).
To give a remote user access to a VPN network organized using the Veeam PN solution, you need to configure OpenVPN on the user machine. To communicate with a machine in a VPN network, this user must connect to a network hub, and that user will already direct traffic to the necessary resources in the VPN network.
Note that there is no need to configure a publicly accessible gateway, public IP address or DNS name.
In the picture, this scenario will look like this:

A detailed guide and description of the different use cases for Veeam PN is available here .
After getting to know this solution, users, of course, wanted something new in functionality. And here is what was implemented in version 2.0:
- Transition to WireGuard Technology
- Accordingly, improved security and increased productivity.
- Choice of protocol (TCP or UDP)
- Simplified Deployment Procedure
Transition to WireGuard Technology
In the latest version of the Veeam PN solution, we have switched from using OpenVPN to WireGuard, since WireGuard is gradually becoming the new standard in the VPN technology industry.
WireGuard scales well, supports a fairly high level of security with improved encryption, surpasses OpenVPN in bandwidth.
WireGuard developers managed to achieve such results by using the kernel directly and writing code “from scratch”, with significantly fewer lines of code (in WireGuard, there are only 4,000 lines versus 600,000 in OpenVPN).
Reliability has also increased when working with a large number of sites - this will undoubtedly come in handy for backup and replication.
Linus Torvalds himself spoke in favor of WireGuard as a de facto new standard for VPN:
"Can I just once again state my love for [WireGuard] and hope it gets merged soon? Maybe the code isn't perfect, but I've skimmed it, and compared to the horrors that are OpenVPN and IPSec, it's a work of art. ”The Veeam PN development team rewrote the source code accordingly.
Linus Torvalds, on the Linux Kernel Mailing List
“Can I once again express my love and hope that it will soon be included in the core? Maybe the code is not perfect, but compared to the horrors of OpenVPN and IPSec, it's a work of art. ”
Linus Torvalds, on the Linux Kernel mailing list
Important! At the same time, as you understand, an upgrade for users of version 1.0 has become impossible, a complete reinstallation is required.
Improved Security, Increased Productivity
One of the reasons for switching from OpenVPN to WireGuard was the improved security in WireGuard. And security is one of the key points for any VPN solution.
WireGuard uses crypto-versioning to prevent crypto attacks. The argument is as follows: during authentication it is easier to work with versions of primitives than to use client-server negotiation of the type of cipher and key lengths.
Thanks to this approach to encryption, as well as the efficiency of code with WireGuard, it is possible to achieve higher performance indicators than with OpenVPN.
This means that the new version of the Veeam PN solution can cope with significantly larger amounts of information - 5-20 times more than OpenVPN, according to test results (depending on the processor configuration). With such performance, the new technology expects a much wider range of tasks than simply transferring data from a remote office or from a home laboratory. Today Veeam PN is not only a way to establish a secure connection between several sites, but also transmit hundreds of megabits per second without interference - and this is very useful for data protection and recovery.
Choice of protocol
One of the nuances in the work of WireGuard is the use of UDP. It is believed that this may be an obstacle to the use of WireGuard in secure networks in which, by default, the use of TCP is preferable than UDP.
To overcome this limitation, our engineers came up with an encapsulation option: encrypted UDP traffic is transmitted over a TCP tunnel. Now users will have the opportunity to choose the appropriate option (work with TCP or UDP) depending on the network security settings.
Installation and configuration are very simple - WireGuard can be installed on the Ubuntu server using a script, there is also an option with embedding in the application.
Note: OpenVPN is still used for point-to-site connections ( point-to-site ), as OpenVPN clients are widely distributed across platforms. Client access to the Veeam PN hub is through OpenVPN, and the site-to-site connection (from site to site) using WireGuard (see examples above).
And something else
In addition to switching to WireGuard for site-to-site connections, Veeam PN 2.0 has other new features, in particular:
- Support for direct DNS forwarding, automatic transfer of DNS settings to client machines to determine FQDNs in all connected sites.
- Improvements in integration with Microsoft Azure.
- New deployment progress report.
useful links
- Download Veeam PN here
- User Guide and Usage Scenarios
- Solution Overview (in Russian)
All Articles