Yes, we can delete everything, no, we do not read your SMS
When they talk about MDM, which is Mobile Device Management, for some reason everyone immediately presents a kill-switch that remotely undermines a lost phone at the command of an information security officer. No, in general, this also exists, only without pyrotechnic effects. But there are still a bunch of other routine tasks that are performed with MDM much easier and more painless.
The business seeks to optimize and unify processes. And if earlier a new employee had to go to a mysterious basement with wires and bulbs, where wise red-eyed elders helped set up corporate mail on his Blackberry, now MDM has grown to an entire ecosystem that allows you to perform these tasks in two clicks. We will talk about security, cucumber-currant Coca-Cola and the differences between MDM and MAM, EMM and UEM. And also about how to remotely engage in a job selling pies.
Friday at the bar

Even the most responsible people sometimes relax. And, as often happens, they forget backpacks, laptops and mobile phones in cafes and bars. The biggest problem is that the loss of these devices can turn into a wild headache for the information security department if they contain company-sensitive information. Employees of the same Apple managed to check in at least twice, first losing the prototype iPhone 4 , and then - iPhone 5 . Yes, now most mobile phones come with encryption out of the box, but the same corporate laptops are not always configured with default encryption of the hard drive.
Plus, threats began to arise such as the targeted theft of corporate devices in order to extract valuable data. The phone is encrypted, everything is as secure as possible and all that. But did you notice the surveillance camera under which you unlocked the phone before it was stolen? Given the potential value of data on a corporate device, such threat models have become quite real.
In general, people are still sclerotics. Many companies in the United States were forced to treat laptops as consumables, which would inevitably be forgotten at a bar, hotel or at the airport. There is evidence that at the same US airports they forget about 12,000 laptops every week, of which at least half contain confidential information without any protection.
All this pretty much added gray hair to the security guards and led to the development of MDM (Mobile Device Management) at first. Then there was a need to manage the life cycle of mobile applications on controlled devices, and MAM (Mobile Application Management) solutions appeared. A few years ago they began to unite under the general name EMM (Enterprise Mobility Management) - a single system for managing mobile devices. The apogee of all this centralization is UEM (Unified Endpoint Management) solutions.
Honey we bought a zoo

The first to appear were vendors who offered solutions for centralized management of mobile devices. One of the most famous companies - Blackberry - is still alive and not feeling bad. Even in Russia it is present and sells its products, mainly for the banking sector. SAP and various smaller companies like Good Technology, later bought by Blackberry, also entered this market. At the same time, the BYOD concept was gaining popularity, when companies tried to save on the fact that employees dragged their personal devices to work.
True, it quickly became clear that technical support and information security are already startled by requests like “How do I configure MS Exchange on my Arch Linux” and “I need a direct VPN to a private Git repository and a product database from my MacBook”. Without centralized solutions, all the savings on BYOD turned into a nightmare in terms of maintaining the entire zoo. Companies needed all management to be automatic, flexible and secure.
In retail, the story has evolved a little differently. About 10 years ago, companies suddenly realized that there were mobile devices. It used to be that employees were sitting behind warm tube monitors, and somewhere nearby, a bearded owner of a sweater was invisibly present, which made it all work. With the advent of full-fledged smartphones, the functions of rare specialized PDAs can now be transferred to a regular inexpensive serial device. At the same time, it came to understand that this zoo needs to be somehow managed, since there are many platforms, and they are all different: Blackberry, iOS, Android, then Windows Phone. On a large company scale, any manual gestures are a shot in the foot. Such a process will eat valuable man-hours of IT units and support.
Vendors at the very beginning offered separate MDM products for each platform. It was quite typical that only smartphones running on iOS or Android were controlled. When we sorted it out more or less with smartphones, it turned out that the data collection terminals in the warehouse also needed to be managed somehow. At the same time, you really need to send a new employee to the warehouse so that he simply scans the barcodes on the necessary boxes and enters this data into the database. If you have warehouses throughout the country, then support has become quite difficult. It is necessary to connect each device to Wi-Fi, install the application and provide access to the database. With modern MDM, or rather EMM, you take the admin, give him the management console and configure thousands of devices with template scripts from one place.
Terminals at McDonald's
In retail, there is an interesting trend - moving away from stationary cash registers and points of registration of goods. If earlier in the same M.Video you liked the kettle, you had to call the seller and stomp with him through the entire hall to the stationary terminal. On the way, the client managed to forget ten times why he was going and change his mind. The very effect of impulsive buying was lost. Now, MDM solutions allow the seller to immediately approach the POS terminal and make a payment. The system integrates and configures warehouse terminals and sellers from a single management console. At one time, one of the first companies that began to change the model of a traditional cash register was McDonald's with its interactive self-service panels and girls with mobile terminals who took orders right in the middle of the line.
Burger King also began to develop its ecosystem by adding an application that allowed you to order remotely so that it was prepared in advance. All this was combined into a harmonious network with managed interactive racks and mobile terminals at employees.
Yourself a cashier
Many grocery hypermarkets reduce the load on cashiers by installing self-service cash registers. The Globe went further. They at the entrance offer to take the Scan & Go terminal with an integrated scanner, with which you simply scan all the goods on the spot, pack them in packages and exit, paying. It is not necessary to gut the groceries laid out in packages at the checkout. All terminals are also centrally managed and integrate with both warehouses and other systems. Some companies are trying similar solutions integrated into the trolley.
A thousand flavors
A separate song is vending machines. They must also be updated on the firmware in the same way, to monitor the remains of burnt coffee and milk powder. Moreover, synchronizing it all with the terminals of staff. Of the large companies, Coca-Cola distinguished itself in this regard, which announced a prize of $ 10,000 for the most original drink recipe. In a sense, it allowed users to mix the most addictive combinations in branded devices. As a result, there appeared options for ginger-lemon cola without sugar and vanilla-peach Sprite. Before the taste of earwax, as in Bertie Bott's Every Flavor Beans sweets, they did not seem to have reached it yet, but they were very determined. All telemetry and the popularity of each combination are carefully monitored. All this also integrates with users’s mobile applications.
We are waiting for new tastes.
We sell pies
The beauty of MDM / UEM systems is that you can quickly scale your business by connecting new employees remotely. You can very well organize the sale of conditional pies in another city with full integration with your systems in two clicks. It will look something like this.
A new device is brought to the employee. In the box is a piece of paper with a barcode. Scan - the device is activated, registered in MDM, takes the firmware, applies and restarts. The user enters his data or a one-time token. All. Now you have a new employee who has access to corporate mail, data on stock balances, necessary applications and integration with a mobile payment terminal. A person arrives at the warehouse, picks up the goods and carries it to direct customers, accepting payment using the same device. Almost like in strategies to hire a couple of new units.
What does it look like

One of the most functional UEM systems on the market is VMware Workspace ONE UEM (formerly AirWatch). It allows you to integrate with almost any mobile and desktop OS and with ChromeOS. Even Symbian was until recently. Workspace ONE also supports Apple TV.
Another important plus. Apple allows only two MDMs, including Workspace ONE, to dig into the API before launching the new version of iOS. To everyone, at best, in a month, and to them in two.
You simply set the necessary usage scenarios, connect the device, and then it works, as they say, automagically. Policies, restrictions arrive, the necessary access to internal network resources is provided, keys are filled in and certificates are installed. A few minutes later, the new employee has a device that is completely ready for work, from which the necessary telemetry is continuously pouring. The number of scenarios is huge ranging from locking the phone’s camera in a specific geolocation to SSO by fingerprint or face.
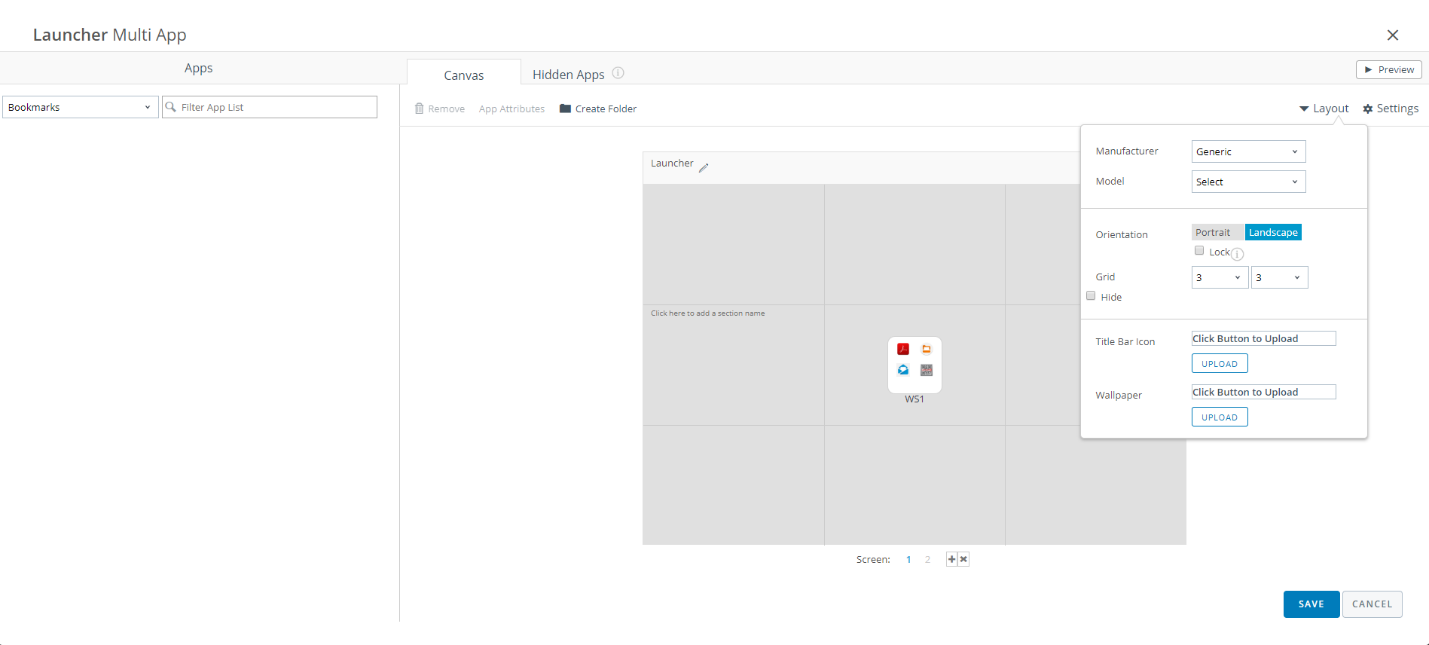
The admin configures the launcher with all the applications that fly to the user.

All possible and impossible parameters, such as the size of the icons, the ban on their movement, the ban on the icon of the call and contacts, are also flexibly configured. Such functionality is useful when using the Android platform as an interactive menu in a restaurant and similar tasks.
From the user's side it looks something like this 

Other vendors have interesting solutions. For example, EMM SafePhone from NII SOKB provides certified solutions for the secure transmission of voice and messages with encryption and recording.
Routed Phones
A headache for information security are rooted phones, where the user has maximum rights. No, purely subjective, this is an ideal option. Your device should give you full control rights. Unfortunately, this runs counter to corporate tasks that require the user to be unable to influence corporate software. For example, he should not be able to get into a protected section of memory with files or slip in a fake GPS.
Therefore, all vendors in one way or another try to detect any suspicious activity on the managed device and block access when it detects root rights or non-standard firmware.
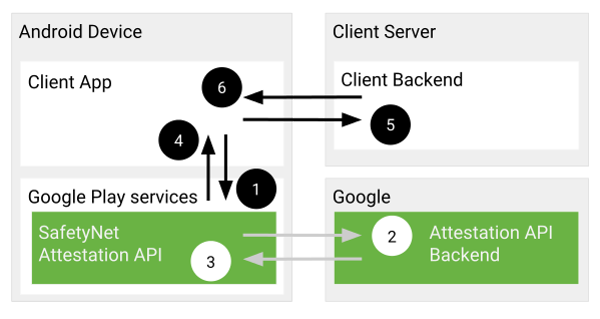
Android typically relies on the SafetyNet API . From time to time, the same Magisk allows you to circumvent its checks, but, as a rule, Google fixes it very quickly. As far as I know, the same Google Pay did not work again on rooted devices after the spring update.
Instead of output
If you are a large company, then you should consider introducing UEM / EMM / MDM. Current trends suggest that such systems are finding wider application - from locked iPad as terminals in the confectionery to large integrations with warehouse bases and courier terminals. A single point of management and quick integration or a change in the role of an employee give very big advantages.
My mail is SVinogradskiy@croc.ru
All Articles