Silent Trinity: exploring a new version of the post-exploitation framework

We constantly monitor changes in hacker tools, whether it is the emergence of new tools or updating existing ones. Therefore, we could not pass by Silent Trinity , announced at DefCon 27 Demo Labs.
What is it and why to study
PT ESC experts deliver knowledge to the company's products and teach them how to detect TTP (tactics, techniques, and procedures) attackers. The post exploitation stage is an integral part of any compromise. Therefore, we consider it our duty to discover such an interesting tool as Silent Trinity. In addition, previously PT ESC experts have already found cases of real attacks using it.
The Silent Trinity post-exploitation framework received an update in the new version 0.3.0. Key innovations are client-server architecture and multi-user mode. Hackers love the framework for using DLR (Dynamic Language Runtime).

Thanks to DLR, implants get more flexibility and stealth compared to C #. At the moment, C2 communication with the victim can occur through four transports - HTTP, HTTPS, DNS, WMI.
How the new Silent Trinity works
We conducted a study of the latest version of the tool in order to find detection options and came to the conclusion: despite all the advantages, Silent Trinity can still be detected both by activity on the host and by network interaction. Let's start with the last one. Typically, HTTPS is selected as the transport. At first launch, Silent Trinity generates a self-signed TLS certificate, which is later used when communicating with a compromised system. Such a certificate will always contain the same information field values.
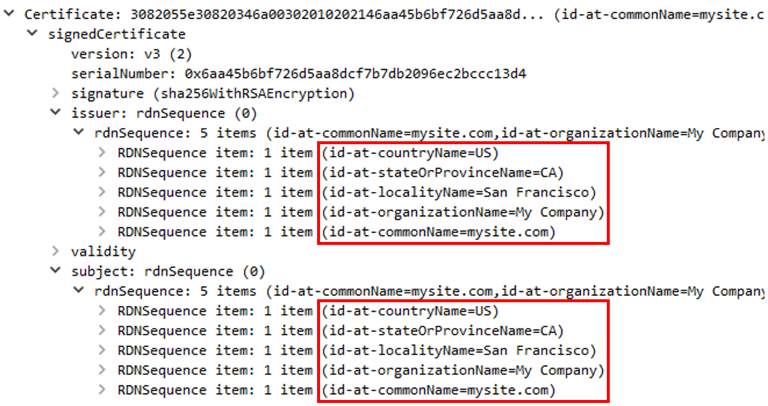
Also unusual in the certificate is its lifetime (9999 days) and the SubjectAlternativeName field with the value 'localhost'.
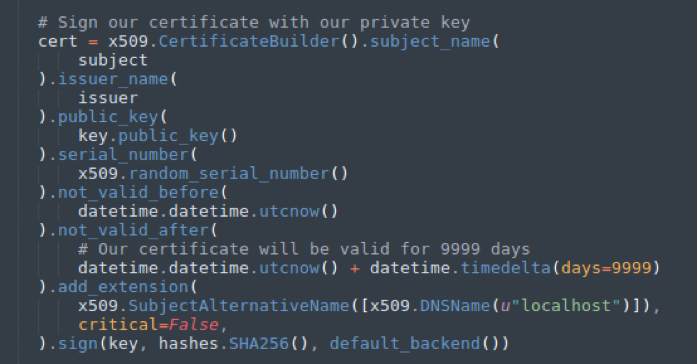
The implant can be launched through powershell, msbuild or wmic. To do this, create a file that is launched by one of the tools. Regardless of how it is launched, the file will contain a serialized base64 format object. It is he who sends the request to C2 to get the payload that will serve as the transport. The victim receives the load, performs the main body of the implant. Such an approach using DLR is really not easy to detect, but there are ways to get event tracing through ETW (Event Tracing for Windows).
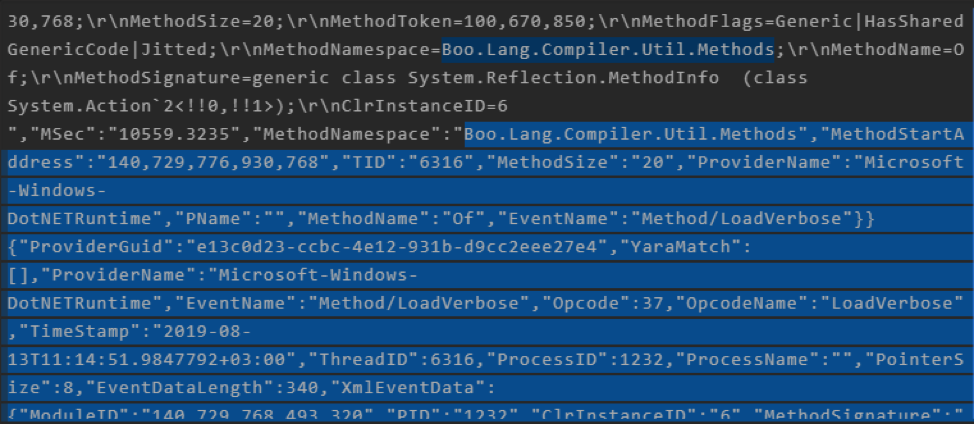
Thanks to this, you can discover the use of the Boo language, in which the implant functions and payload modules are written. Boo itself is a Python-like OOP language and is rare.
Thus, for the new version of Silent Trinity, a number of unique parameters are gathered that help to detect its use.
After the update, as well as Demo Labs on Defcon 27, the number of references to the tool on thematic forums and channels increased, which indicates the growing popularity of Silent Trinity. Therefore, it is possible to increase the number of attacks involving the framework.
PT ESC experts recommend using the MaxPatrol SIEM and PT Network Attack Discovery tools, they already implemented the necessary checks in the form of rules and correlations.
All Articles