Detection of vulnerabilities and assessment of resistance to hacker attacks of smart cards and crypto processors with built-in protection
Over the past decade, in addition to methods for extracting secrets or performing other unauthorized actions, attackers began to use unintentional data leakage and manipulation of the program execution process through side channels.
Traditional attack methods can be expensive in terms of knowledge, time, and processing power. Side channel attacks, on the other hand, can be more easily implemented and non-destructive, as they reveal or control the physical properties that are available during normal functioning.
Using statistical methods for processing side channel measurements or by entering failures into the closed channels of a microcircuit, an attacker can gain access to its secrets within a few hours.

More than 5,000 million smart cards are issued annually, new built-in cryptographic technologies appear on the markets, so the need to ensure the security of both business and privacy is growing.
In the Netherlands, Riscue has created the Inspector system, which provides research laboratories as well as manufacturers with new, high-performance security threat detection tools.
The Inspector system supports various side channel analysis (SCA) methods such as power analysis (SPA / DPA), clock, radio frequency, and electromagnetic analysis (EMA) and disturbance attacks (FI) such as voltage failures, clock failures, and laser manipulation. The system’s built-in functions support numerous cryptographic algorithms, application protocols, interfaces, and instrumentation.
The system allows you to expand and implement new methods and proprietary applications for vulnerability detection.
After the measurement results are obtained, a variety of signal processing methods are available to form multiple traces with a high level of signals and a low noise level. Signal processing functions have been developed that take into account the subtle differences between electromagnetic trace signal processing, power consumption trace, and RF (RF) trace. Inspector’s powerful graphical trace presentation tools allow users to temporarily analyze or verify traces, for example, for SPA vulnerabilities.
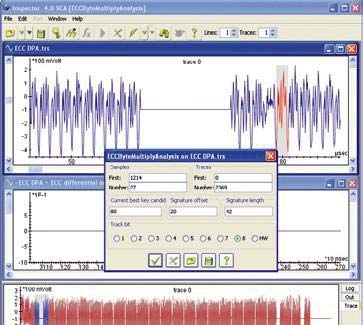
DPA implementation with ECC implementation
For many security implementations that are nowadays considered SPA-resistant, the focus of testing is usually on differential test methods (i.e. DPA / CPA ). To this end, Inspector offers a wide range of configurable methods regarding a large number of cryptographic algorithms and widely used algorithms such as (3) DES, AES, RSA and ECC.
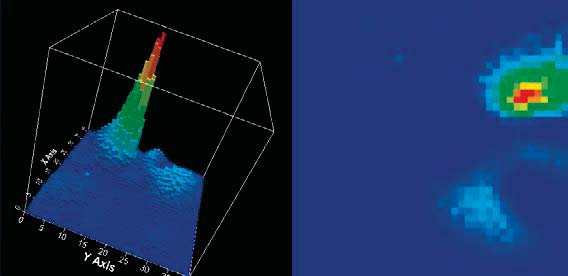
EM radiation from the chip to find the best location when implementing DEMA
In addition to the workstation, the PC Inspector SCA uses hardware optimized for side channel data and signal collection:
Evaluated objects often require measurements, switching, and hardware controls that are required to perform SCA. The Inspector’s flexible hardware manager, open development environment and broad interface options provide a solid foundation for high-quality measurements using user equipment.
Inspector SCA
Joh John Connor, lead internal security engineer, speaks of the system as follows:
“The Inspector has fundamentally changed the way we evaluate the resilience of our products to a differential energy attack differential DPA. Its strength lies in the fact that it integrates the collection and analysis processes that allow us to quickly evaluate the effectiveness of new cryptographic hardware projects. Moreover, its excellent graphical interface allows the user to visualize power signatures from collected discrete data individually or simultaneously - which is invaluable when preparing data for DPA during an attack - while its powerful analytic libraries support the most commonly used commercial encryption algorithms. Riscure’s timely software and technology updates help us keep our products safe. ”
Inspector FI - Fault Injection - offers a wide range of features to perform fault testing on smart cards and embedded devices. Supported test methods include clock failures, voltage failures, and optical attacks using laser equipment. Failure attacks - also known as disturbance attacks - modify the behavior of the chip, causing usable failure.
Using the Inspector FI, users can test whether it is possible to extract the key by causing failures in the cryptographic operations of the chip, bypass a check such as authentication or the life cycle state, or change the program execution process on the chip.
Inspector FI includes a large number of user-configurable parameters for programmatically controlling switching and disturbances, such as peak pulses of different durations, pulse repetition, and voltage level changes. The software presents the results, showing expected behavior, card discards, and unexpected behavior, along with detailed logging. DFA attack modules are available for basic encryption algorithms. Using a “wizard”, users can also create a custom perturbation program with an API.
Inspector FI can be used with the following hardware components to conduct attacks:

Inspector FI with VC Glitcher fault generator, icWaves trigger generator, Glitch Amplifier and Laser Station
The VC Glitcher generates the core of the Inspector system failover architecture. Using ultra-fast FPGA technology, faults of just two nanoseconds can be generated. The hardware has a user-friendly programming interface. The crash program created by the user is loaded into the FPGA before the test run. The VC Glitcher includes an integrated circuit for introducing voltage and clock faults, as well as a channel output for controlling the laser station.
The diode laser station consists of a special set of high-power diode lasers with custom-made optics, which are quickly and flexibly controlled by the VC Glitcher. The equipment takes optical testing to a new level, providing effective multiple failures, precise control of power consumption and a quick and predictable response for switching pulses.
By updating the diode laser station to the multi-drop version, several areas can be tested on the chip using various parameters for synchronization and supply voltage.
Clock jitter, random process interruptions, and data-dependent process durations require flexible failover and side-channel data collection. The Inspector icWaves generator generates a trigger pulse in response to real-time detection of differences from a given model in the power supply of the microcircuit or EM signal. The device includes a special narrow-band filter to ensure detection of model matching even with a noisy signal.
The reference trace used to match the model inside the FPGA-based device can be modified using the Inspector signal processing functions. A smart card that detects a malfunction can initiate a security mechanism to remove sensitive data or block the card. The icWaves component can also be used to initiate a shutdown of the card each time the power consumption or EM profile deviates from standard operation.

Laser Station Laser Station (LS) with Multipoint Access,
with microscope and coordinate table
The Inspector development environment is designed to provide maximum flexibility to the user using SCA and FI for any purpose.

Inspector fi
Inspector combines failover and side channel analysis techniques in one high-performance package.
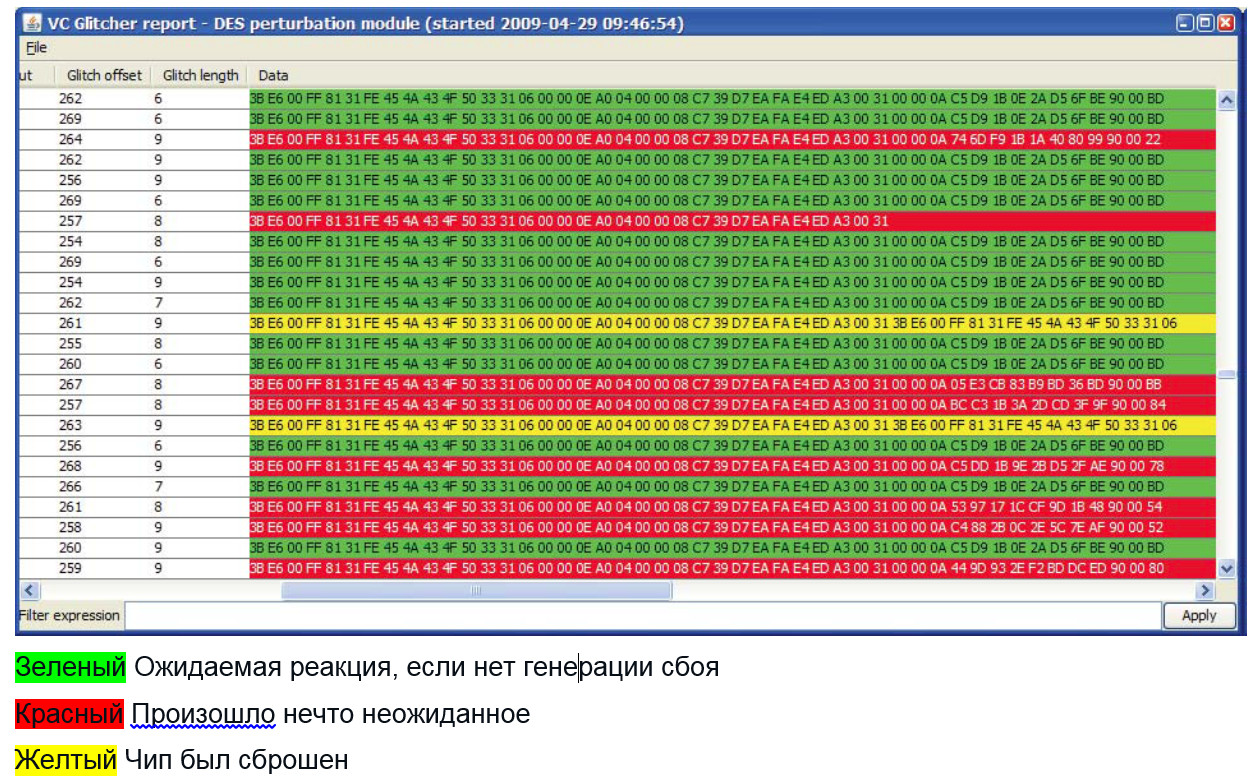
An example of failure behavior analysis:
The area of attack through side channels is developing rapidly, and new research results are published every year, become well-known or make certification of schemes and standards mandatory. Inspector allows users to keep abreast of new developments and regular software updates that implement new methods.
Traditional attack methods can be expensive in terms of knowledge, time, and processing power. Side channel attacks, on the other hand, can be more easily implemented and non-destructive, as they reveal or control the physical properties that are available during normal functioning.
Using statistical methods for processing side channel measurements or by entering failures into the closed channels of a microcircuit, an attacker can gain access to its secrets within a few hours.

More than 5,000 million smart cards are issued annually, new built-in cryptographic technologies appear on the markets, so the need to ensure the security of both business and privacy is growing.
In the Netherlands, Riscue has created the Inspector system, which provides research laboratories as well as manufacturers with new, high-performance security threat detection tools.
The Inspector system supports various side channel analysis (SCA) methods such as power analysis (SPA / DPA), clock, radio frequency, and electromagnetic analysis (EMA) and disturbance attacks (FI) such as voltage failures, clock failures, and laser manipulation. The system’s built-in functions support numerous cryptographic algorithms, application protocols, interfaces, and instrumentation.
The system allows you to expand and implement new methods and proprietary applications for vulnerability detection.
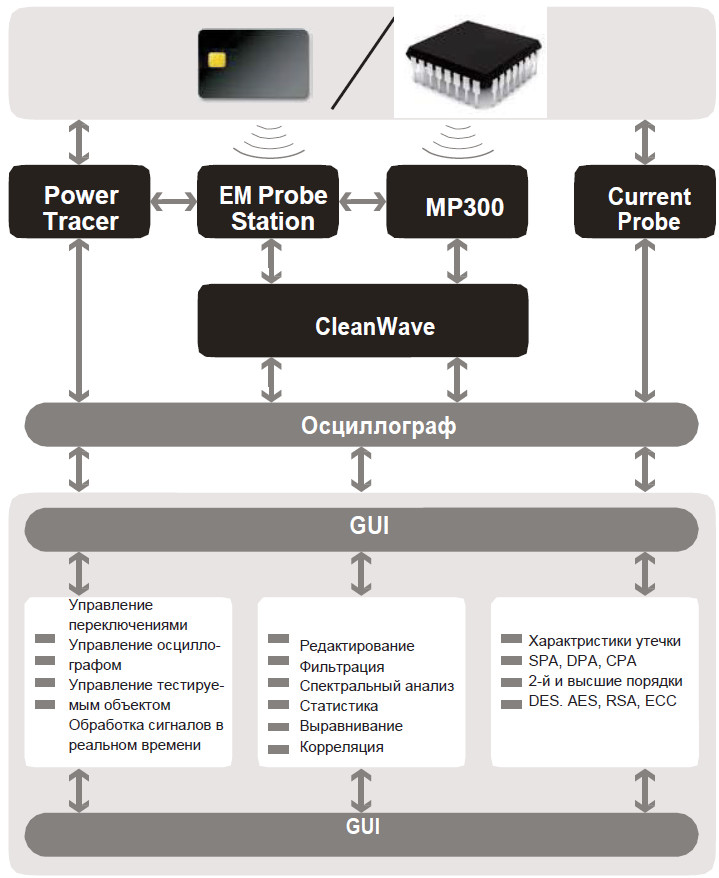
The Inspector SCA side channel analysis system includes:
- Power Tracer Power Tracer
- installation of electromagnetic sounding EM Probe Station;
- trigger generator icWaves;
- CleanWave Filter
- current probe Current Probe.
Among the main "goodies" can distinguish the main:
- This is a single integrated tool for side channel analysis and testing by introducing failures;
- Inspector meets the requirements for side channel testing, certified by EMVco and CMVP according to common criteria;
- This is an open environment that includes the source code of modules, thereby allowing you to modify existing methods and include new testing methods that can be developed by the user for the Inspector;
- Stable and integrated software and hardware includes high-speed data collection across millions of traces;
- A six-month software release cycle allows users to keep abreast of the latest field channel testing methods.
Inspector is available in various versions on a single platform:
- Inspector SCA offers all the necessary options for analyzing DPA and EMA side channels.
- Inspector FI offers full fault logging functionality (perturbation attacks) as well as differential fault analysis ( DFA ).
- Inspector Core and SP (signal processing) offer SCA core functionality, implemented as separate modules, to provide an affordable software package for data collection or post-processing.
Inspector SCA
After the measurement results are obtained, a variety of signal processing methods are available to form multiple traces with a high level of signals and a low noise level. Signal processing functions have been developed that take into account the subtle differences between electromagnetic trace signal processing, power consumption trace, and RF (RF) trace. Inspector’s powerful graphical trace presentation tools allow users to temporarily analyze or verify traces, for example, for SPA vulnerabilities.

DPA implementation with ECC implementation
For many security implementations that are nowadays considered SPA-resistant, the focus of testing is usually on differential test methods (i.e. DPA / CPA ). To this end, Inspector offers a wide range of configurable methods regarding a large number of cryptographic algorithms and widely used algorithms such as (3) DES, AES, RSA and ECC.

EM radiation from the chip to find the best location when implementing DEMA
Key Features
- This solution combines power analysis (SPA / DPA / CPA), electromagnetic (SEMA / DEMA / EMA-RF), and non-contact test methods (RFA).
- The speed of data acquisition is greatly enhanced by the tight integration of the oscilloscope with the Inspector.
- Improved Alignment Techniques Used to Prevent Jitter and Randomization
- The user can configure cryptanalysis modules that support primary attacks and high-order attacks on all major algorithms, such as (3) DES, AES, RSA and ECC.
- Expanded support for area-specific algorithms is used, including SEED, MISTY1, DSA, including Camellia.
Hardware
In addition to the workstation, the PC Inspector SCA uses hardware optimized for side channel data and signal collection:
- Power Tracer for SPA / DPA / CPA on smart cards
- EM Probe station for SEMA / DEMA / EMA RF
- Current Probe for SPA / DPA / CPA on embedded devices
- CleanWave Filter with Micropross MP300 TCL1 / 2 for RFA and RF EMA
- IVI compatible oscilloscope
Evaluated objects often require measurements, switching, and hardware controls that are required to perform SCA. The Inspector’s flexible hardware manager, open development environment and broad interface options provide a solid foundation for high-quality measurements using user equipment.

Inspector SCA
Joh John Connor, lead internal security engineer, speaks of the system as follows:
“The Inspector has fundamentally changed the way we evaluate the resilience of our products to a differential energy attack differential DPA. Its strength lies in the fact that it integrates the collection and analysis processes that allow us to quickly evaluate the effectiveness of new cryptographic hardware projects. Moreover, its excellent graphical interface allows the user to visualize power signatures from collected discrete data individually or simultaneously - which is invaluable when preparing data for DPA during an attack - while its powerful analytic libraries support the most commonly used commercial encryption algorithms. Riscure’s timely software and technology updates help us keep our products safe. ”
Inspector fi
Inspector FI - Fault Injection - offers a wide range of features to perform fault testing on smart cards and embedded devices. Supported test methods include clock failures, voltage failures, and optical attacks using laser equipment. Failure attacks - also known as disturbance attacks - modify the behavior of the chip, causing usable failure.
Using the Inspector FI, users can test whether it is possible to extract the key by causing failures in the cryptographic operations of the chip, bypass a check such as authentication or the life cycle state, or change the program execution process on the chip.
Extensive configurable options
Inspector FI includes a large number of user-configurable parameters for programmatically controlling switching and disturbances, such as peak pulses of different durations, pulse repetition, and voltage level changes. The software presents the results, showing expected behavior, card discards, and unexpected behavior, along with detailed logging. DFA attack modules are available for basic encryption algorithms. Using a “wizard”, users can also create a custom perturbation program with an API.
Key Features
- Non-parallel and easily reproducible accuracy and synchronization for all glitching hardware.
- Attack design scenarios using a powerful command system and integrated IDE Inspector.
- Extensive Inspector configuration options for automated failover testing.
- Laser equipment for multi-glitching on the back and front of the card, custom-made for testing by the method of making a failure.
- DFA modules for implementations of popular encryption algorithms, including RSA, AES, and 3DES
- Upgrading to a multipoint laser provides the ability to affect the chip in several places at once.
- Operation-specific synchronization using the icWaves trigger generator can prevent countermeasures and prevent sample loss.
Hardware
Inspector FI can be used with the following hardware components to conduct attacks:
- VC Glitcher with optional fault amplifier
- Diode laser station with optional multi-drop update
- PicoScope 5203 or IVI compatible oscilloscope

Inspector FI with VC Glitcher fault generator, icWaves trigger generator, Glitch Amplifier and Laser Station
The VC Glitcher generates the core of the Inspector system failover architecture. Using ultra-fast FPGA technology, faults of just two nanoseconds can be generated. The hardware has a user-friendly programming interface. The crash program created by the user is loaded into the FPGA before the test run. The VC Glitcher includes an integrated circuit for introducing voltage and clock faults, as well as a channel output for controlling the laser station.
The diode laser station consists of a special set of high-power diode lasers with custom-made optics, which are quickly and flexibly controlled by the VC Glitcher. The equipment takes optical testing to a new level, providing effective multiple failures, precise control of power consumption and a quick and predictable response for switching pulses.
By updating the diode laser station to the multi-drop version, several areas can be tested on the chip using various parameters for synchronization and supply voltage.
Signal-based triggering using icWaves trigger pulse generator
Clock jitter, random process interruptions, and data-dependent process durations require flexible failover and side-channel data collection. The Inspector icWaves generator generates a trigger pulse in response to real-time detection of differences from a given model in the power supply of the microcircuit or EM signal. The device includes a special narrow-band filter to ensure detection of model matching even with a noisy signal.
The reference trace used to match the model inside the FPGA-based device can be modified using the Inspector signal processing functions. A smart card that detects a malfunction can initiate a security mechanism to remove sensitive data or block the card. The icWaves component can also be used to initiate a shutdown of the card each time the power consumption or EM profile deviates from standard operation.

Laser Station Laser Station (LS) with Multipoint Access,
with microscope and coordinate table
Integrated Development Environment (IDE)
The Inspector development environment is designed to provide maximum flexibility to the user using SCA and FI for any purpose.
- Open API: simplifies implementation of new modules
- Source code: each module comes with its own source code, so the modules can be adapted to the user's wishes or used as the basis for creating new modules

Inspector fi
Inspector combines failover and side channel analysis techniques in one high-performance package.
An example of failure behavior analysis:

The area of attack through side channels is developing rapidly, and new research results are published every year, become well-known or make certification of schemes and standards mandatory. Inspector allows users to keep abreast of new developments and regular software updates that implement new methods.
All Articles