Tom Hunter's Diary: The Hound of the Baskervilles
Delaying with signing is a common thing for any large company. An exception was not an agreement between Tom Hunter and one online pet store for a thorough pentesting. It was necessary to check both the site, and the internal network, and even working Wi-Fi.
It is not surprising that the hands were combed before all formalities were settled. Well, just scan the site just in case, it’s unlikely that such a well-known store as the “Baskervilov Dog” will make mistakes here. After a couple of days, Tom nevertheless delivered the signed original contract - at this time, behind the third cup of coffee, Tom from the internal CMS assessed with interest the condition of the warehouses ...
 Source: Ehsan Taebloo
Source: Ehsan Taebloo
But it was not possible to manage especially in CMS - the site administrators banned the IP of Tom Hunter. Although one could have time to generate bonuses on the store’s card and feed the beloved cat for cheap for months ... “Not this time, Darth Sidious,” thought Tom with a smile. It would be no less fun to go from the zone of the website to the local network of the customer, but apparently these segments are not connected with the client. Still, this happens more often in very large companies.
After all the formalities, Tom Hunter armed himself with the provided VPN account and went to the customer’s local network. The account was inside the Active Directory domain, so it was possible to take and without any tricks to dump AD - to merge all public information about users and working machines.
Tom launched the adfind utility and started sending LDAP requests to the domain controller. With a filter by class objectategory, specifying person as an attribute. The answer returned here with this structure:
In addition, there was still a lot of useful information, but the most interesting was in the> description:> description field. This account comment is, in principle, a convenient place to store minor notes. But the client’s administrators felt that passwords could also rest here calmly. Who, after all, might be interested in all of these minor service records? Therefore, the comments that Tom received looked like:
You do not need to be seven spans in the forehead to understand why the combination is useful at the end. It remained to parse a large response file from the CD by the field> description: and here they are - 20 login-password pairs. Moreover, almost half have RDP access rights. Good foothold, time to split the attacking forces.
The accessible Baskerville Dogs balls resembled a big city in all its chaos and unpredictability. With user and RDP profiles, Tom Hunter was a poor boy in this city, but even he managed to look at a lot of things through the shining windows of security policies.
Parts of file servers, accounting accounts, and even scripts associated with them - all this has been shared. In the settings of one of these scripts, Tom found the MS SQL hash of one user. A bit of brute force magic - and the user's hash turned into a plain text password. Thanks to John The Ripper and Hashcat.

This key should have come to some chest. The chest was found, and moreover, ten more “chests” were connected with it. And inside six lay ... superuser rights, nt authority \ system! On two, I managed to run the stored procedure xp_cmdshell and send cmd commands to Windows. What more could you want?
Tom Hunter has prepared the second blow for domain controllers. There were three of them in the Baskerville Dogs network, in accordance with the number of geographically remote servers. Each domain controller has a public folder, like an open storefront in a store, next to which the same impoverished boy Tom hangs around.
And this time the guy was lucky again - they forgot to remove the script from the window where the password of the local server admin was hardcoded. So the path to the domain controller was open. Come in, Tom!
Here, a mimikatz was extracted from the magic hat, which was profitable by several domain administrators. Tom Hunter got access to all the machines on the local network, and a fiendish laugh scared the cat from a nearby chair. This path was shorter than expected.
The memory of WannaCry and Petya is still alive in the minds of pentesters, but some admins seem to have forgotten about cryptographers in the stream of other evening news. Tom discovered three nodes with a vulnerability in the SMB protocol - CVE-2017-0144 or EternalBlue. This is the same vulnerability with the help of the WannaCry and Petya ransomware, a vulnerability that allows arbitrary code to be executed on a host. At one of the vulnerable sites there was a domain admin session - “exploit and get.” What can you do, time has not taught everyone.

Information security classics like to repeat that the weakest point of any system is a person. Notice that the title above does not match the store name? Perhaps not everyone is so careful.
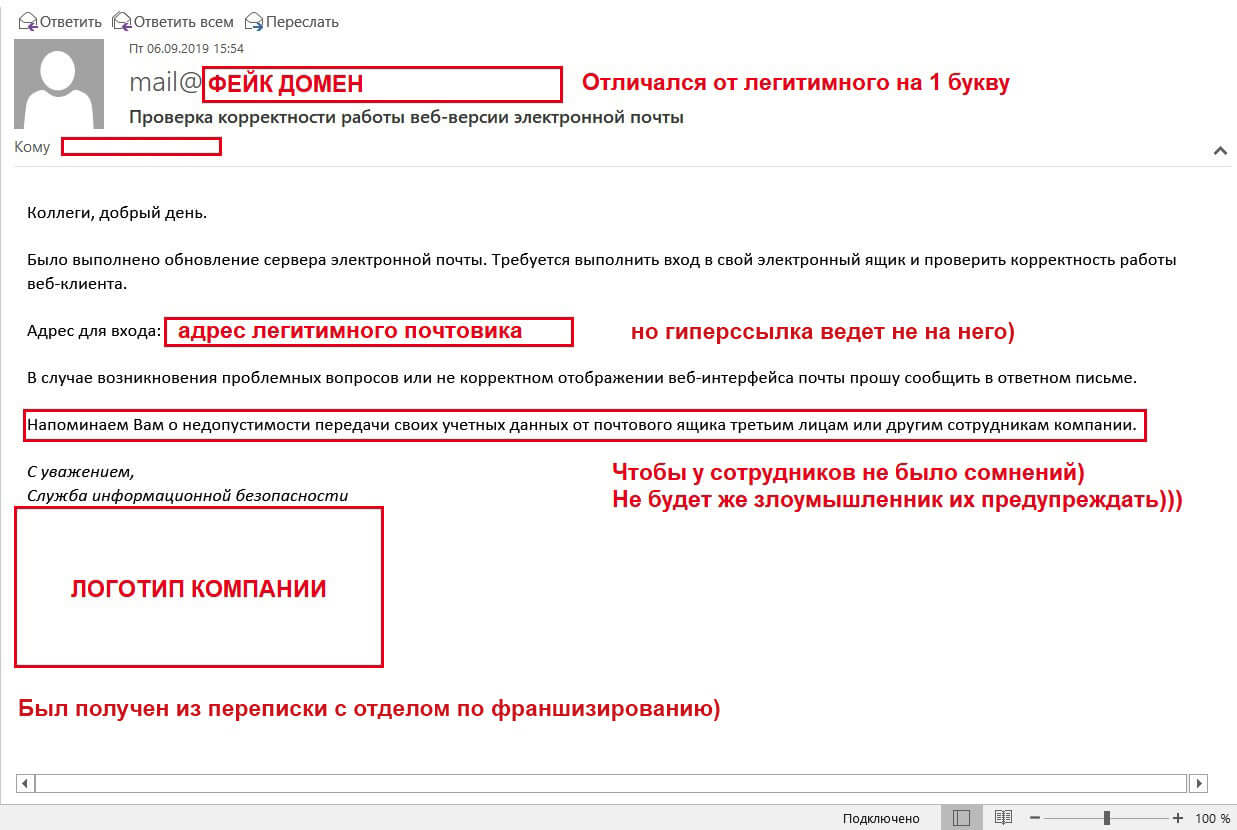
In the best tradition of phishing blockbusters, Tom Hunter has registered a domain one letter different from the Baskerville Dogs domain. The mailing address on this domain simulated the address of the store’s information security service. Within 4 days from 4:00 p.m. to 5:00 p.m., a message like this was sent evenly to 360 addresses from a fake address:
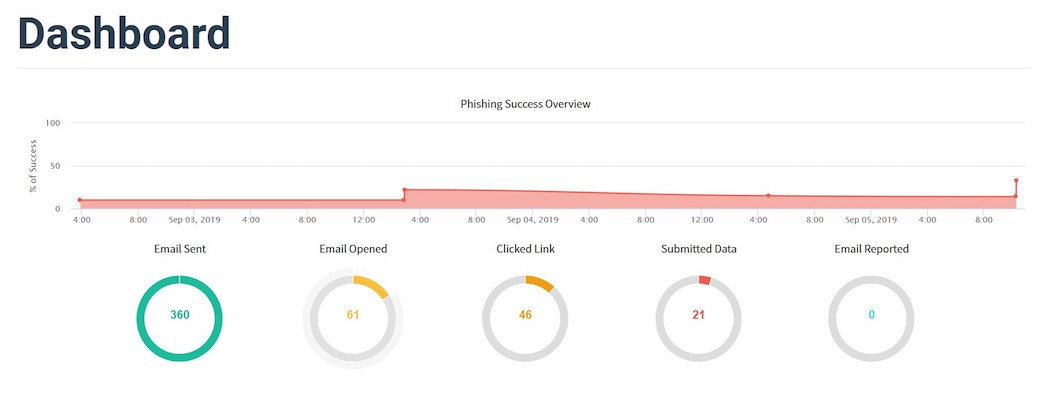
Perhaps, only their own laziness saved the employees from mass dumping of passwords. Out of 360 letters, only 61 were opened - the security service is not very popular. But then it was easier.
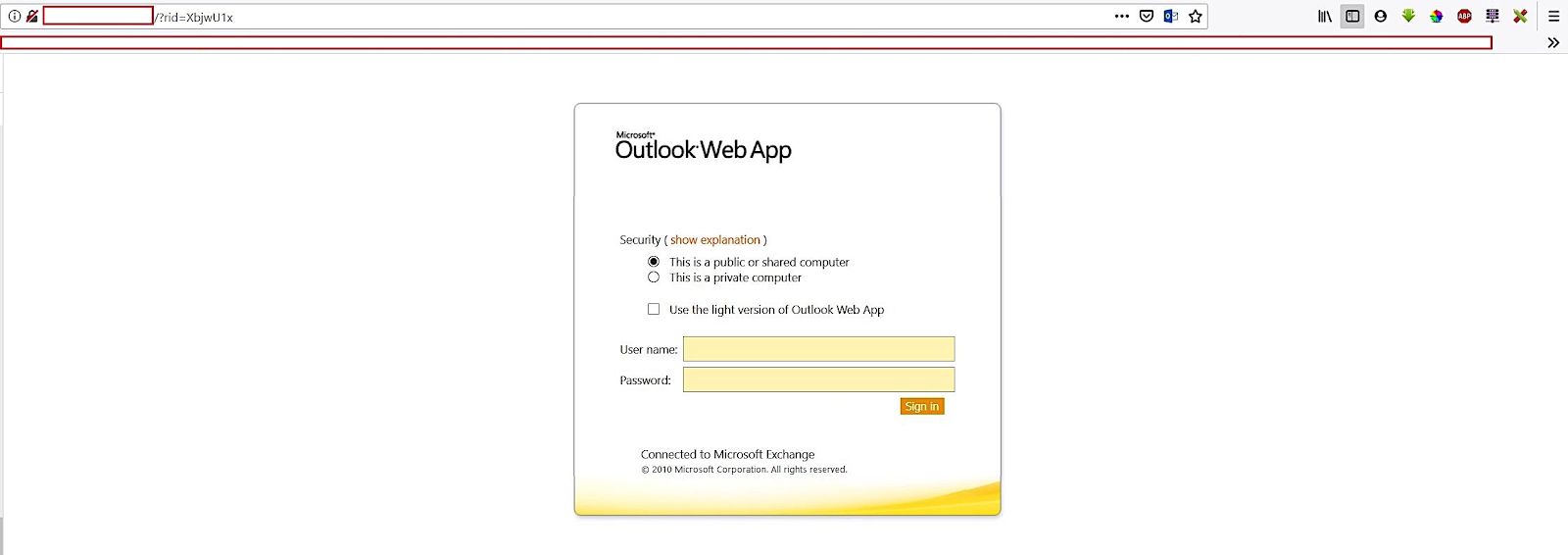
Phishing page
46 people clicked on the link and almost half - 21 employees - did not look into the address bar and calmly entered their usernames and passwords. Good catch, Tom.
Now I did not have to rely on the help of a cat. Tom Hunter threw a few pieces of iron into his old sedan and headed for the Baskerville Dogs office. His visit was not agreed: Tom was going to test the customer’s Wi-Fi. In the parking lot of the business center, there were several free spots that successfully entered the perimeter of the target network. Apparently, they didn’t especially think about its restriction - as if administrators randomly poked additional dots in response to any complaint about weak Wi-Fi.
How does WPA / WPA2 PSK work? The encryption between the access point and the clients provides a pre-session key - Pairwise Transient Key (PTK). PTK uses the Pre-Shared Key and five other parameters - SSID, Authenticator Nounce (ANounce), Supplicant Nounce (SNounce), MAC addresses of the access point and client. Tom intercepted all five parameters, and now only the Pre-Shared Key was missing.

The Hashcat utility got this missing link in about 50 minutes - and our hero found himself in a guest network. From it one could already see the worker - strangely enough, here Tom managed the password for nine minutes. And all this without leaving the parking lot, without any VPN. The working network opened our hero open spaces for monstrous activity, but he ... did not throw bonuses on the store card.
Tom paused, looked at his watch, threw a couple of banknotes on the table and, saying goodbye, left the cafe. Maybe again a pentest, or maybe I decided to write to the telegram channel ...
It is not surprising that the hands were combed before all formalities were settled. Well, just scan the site just in case, it’s unlikely that such a well-known store as the “Baskervilov Dog” will make mistakes here. After a couple of days, Tom nevertheless delivered the signed original contract - at this time, behind the third cup of coffee, Tom from the internal CMS assessed with interest the condition of the warehouses ...
 Source: Ehsan Taebloo
Source: Ehsan Taebloo
But it was not possible to manage especially in CMS - the site administrators banned the IP of Tom Hunter. Although one could have time to generate bonuses on the store’s card and feed the beloved cat for cheap for months ... “Not this time, Darth Sidious,” thought Tom with a smile. It would be no less fun to go from the zone of the website to the local network of the customer, but apparently these segments are not connected with the client. Still, this happens more often in very large companies.
After all the formalities, Tom Hunter armed himself with the provided VPN account and went to the customer’s local network. The account was inside the Active Directory domain, so it was possible to take and without any tricks to dump AD - to merge all public information about users and working machines.
Tom launched the adfind utility and started sending LDAP requests to the domain controller. With a filter by class objectategory, specifying person as an attribute. The answer returned here with this structure:
dn:CN=,CN=Users,DC=domain,DC=local >objectClass: top >objectClass: person >objectClass: organizationalPerson >objectClass: user >cn: >description: >distinguishedName: CN=,CN=Users,DC=domain,DC=local >instanceType: 4 >whenCreated: 20120228104456.0Z >whenChanged: 20120228104456.0Z
In addition, there was still a lot of useful information, but the most interesting was in the> description:> description field. This account comment is, in principle, a convenient place to store minor notes. But the client’s administrators felt that passwords could also rest here calmly. Who, after all, might be interested in all of these minor service records? Therefore, the comments that Tom received looked like:
, 2018.11.16 7po!*Vqn
You do not need to be seven spans in the forehead to understand why the combination is useful at the end. It remained to parse a large response file from the CD by the field> description: and here they are - 20 login-password pairs. Moreover, almost half have RDP access rights. Good foothold, time to split the attacking forces.
network environment
The accessible Baskerville Dogs balls resembled a big city in all its chaos and unpredictability. With user and RDP profiles, Tom Hunter was a poor boy in this city, but even he managed to look at a lot of things through the shining windows of security policies.
Parts of file servers, accounting accounts, and even scripts associated with them - all this has been shared. In the settings of one of these scripts, Tom found the MS SQL hash of one user. A bit of brute force magic - and the user's hash turned into a plain text password. Thanks to John The Ripper and Hashcat.

This key should have come to some chest. The chest was found, and moreover, ten more “chests” were connected with it. And inside six lay ... superuser rights, nt authority \ system! On two, I managed to run the stored procedure xp_cmdshell and send cmd commands to Windows. What more could you want?
Domain controllers
Tom Hunter has prepared the second blow for domain controllers. There were three of them in the Baskerville Dogs network, in accordance with the number of geographically remote servers. Each domain controller has a public folder, like an open storefront in a store, next to which the same impoverished boy Tom hangs around.
And this time the guy was lucky again - they forgot to remove the script from the window where the password of the local server admin was hardcoded. So the path to the domain controller was open. Come in, Tom!
Here, a mimikatz was extracted from the magic hat, which was profitable by several domain administrators. Tom Hunter got access to all the machines on the local network, and a fiendish laugh scared the cat from a nearby chair. This path was shorter than expected.
Eternalblue
The memory of WannaCry and Petya is still alive in the minds of pentesters, but some admins seem to have forgotten about cryptographers in the stream of other evening news. Tom discovered three nodes with a vulnerability in the SMB protocol - CVE-2017-0144 or EternalBlue. This is the same vulnerability with the help of the WannaCry and Petya ransomware, a vulnerability that allows arbitrary code to be executed on a host. At one of the vulnerable sites there was a domain admin session - “exploit and get.” What can you do, time has not taught everyone.

The Basterville Dog
Information security classics like to repeat that the weakest point of any system is a person. Notice that the title above does not match the store name? Perhaps not everyone is so careful.
In the best tradition of phishing blockbusters, Tom Hunter has registered a domain one letter different from the Baskerville Dogs domain. The mailing address on this domain simulated the address of the store’s information security service. Within 4 days from 4:00 p.m. to 5:00 p.m., a message like this was sent evenly to 360 addresses from a fake address:

Perhaps, only their own laziness saved the employees from mass dumping of passwords. Out of 360 letters, only 61 were opened - the security service is not very popular. But then it was easier.

Phishing page
46 people clicked on the link and almost half - 21 employees - did not look into the address bar and calmly entered their usernames and passwords. Good catch, Tom.

Wi-Fi network
Now I did not have to rely on the help of a cat. Tom Hunter threw a few pieces of iron into his old sedan and headed for the Baskerville Dogs office. His visit was not agreed: Tom was going to test the customer’s Wi-Fi. In the parking lot of the business center, there were several free spots that successfully entered the perimeter of the target network. Apparently, they didn’t especially think about its restriction - as if administrators randomly poked additional dots in response to any complaint about weak Wi-Fi.
How does WPA / WPA2 PSK work? The encryption between the access point and the clients provides a pre-session key - Pairwise Transient Key (PTK). PTK uses the Pre-Shared Key and five other parameters - SSID, Authenticator Nounce (ANounce), Supplicant Nounce (SNounce), MAC addresses of the access point and client. Tom intercepted all five parameters, and now only the Pre-Shared Key was missing.

The Hashcat utility got this missing link in about 50 minutes - and our hero found himself in a guest network. From it one could already see the worker - strangely enough, here Tom managed the password for nine minutes. And all this without leaving the parking lot, without any VPN. The working network opened our hero open spaces for monstrous activity, but he ... did not throw bonuses on the store card.
Tom paused, looked at his watch, threw a couple of banknotes on the table and, saying goodbye, left the cafe. Maybe again a pentest, or maybe I decided to write to the telegram channel ...
All Articles