PVS-Studio 7.04

Summer is not only a vacation season, but also a time of fruitful work. Sunny days are so energized that they have enough energy for late walks and voluminous code commits. The second summer release of PVS-Studio 7.04 turned out to be quite large, so we bring to your attention a press release in which we will talk about everything.
PVS-Studio is a tool for detecting errors and potential vulnerabilities in the source code of programs written in C, C ++, C # and Java. Works in the environment of Windows, Linux and macOS.
The capabilities of the analyzer are well demonstrated by the extensive collection of errors in the code that we found during the verification of various open-source projects.
We bring to your attention an overview of the new features included in the PVS-Studio 7.04 release.
Search files with Copyleft licenses
Developers from where they just do not get the code, working on the task. A popular source for Copy-Paste code is the Stackoverflow site and the like. But there may be situations where the programmer takes the code from the Open Source project and does not check the license requirements. Thus, several files from the Open Source project with Copyleft-license may accidentally get into a closed-source project, i.e. obliging to make all project code public. In companies with a large number of employees, this is difficult to keep track of, and risks and problems can be serious due to such actions. So, in PVS-Studio for all supported languages (C, C ++, C #, Java), diagnostics have appeared that will help to find such files.
Diagnostic numbers for different languages:
Let's dwell on these diagnostics in more detail and analyze what they are made for. An example of a comment on which the analyzer will issue a warning:
/* This program is free software: you can redistribute it and/or modify * it under the terms of the GNU General Public License as published by * the Free Software Foundation, either version 3 of the License, or * (at your option) any later version. * * This program is distributed in the hope that it will be useful, * but WITHOUT ANY WARRANTY; without even the implied warranty of * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the * GNU General Public License for more details. * * You should have received a copy of the GNU General Public License * along with this program. If not, see <https://www.gnu.org/licenses/>. */
For closed projects
If you add a file with such a license (GPL3 in this case) to a closed project, then the rest of the source code will need to be opened, due to the nature of this license.
This type of copyleft license is called a " viral " license, due to its ability to spread to other project files. The problem is that using at least one file with a similar license in a closed project automatically makes all the source code open and requires you to distribute it along with the binary files.
Diagnostics searches for the following “viral” licenses:
- AGPL-3.0
- GPL-2.0
- GPL-3.0
- LGPL-3.0
There are the following options, what you can do when you discover the use of files with copyleft license in a closed project:
- Refuse to use this code (library) in your project;
- Replace the used library;
- Make your project open.
For open source projects
We understand that this diagnosis is not appropriate for open source projects. The PVS-Studio team contributes to the development of open projects, helps to fix errors in them , and provides free license options . However, our product is a B2B solution and therefore this diagnostic is enabled by default.
If your code is distributed under one of the above copyleft licenses, then you can disable this diagnostics in the following ways (for C \ C ++ it is V1042):
- If you use the PVS-Studio plug-in for Visual Studio, then by going to Options> PVS-Studio> Detectable Errors> 1.General Analysis> V1042, you can disable the display of this diagnostic in the analyzer output window. The disadvantage of this method is that the error will still be written to the analyzer log when it is saved (or if the analysis was launched from the command line). Therefore, when opening such a log on another machine or converting the analysis results to a different format, messages disabled in this way may appear again.
- If you do not use the plugin, you want to block the rule for the entire command or remove its messages from the analyzer report, then you can add the comment "// - V :: 1042" to the configuration file (.pvsconfig) or to one of the global header files. For developers using Visual C ++, a good option would be to add this comment to the stdafx.h file. This comment tells the analyzer to disable the V1042 diagnostic. For more information on disabling diagnostics using comments, see the documentation .
- If the Plog Converter utility is used to convert reports, you can turn off diagnostics using the "-d" switch.
For C #, it means V3144, respectively, and for Java - V6071.
Adding to the list of dangerous licenses
If you also know the types of “viral” licenses that the tool does not currently detect, then you can inform us about them through the feedback form . And we will add their identification in the next release.
New diagnostics
C, C ++ (General)
- V1040 . Possible typo in the spelling of a pre-defined macro name.
- V1041 . Class member is initialized with dangling reference.
- V1042 . This file is marked with copyleft license, which requires you to open the derived source code.
- V1043 . A global object variable is declared in the header. Multiple copies of it will be created in all translation units that include this header file.
Separately, I want to note the diagnostics with the number V1040 . Even in beta status, she already found an interesting error in the library of the well-known CMake project:
V1040 Possible typo in the spelling of a pre-defined macro name. The '__MINGW32_' macro is similar to '__MINGW32__'. winapi.h 4112
/* from winternl.h */ #if !defined(__UNICODE_STRING_DEFINED) && defined(__MINGW32_) #define __UNICODE_STRING_DEFINED #endif
Here they made a typo in the name __MINGW32_ . In the end, one underscore is missing. If you search by code with this name, you can make sure that the project actually uses the version with two underscores on both sides:
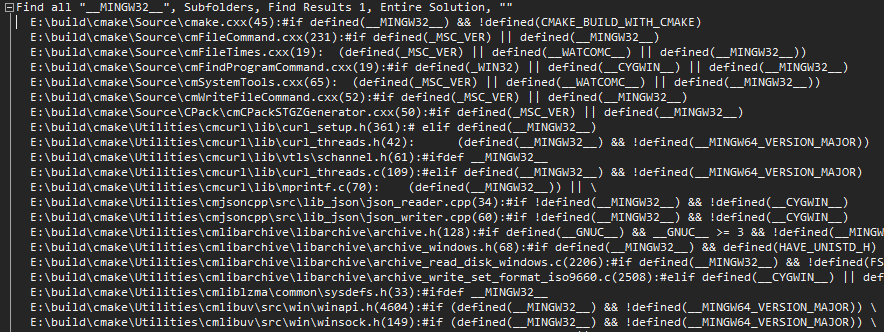
You can see all the errors found in the CMake project in the article " CMake: the case when the quality of its code is inexcusable to the project ."
C, C ++ (MISRA)
- V2551 . Misra. Variable should be declared in a scope that minimizes its visibility.
- V2552 . Misra. Expressions with enum underlying type should have values corresponding to the enumerators of the enumeration.
- V2553 . Misra. Unary minus operator should not be applied to an expression of the unsigned type.
- V2554 . Misra. Expression containing increment (++) or decrement (-) should not have other side effects.
- V2555 . Misra. Incorrect shifting expression.
- V2556 . Misra. Use of a pointer to FILE when the associated stream has already been closed.
- V2557 . Misra. Operand of sizeof () operator should not have other side effects.
C #
- V3140 Property accessors use different backing fields.
- V3141 . Expression under 'throw' is a potential null, which can lead to NullReferenceException.
- V3142 . Unreachable code detected. It is possible that an error is present.
- V3143 . The 'value' parameter is rewritten inside a property setter, and is not used after that.
- V3144 . This file is marked with copyleft license, which requires you to open the derived source code.
- V3145. Unsafe dereference of a WeakReference target. The object could have been garbage collected before the 'Target' property was accessed.
Also in the C # analyzer, the calculation of return / write values from get and set property access methods and async methods has been added.
We are currently working on improving tracking of field values and properties of objects when passing them to methods, as well as tracking the contents of tuples. These improvements will be available in the next release of the analyzer.
Java
- V6068 Suspicious use of BigDecimal class.
- V6069 Unsigned right shift assignment of negative 'byte' / 'short' value.
- V6070 Unsafe synchronization on an object.
- V6071 This file is marked with copyleft license, which requires you to open the derived source code.
SonarQube 7.9 LTS
Long-awaited release
Almost 2 years have passed since the last release of the LTS version of SonarQube 6.7. A new version was expected with special zeal, starting with SQ 7.x, and when the LTS release took place, users began to actively switch to it, which caused various problems. SQ 7.9.1 LTS was soon released with minor fixes, and third-party plugin developers also prepared patches.
Fortunately, there was only one small problem in the PVS-Studio plugin related to the transition to Java 11, which we quickly fixed, and our customers immediately switched to a working version.
We also maintained compatibility with older versions of SonarQube, and the list of supported versions now looks like this: SonarQube 6.7 LTS and higher .
More language plugins supported
The PVS-Studio plugin only converts the analysis results into the format of the SonarQube database. In other words, it simply loads the PVS-Studuio analysis results into SQ. But for the full operation of the SonarScanner utility, plug-ins for programming languages must be installed. We did not begin to develop what already exists, therefore we simply add support for already existing popular plugins. In this version, we added compatibility with the Sonar C Community and SonarCFamily language plugins.
The entire list of supported language plugins looks like this:
- Sonar C ++ Community
- Sonar c community
- SonarC #
- Sonarjava
- SonarCFamily (SQ Developer Edition)
To download PVS-Studio analysis results, it is enough to install at least one plugin from this list. Most users only need to install the Sonar C ++ Community, SonarC # or SonarJava. Other plugins may be needed for more specific projects.
When choosing plugins, it is necessary to take into account the fact that Community plugins are not compatible with SonarCFamily. But if you use only SonarQube Community Edition, then such a problem will not arise.
New settings page
Previously, you could configure the analyzer only through the sonar-project.properties configuration file. There are no complaints about this method. It is very convenient and is used in 99% of cases, but we additionally made the settings page in Administration> Configuration> PVS-Studio on the SonarQube server, because It is also convenient to use in some scenarios.
The settings page looks like this:
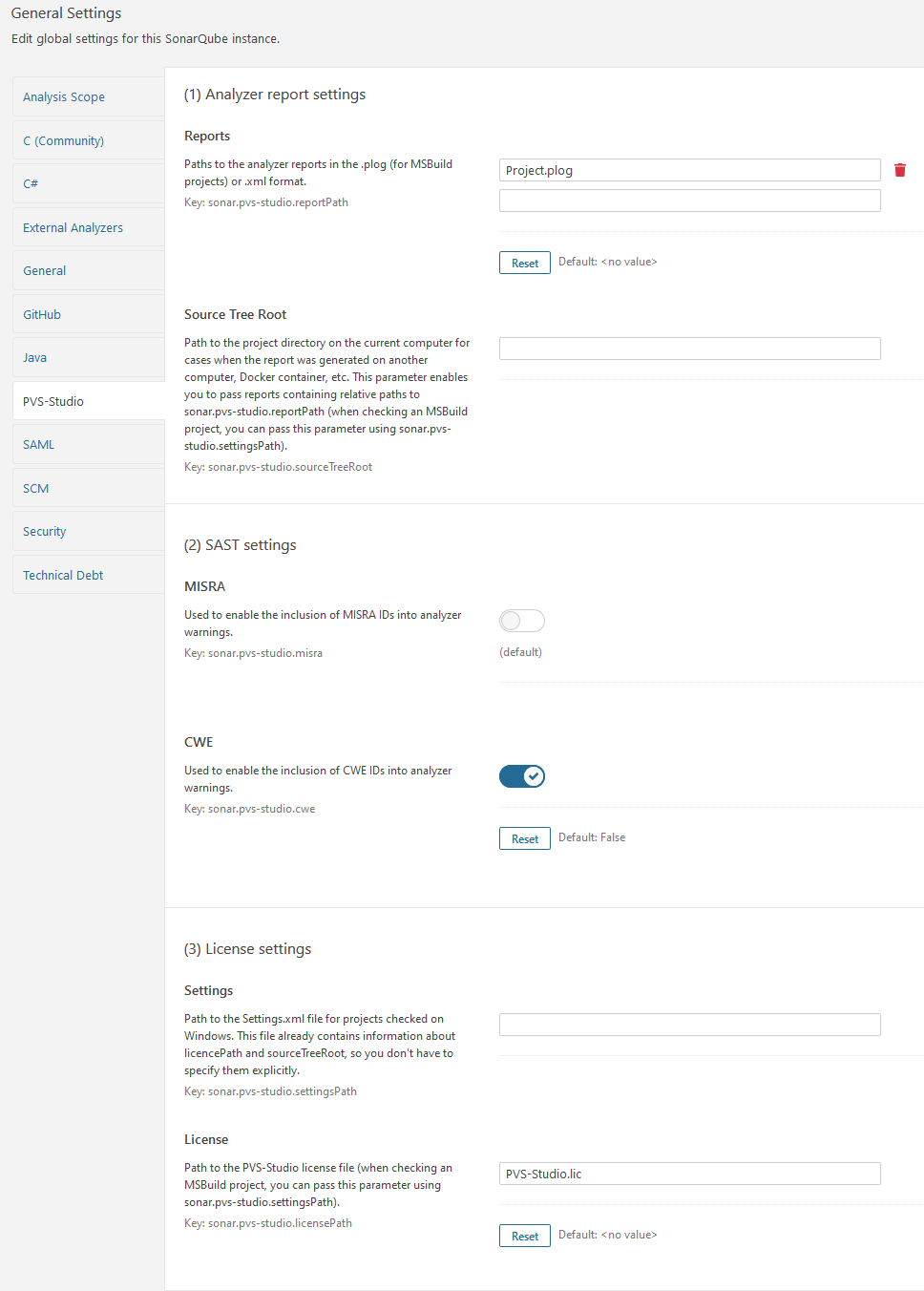
When setting the settings in two ways, the priority is given to those specified in the sonar-project.properties file.
Plugin for IntelliJ IDEA
Releases of new IntelliJ IDEA and PVS-Studio versions differ in dates, and recently there was a situation when IntelliJ IDEA 192. * was released, but the PVS-Studio plug-in was not installed on it. In this release, we added support for the latest version of IntelliJ IDEA, and also made improvements to avoid similar problems in the future.
Plugins for Jenkins
PVS-Studio Plugin
PVS-Studio Plugin is designed to publish the results of the PVS-Studio analyzer in the Jenkins continuous integration system in HTML format. Previously, this plugin was available only to Windows users, as called the report converter automatically and did it only for Windows. In PVS-Studio 7.04, the plugin only supports HTML reports, which must be generated in a separate step, but this made the plugin cross-platform.
Warnings NG Plugin
For Jenkins, there is a useful Warnings Next Generation Plugin plugin for viewing analysis results from various tools. Recently we added support for PVS-Studio in it. The ability to load PVS-Studio analysis results using this plugin became available in version 6.0.0 , the release of which coincided with the release of PVS-Studio 7.04:
Other improvements
PVS-Studio_Cmd
A special operating mode - credentials was added to PVS-Studio_Cmd.exe . This mode allows you to create a settings file and enter license information without using a GUI interface (for example, a plug-in for Visual Studio or the utility C and C ++ Compiler Monitoring UI). This mode is especially relevant when used on a build server (where the GUI utilities may not be described), in containers, and when integrated with cloud solutions.
Analysis of Unreal Engine Projects
In the PVS-Studio plug-in for Visual Studio, the AutoloadUnrealEngineLog option was added, the inclusion of which allows you to automatically load the analyzer report into the PVS-Studio output window after passing the analysis. Without this option, log loading must be done manually through the plugin menu.
Also, in the documentation section " Testing Unreal Engine Projects ", changes to standard assembly scripts were described that allow assembly and analysis in one action. Without modifying the scripts (when adding the -StaticAnalyzer = PVSStudio flag to the startup arguments), only the project is analyzed, without having to build it.
CLMonitor
For the CLMonitor utility, the ability to track compiler launches for a specific process has been added. This will allow you to track the starts of compilers related only to a specific project, even when building several projects in parallel. To work in this mode, the flags --parentProcessID% PID% (CLMonitor monitors processes that are children relative to the specified) and --attach (CLMonitor monitors processes that are child relative to the current console) are used.
pvs-studio-analyzer
The --ignore-ccache flag has been added to the pvs-studio-analyzer utility, which is designed to check projects on Linux and macOS:
pvs-studio-analyzer analyze ... --ignore-ccache ...
If the ccache utility is used in the project assembly, then PVS-Studio operates in incremental analysis mode. To check the project completely without dropping the ccache utility cache , use this flag.
Sitelinks
To keep abreast of our new publications, we invite you to subscribe to us:
- Twitter: pvsstudio_rus
- VKontakte: PVS-Studio analyzer
- Facebook: @StaticCodeAnalyzer
- Instagram: @pvsstudio_rus
- Telegram: PVS-Studio rus
- RSS: viva64-blog-en
PVS-Studio:
If you want to share this article with an English-speaking audience, then please use the link to the translation: Svyatoslav Razmyslov. PVS-Studio 7.04 .
All Articles
