Summ3r of h4ck 2019. Security Analysis Department
The summer program Summ3r of h4ck 2019 has ended, and it is time to take stock. In this article we will tell you what results the trainees of the security analysis department have achieved.

Here you can see the results of past years:
We adhered to the previous practice: the participants were offered a list of topics on which they could work during the passage of the program. Someone had their own interesting idea for research, and we were always ready to discuss it.
So, how did the selection go to the department? The first stage is to fill out the questionnaire, which we posted on the company's website . It contained 10 interesting tasks. They helped to evaluate the level of preparation of the person, his knowledge and some practical skills.
In collaboration with Korgik_0, we have already made a detailed analysis of entrance tests ; In addition, a system for evaluating responses and some interesting statistics are presented. Therefore, we will not dwell on them again, but rather move on to the most interesting.
Our employeesbreak down neighboring Wi-Fi, conduct penetration tests in corporate networks, analyze the security of web applications and corporate software, and carefully look at the source code, including mobile and banking applications. (from)
This year, there were a lot of people who wanted to participate, including from other cities. Geographically, Summ3r of h4ck always takes place in the beautiful city of St. Petersburg.
This year’s recruitment included both new and already familiar faces: someone had already undergone a student internship at our university and had now dealt with the qualification questionnaire at a decent level, and someone in previous years had visited us on Summ3r of h4ck looked in. We are always happy to observe the professional growth of young professionals, especially if we ourselves contribute to this :)
An important part of the training is lectures from our employees. The lecture list of the security analysis department this year was something like this:
The participants themselves also acted as lecturers - closer to the completion of Summ3r of h4ck, they made presentations about the results of their research, shared the problems that arose in the process of work, and told what goals were achieved. Several people teamed up and worked on projects together.
In addition, we have developed a laboratory environment in which you can practice the skills of practical information security. Tasks are not only useful, but also important - at the end of Summ3r of h4ck 2019, the program manager looks at the overall statistics and identifies those people who completed the most tasks. This, as you understand, affects later on the selection of candidates for Digital Security.
All successful speakers were solemnly awarded the Summ3r of h4ck 2019 certificate of completion.

Those who successfully reached the finals, we were asked to take a short survey for us.
The spelling, punctuation and style of the authors are preserved.
1. Often noticed the company on the Internet on its publications and research. I got the impression as a company where there is a real opportunity to engage in practically applicable research activities in information security.
2. I liked the internship. I have long wanted myself in prof. areas that would help me to develop and at the same time bring some benefit to the community. The project, which I was engaged in, just gave such an opportunity. Reality coincided with better expectations.
3. I participated in writing cheats on mitm attacks, took up the network level, which I had long wanted to pump in the security context.
4. The tasks are very interesting, give a lot of freedom, since the first task is to figure it out for yourself in order to convey it to people normally.
5. Ready to return to the internship, possibly to work.
The results of the study can be found here (the project is under active editing and development).
1. I am very interested in working on tasks that can be used in practice. I love practical tasks in the framework of information protection (and not only protection :)). In addition, it is always a pleasure to work with smart people who know and know more than you :)
2. I really liked the internship, now I have a lot more knowledge about javascript in my head - and I got them myself in practice. I usually thought js was something boring, but now I know that it is not.
I especially remembered how I tested the ICMP redirect attack - it turns out that some distributions are still vulnerable to it (although the attack is very ancient)
3. I managed to participate in two tasks - compiling mitm cheatsheet and javascript fullscreen phishing. As part of the first, we made up a small cheat sheet on mitm attacks, checking them and selecting funds for them. And as part of the second, we made a small phishing page similar to the password entry window in windows 7 - it turned out interesting :)
4. It is a pity that only I was very busy at work - there was little time for solving tasks. We managed to finish the projects only partially - we’ll finish them in the fall, it turned out quite interesting.
5. Return to the company for an internship - be sure next year. At work - it would also be interesting, the only obstacle is that I live in Arkhangelsk :)))
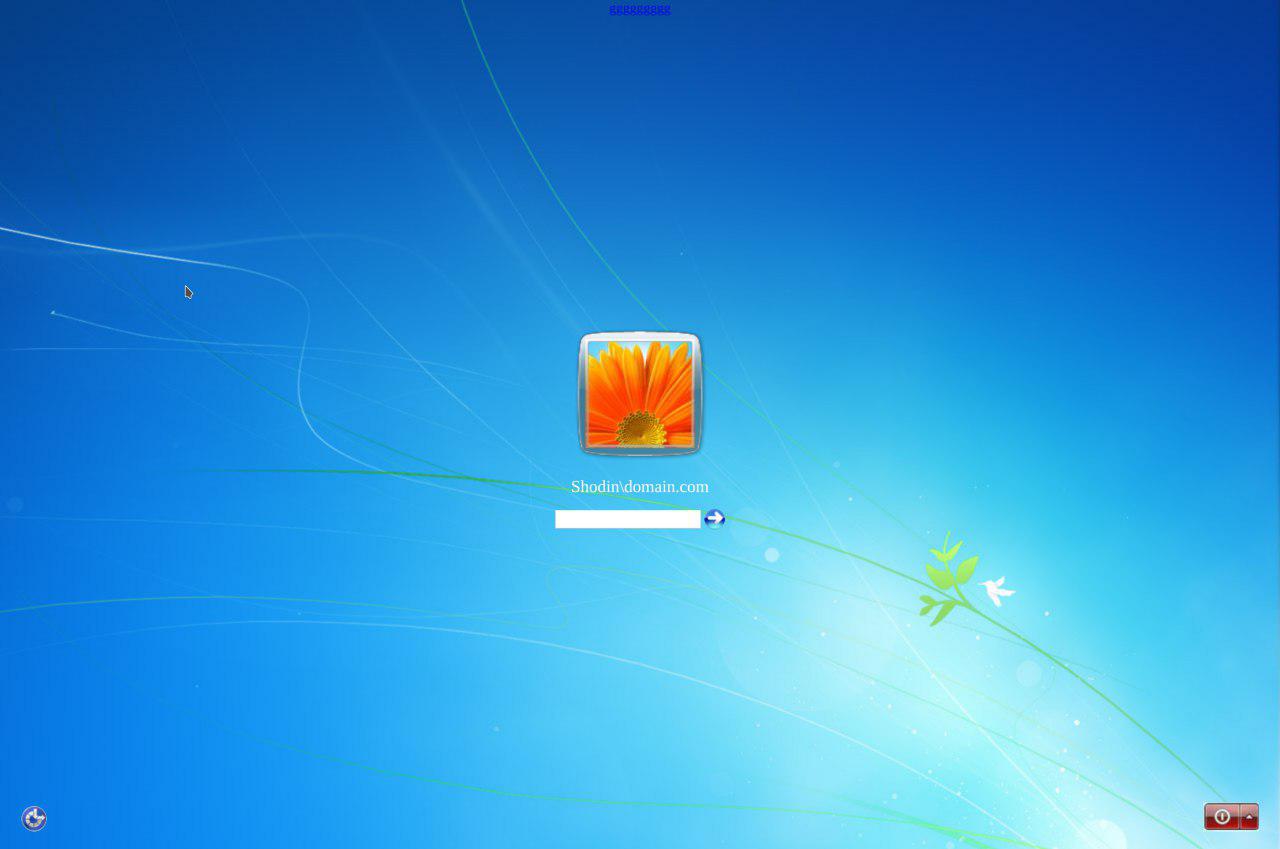
Phishing page in the layout process
1. Digital Security Company allows you to realize the dream of almost any CTF-filer - this gives you the opportunity to do what you love at the professional level. Answering the question “What attracted the company?” - just this opportunity.
2. Due to the extremely high cost of the trip, which consists of moving, living, and in general the cost of living in the city, and only because of this I can not overestimate this program. I would rate it at 3.8-4.3 points. The estimation coefficient consisted of such a formula - new knowledge / money spent = utility.
Just to make you understand. In order for me to come to your program I will have to pay about 55 thousand rubles. That's too much. This money can be used for advanced training or for training prof. English language. This is stupidly more profitable than “summer of hack”. I think the company should pay attention to Sirius as a platform for training students. And take an example from colleagues at Solar Security. I tend to the fact that these programs are completely free for students. Which is a huge plus. You know, I didn’t have the “student-teacher” interaction. It would be a huge plus in karma for the teacher, and not only him, if there was an exchange of experience on the project. Perhaps the curator already had experience with the cloud or he has some developments on this topic (the same review would be a good help).
3. The goal of the project - the essence of my work is to find weaknesses in configuring AWS. And based on the problems found, writing a script to map the cloud infrastructure.
4. Of course, for myself, I chose projects in which I could start from scratch. And answering the question of whether it was interesting to me - of course.
5. I think at “summer of hack 2020” I would come back again to test myself. Check on what level I am now. It’s too early to talk about employment, because I need about 2 years to finish my studies and another year to put together the nth amount for moving to St. Petersburg. But in any case, Digital Security will be a priority place of employment.

Black color - implemented; Red color - not implemented
1. I decided to do internship in DSek because it is one of the few companies that provide a cool opportunity to practice practical safety while still a student. I also attracted a large list of publications by company specialists on various resources (most of them were Habr, of course) and their participation in bugbount programs.
2. I really liked the internship, and reality definitely exceeded expectations. The lectures were very interesting and useful, a lot of new information. The labs were fascinating and complex, after them the cars on the HackTheBox will probably seem easy.
3. My task was to add modules to the utility used in pentests to collect useful information from a captured machine. I implemented the collection of information from popular network clients ( PuTTY , MobaXterm , FileZilla ), extracted hosts, user names, keys. Link to the module.
He also wrote a port scanner available to the client on the external network. Such a scanner is needed if a firewall is used on the network that blocks access to certain ports. The client part of the scanner is trying to connect to the specified list of ports. The server side receives incoming tcp packets, establishes a connection and writes down the port number to which the packets arrived. On this side, we work with raw tcp sockets, as it is faster and more interesting in writing :)
4. Work on the tasks was very interesting. For example, write on a previously unknown Golang, deal with the device fields of tcp packets, and study asynchronous run. It would be nice to learn how to decrypt the data of MobaXterm, FileZilla programs, but the reverse of such voluminous projects is difficult for a beginner pentester). Also, there was not enough time to completely deal with asynchronism, but I think I will do it in the near future.
5. Yes, definitely! Many thanks to the organizers for an interesting summer)

1. The friends gave me the idea to send the questionnaire, saying that the company is one of the leading companies in the information security market, in addition, the projects will be very interesting, and this is a great opportunity to raise the skill.
2. I liked it, and reality exceeded my expectations. A great atmosphere in the office, friendly relations with employees and other interns, an exciting work process - that’s what remains in memory.
3. I worked on the topic “Golang Social Bot” - a bot used in penetration testing. The main goal was to write modules that collect useful data, somehow interact with computer resources.
4. There were a large number of tasks, some easier, some more difficult, but no less interesting. It seems to me that a lot of work has been done, although, summing up, I understand that I could have done even more.
5. Of course! The internship provides an excellent opportunity to delve into not only the topic of your project, but also to develop skills, gain knowledge on other topics, for which many thanks to the company!
1. After playing CTF for a year, I decided to try myself on real projects. I saw an internship from Digital Security, became interested. By that time, many people whom I knew already worked there, which gave confidence in my decision.
2. Yes! There were many interesting lectures, as well as a “lab” in which there were many wheelbarrows. It was possible to apply the knowledge gained at lectures for breaking machines from the lab.
3. My topic was the creation of a security sheet for the Kubernetes cluster.
The main misconfiguration, what to enable, so that it is "secured" and so on.
4. Of course. Having studied previous studies, I realized that they were partially outdated or were carried out on older versions of kubernetes, where most secure features are not enabled by default. In the new versions, it was difficult to find something that is a “out of the box” hole. I looked at the study from the other side and began to rely on a typical scenario with vulnerable applications. After all, we must protect data first, not the cluster. As a result, I found options that could complicate the life of the attacker, but not turned on by default.
5. Yes!

K8numerator bash script to iterate over services in Kubernetes cluster
The results of the study can be found here .
We continue to improve the Summ3r of h4ck program, and this year we received from our participants several valuable wishes that we will try to fulfill.
From ourselves we want to say “Thank you!” To those who solved our tasks and worked on research - you are great fellows!
See you at Summ3r of h4ck 2020;)

Here you can see the results of past years:
- research department 2016
- Security Analysis Department 2017
- research department 2017
- Summ3r 0f h4ck: summer internship at Digital Security
We adhered to the previous practice: the participants were offered a list of topics on which they could work during the passage of the program. Someone had their own interesting idea for research, and we were always ready to discuss it.
So, how did the selection go to the department? The first stage is to fill out the questionnaire, which we posted on the company's website . It contained 10 interesting tasks. They helped to evaluate the level of preparation of the person, his knowledge and some practical skills.
In collaboration with Korgik_0, we have already made a detailed analysis of entrance tests ; In addition, a system for evaluating responses and some interesting statistics are presented. Therefore, we will not dwell on them again, but rather move on to the most interesting.
What does the security analysis department do?
Our employees
Introduction
This year, there were a lot of people who wanted to participate, including from other cities. Geographically, Summ3r of h4ck always takes place in the beautiful city of St. Petersburg.
This year’s recruitment included both new and already familiar faces: someone had already undergone a student internship at our university and had now dealt with the qualification questionnaire at a decent level, and someone in previous years had visited us on Summ3r of h4ck looked in. We are always happy to observe the professional growth of young professionals, especially if we ourselves contribute to this :)
An important part of the training is lectures from our employees. The lecture list of the security analysis department this year was something like this:
- AD Security
- Burp and useful plugins
- Linux LPE
- Windows LPE
- Web Security Lectures
- Wi-Fi Security
- Researching (in) Security of Android Applications
The participants themselves also acted as lecturers - closer to the completion of Summ3r of h4ck, they made presentations about the results of their research, shared the problems that arose in the process of work, and told what goals were achieved. Several people teamed up and worked on projects together.
In addition, we have developed a laboratory environment in which you can practice the skills of practical information security. Tasks are not only useful, but also important - at the end of Summ3r of h4ck 2019, the program manager looks at the overall statistics and identifies those people who completed the most tasks. This, as you understand, affects later on the selection of candidates for Digital Security.
All successful speakers were solemnly awarded the Summ3r of h4ck 2019 certificate of completion.

Those who successfully reached the finals, we were asked to take a short survey for us.
The questions for the mini interview were:
- Why did you decide to do an internship at Digital Security? What attracted you to the company?
- Did you like Summ3r of h4ck? What was especially memorable? How did reality coincide with your expectations?
- Tell us about your task / tasks.
- Did the tasks you worked on during the preparation process seem interesting? Was there something you wanted to do but failed?
- Are you ready to return to the company for a new round of Summ3r of h4ck or for work?
The spelling, punctuation and style of the authors are preserved.
Alexander Chernenkov, MITM cheat-sheet topic
1. Often noticed the company on the Internet on its publications and research. I got the impression as a company where there is a real opportunity to engage in practically applicable research activities in information security.
2. I liked the internship. I have long wanted myself in prof. areas that would help me to develop and at the same time bring some benefit to the community. The project, which I was engaged in, just gave such an opportunity. Reality coincided with better expectations.
3. I participated in writing cheats on mitm attacks, took up the network level, which I had long wanted to pump in the security context.
4. The tasks are very interesting, give a lot of freedom, since the first task is to figure it out for yourself in order to convey it to people normally.
5. Ready to return to the internship, possibly to work.
The results of the study can be found here (the project is under active editing and development).
Vladimir Dushkevich, topics MITM cheat-sheet, Fullscreen web phishing
1. I am very interested in working on tasks that can be used in practice. I love practical tasks in the framework of information protection (and not only protection :)). In addition, it is always a pleasure to work with smart people who know and know more than you :)
2. I really liked the internship, now I have a lot more knowledge about javascript in my head - and I got them myself in practice. I usually thought js was something boring, but now I know that it is not.
I especially remembered how I tested the ICMP redirect attack - it turns out that some distributions are still vulnerable to it (although the attack is very ancient)
3. I managed to participate in two tasks - compiling mitm cheatsheet and javascript fullscreen phishing. As part of the first, we made up a small cheat sheet on mitm attacks, checking them and selecting funds for them. And as part of the second, we made a small phishing page similar to the password entry window in windows 7 - it turned out interesting :)
4. It is a pity that only I was very busy at work - there was little time for solving tasks. We managed to finish the projects only partially - we’ll finish them in the fall, it turned out quite interesting.
5. Return to the company for an internship - be sure next year. At work - it would also be interesting, the only obstacle is that I live in Arkhangelsk :)))

Phishing page in the layout process
Danila Leontiev, Amazon Network Digger Theme
1. Digital Security Company allows you to realize the dream of almost any CTF-filer - this gives you the opportunity to do what you love at the professional level. Answering the question “What attracted the company?” - just this opportunity.
2. Due to the extremely high cost of the trip, which consists of moving, living, and in general the cost of living in the city, and only because of this I can not overestimate this program. I would rate it at 3.8-4.3 points. The estimation coefficient consisted of such a formula - new knowledge / money spent = utility.
Just to make you understand. In order for me to come to your program I will have to pay about 55 thousand rubles. That's too much. This money can be used for advanced training or for training prof. English language. This is stupidly more profitable than “summer of hack”. I think the company should pay attention to Sirius as a platform for training students. And take an example from colleagues at Solar Security. I tend to the fact that these programs are completely free for students. Which is a huge plus. You know, I didn’t have the “student-teacher” interaction. It would be a huge plus in karma for the teacher, and not only him, if there was an exchange of experience on the project. Perhaps the curator already had experience with the cloud or he has some developments on this topic (the same review would be a good help).
3. The goal of the project - the essence of my work is to find weaknesses in configuring AWS. And based on the problems found, writing a script to map the cloud infrastructure.
4. Of course, for myself, I chose projects in which I could start from scratch. And answering the question of whether it was interesting to me - of course.
5. I think at “summer of hack 2020” I would come back again to test myself. Check on what level I am now. It’s too early to talk about employment, because I need about 2 years to finish my studies and another year to put together the nth amount for moving to St. Petersburg. But in any case, Digital Security will be a priority place of employment.

Black color - implemented; Red color - not implemented
Timur Abdullin, Golang Social Bot theme
1. I decided to do internship in DSek because it is one of the few companies that provide a cool opportunity to practice practical safety while still a student. I also attracted a large list of publications by company specialists on various resources (most of them were Habr, of course) and their participation in bugbount programs.
2. I really liked the internship, and reality definitely exceeded expectations. The lectures were very interesting and useful, a lot of new information. The labs were fascinating and complex, after them the cars on the HackTheBox will probably seem easy.
3. My task was to add modules to the utility used in pentests to collect useful information from a captured machine. I implemented the collection of information from popular network clients ( PuTTY , MobaXterm , FileZilla ), extracted hosts, user names, keys. Link to the module.
He also wrote a port scanner available to the client on the external network. Such a scanner is needed if a firewall is used on the network that blocks access to certain ports. The client part of the scanner is trying to connect to the specified list of ports. The server side receives incoming tcp packets, establishes a connection and writes down the port number to which the packets arrived. On this side, we work with raw tcp sockets, as it is faster and more interesting in writing :)
4. Work on the tasks was very interesting. For example, write on a previously unknown Golang, deal with the device fields of tcp packets, and study asynchronous run. It would be nice to learn how to decrypt the data of MobaXterm, FileZilla programs, but the reverse of such voluminous projects is difficult for a beginner pentester). Also, there was not enough time to completely deal with asynchronism, but I think I will do it in the near future.
5. Yes, definitely! Many thanks to the organizers for an interesting summer)

Vladislav Trofimov, Golang Social Bot theme
1. The friends gave me the idea to send the questionnaire, saying that the company is one of the leading companies in the information security market, in addition, the projects will be very interesting, and this is a great opportunity to raise the skill.
2. I liked it, and reality exceeded my expectations. A great atmosphere in the office, friendly relations with employees and other interns, an exciting work process - that’s what remains in memory.
3. I worked on the topic “Golang Social Bot” - a bot used in penetration testing. The main goal was to write modules that collect useful data, somehow interact with computer resources.
4. There were a large number of tasks, some easier, some more difficult, but no less interesting. It seems to me that a lot of work has been done, although, summing up, I understand that I could have done even more.
5. Of course! The internship provides an excellent opportunity to delve into not only the topic of your project, but also to develop skills, gain knowledge on other topics, for which many thanks to the company!
Danil Beltyukov, cheat-sheet Kubernetes theme
1. After playing CTF for a year, I decided to try myself on real projects. I saw an internship from Digital Security, became interested. By that time, many people whom I knew already worked there, which gave confidence in my decision.
2. Yes! There were many interesting lectures, as well as a “lab” in which there were many wheelbarrows. It was possible to apply the knowledge gained at lectures for breaking machines from the lab.
3. My topic was the creation of a security sheet for the Kubernetes cluster.
The main misconfiguration, what to enable, so that it is "secured" and so on.
4. Of course. Having studied previous studies, I realized that they were partially outdated or were carried out on older versions of kubernetes, where most secure features are not enabled by default. In the new versions, it was difficult to find something that is a “out of the box” hole. I looked at the study from the other side and began to rely on a typical scenario with vulnerable applications. After all, we must protect data first, not the cluster. As a result, I found options that could complicate the life of the attacker, but not turned on by default.
5. Yes!

K8numerator bash script to iterate over services in Kubernetes cluster
The results of the study can be found here .
Conclusion
We continue to improve the Summ3r of h4ck program, and this year we received from our participants several valuable wishes that we will try to fulfill.
From ourselves we want to say “Thank you!” To those who solved our tasks and worked on research - you are great fellows!
See you at Summ3r of h4ck 2020;)
All Articles