Training Cisco 200-125 CCNA v3.0. Day 28. In-depth study of ACL
Today we will continue the topic of the video tutorial on the 27th day and do an in-depth study of ACLs: we’ll talk a bit about the Wildcard Mask reverse mask, the extended ACL list, setting up the extended ACL list and the commands that help diagnose network design problems.
In the previous lesson, we got acquainted with the new inverse mask concept for us, and now I will talk about Wildcard Mask in more detail. If you remember, the subnet mask helps us visually divide the network into the address part of the network and the address part of the host.
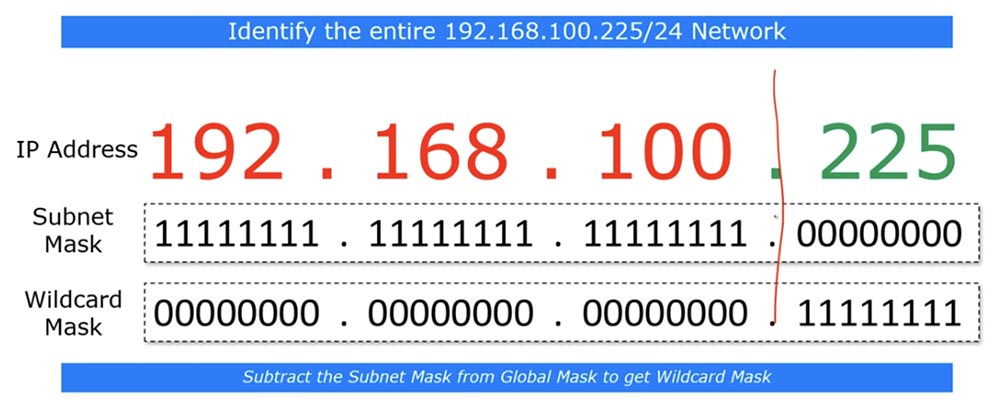
If you go to the bit level, you can see that the subnet mask consists of a series of units denoting the network part, and a series of zeros that indicate part of the host. The reverse mask is very similar to the subnet mask, only in the “inverted” form - where there are units in the subnet mask, zeros are in the reverse mask, and vice versa. This is not a mandatory rule - in some cases, the reverse mask is formed according to a different principle, but when studying CCNA, this rule always applies.
The best way to calculate the inverse mask is to subtract the subnet mask octets from the global mask, which always looks like 255.255.255.255.
So, to calculate the inverse mask for the subnet mask 255.255.255.0, we simply subtract it from the global mask and get 0.0.0.255.

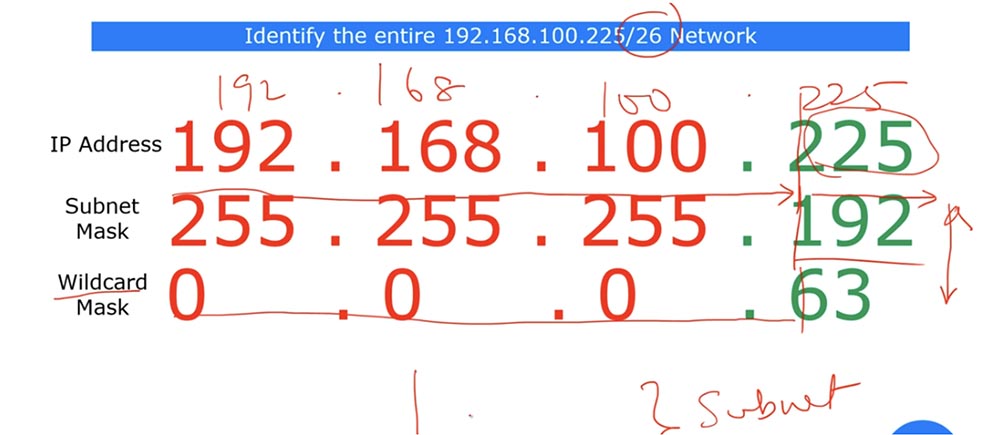
In this example, we looked at the network 192.168.100.255/24, and now let's look at the network / 26. If you have / 26, then the last octet of the subnet mask will be 192.
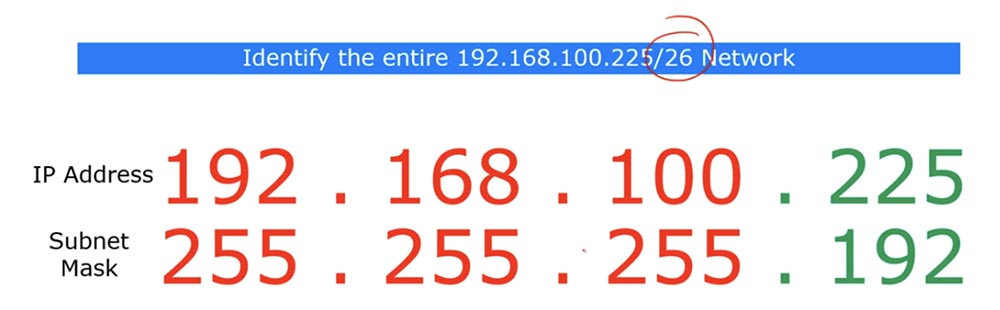
If you look at the bit form of these IP addresses, you will see that the subnet mask contains 26 single and 6 zero bits.
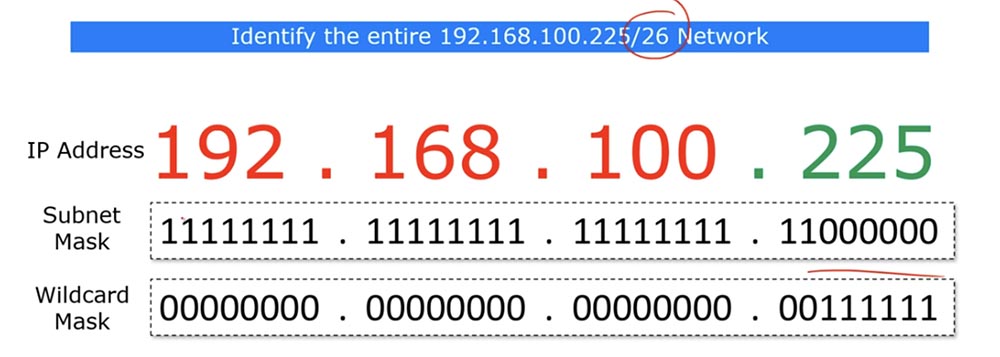
In this case, the reverse mask should consist of 26 zeros and 6 units. As we already said, those places where 0 are located show the matching address parameters, and you can ignore places where units are located.
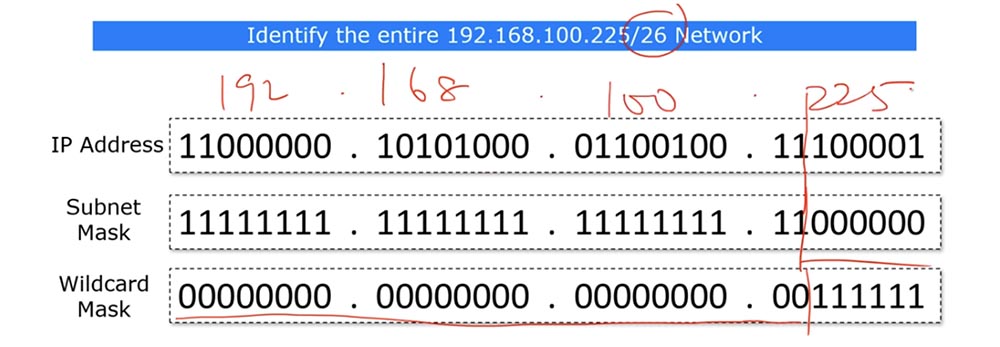
To make it clearer, I will write the IP address in decimal form on top. The last octet of the inverse mask corresponds to the number 63, and I can display it as 0.0.0.63. simply put, / 26 means that the 26 zeros, or the first 3 octets of the IP address are the same, and the last 6 bits can be anything - zeros or ones.
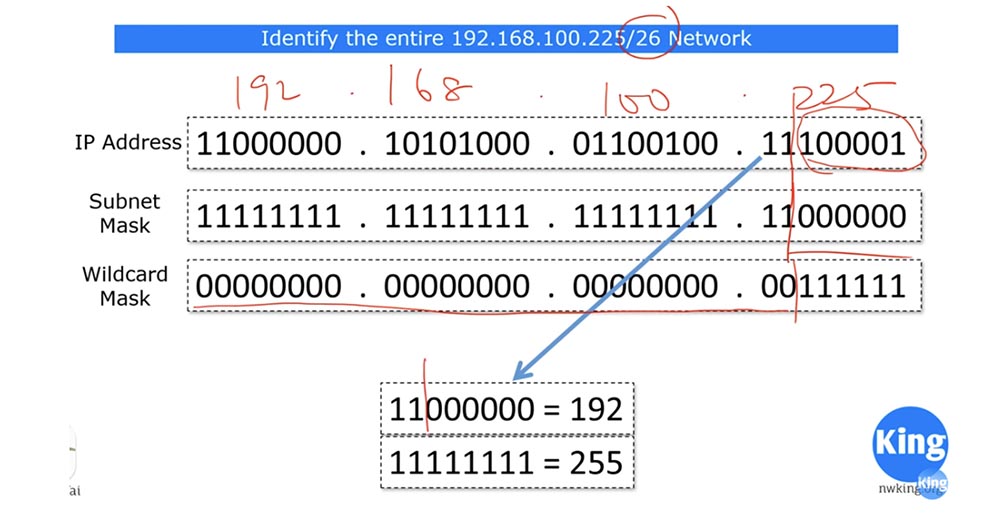
Look - if we replace these last 6 bits of the IP address with zeros, we get the number 192, and if the ones we get the number 255. Thus, the reverse mask shows that the subnet with IP addresses whose last octet is in the range from 192 to 255 , that is, part of the network 192.168.100.225/26, is subject to the specified ACL condition.
You may ask why two masks are needed: a subnet mask and a Wildcard mask. I myself asked this question when I was a student, and still many people, even working at Cisco, ask this question. I will try to answer it. In general, the subnet mask and reverse mask show the same thing when it comes to the subnet, that is, the part of the IP address denoting the network. When we identify the whole network, the inverse mask is simply an “inverted” version of the direct mask.
However, host identification is different. If you want to identify the whole subnet with all addresses included in it, you can use the subnet mask. But if you only need to identify a few hosts from this network in order to selectively apply ACL rules to them, you need a reverse mask.
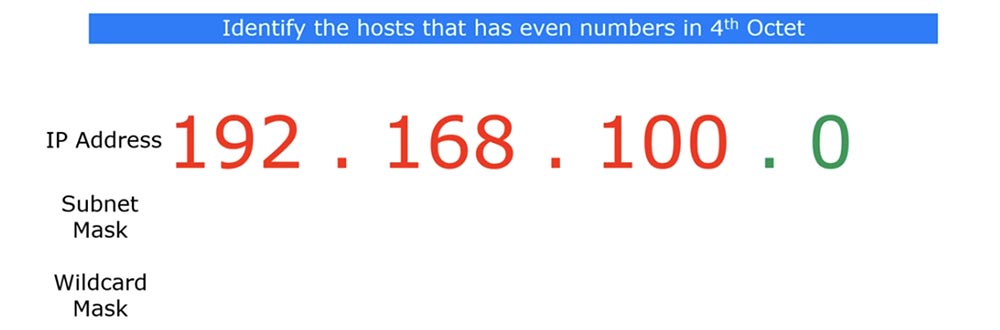
You will never encounter a subnet mask that would consist of alternating ones and zeros - it always has units first and zeros at the end. Wildcard is therefore called “wild” because it can consist of any sequence of ones and zeros. To make it clearer, let's solve the problem: "identify hosts on a given network that have even numbers in the fourth octet."
This is necessary to create an ACL rule of this type: permit 192.168.100.0 <reverse mask>, that is, traffic will be allowed for the IP addresses of this subnet with only even fourth octets. Can this be done using a subnet mask? I don’t think, because the fourth octet of a regular subnet mask can contain only one specific number. Let's look at a 4 octet inverse mask.
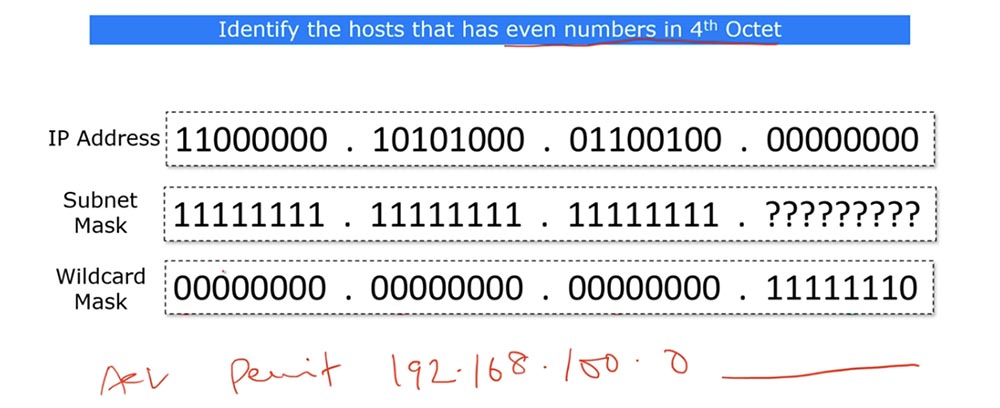
In the last octet of the inverse mask, you can place the following bits: 11111110. I will explain what it is. If the 4th octet contains even numbers, then the last bit of the octet is necessarily 0, and if the last bit is 1, then the number is odd. If we are talking about the / 24 subnet, then only the last octet in it can contain an even number.
In the case of the reverse mask, the first three octets are 0, and the first seven bits of the fourth octet do not bother us, the main thing is that the eighth bit of the octet is zero, because it must coincide with the last octet of the network IP address, which is 0.
If the last bit of the IP address is 1, this address will be denied, now I will add the condition to our ACL - Deny any. Thus, only if the last octet of any IP address of our subnet ends in 0, that is, it is even, we will meet the condition for matching the backward mask, which also ends with 0, and the ACL condition “allow all addresses with an even 4th octet” will be satisfied. Otherwise, that is, for all odd IP addresses, the deny any condition will apply.
Thus, we don’t care what exact value an even octet will have - 2,4,6, 8 and so on, the main thing is that it will have a zero bit at the end. If we used a regular subnet mask, we would have to create a separate entry for each IP address that has an even 4th octet. Using the inverse mask allows you to replace all these entries with one.
Exactly the same principle applies to odd numbers of the 4th octet, just the last bit of the reverse mask in this case should be equal to 1. In this case, a general rule will be established, permit or deny, for all IP addresses of the subnet having an odd 4- th octet. See what this decimal example looks like.
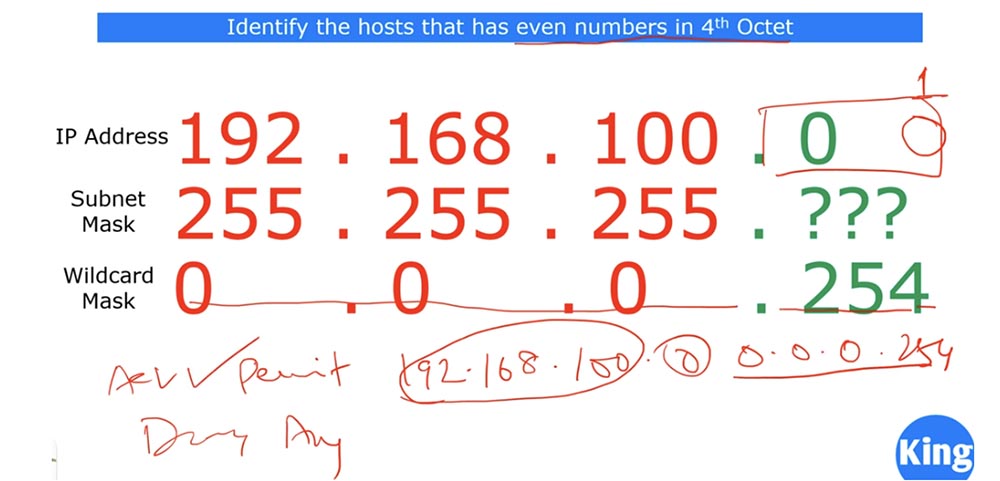
If I use the reverse mask 0.0.0.254, our problem will be solved: all hosts with an even fourth octet are allowed, and all other hosts are prohibited. The advantage of a reverse mask is that when you create an ACL, you can configure it to fit your needs. You don’t have to worry much about specific reverse masks, because CCNA does not require this. It’s enough to just remember the rule: the reverse mask is obtained when the subnet mask is removed from the global mask 255.255.255.255. Note that the CCNA course focuses more on subnets rather than hosts.
Let's go back to the previous slide, and I'll talk about another way to calculate the Wildcard mask.
If you remember from our “magic” table, / 26 means the size of the block of bits equal to 64. If this block is 64, the last octet of the inverse mask will have the value (64-1) = 63. If we have / 25, the block size will be 128, which means that the last octet of the inverse mask will be (128-1) = 127. This is another hint to facilitate the calculation of the inverse mask value. But if you do not want to use it, use the usual method, subtracting the subnet mask from the global mask.
Now let's move on to the syntax of the extended ACL commands. As with the standard ACL, there are two types of command recording: classic and modern.
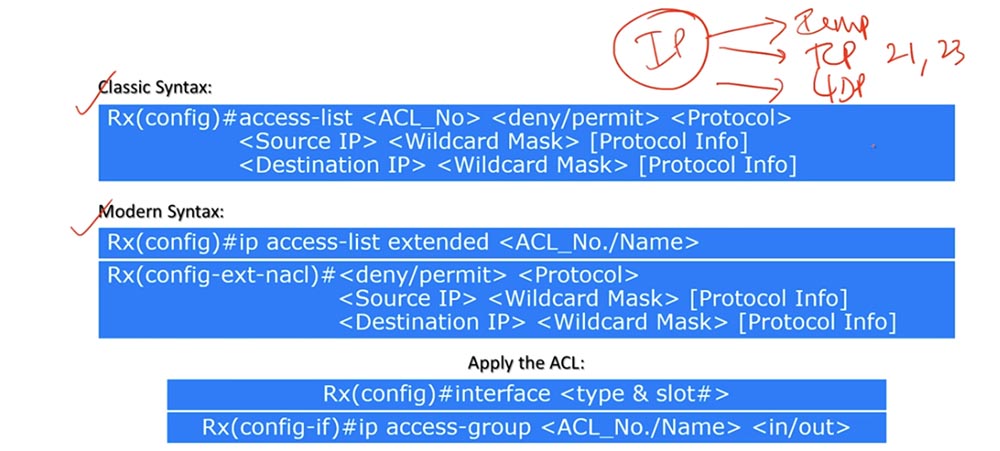
The classic command is the entry access-list <ACL number> <disable / allow> <protocol>. Thus, the first extended ACL command differs from the standard ACL command by specifying a protocol, not a criterion. This means that traffic filtering is performed here not according to the source or destination IP address, but according to the protocol used.
In all cases, we use the IP protocol, which is of three types: ICMP, or the ping known to us, TCP, which depends on the specific port 21,23 and so on, and UDP. Let me remind you that Wikipedia has an article with a list of all protocols and their corresponding port numbers.
The following is the command line <source IP> <reverse mask> [protocol information]. Protocol information means specifying a port number. That is, in the previous command as <protocol> you specify ICMP, TCP or UDP, and in the second command as the parameter [protocol information] specify the port number 21.23, etc.
The third line of the command is <destination IP> <reverse mask> [protocol information], that is, the parameters regarding the destination.
If you remember from previous lessons, the source port number is a random number, because the device sending the traffic creates a random number port for this. In this regard, in the first line regarding the traffic source, you indicate the [protocol information] destination, for example, FTP, that is, the protocol of the device whose traffic you want to block.
Let me remind you that in order to make changes to the list of extended ACLs of the classical type, you will have to re-form the entire list manually, as in the case of the standard ACLs of the classical type.
A modern-looking team begins with the expression ip, which has nothing to do with the IP protocol, it's just a keyword. So, the first line contains the ip keyword, the “extended access-list” parameter, and the number or name of the ACL. After executing the first command, you go to solve the config-ext-nacl subcommands and enter <disable / allow> <protocol>, as we discussed above.
The following are two commands <source IP> <reverse mask> [protocol information] and <destination IP> <reverse mask> [protocol information], the first usually ignoring the [source protocol information] parameter, and instead the [protocol information] parameter destination]. Sometimes it may be necessary to specify the source port, but in CCNA in most cases you can ignore this parameter.
Using an extended ACL is similar to using a standard ACL. Here you also need to specify the interface of the device to which the list is applied, then use the ip access-group parameter, the ACL list number or name, and the traffic flow direction - inbound or outbound. In the previous video, we already discussed how traffic direction is determined for a specific port.
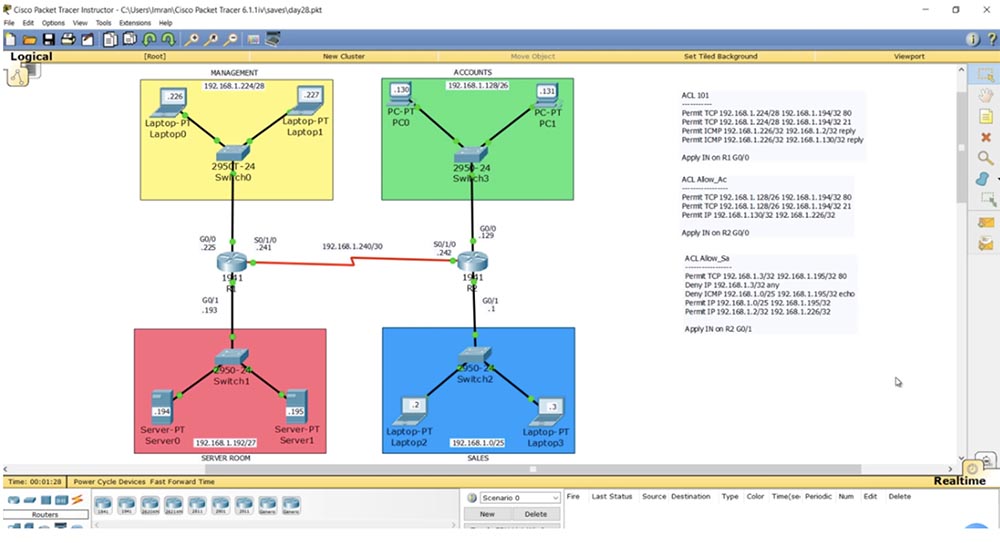
Let's move on to the scheme and configure the advanced ACL using the network topology from the previous lesson. Problem number 1 is: "The computers in the network of the management department and the network of the financial department can access via the HTTP (80) and FTP (21) protocols only to the Server0 server located on the server network."
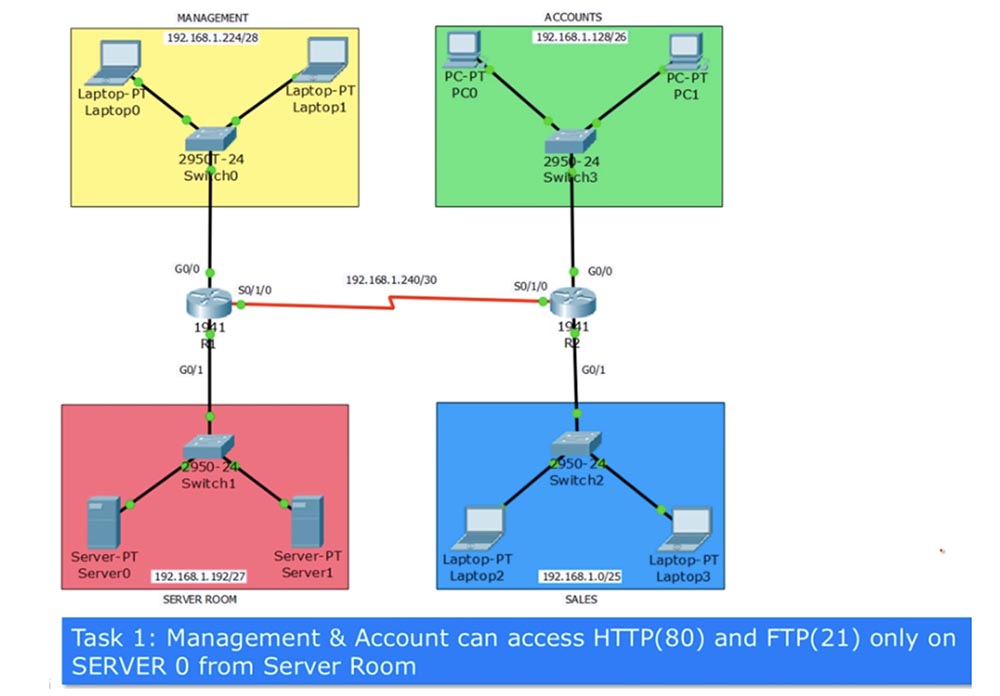
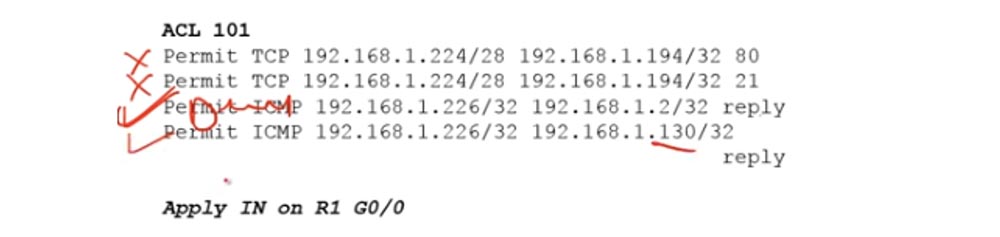
At the same time, not all traffic is allowed, but only that which comes from ports 80 and 21, that is, for example, traffic via the SSH protocol should be blocked. If you remember, the extended ACL should be applied closer to the source, so for the management department it should be applied to port G0 / 0 of router R1, and for accounting, to port G0 / 0 of router R2. In relation to the router, we block incoming traffic, so we use the IN parameter in the list commands. Assign the ACL to the list number 101 and make a list of lines that it should contain using the classical approach.
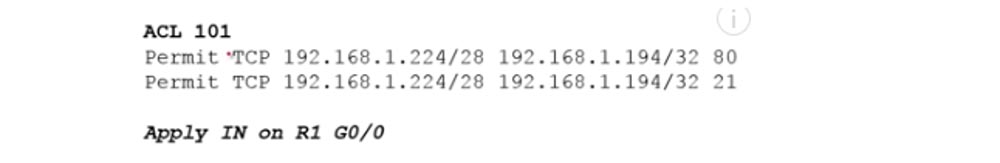
The first line allows TCP, because HTTP port 80 means TCP, then we indicate the network of the management department, 192.168.1.224/28. In this example, I omit the reverse mask, we use it in Packet Tracer, so far the principle of list formation is important to us. The management network is the source of traffic, after it the destination IP address 192.168.1.194/32 is indicated, where 194 is the last octet of the Server0 address, and / 32 means that the condition applies only to this particular device located on the 192.168.1.192/27 subnet. At the end of the line, we indicate the allowed destination port 80, intended for HTTP traffic.
In the same way, an entry is created for port 21 used to transmit FTP traffic. I am not writing a third line, which by default looks like Deny any and prohibits any outgoing traffic from devices that do not belong to this subnet. Next, you must specify that the list is applied to the G0 / 0 port of R1 in the IN direction, that is, for incoming traffic.
We do the same in compiling ACL Allow_Acc entries for the finance department, allowing TCP traffic from ports 80 and 21 and applying this list to the input interface G0 / 0 of router R2.

Problem number 2 is: "Computers in the sales department network can use all protocols except PING (ICMP) only on Server1, located on the server network." This means that for communication with the server, the computers of the sales department can use the HTTP, SSH, FTP protocols - any protocols other than ICMP. In this case, the ACL condition list will look like this.
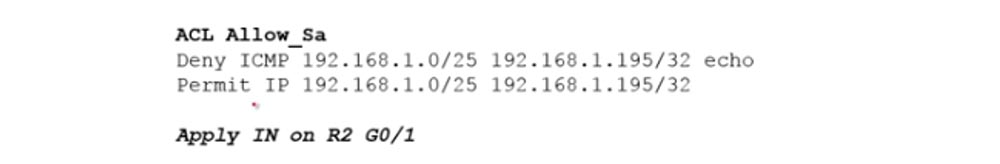
In the first line, we prohibit all traffic via ICMP, placing a specific condition at the top of the list, and general at the end of the list. This record shows the sales department subnet identifier 192.168.1.0/25, the IP address of a specific Server 1 server is 192.168.1.195/32. The echo parameter means ping traffic, that is, a packet that is sent to the server in order to return back to the computer should be denied.
The second line allows all other traffic coming from the 192.168.1.0/25 subnet to the server address 192.168.1.195/32. As usual, at the end of the list, the default line is Deny any, which means that if the computers in the sales department try to contact the financial department, this traffic will be discarded. Next, we indicate to which router interface the ACL should be applied, and the second problem is solved.
Task 3 is: “Sales2 laptop Laptop2 and finance department PC0 can access management0 laptop Laptop0.” Suppose that these devices are managed by the heads of the sales and accounting departments, who can communicate with the CFO of the CFO located in the management department. There are no restrictions regarding the protocols used, including ICMP.
We already have three ACLs applied to the interfaces that I circled in red on the diagram. Laptop2 cannot contact Laptop0 at the moment, because this contradicts the conditions of Task 3.
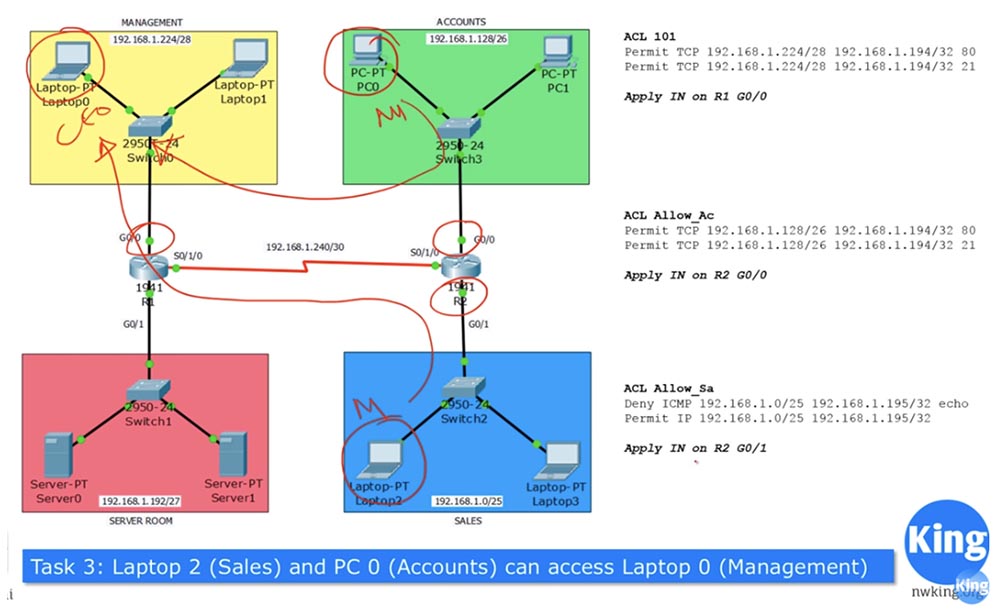
To communicate between these two devices, you must add additional conditions to the Allow_Sa ACL.

Similarly, you need to add conditions to the Allow_Acc ACL so that PC0 can freely contact Laptop0.

In both lists, we add lines with the Permit IP parameter, which means allowing traffic over any IP protocol.
As you know, ICMP uses two-way traffic: you send ping, and echo returns it. In our situation, if Laptop2 addresses the address of Laptop0 ping, traffic will flow freely into the network of the management department. However, when the package is returned back to the laptop of the sales department, it will go to the G0 / 0 interface of the R1 router, where the ACL 101 is active. Since the return traffic does not match any of the conditions in this list, it will be blocked. Therefore, we need to supplement the ACL101 list with resolving conditions for both pinging from the Sales2 laptop2 of the sales department and pinging from the finance department's PC0 computer.
We have solved Task No. 3 and now move on to solving Problem No. 4: “The Sales3 laptop Laptop3 can only access its own SALES network and only the Web Service through port 80 on Server 1”.
The first part of the task means that as soon as Laptop3 tries to leave the SALES network, its traffic will be blocked by the R2 router. However, according to the second part of the task, this computer must have access to a Web Service located outside the SALES network. This means that all traffic except traffic directed to the server is blocked.
From the previous tasks, we know that the traffic coming from the sales department is regulated by the Allow_Sa ACL, which we applied to the input interface G0 / 1 of the R2 router. Therefore, we need to change this list, first of all adding the line “allow TCP to server 1 through port 80” in this line: Permit TCP 192.168.1.3/32 192.168.1.195/32 80
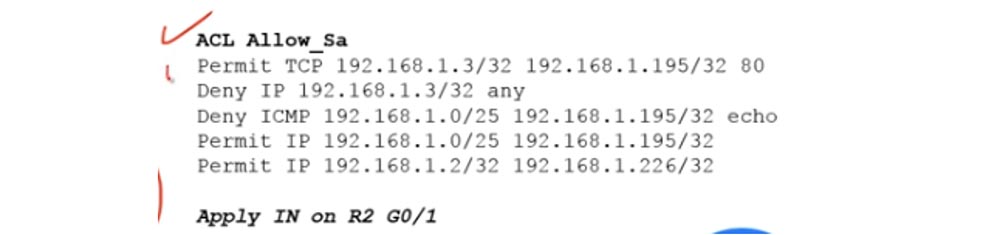
The first line means that any HTTP traffic reaches the server, and the second Deny IP 192.168.1.3/32 any means that the rest of the traffic, for example, FTP coming from Laptop3, will be dropped. Next, we leave unchanged the three following lines of the previous ACL, thus solving Problem 4.
I already said that I advise you to write down the solutions to these problems on paper or type them manually on a computer, because they change, and on paper or on a computer you can always add, cross out or delete lines. I draw your attention to the fact that if you simply add the solution to the fourth problem at the end of the ACL, adding two lines, the system will ignore them, because the conditions located above absorb these rules. Since the second line of the old list allows all traffic, the Deny IP condition 192.168.1.3/32, located at the end of the list, simply will not be satisfied.
Thus, the correct sequence of ACL entries is of great importance. First you should develop a logical chain of operations and arrange the lines so that they do not contradict each other. Now let's move on to Packet Tracer and complete all the settings according to the solutions.
Let's start the configuration from the first router, Router1. I use the show access-list command to show that the ACL is currently missing. Next, using the show ip route command, I show that the RIP between the two routers is already configured and working.
Let's go to Laptop0 and ping Server1 at 192.168.1.195. As you can see, pinging is successful, since we do not have any ACLs that prohibit or filter traffic. I am also free to ping Server0.
Now we’ll go to the router Router1, enter the global settings mode and create the ACL 101 list. To do this, I type the command access-list 101 permit tcp. Please note - the system gives a hint which parameter value, except tcp, can be used in this command.
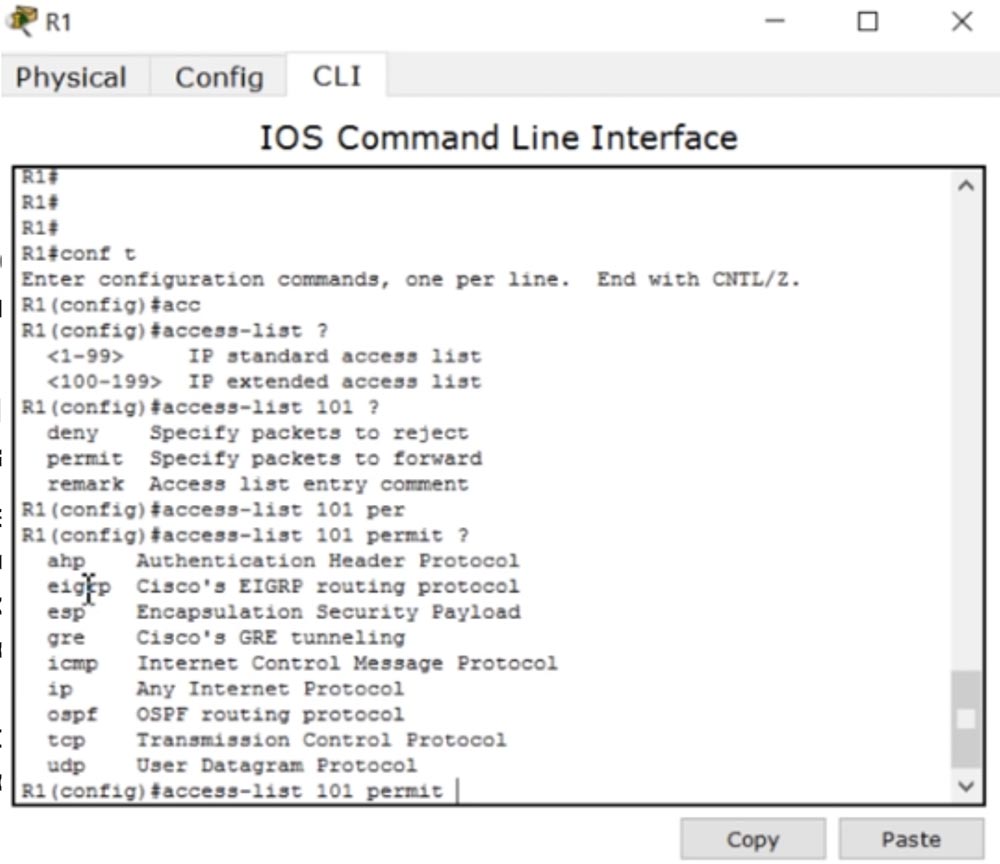
It can be esp, icmp, osfp and so on. CCNA ip, ismp, tcp udp.
, access-list 101 permit tcp 192.168.1.224. /28 16 , 0.0.0.15.
28 4 , 1 , 128, 2 – 64, – 32, 4 16, , (16-1) =15. , . , host IP-, : access-list 101 permit tcp 192.168.1.224 0.0.0.15 host 192.168.1.194.
, , , .
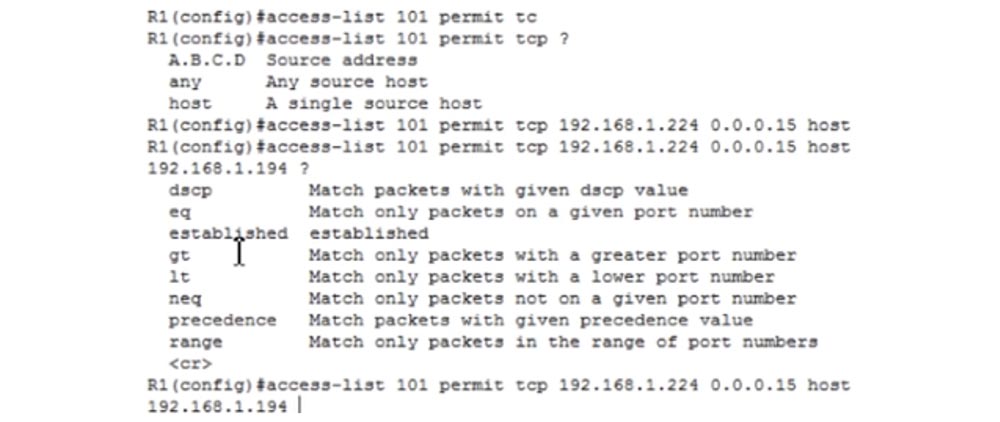
dscp, , eq, , gt – , , lt – .. , eq. .
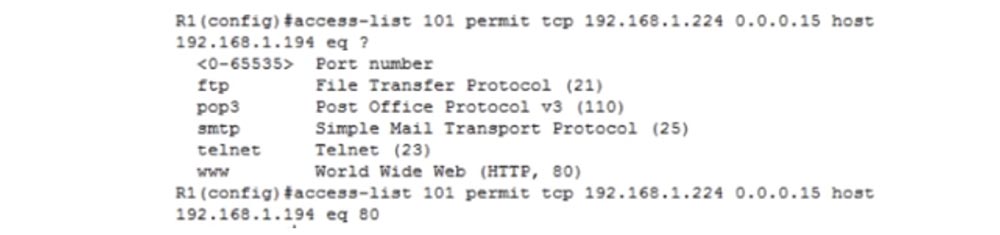
0 65535, , . FTP 21, SMTP – 25, www – HTTP- 80. 80.
do show run , , 80 www. , , 80 21: access-list 101 permit tcp 192.168.1.224 0.0.0.15 host 192.168.1.194 eq 21.
ICMP-, . access-list 101 permit icmp. host, , IP- 192.168.1.226 0.0.0.0, , . host IP- Laptop2 – 192.168.1.2. – , .
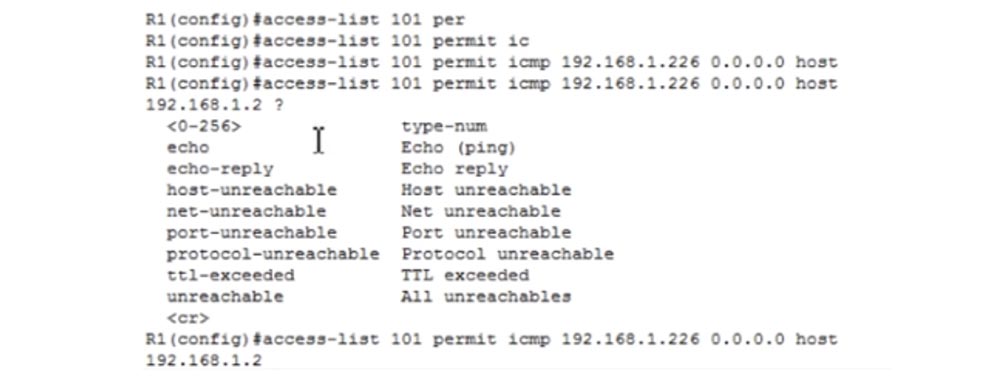
, echo-replay. , . : access-list 101 permit icmp192.168.1.226 0.0.0.0 host 192.168.1.2 echo-replay. : access-list 101 permit icmp 192.168.1.226 0.0.0.0 host 192.168.1.130 echo-replay.
, int g0/0 ip access-group, 101 , IN. Laptop0 192.168.1.194, ACL . , , . IP- 192.168.1.195, .
, Server0 Laptop0 . HTTP FTP- 80 21, ICMP-, . .
-, 192.168.1.194, - Server0.
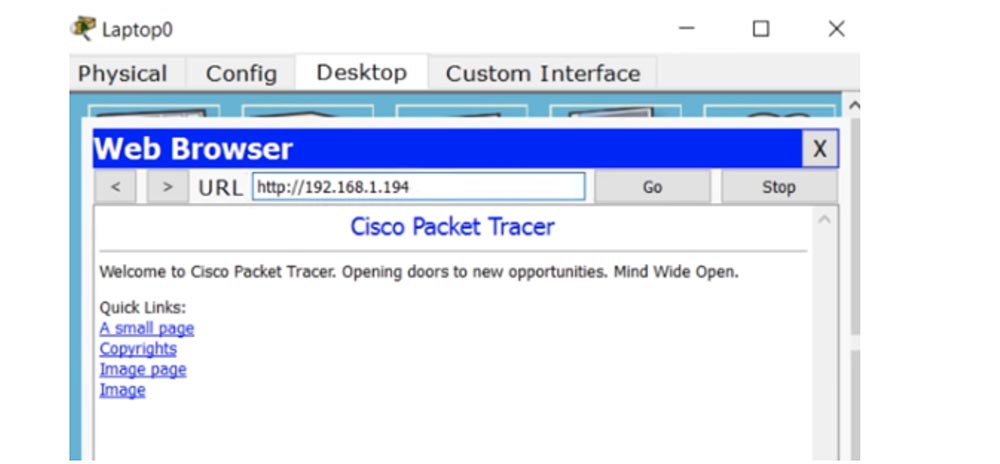
192.168.1.195, , ACL .
№1 R2 ACL – Allow_Ac. , ACL , . ip access-list extended Allow_Ac .
permit tcp 192.168.1.128. /26, , , – 128, – 64, , 0.0.0.63. , 255.255.255.192 255.255.255.255. permit tcp 192.168.1.128 0.0.0.63 host 192.168.1.194 eq 80. : permit tcp 192.168.1.128 0.0.0.63 host 192.168.1.194 eq 21.
№1 – PC0 Laptop0 . permit ip host 192.168.1.130 host 192.168.1.226 , .
ACL g0/0, ip access-group Allow_Ac IN. , PC0 Server 0, - . PC0 192.168.1.194, Packet Tracer, , R2 .
ACL , ip access-list extended Allow_Sa permit tcp host 192.168.1.3 host 192.168.1.195 eq 80. , HTTP- , , deny ip host 192.168.1.3 any.
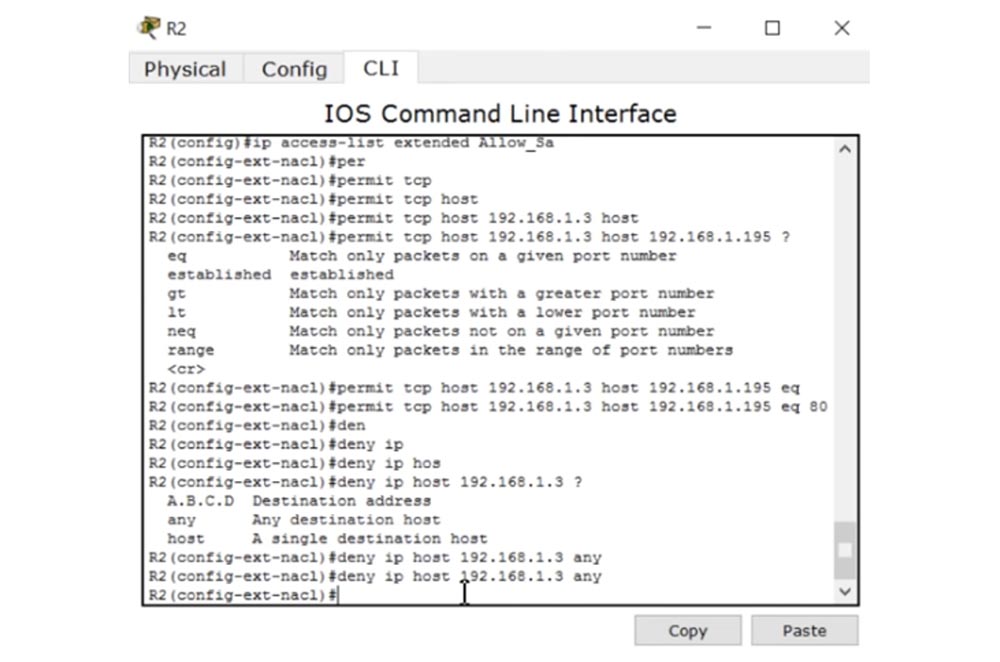
, , . deny icmp 192.168.1.0. /25, 1 , 128 , , 0.0.0.127. 192.168.1.195, Server2. ACL : deny icmp 192.168.1.0 0.0.0.127 host 192.168.1.195 echo.
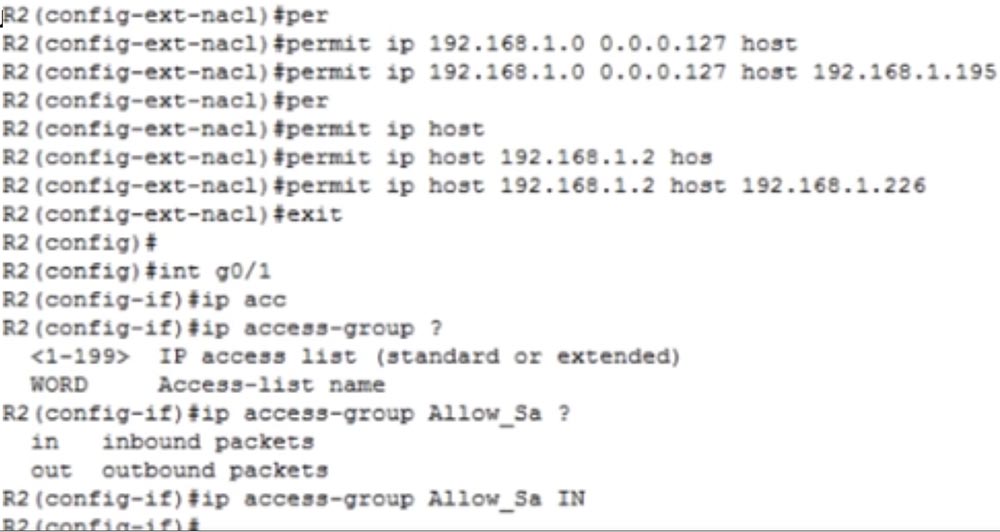
4- , , : permit ip 192.168.1.0 0.0.0.127 host 192.168.1.195.
, Laptop2 Laptop0. permit host 192.168.1.2 host 192.168.1.226, g0/1 ip access-group Allow_Sa IN.
, ACL Laptop3, , - . 192.168.1.195 , PC 192.168.1.130 192.168.1.226. , – - Server1.

Laptop2 Laptop0, . , , 192.168.1.226. Laptop1 , ACL , Laptop0. Laptop2 Server1 192.168.1.195, - . , 4- , ACL.
, , . ACL – , . , , , .
The advantage of CCNA is to learn all the concepts of network development, and the best way to learn the material is to design your own network. I will be glad if you solve these problems in your own way and describe it in the comments to this video. In addition, based on the considered network topology, you can come up with other tasks and try to solve them yourself.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that was invented by us for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
In the previous lesson, we got acquainted with the new inverse mask concept for us, and now I will talk about Wildcard Mask in more detail. If you remember, the subnet mask helps us visually divide the network into the address part of the network and the address part of the host.

If you go to the bit level, you can see that the subnet mask consists of a series of units denoting the network part, and a series of zeros that indicate part of the host. The reverse mask is very similar to the subnet mask, only in the “inverted” form - where there are units in the subnet mask, zeros are in the reverse mask, and vice versa. This is not a mandatory rule - in some cases, the reverse mask is formed according to a different principle, but when studying CCNA, this rule always applies.
The best way to calculate the inverse mask is to subtract the subnet mask octets from the global mask, which always looks like 255.255.255.255.
So, to calculate the inverse mask for the subnet mask 255.255.255.0, we simply subtract it from the global mask and get 0.0.0.255.

In this example, we looked at the network 192.168.100.255/24, and now let's look at the network / 26. If you have / 26, then the last octet of the subnet mask will be 192.

If you look at the bit form of these IP addresses, you will see that the subnet mask contains 26 single and 6 zero bits.

In this case, the reverse mask should consist of 26 zeros and 6 units. As we already said, those places where 0 are located show the matching address parameters, and you can ignore places where units are located.

To make it clearer, I will write the IP address in decimal form on top. The last octet of the inverse mask corresponds to the number 63, and I can display it as 0.0.0.63. simply put, / 26 means that the 26 zeros, or the first 3 octets of the IP address are the same, and the last 6 bits can be anything - zeros or ones.

Look - if we replace these last 6 bits of the IP address with zeros, we get the number 192, and if the ones we get the number 255. Thus, the reverse mask shows that the subnet with IP addresses whose last octet is in the range from 192 to 255 , that is, part of the network 192.168.100.225/26, is subject to the specified ACL condition.
You may ask why two masks are needed: a subnet mask and a Wildcard mask. I myself asked this question when I was a student, and still many people, even working at Cisco, ask this question. I will try to answer it. In general, the subnet mask and reverse mask show the same thing when it comes to the subnet, that is, the part of the IP address denoting the network. When we identify the whole network, the inverse mask is simply an “inverted” version of the direct mask.
However, host identification is different. If you want to identify the whole subnet with all addresses included in it, you can use the subnet mask. But if you only need to identify a few hosts from this network in order to selectively apply ACL rules to them, you need a reverse mask.
You will never encounter a subnet mask that would consist of alternating ones and zeros - it always has units first and zeros at the end. Wildcard is therefore called “wild” because it can consist of any sequence of ones and zeros. To make it clearer, let's solve the problem: "identify hosts on a given network that have even numbers in the fourth octet."

This is necessary to create an ACL rule of this type: permit 192.168.100.0 <reverse mask>, that is, traffic will be allowed for the IP addresses of this subnet with only even fourth octets. Can this be done using a subnet mask? I don’t think, because the fourth octet of a regular subnet mask can contain only one specific number. Let's look at a 4 octet inverse mask.

In the last octet of the inverse mask, you can place the following bits: 11111110. I will explain what it is. If the 4th octet contains even numbers, then the last bit of the octet is necessarily 0, and if the last bit is 1, then the number is odd. If we are talking about the / 24 subnet, then only the last octet in it can contain an even number.
In the case of the reverse mask, the first three octets are 0, and the first seven bits of the fourth octet do not bother us, the main thing is that the eighth bit of the octet is zero, because it must coincide with the last octet of the network IP address, which is 0.
If the last bit of the IP address is 1, this address will be denied, now I will add the condition to our ACL - Deny any. Thus, only if the last octet of any IP address of our subnet ends in 0, that is, it is even, we will meet the condition for matching the backward mask, which also ends with 0, and the ACL condition “allow all addresses with an even 4th octet” will be satisfied. Otherwise, that is, for all odd IP addresses, the deny any condition will apply.
Thus, we don’t care what exact value an even octet will have - 2,4,6, 8 and so on, the main thing is that it will have a zero bit at the end. If we used a regular subnet mask, we would have to create a separate entry for each IP address that has an even 4th octet. Using the inverse mask allows you to replace all these entries with one.
Exactly the same principle applies to odd numbers of the 4th octet, just the last bit of the reverse mask in this case should be equal to 1. In this case, a general rule will be established, permit or deny, for all IP addresses of the subnet having an odd 4- th octet. See what this decimal example looks like.

If I use the reverse mask 0.0.0.254, our problem will be solved: all hosts with an even fourth octet are allowed, and all other hosts are prohibited. The advantage of a reverse mask is that when you create an ACL, you can configure it to fit your needs. You don’t have to worry much about specific reverse masks, because CCNA does not require this. It’s enough to just remember the rule: the reverse mask is obtained when the subnet mask is removed from the global mask 255.255.255.255. Note that the CCNA course focuses more on subnets rather than hosts.
Let's go back to the previous slide, and I'll talk about another way to calculate the Wildcard mask.

If you remember from our “magic” table, / 26 means the size of the block of bits equal to 64. If this block is 64, the last octet of the inverse mask will have the value (64-1) = 63. If we have / 25, the block size will be 128, which means that the last octet of the inverse mask will be (128-1) = 127. This is another hint to facilitate the calculation of the inverse mask value. But if you do not want to use it, use the usual method, subtracting the subnet mask from the global mask.
Now let's move on to the syntax of the extended ACL commands. As with the standard ACL, there are two types of command recording: classic and modern.

The classic command is the entry access-list <ACL number> <disable / allow> <protocol>. Thus, the first extended ACL command differs from the standard ACL command by specifying a protocol, not a criterion. This means that traffic filtering is performed here not according to the source or destination IP address, but according to the protocol used.
In all cases, we use the IP protocol, which is of three types: ICMP, or the ping known to us, TCP, which depends on the specific port 21,23 and so on, and UDP. Let me remind you that Wikipedia has an article with a list of all protocols and their corresponding port numbers.
The following is the command line <source IP> <reverse mask> [protocol information]. Protocol information means specifying a port number. That is, in the previous command as <protocol> you specify ICMP, TCP or UDP, and in the second command as the parameter [protocol information] specify the port number 21.23, etc.
The third line of the command is <destination IP> <reverse mask> [protocol information], that is, the parameters regarding the destination.
If you remember from previous lessons, the source port number is a random number, because the device sending the traffic creates a random number port for this. In this regard, in the first line regarding the traffic source, you indicate the [protocol information] destination, for example, FTP, that is, the protocol of the device whose traffic you want to block.
Let me remind you that in order to make changes to the list of extended ACLs of the classical type, you will have to re-form the entire list manually, as in the case of the standard ACLs of the classical type.
A modern-looking team begins with the expression ip, which has nothing to do with the IP protocol, it's just a keyword. So, the first line contains the ip keyword, the “extended access-list” parameter, and the number or name of the ACL. After executing the first command, you go to solve the config-ext-nacl subcommands and enter <disable / allow> <protocol>, as we discussed above.
The following are two commands <source IP> <reverse mask> [protocol information] and <destination IP> <reverse mask> [protocol information], the first usually ignoring the [source protocol information] parameter, and instead the [protocol information] parameter destination]. Sometimes it may be necessary to specify the source port, but in CCNA in most cases you can ignore this parameter.
Using an extended ACL is similar to using a standard ACL. Here you also need to specify the interface of the device to which the list is applied, then use the ip access-group parameter, the ACL list number or name, and the traffic flow direction - inbound or outbound. In the previous video, we already discussed how traffic direction is determined for a specific port.
Let's move on to the scheme and configure the advanced ACL using the network topology from the previous lesson. Problem number 1 is: "The computers in the network of the management department and the network of the financial department can access via the HTTP (80) and FTP (21) protocols only to the Server0 server located on the server network."

At the same time, not all traffic is allowed, but only that which comes from ports 80 and 21, that is, for example, traffic via the SSH protocol should be blocked. If you remember, the extended ACL should be applied closer to the source, so for the management department it should be applied to port G0 / 0 of router R1, and for accounting, to port G0 / 0 of router R2. In relation to the router, we block incoming traffic, so we use the IN parameter in the list commands. Assign the ACL to the list number 101 and make a list of lines that it should contain using the classical approach.

The first line allows TCP, because HTTP port 80 means TCP, then we indicate the network of the management department, 192.168.1.224/28. In this example, I omit the reverse mask, we use it in Packet Tracer, so far the principle of list formation is important to us. The management network is the source of traffic, after it the destination IP address 192.168.1.194/32 is indicated, where 194 is the last octet of the Server0 address, and / 32 means that the condition applies only to this particular device located on the 192.168.1.192/27 subnet. At the end of the line, we indicate the allowed destination port 80, intended for HTTP traffic.
In the same way, an entry is created for port 21 used to transmit FTP traffic. I am not writing a third line, which by default looks like Deny any and prohibits any outgoing traffic from devices that do not belong to this subnet. Next, you must specify that the list is applied to the G0 / 0 port of R1 in the IN direction, that is, for incoming traffic.
We do the same in compiling ACL Allow_Acc entries for the finance department, allowing TCP traffic from ports 80 and 21 and applying this list to the input interface G0 / 0 of router R2.

Problem number 2 is: "Computers in the sales department network can use all protocols except PING (ICMP) only on Server1, located on the server network." This means that for communication with the server, the computers of the sales department can use the HTTP, SSH, FTP protocols - any protocols other than ICMP. In this case, the ACL condition list will look like this.

In the first line, we prohibit all traffic via ICMP, placing a specific condition at the top of the list, and general at the end of the list. This record shows the sales department subnet identifier 192.168.1.0/25, the IP address of a specific Server 1 server is 192.168.1.195/32. The echo parameter means ping traffic, that is, a packet that is sent to the server in order to return back to the computer should be denied.
The second line allows all other traffic coming from the 192.168.1.0/25 subnet to the server address 192.168.1.195/32. As usual, at the end of the list, the default line is Deny any, which means that if the computers in the sales department try to contact the financial department, this traffic will be discarded. Next, we indicate to which router interface the ACL should be applied, and the second problem is solved.
Task 3 is: “Sales2 laptop Laptop2 and finance department PC0 can access management0 laptop Laptop0.” Suppose that these devices are managed by the heads of the sales and accounting departments, who can communicate with the CFO of the CFO located in the management department. There are no restrictions regarding the protocols used, including ICMP.
We already have three ACLs applied to the interfaces that I circled in red on the diagram. Laptop2 cannot contact Laptop0 at the moment, because this contradicts the conditions of Task 3.

To communicate between these two devices, you must add additional conditions to the Allow_Sa ACL.

Similarly, you need to add conditions to the Allow_Acc ACL so that PC0 can freely contact Laptop0.

In both lists, we add lines with the Permit IP parameter, which means allowing traffic over any IP protocol.
As you know, ICMP uses two-way traffic: you send ping, and echo returns it. In our situation, if Laptop2 addresses the address of Laptop0 ping, traffic will flow freely into the network of the management department. However, when the package is returned back to the laptop of the sales department, it will go to the G0 / 0 interface of the R1 router, where the ACL 101 is active. Since the return traffic does not match any of the conditions in this list, it will be blocked. Therefore, we need to supplement the ACL101 list with resolving conditions for both pinging from the Sales2 laptop2 of the sales department and pinging from the finance department's PC0 computer.

We have solved Task No. 3 and now move on to solving Problem No. 4: “The Sales3 laptop Laptop3 can only access its own SALES network and only the Web Service through port 80 on Server 1”.
The first part of the task means that as soon as Laptop3 tries to leave the SALES network, its traffic will be blocked by the R2 router. However, according to the second part of the task, this computer must have access to a Web Service located outside the SALES network. This means that all traffic except traffic directed to the server is blocked.
From the previous tasks, we know that the traffic coming from the sales department is regulated by the Allow_Sa ACL, which we applied to the input interface G0 / 1 of the R2 router. Therefore, we need to change this list, first of all adding the line “allow TCP to server 1 through port 80” in this line: Permit TCP 192.168.1.3/32 192.168.1.195/32 80

The first line means that any HTTP traffic reaches the server, and the second Deny IP 192.168.1.3/32 any means that the rest of the traffic, for example, FTP coming from Laptop3, will be dropped. Next, we leave unchanged the three following lines of the previous ACL, thus solving Problem 4.
I already said that I advise you to write down the solutions to these problems on paper or type them manually on a computer, because they change, and on paper or on a computer you can always add, cross out or delete lines. I draw your attention to the fact that if you simply add the solution to the fourth problem at the end of the ACL, adding two lines, the system will ignore them, because the conditions located above absorb these rules. Since the second line of the old list allows all traffic, the Deny IP condition 192.168.1.3/32, located at the end of the list, simply will not be satisfied.
Thus, the correct sequence of ACL entries is of great importance. First you should develop a logical chain of operations and arrange the lines so that they do not contradict each other. Now let's move on to Packet Tracer and complete all the settings according to the solutions.

Let's start the configuration from the first router, Router1. I use the show access-list command to show that the ACL is currently missing. Next, using the show ip route command, I show that the RIP between the two routers is already configured and working.
Let's go to Laptop0 and ping Server1 at 192.168.1.195. As you can see, pinging is successful, since we do not have any ACLs that prohibit or filter traffic. I am also free to ping Server0.
Now we’ll go to the router Router1, enter the global settings mode and create the ACL 101 list. To do this, I type the command access-list 101 permit tcp. Please note - the system gives a hint which parameter value, except tcp, can be used in this command.

It can be esp, icmp, osfp and so on. CCNA ip, ismp, tcp udp.
, access-list 101 permit tcp 192.168.1.224. /28 16 , 0.0.0.15.
28 4 , 1 , 128, 2 – 64, – 32, 4 16, , (16-1) =15. , . , host IP-, : access-list 101 permit tcp 192.168.1.224 0.0.0.15 host 192.168.1.194.
, , , .

dscp, , eq, , gt – , , lt – .. , eq. .

0 65535, , . FTP 21, SMTP – 25, www – HTTP- 80. 80.
do show run , , 80 www. , , 80 21: access-list 101 permit tcp 192.168.1.224 0.0.0.15 host 192.168.1.194 eq 21.
ICMP-, . access-list 101 permit icmp. host, , IP- 192.168.1.226 0.0.0.0, , . host IP- Laptop2 – 192.168.1.2. – , .

, echo-replay. , . : access-list 101 permit icmp192.168.1.226 0.0.0.0 host 192.168.1.2 echo-replay. : access-list 101 permit icmp 192.168.1.226 0.0.0.0 host 192.168.1.130 echo-replay.
, int g0/0 ip access-group, 101 , IN. Laptop0 192.168.1.194, ACL . , , . IP- 192.168.1.195, .
, Server0 Laptop0 . HTTP FTP- 80 21, ICMP-, . .
-, 192.168.1.194, - Server0.

192.168.1.195, , ACL .
№1 R2 ACL – Allow_Ac. , ACL , . ip access-list extended Allow_Ac .
permit tcp 192.168.1.128. /26, , , – 128, – 64, , 0.0.0.63. , 255.255.255.192 255.255.255.255. permit tcp 192.168.1.128 0.0.0.63 host 192.168.1.194 eq 80. : permit tcp 192.168.1.128 0.0.0.63 host 192.168.1.194 eq 21.
№1 – PC0 Laptop0 . permit ip host 192.168.1.130 host 192.168.1.226 , .
ACL g0/0, ip access-group Allow_Ac IN. , PC0 Server 0, - . PC0 192.168.1.194, Packet Tracer, , R2 .
ACL , ip access-list extended Allow_Sa permit tcp host 192.168.1.3 host 192.168.1.195 eq 80. , HTTP- , , deny ip host 192.168.1.3 any.

, , . deny icmp 192.168.1.0. /25, 1 , 128 , , 0.0.0.127. 192.168.1.195, Server2. ACL : deny icmp 192.168.1.0 0.0.0.127 host 192.168.1.195 echo.
4- , , : permit ip 192.168.1.0 0.0.0.127 host 192.168.1.195.
, Laptop2 Laptop0. permit host 192.168.1.2 host 192.168.1.226, g0/1 ip access-group Allow_Sa IN.

, ACL Laptop3, , - . 192.168.1.195 , PC 192.168.1.130 192.168.1.226. , – - Server1.

Laptop2 Laptop0, . , , 192.168.1.226. Laptop1 , ACL , Laptop0. Laptop2 Server1 192.168.1.195, - . , 4- , ACL.
, , . ACL – , . , , , .
The advantage of CCNA is to learn all the concepts of network development, and the best way to learn the material is to design your own network. I will be glad if you solve these problems in your own way and describe it in the comments to this video. In addition, based on the considered network topology, you can come up with other tasks and try to solve them yourself.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that was invented by us for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
All Articles