10 interesting reports from hacker conferences
I thought that it would be great to cover events from international conferences. And not just in the general review, but to talk about the most interesting reports. I bring to your attention the first hot ten.
- Waiting for a friendly tandem of IoT attacks and ranzomvari
- “Open your mouth, say 0x41414141”: Attack on medical cyber infrastructure
- Toothy exploit on the edge of contextual advertising skewers
- How real hackers dodge targeted advertising
- 20 years of hacking MMORPG: cooler graphics, exploits are the same
- Hack the robots until Skynet arrives
- The militarization of machine learning
- Remember everything: password implantation in cognitive memory
- And asked the baby: “Do you really think that only government hackers can carry out cyber attacks on the power grid?”
- The Internet already knows that I'm pregnant
1. Waiting for a friendly tandem of IoT attacks and ranzomvari
Christopher Elisan. Demystifying The Ransomware and IoT Threat // ROOTCON. 2017
In 2016, we saw a rapid increase in ranzomvari attacks. We have not yet recovered from these attacks, as a new wave of DDoS attacks using IoT has covered us. In this report, the author provides a phased description of how the attack of ranzomvar occurs. How ranzomvar works, and what the researcher should do at each stage, to counter ranzvomar.
At the same time, he relies on proven techniques. Then the speaker sheds light on how IoTs are involved in DDoS attacks: tells what role the auxiliary malware plays in the implementation of these attacks (for subsequent assistance on its part, in conducting a DDoS attack by the IoT army). It also tells how a tandem of ranzomvari and IoT attacks can become a big threat in the coming years. The speaker is the author of the books “Malware, Rootkits & Botnets: a Beginner's Guide”, “Advanced Malware Analysis”, “Hacking Exposed: Malware & Rootkits Secrets & Solutions” - so it’s expertly reported.
2. “Open your mouth, say 0x41414141”: Attack on medical cyber infrastructure
Robert Portvliet. Open Up and Say 0x41414141: Attacking Medical Devices // ToorCon. 2017.
Medical equipment connected to the Internet is ubiquitous clinical reality. Such equipment is of great help to the medical staff, since a significant part of the routine is automated. However, this equipment contains many vulnerabilities (both software and hardware) that open up a wide field of activity for a potential attacker. In the report, the speaker shares his personal experience in conducting pentests for medical cyber infrastructure; and also tells how attackers compromise medical equipment.
The speaker describes: 1) how attackers exploit proprietary communication protocols, 2) how they look for vulnerabilities in network services, 3) how they compromise life support systems, 4) how they exploit hardware debugging interfaces and a system data transfer bus; 5) how they attack the main wireless interfaces and specific proprietary wireless technologies; 6) how they penetrate into medical information systems, and then read and edit: personal information about the patient’s health; official medical records whose contents are normal even from the patient; 7) how they violate the communication system, which medical equipment uses to exchange information and service teams; 8) how do medical personnel restrict access to equipment; or even block it.
During his pentests, the speaker found a lot of problems with medical equipment. Among them: 1) weak cryptography, 2) the ability to manipulate data; 3) the ability to remotely replace equipment, 3) vulnerabilities in proprietary protocols, 4) the possibility of unauthorized access to databases, 5) hard-coded immutable usernames / passwords. And also other sensitive information stored either in the firmware of the equipment or in the system binaries; 6) the susceptibility of medical equipment to remote DoS attacks.
After getting acquainted with the report, it becomes obvious that the cybersecurity of the medical sector today is a clinical case and needs intensive care.

3. Toothy exploit on the edge of contextual advertising skewers
Tyler Cook. False Advertising: How Modern Ad Platforms Can Be Used for Targeted Exploitation // ToorCon. 2017.
Every day, millions of people go to social networks: for work, for entertainment or just like that. Under the hood of social networks are ads-platforms invisible to the average visitor, responsible for delivering relevant contextual advertising to visitors of social networks. Ads platforms are easy to use and very effective. Therefore, in demand among advertisers.
In addition to the opportunity to reach a wide audience, which is very beneficial for business, Ads-platforms also allow you to narrow the scope of targeting - down to one specific person. Moreover, the functionality of modern Ads-platforms even allows you to choose on which of the many gadgets of this particular person to show ads.
T.O. modern Ads-platforms allow the advertiser to reach any person, anywhere in the world. But this opportunity can also be used by attackers, as an entrance gateway to the network in which their alleged victim works. The speaker demonstrates how a malicious advertiser can use the Ads platform to accurately target his phishing campaign, deployed to deliver a personalized exploit to one specific person.
4. How real hackers dodge targeted advertising
Weston Hecker. Opt Out or Deauth Trying! - Anti-Tracking Bots Radios and Keystroke In-jection // DEF CON. 2017.
We use many different computerized services in our daily lives. And it’s hard for us to refuse them, even when we suddenly find out that they are conducting total surveillance on us. So total that they track our every movement and each of our fingertips.
The speaker lucidly explains how exactly modern marketers use a wide variety of esoteric targeting methods. We recently wrote about mobile paranoia, about total surveillance. And many readers took what was written with an innocuous joke, but it can be seen from the presented report that modern marketers are already fully using similar technologies to track us.
Well, what can you do, the contextual advertising industry, which fuels this total surveillance, is taking leaps and bounds. To the extent that modern Ads-platforms can track not only the network activity of a person (keystrokes, moving the mouse pointer, etc.), but also his physiological characteristics (how we press keys and move the mouse). T.O. modern means of tracking Ads-platforms built into services without which we cannot imagine life - not only under our underwear crawl to us, but even under our skin. If we do not have the opportunity to refuse these overly observational services, then why not try to at least bombard them with useless information?
The report demonstrated the author's device (hardware and software bot), which allows you to: 1) inject Bluetooth beacons; 2) noisy data collected from the vehicle's on-board sensors; 3) falsify the identification parameters of the mobile phone; 4) to make noise in the manner of fingering (on the keyboard, mouse and sensor). All this information is known to be used to target ads on mobile gadgets.
The demonstration shows that after the launch of the author’s device, the tracking system goes crazy; that the information she collects becomes so noisy and inaccurate that our observers will no longer benefit from it. As a joke, the speaker demonstrates how, thanks to the presented device, the “tracking system” begins to perceive a 32-year-old hacker - for a 12-year-old girl who loves horses madly.
5. 20 years of hacking MMORPG: cooler graphics, exploits are the same
Twenty Years of MMORPG Hacking: Better Graphics, Same Exploits // DEF CON. 2017.
The topic of hacking MMORPG has been discussed at DEF CON for 20 years. Paying tribute to the anniversary, the presenter describes the most iconic moments of these discussions. In addition, he talks about his adventures in the field of poaching in online toys. Starting with Ultima Online (in 1997). And the following years: Dark Age of Camelot, Anarchy Online, Asherons Call 2, ShadowBane, Lineage II, Final Fantasy XI / XIV, World of Warcraft. Including several fresh representatives: Guild Wars 2 and Elder Scrolls Online. And this is far from the whole track record of the speaker!
The report provides technical details on creating exploits for MMORPGs that help virtual money get hold of, and which are relevant for almost every MMORPG. The speaker briefly talks about the eternal confrontation between poachers (manufacturers of exploits) and "fish surveillance"; and the current technical condition of this arms race.
Explains the technique of detailed analysis of packages and how to configure exploits so that the fact of poaching was not detected on the server side. Including presents the latest exploit, which at the time of the report - had an advantage over the "fish surveillance" in the arms race.
6. Hack robots until Skynet comes
Lucas Apa. Hacking Robots before Skynet // ROOTCON. 2017.
Robots are now heard. In the near future, they will be everywhere: on military missions, in surgical operations, in the construction of skyscrapers; Shop assistants in stores hospital attendants; business assistants, sexual partners; home cooks and full family members.
As the ecosystem of robots expands, and the influence of robots in our society and economy grows rapidly, they begin to pose a significant threat to people, animals and enterprises. At its core, robots are computers with arms, legs and wheels. And with the current realities of cybersecurity, these are vulnerable computers with arms, legs, and wheels.
Software and hardware vulnerabilities of modern robots allow an attacker to use the physical capabilities of the robot, - to cause property or financial damage; or even by accident or intentionally create a threat to human life. Potential threats to everything near robots increase exponentially over time. Moreover, they are growing in such contexts as the established industry of computer security had never seen before.
In his recent studies, the speaker found many critical vulnerabilities in home, corporate and industrial robots, from well-known manufacturers. In the report, he reveals the technical details of current threats, and explains how attackers can compromise various components of the robot ecosystem. With a demonstration of existing exploits.
Among the problems identified by the speaker in the ecosystem of robots: 1) unsafe communications; 2) the possibility of memory corruption; 3) vulnerabilities that allow remote code execution (RCE); 4) the possibility of violating the integrity of the file system; 5) problems with authorization; and in some cases a general lack thereof; 6) weak cryptography; 7) problems with updating the firmware; 8) privacy issues; 8) undocumented features (also vulnerable to RCE, etc.); 9) weak default configuration; 10) vulnerable Open Source "frameworks for controlling robots" and software libraries.
The speaker gives live demonstrations of various hacking scenarios related to cyber espionage, insider threat, property damage, etc. Describing realistic scenarios that can be observed in the wild, the speaker talks about how the insecurity of modern robot technology can lead to hacking. Explains why hacked robots are even more dangerous than any other compromised technology.
The speaker also draws attention to the fact that raw research projects go into production before security issues are resolved. Marketing always wins. An urgent need to correct this unhealthy state of affairs. Until Skynet comes. Although ... The next report suggests that Skynet has already arrived.
7. The militarization of machine learning
Damien Cauquil. Weaponizing Machine Learning: Humanity Was Overrated Anyway // DEF CON 2017.
At the risk of being known as an extravagant scientist, the speaker is still touched by his “brand new devilish creation”, proudly presenting DeepHack: an open source hacker AI. This bot is a self-learning web application cracker. It is based on a neural network, which is trained by trial and error. At the same time, to possible consequences for a person from these trial and error, DeepHack treats with terrifying neglect.
Using just one universal algorithm, he learns to exploit various types of vulnerabilities. DeepHack opens the door to the realm of hacker AI, many of which can already be expected in the near future. In this regard, the speaker proudly characterizes his bot as "the beginning of the end."
The speaker believes that AI-based hacking tools that are coming soon following DeepHack are a fundamentally new technology that cyber defenders and cyber attackers have yet to adopt. The speaker guarantees that next year each of us will either write hacker tools with machine learning himself, or he will desperately try to defend himself against them. There is no third.
Also, either jokingly or seriously, the speaker states: “The inevitable anti-utopia of AI, which is no longer the prerogative of diabolical geniuses, is already available to everyone today. Therefore, join us and we will show how you can participate in the destruction of mankind by creating your own militarized machine learning system. Of course, if guests from the future do not prevent us from doing this. ”

8. Recall everything: implanting passwords into cognitive memory
Tess Schrodinger. Total Recall: Implanting Passwords in Cognitive Memory // DEF CON. 2017.
What is cognitive memory? How can one “implant” a password there? And is it generally safe? And why do such tricks? The idea is that when using the described approach, you will not be able to chat about your passwords, even under duress; while maintaining the possibility of authorization in the system.
The report begins with an explanation of what cognitive memory is. It then explains the difference between explicit and implicit memory. Next, the concepts of the conscious and the unconscious are analyzed. And it also explains what kind of essence it is - consciousness. It describes how our memory encodes, stores and retrieves information. The limitations of human memory are described. And also how our memory is trained. And the report ends with a story about modern research on human cognitive memory, in the context of how to introduce passwords into it.
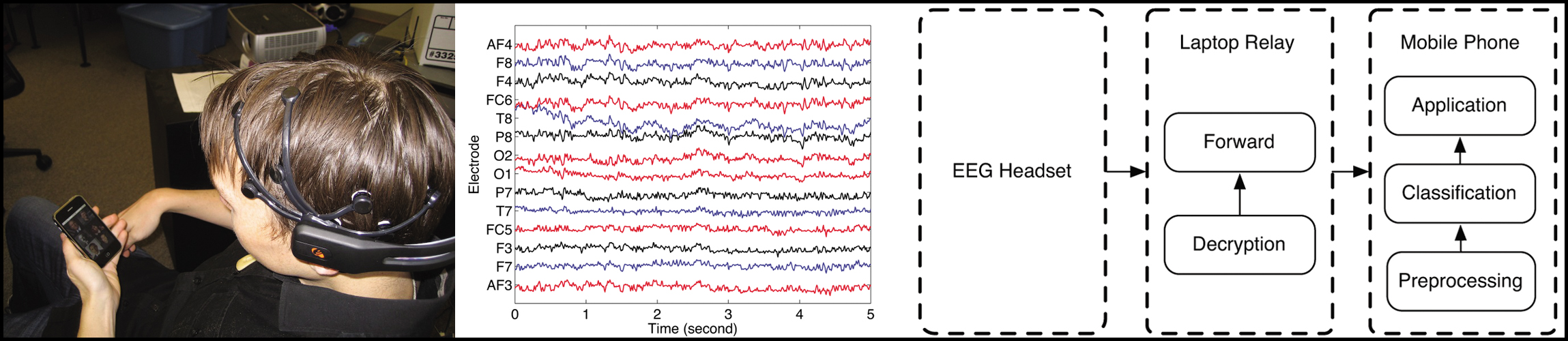
The speaker, of course, did not bring the ambitious statement made in the title of his presentation to a complete solution, but at the same time he brought several interesting studies that are on the approaches to solving the problem. In particular, research at Stanford University, the subject of which is the same subject. And a project to develop a human-machine interface for visually impaired people - with a direct connection to the brain. The speaker also refers to a study by German scientists who managed to carry out an algorithmic connection between brain electrical signals and verbal phrases; the device they developed allows you to type text just by thinking about it. Another interesting study referred to by the speaker is a neurotelephone, an interface between the brain and a mobile phone, using a wireless EEG headset (Dartmouth College, USA).
As already noted, the speaker made no ambitious statement in the title of his presentation to a complete decision. However, the speaker notes that despite the fact that there is no technology for implanting a password into cognitive memory yet, the malware who is trying to extract it from there is already there.
9. And the crumb asked: “Do you really think that only government hackers can carry out cyber attacks on the power grid?”
Anastasis Keliris. And then the Script-Kiddie Said Let There Be No Light. Are Cyber-Attacks On the Power Grid Limited To Nation-State Actors? // BlackHat. 2017.
The uninterrupted operation of electricity is of paramount importance in our daily lives. Our dependence on electricity becomes especially apparent when it is turned off - even for a short time. Today it is generally accepted that cyber networks on the grid are extremely complex, and are available only to government hackers.
The speaker disputes this established opinion and presents a detailed description of the attack on the power grid, the costs of which are acceptable even for non-governmental hackers. It demonstrates information collected from the Internet that will be useful in modeling and analyzing the target energy network. It also explains how this information can be used to model attacks on power grids around the world.
The report also demonstrates the critical vulnerability discovered by the speaker in the products of General Electric Multilin, which are widely used in the energy sector. The speaker describes how he completely compromised the encryption algorithm used in these systems. This algorithm is used in General Electric Multilin products for secure communication of internal subsystems, and for managing these subsystems. Including for authorization of users and providing access to privileged operations.
Having learned access codes (as a result of compromising the encryption algorithm), an attacker can completely cut down the device and turn off the electricity in the given sectors of the power network; block operators. In addition, the speaker demonstrates the technique of remotely reading digital tracks, which leaves equipment vulnerable to cyber attacks.
10. The Internet already knows I'm pregnant
Cooper Quintin. The Internet Already Knows I'm Pregnant // DEF CON. 2017.
Women's health is big business. There are so many Android apps on the market that help women track their monthly cycle, know when they are most likely to conceive, or track their pregnancy status. These apps encourage women to capture the most intimate details of their life, such as mood, sexual activity, physical activity, physical symptoms, height, weight, and more.
But how confidential are these applications, and how secure are they? After all, if the application stores such intimate details about our personal life, it would be nice if it did not scatter these data with anyone else; for example, with a friendly company (targeting ads, etc.) or with a malicious partner / parent.
The speaker presents the results of his cybersecurity analysis of more than a dozen applications that predict the likelihood of conception and track the course of pregnancy. He found that in most of these applications, there are serious problems with cybersecurity in general and privacy in particular.
All Articles