Security Week 33: interesting with Black Hat / DEF CON 2019
 The next Black Hat / DEF CON double conference was held in Las Vegas last week. If the first event smoothly moves towards a business rivalry, the second is still the best conference for hackers (mainly in the good sense of the word), for whom finding weak spots in hardware and software remains primarily an art, and only after that - a way to make money for life. In a digest based on these two conferences last year, we talked about vulnerabilities in outdated VIA C3 processors, supply chain attacks on Apple computers and about breaking into an unnecessary Wi-Fi SD adapter.
The next Black Hat / DEF CON double conference was held in Las Vegas last week. If the first event smoothly moves towards a business rivalry, the second is still the best conference for hackers (mainly in the good sense of the word), for whom finding weak spots in hardware and software remains primarily an art, and only after that - a way to make money for life. In a digest based on these two conferences last year, we talked about vulnerabilities in outdated VIA C3 processors, supply chain attacks on Apple computers and about breaking into an unnecessary Wi-Fi SD adapter.
This year's agenda included attacks on printers, office phones and children's tablets, a half-round bypass of Apple FaceID's face recognition system and (who would have thought) a ransomware-encryptor in the Canon camera. Plus two, let's say, an art project: cables for the iPhone with a backdoor and cheating on a smart exercise bike. Finally, an interesting study about the use of GDPR to steal another person’s personal information. Wait, but GDPR is legislation aimed at protecting personal data? Well, we thought so too.
Hacking printers, office phones and children's tablets
Let's start with a relatively boring study. NCC Group specialists found many vulnerabilities in office printers manufactured by HP, Ricoh, Xerox, Lexmark, Kyocera and Brother. The magnitude of the problem can be assessed by the example of a report for HP printers: there are vulnerabilities in the IPP network printing protocol, and buffer overflows in the built-in web server, and errors leading to cross-site scripting attacks. The most dangerous vulnerabilities allow you to either organize a DoS attack or execute arbitrary code with incomprehensible consequences.
An incident occurred last year showing what happens to printers that are a) unprotected and b) accessible from the Internet. On 50 thousand devices, an anonymous “activist” printed a call to subscribe to one odious YouTube. In the NCC Group study, there is a hint of

But what if you use not printers, but office phones? This option was investigated by a McAfee representative. He found a ten-year-old firmware in Avaya VoIP phones. Among other things, the dhclient client used in phones had a vulnerability known since 2009 . This problem can cause buffer overflows if the subnet mask parameter is too long to pass to the DHCP client, and, again, there is a theoretical danger of arbitrary code execution. So the “work - do not touch” approach is not applicable even in the case of such relatively simple devices as an office phone. Although the vulnerability in dhclient is exploited if you have access to the local network, it’s still worth rolling the patch onto the telephones. Need to touch!

A study of LeapFrog's LeadPad Ultimate children's tablets revealed childhood vulnerabilities. Chekmarx experts showed how you can locate devices using readily available tools and intercept traffic. The most serious problem is caused by the additional application Pet Chat, which allows parents to communicate with their children (or children to communicate with each other) using a set of phrases “wired” into the tablet. To establish a connection, the tablet creates an open access point called Pet Chat. The geolocation of a certain number of tablets was found in open databases of Wi-Fi access points. Authorization of the pair “parent’s smartphone - child’s tablet” is not provided, so anyone within the range of the wireless network can connect to the device. We must pay tribute to the manufacturer: the problem was quickly resolved by removing the application from free access. Oh yes, in any case, the tablet communicated with the manufacturer’s servers via HTTP, which allowed for an attack such as Man-in-the-Middle:
Glasses with electrical tape, a trojan in the camera, a cable for iPhone with a surprise
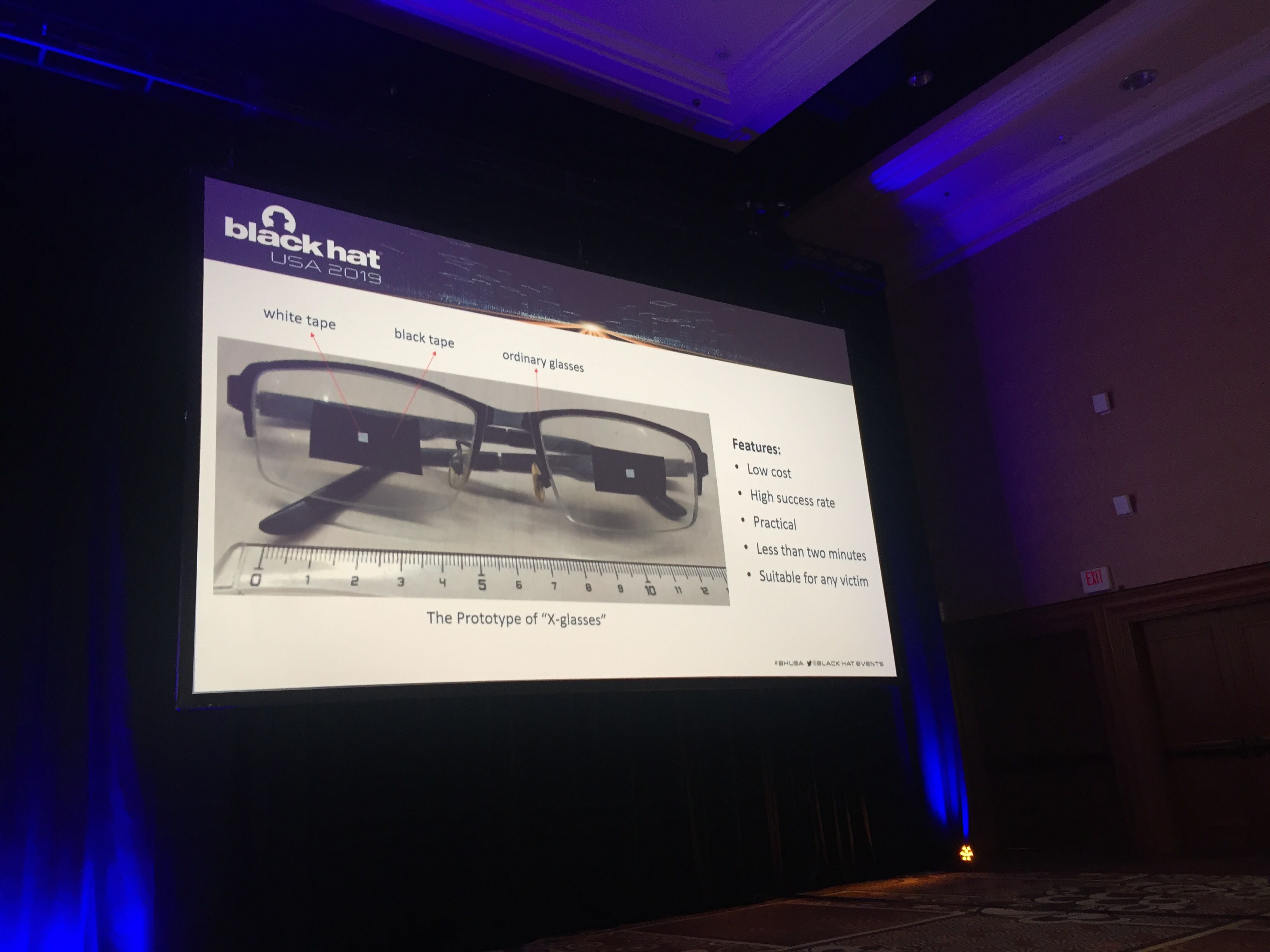
Let's move on to the more interesting, although perhaps less practical topics of presentations at Black Hat / DEF CON. Researchers from the Tencent company showed ( news , one more news on Habré) a way to partially bypass FaceID facial recognition system in Apple smartphones. FaceID is quite well protected from attempts to unlock using the owner’s photo, or if, for example, you bring the phone to a sleeping person. For this, a three-dimensional model of the face is created and eye movement is monitored. But if the user wears glasses, then a detailed 3D model for this part of the face is not created - presumably in order to avoid recognition problems. In this case, the iPhone still checks whether the person’s eyes are open, identifying pupils with the camera. But since the recognition quality is intentionally impaired, the “open-eye detector” was circumvented using electrical tape: a light square on a dark background, glued to the lenses, is identified by the phone as pupils.
Okay, this is a cool study, but in practice it’s only a little easier to unlock someone else’s phone. It is necessary to sneak up on a sleeping person and put on him glasses with electrical tape. Or to assume not the most pleasant scenario in which a person is unconscious. In any case, the recognition algorithm would be worth tightening up: even if building a 3D model with glasses is impossible for some reason, it is advisable in this situation to improve the quality of image analysis from a conventional camera.

Check Point Software hacked the Canon EOS 80D. Why a camera? Because they could! In total, six vulnerabilities were discovered in the camera, and the most serious of them is present in the PTP protocol for communicating with a computer. As it turned out, when connected to a PC, you can initiate a device firmware update without user confirmation. Through forced flashing, the researchers were able to install a real ransomware trojan on the camera: it encrypts the photos on the memory card and displays the ransom demand on the screen. Canon has released a newsletter for camera owners (in which for some reason there is no direct link to the new firmware version). The report says that there are no real victims and it is recommended not to connect the camera to questionable computers. Indeed, to whom it would occur to attack a camera?
Vice wrote about an activist who was distributing (and selling for $ 200) homemade iPhone cables with a built-in backdoor on Black Hat. The victim of this cable, however, is not the phone, but the computer to which the device is connected for synchronization (synchronization, if that, also works). The backdoor is a Wi-Fi access point and, apparently, a keyboard emulator. At the beginning of the article, we used the term “hackers” in its positive meaning, but this experiment, so to speak, is on the lower boundary of the positive. The cable creator remained anonymous, sold cables using bookmarks in the conference area. And he successfully sold all two hundred pieces.
Finally, the attention of The Register news site was awarded by the presentation of a student at Oxford University, James Pavur. He conducted a social experiment, sending 150 companies the requirement to provide information in accordance with the norms of the European legislation GDPR. The law gives users the right to receive information about themselves from companies that collect and process personal data. An important nuance of history is that James did not request information about himself, but about his bride. Of the 150 companies surveyed, 72% answered the request.
Of these, 84% admitted that they have information about the bride of the researcher. As a result, a social security number, date of birth, maiden name, credit card number, and partially the address of residence were obtained. One company collecting information about leaked passwords sent a list of passwords for the email address. And this despite the fact that not all companies agreed to provide data: in 24% of cases, the email address and phone number of the (voluntary) victim were sufficient for identification, in 16% of cases an ID scan (easily forged) was required, and another 3% of companies just deleted all the data without providing it. This experiment is not intended to disprove the benefits of GDPR. Rather, it shows that companies are not always ready to fulfill their new obligations, and there are no generally accepted methods for identifying users yet. But it would be necessary: otherwise, attempts to follow the law lead to the completely opposite effect.
Bonus Material: Researcher Brad Dixon has found a way to trick an exercise bike with built-in gamification ( article in Vice, project website ). Zwift simulators allow you to turn a real bike into a room version for home workouts by replacing the rear wheel with a module that provides the load. The simulator comes with software for virtual bike rides, with records and competition. Zwift identifies simple cheaters (screwing a screwdriver to a simulator), so Dixon had to bypass protection using non-trivial methods: intercept signals from sensors, emulate plausible traffic, and so on. As a result, the gas pedal (go very fast) and the cruise control (go at a constant speed, slightly changing the fake data from the sensors) were added to the simulator. “Now you have the opportunity, without interrupting your training, to go for a beer or for something else,” commented the author of the study.
Disclaimer: The opinions expressed in this digest may not coincide with the official position of Kaspersky Lab. Dear editors generally recommend treating any opinions with healthy skepticism.
All Articles