Vulnerability in Intel CPU: affected by Windows and Linux, closing the vulnerability will lead to a performance drop of up to 30%
If the messages are correct, Intel has allowed a very serious vulnerability in its CPUs, and it cannot be fixed by updating the microcode. Vulnerability affects all Intel processors over the past ten years at least.
Closing the vulnerability requires an OS update, patches for Linux have already been released, Microsoft plans to close it as part of the traditional monthly “Tuesday patches”. At the moment, the details of the vulnerability have not been disclosed, but some details still emerged out thanks to Python Sweetness and The Register.

Vulnerability allows programs to gain unauthorized access to certain data in a protected area of kernel memory. This can be prevented by introducing kernel memory isolation (Kernel Page Table Isolation), which will make the kernel “invisible” to current processes. This is not an ideal solution, but future patches for Windows, Linux and macOS will use this approach.
However, such a decision can seriously hit performance. The drop in performance due to insulation can be as high as 30 percent. Fortunately, the latest models of Intel processors with PCID technology (process context identifiers) may reduce the performance drop, though not avoiding it at all.
Vulnerability can be exploited in real conditions; in the first place, companies using virtualization can be hit.
“The development of a software solution to the problem is being carried out urgently, and it has recently been introduced into the Linux kernel; in NT cores, a similar decision began to appear in November, ”the Python Sweetness unit reported. “In the worst case, this would entail a serious slowdown in everyday tasks.”
"There is reason to suspect that popular virtualization environments are vulnerable, including Amazon EC2 and Google Compute Engine."
Microsoft Azure and Amazon Web Services have already scheduled a temporary shutdown of servers next week, although they do not comment on the cause of the work. However, it is probably the need to protect against possible attacks using the found vulnerability is its cause.
Note that AMD has not been mentioned yet. It's simple: AMD processors are not affected by this vulnerability - and, therefore, they do not need resource-intensive protection from it.
Thomas Lendaki, a member of the Linux group working with AMD, reports :
“AMD processors are not subject to attacks, which are protected by core memory isolation. The AMD architecture does not allow access to data in the absence of appropriate privileges. ”
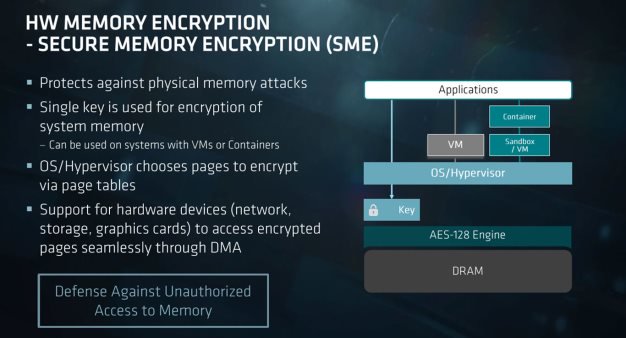
In addition, AMD's new EPYC server chips, as well as their Ryzen Pro desktop processors, have encrypted memory encryption technology that provides additional protection against attacks of this kind.
One way or another, until the details of the patches are revealed, and Intel, for obvious reasons, prefers to remain silent, we can only wait until the seriousness of the problem and the threat it carries to existing computer platforms can be fully assessed. But at the moment it all looks very serious. The patch with the solution (kpti) for Linux was added to the kernel personally by Linus Torvalds .
Phoronix has already tested performance with kpti turned on and came to the conclusion that drawdowns of up to 17-18 percent are possible.
It is also reported that the patch for Linux will by default include kpti on computers with AMD processors, causing a corresponding drop in performance. AMD does not recommend using kpti on computers with AMD processors. Details of the Windows solution are not yet known.
Closing the vulnerability requires an OS update, patches for Linux have already been released, Microsoft plans to close it as part of the traditional monthly “Tuesday patches”. At the moment, the details of the vulnerability have not been disclosed, but some details still emerged out thanks to Python Sweetness and The Register.

Vulnerability allows programs to gain unauthorized access to certain data in a protected area of kernel memory. This can be prevented by introducing kernel memory isolation (Kernel Page Table Isolation), which will make the kernel “invisible” to current processes. This is not an ideal solution, but future patches for Windows, Linux and macOS will use this approach.

However, such a decision can seriously hit performance. The drop in performance due to insulation can be as high as 30 percent. Fortunately, the latest models of Intel processors with PCID technology (process context identifiers) may reduce the performance drop, though not avoiding it at all.
Vulnerability can be exploited in real conditions; in the first place, companies using virtualization can be hit.
“The development of a software solution to the problem is being carried out urgently, and it has recently been introduced into the Linux kernel; in NT cores, a similar decision began to appear in November, ”the Python Sweetness unit reported. “In the worst case, this would entail a serious slowdown in everyday tasks.”
"There is reason to suspect that popular virtualization environments are vulnerable, including Amazon EC2 and Google Compute Engine."
Microsoft Azure and Amazon Web Services have already scheduled a temporary shutdown of servers next week, although they do not comment on the cause of the work. However, it is probably the need to protect against possible attacks using the found vulnerability is its cause.
Note that AMD has not been mentioned yet. It's simple: AMD processors are not affected by this vulnerability - and, therefore, they do not need resource-intensive protection from it.
Thomas Lendaki, a member of the Linux group working with AMD, reports :
“AMD processors are not subject to attacks, which are protected by core memory isolation. The AMD architecture does not allow access to data in the absence of appropriate privileges. ”

In addition, AMD's new EPYC server chips, as well as their Ryzen Pro desktop processors, have encrypted memory encryption technology that provides additional protection against attacks of this kind.
One way or another, until the details of the patches are revealed, and Intel, for obvious reasons, prefers to remain silent, we can only wait until the seriousness of the problem and the threat it carries to existing computer platforms can be fully assessed. But at the moment it all looks very serious. The patch with the solution (kpti) for Linux was added to the kernel personally by Linus Torvalds .
Phoronix has already tested performance with kpti turned on and came to the conclusion that drawdowns of up to 17-18 percent are possible.
It is also reported that the patch for Linux will by default include kpti on computers with AMD processors, causing a corresponding drop in performance. AMD does not recommend using kpti on computers with AMD processors. Details of the Windows solution are not yet known.
All Articles