SIGSALY or the Green Hornet: on the protection line of communication Washington - London
SIGSALY was a digital voice encryption system, developed by Bell Telephone Laboratories (BTL, USA) in 1941-1942 and released by Western Electric (New York, USA) in 1943. The system was commissioned in April 1943 and was used during the Second World War until 1944. SIGSALY served for confidential negotiations at the highest state level, between British Prime Minister Winston Churchill and US President Roosevelt. The system worked according to the principle of the Vernam cipher (OTP). Known was under various code names, one of which is "The Green Hornet / Green Hornet".

Bell Telephone Laboratories (BTL) - an American research company, was founded in 1925. Initially, it was a union of Western electrical research laboratories and the engineering department of the American Telephone and Telegraph Company (AT & T). Over its history, the company bore various names: Bell Laboratory, Bell Telephone Laboratories, Bell Telephone Labs, Bell Labs, AT & T Bell Laboratories, AT & T Bell Labs, Lucent Technologies, Bell Labs Innovations. At the moment - Nokia Bell Labs.

BTL has many important inventions and developments: radio astronomy, transistor, laser, photovoltaic cell, charge-coupled device (eng. CCD, Charge-Coupled Device), the first versions of the UNIX operating system and programming languages C and C ++. In the war years, the Bell laboratory developed the unbreakable telephone system, SIGSALY, to transfer messages between Allied forces.

The SIGSALY system embodied a number of innovative digital communication concepts, including the first pulse code modulation (PCM / PCM), which is used to digitize analog signals.
The SIGSALY system consisted of more than 30 equipment racks, 4 disk rotation mechanisms (two on each side). The system weighed 50 tons, and consumed such a machine of 30 kW. In 1943, the cost of one such terminal was 1 million US dollars. A total of 12 SIGSALY terminals installed worldwide, the first system in the Pentagon.
The second system was installed in London, in the basement of Selfridges department store in London on the famous Oxford Street. Another system worked on a ship plying the ocean under the command of General Douglas MacArthur (during the times of the Pacific campaigns). Although MacArthur was plagued by doubts about the reliability of classifying telephone conversations, he preferred to use the direct-printing SYGTOT radio communications equipment with preliminary encryption of information. After installation, the systems were serviced by specially trained and reliable members of the 805 communications company of the United States Armed Forces. During the period 1943 - 1946, over 3,000 telephone conversations at the highest state level were conducted by means of 12 working terminals SIGSALY.
SIGSALY provided full-duplex voice communication over high-frequency (HF) radio channels in the HF band. Each half of the channel used 12 separate data channels or carrier frequencies, MFSK (Multi-Shift Frequency Keying) data transmission protocols were used, such protocols did not have a range limitation and were resistant to interference occurring on the low-frequency HF bands.
Human speech was analyzed only 50 times / second, every 20 ms it was broken up into components, and then encoded and sent across the Atlantic. On the receiving side, the data was decoded, restored, after which the original speech was reproduced.
As a result of the low data transfer rate (today comparable to 1500 baud) it was difficult to recognize a person by voice at the other end. Later the technology was improved, other speech coding algorithms appeared, such as LPC-10, CELP and MRELP (for example, in STU-I equipment).
After the system was ready, the BTL developers conducted the rest of the war, working on the successor to SIGSALY, known as Junior X or AN / GSQ-3. Junior X was planned as a mobile version and occupied "only" six racks, could be installed in a mobile van, but the project was never completed on time, and therefore was not used. After the war, the SIGSALY system was decommissioned, partially destroyed, including documentation, the racks were thrown overboard in 1946.

The SIGSALY system used a cryptographically unbreakable coding scheme based on the so-called OTP (One-Time Pad / disposable notebook)
The principle of this scheme was as follows: the human voice was initially digitized, then mixed with an element from a previously randomly generated key stream. When properly applied, such a system could be unbreakable. The main requirement is that both parties should have a sufficient amount of key material.
In the SIGSALY system, a random key stream was recorded on encrypted disks. Only two copies of records were made, one copy was sent by a special courier to the other end of the line. Since each disc could contain only 12 minutes of key material, accordingly, more than one such disc and the correct distribution of key material were required for long conversations.
In addition to the key distribution problem, there was another difficulty - synchronization. At the two ends of the radio link, not only identical cipher-disks had to be installed, but they also had to work at the same rotational speed in order to ensure synchronization of key sequences generation.
As mentioned earlier, the record contained 12 minutes of key material, two synchronized encryption disks were used, the second was a replica of the first one. Since SIGSALY was a full duplex system, each terminal had four players: two transmitters and two receivers. Vinyl records were originally used (1943). They had a code name - SIGGRUV. Later they were replaced by thin-coated aluminum plates of acetate varnish codenamed SIGJINGS.
Such plates with SIGGRUV and SIGJINGS records are called OTP records or disposable records (OTR). After use, such records were immediately destroyed, so that the enemy could never decipher any part of the secret conversation.

The first SIGSALY terminal was installed at the Pentagon (Washington, USA), the new headquarters of the US Department of Defense, whose construction was completed in January 1943. It was originally planned to place the car in the White House, but because of its size, this idea was rejected. Instead, the Pentagon became the home of SIGSALY, and an additional line of communication was laid to the presidential residence. After installation, 805 communications companies of the United States Armed Forces took up maintenance. The members of the company were selected and underwent special training from BTL employees at a special school established for this purpose in New York. In 1944, except for the 805 company, and the school itself was moved to the Pentagon. 193 officers were trained in the use of SIGSALY. 805 company consisted of 356 people: 81 officers and 275 soldiers, who were divided into 12 troops. In each detachment there were 5 officers and 10 servicemen. They followed the work of the system 24/7.

In the UK, the SIGSALY system was located in the SWOD basement to Selfridges department store on Oxford Street (London). The first conference was held on July 15, 1943; British Prime Minister Winston Churchill was among the users of this machine.
The image above is the main building of the Selfridges department store on Oxford Street (1929) ten years before the start of World War II. At the time, the Selfridges building had a basement known as SWOD, it was named after the four roads that surrounded it: Somerset, Wigmore, Orchard and Duke (the last three streets still exist). So this basement had its basement 60 meters below the ground. In 1942, after the United States entered World War II, the SWOD basement room was used by the United States Army because the room was a safe bomb shelter. Here we had a secure communication line, and in April 1943 we installed the SIGSALY terminal. The first negotiations between the two countries probably concerned the Allied invasion of Sicily and the upcoming invasion of Italy.
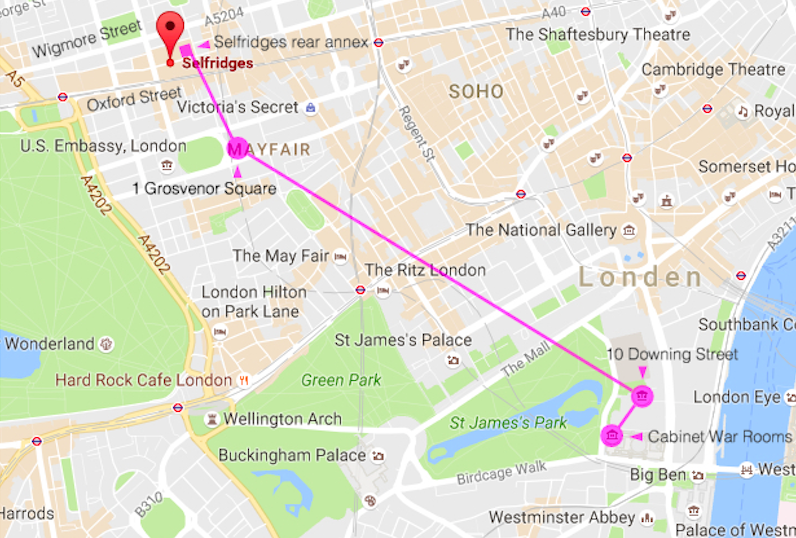
The map above shows that Selfridges basement was located close to the US Embassy. Even today there are rumors about a tunnel between two objects. Initially, in order to use SIGSALY for a safe conversation with the US president, Selfridges had to come, later the system was connected via extended lines to the US embassy, to the office of British Prime Minister Winston Churchill on Downing Street, to the bunker. Churchill could, if necessary, contact the US president at any time of the day or night.
Because of its size, the SIGSALY system, as a rule, was not installed in the office, but was located, as a rule, in large rooms nearby. The offices, in turn, were connected to the SIGSALY terminal through special protected extension lines, known as OPEPS.

OPEPS is short for Off-Premises Extension Privacy System. In Washington, two OPEPS lines were conducted from the Pentagon to the White House and to the building of the Naval Ministry (USA). In London, three such lines were carried out: one to the US embassy, the other to the cabinet of British Prime Minister Winston Churchill on Downing Street, and the third to the bunker (Church War Cabinet).

Since these extended lines allowed “top-secret traffic” to pass through at a high state level, various security measures had to be applied to protect them from both wiretapping and external interference. Cables and connections between SIGSALY and its extended lines have been protected using gas and microswitches. Any interference led to a drop in gas pressure, which triggered the alarm. At the slightest interference, an imbalance occurred on the line, causing strong noise interference, the user heard noise and understood that the line was unsafe at that moment.
Do not confuse OPEPS with the SIGSALY system, the lines connecting the system with Secraphone - known as the scrambler. Although both phones looked the same and served similar purposes, Secraphone was not so secure and protected. It was used to protect against accidental eavesdropping, for example, by a telephone exchange operator, but not against professional wiretapping. Synonym for him is confidentiality, but not secrecy.

Secraphone

At the beginning of World War II, the United States Armed Forces used the A-3 voice scrambler developed by Western Electric for state-level negotiations. The A-3 scrambler was used by both sides during the war, although it was known that it did not have a sufficient measure of reliability and security, the information could be easily intercepted and cracked using simple tools such as a regular oscilloscope. The fact remained a fact, and the issue of creating a secure connection reached its climax. As early as October 1940, Bell Telephone Laboratories (BTL) began the development of an unbreakable transatlantic voice telephony system called Project X.
In Bell, the study was carried out by two teams: one conducted basic research, and the second was engaged in solving practical problems of design, construction, and instruction. During the research, Peterson and Dudley's works on the invention and principle of operation of the vocoder were taken.
Vocoder Dudley, dubbed Voder 3, was demonstrated by BTL at the New York World's Fair in 1939, the company showed how, by analyzing the speech signal, the voice path is modeled by a shaping filter. Vocoder compressed 10: 1 voice bandwidths. The device determined the main parameters of the signal, encoded them and transmitted the radio signal via short-wave channels. Such a digital encryption system is similar to that developed by Gilbert Vernam.

But before the secure, secure transatlantic telephone system saw the world, it was necessary to solve many technical and mathematical problems. Numerous tests and experiments were conducted, as a result of which it was decided to combine the principles of operation of the vocoder and the device for encrypting alphanumeric information. The frequency spectrum (150 Hz - 2950 Hz) was divided into 10 channels, each of which was digitized.
In the process of developing the system and solving its problems, many discoveries and inventions were made, a considerable number of (secret) patents were filed, some of which for 35 years remained under the “secret” stamp.

By the end of 1941, the designs of individual parts of the system were more or less ready, and the layouts were created. The next stage - the creation of a prototype - was taken up by the AM Curtis research group. The system was assembled on the 12th floor of the Graybar-Varick building in New York.

Graybar-Varick, New York
In fact, Western Electric (WE) was involved in the production of machines. BTL engineers used standard spare parts from WE, which were easily accessible, and not “original-designed” parts for the machine. Because of this, the dimensions of the system have increased, but this significantly reduced the time to manufacture.
The system included 12 parallel data transmission channels. In March 1942, the data channel was tested using a signal level control, imitating a transatlantic radio. In April 1942, after the successful completion of the tests, they set up the remaining channels. The experimental model of the system was completed by the end of the summer of 1942.
In November of the same year, the system was first tested on transatlantic radio, later the system was tuned and improved.
The prototype was nicknamed The Green Hornet / Green Hornet, in honor of the popular radio show of the 1930s with the same name. The melody of the show was reminiscent of a buzzing sound, reminiscent of sound when transmitting coded signals.

It is necessary to emphasize the fact that all work was initiated by BTL, although both the National Defense Research Committee and the Corps of Communications were aware of the work, they became interested in this program as early as 1942. After completing work on an experimental model, the Corps of Communications Troops sponsored the development of several terminals. From that moment on, the project began to carry the code name SIGSALY.
After completing and testing some parts of the Western Electric system, they were sent to Room L30 on West Street, the former sound film lab, where they were assembled into a single system. Work on the first system was completed on April 1, 1943, the second system was soon ready, and this allowed the first real test to be carried out.
At the end of April 1943, the first terminals were installed in Washington (Pentagon), London and North Africa. In the middle of summer systems appeared in other countries of the world.
SIGSALY is considered to be the official date of installation and commencement of work on July 15, 1943, shortly after the invasion of Sicily. On that day, at a meeting on the occasion of the launch of the machines at the Pentagon, those present were Lieutenant-General T. McNarni, President of BTL, Lieutenant-General Bregon Somervell.
At the same time, Lieutenant General JL Devers, Major General IH Edwards and others attended the meeting in London. Oliver Buckley, BTL president, gave a short speech to the participants.

The entire SIGSALY terminal consisted of more than 30 racks. About half of these racks were used for the receiver system, while the other half were used for the transmitter system.
The simplified block diagram below shows how SIGSALY works. On the left, an analyzer that converted analog speech to a digital signal, after which the converted signal was encrypted and modulated onto the transmitter. The encryption key was created on a one-time key (one-time) resembling a regular gramophone record disc recorded on devices for recording encrypted disks. An important condition was the need to establish identical cipherdisks, to ensure the same speed of their rotation and synchronization of the generation of key sequences on both sides of the radio link. Therefore, it was necessary to synchronize the turn-on time of the disk rotation mechanisms.
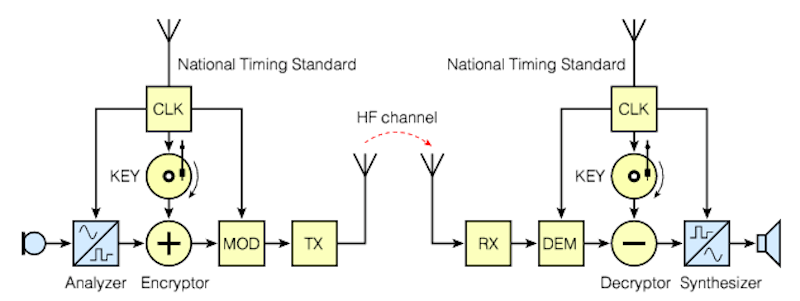
Synchronization of the rotation of the disks at the stations was achieved with the help of transmitted synchronization signals and phase adjustment of the rotational speed of the disk by the operator. After demodulation of the incoming signal, it was decrypted and fed to a speech synthesizer, which converted it into audio analog speech. On each side, the system had two mechanisms for rotating discs, in case the talk time exceeded 12 minutes.
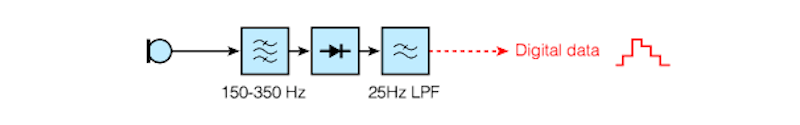
Vocoder is a device for changing human speech by increasing the bandwidth of voice information transmission channels (telephone lines) by reducing the necessary bandwidth of frequencies. In the analysis, the original signal was split across the spectrum (150 Hz - 2950 Hz) into 10 equal frequency bands, in each of which the change in amplitude was monitored. A so-called linear rectifier was used, a low-pass filter of 25 Hz was used to smooth the ripple.
A separate system was used to determine vocalized (such as a, e, o) or unvoiced (such as s, f, k) signals.

As a result, there were 12 low-frequency data channels that were sent to the receiving terminal for synthesizing into human speech. If the original sound was unvoiced, the synthesizer generated white noise (stationary noise, the spectral components of which are evenly distributed over the whole range of frequencies involved). The speech synthesizer repeated the amplitude changes in the same frequency bands - and as a result, the source code, the original speech, was recreated.
The above diagram shows the 11 data transmission channels, they are marked with red dotted lines and contain analog information, such data cannot be sent over a narrow-band radio channel, and it is not easy to encrypt them. This problem is solved in several steps by converting information. This process is known as quantization. In the SIGSALY system, the data was converted into 6 (non-linear) steps.

The original (analog) signal in the diagram is indicated by a black line. This signal is “sampled” at a certain interval on one of 6 levels (marked in red). Each of the 10 frequency / amplitude signals is quantized separately. In the BTL laboratory, quantization was called STEPPING, and the sampling scheme itself was called STEPPER. In terminology, the process is known as pulse code modulation.
Speech recognition (namely, the fundamental frequency of the human voice) is a slightly more complex process than conversion. The first experiments of BTL showed that for a good reproduction of a speech signal a greater number of quantization levels are needed than 6 steps, ideally more than 30 steps. The solution was found - the use of two 6-level channels for transmission.
In the digital system SIGSALY timing (determining the point in time) was of paramount importance. For the system to work correctly, a prerequisite was the synchronized operation of the mechanisms for rotating cipherdisks during the entire conversation on two sides of the Atlantic. It was necessary to take into account the fact that the radio communication could stop - since the distance was 14,000+ km. Initially, this seemed to be a difficult task, but in reality everything turned out to be much simpler, the sampling rate of 20 ms (50 Hz) was chosen.
All that was required to ensure the stability of the rotational speed of the discs was the presence and use of reference oscillators with quartz frequency stabilization. As soon as both systems were synchronized, they remained “in this state” for several hours. Short-term signal loss was not a problem for the sampling rate, and long-term could easily be compensated. BTL engineers have developed an automatic frequency correction system (AFC).
In practice, synchronization has never caused serious problems. Even if the signal disappeared completely due to atmospheric conditions, the system worked correctly after the transmission was restored. Timing was critical for the key receiving mechanism.

Generation and duplication of key material are the most important components of the system, it was they who determined the level of encryption security. Each part of a key or step had to be random, and a random sequence of keys was never repeated. For each of the 12 transmission channels, a separate stream of random keys was required, using the same key for all transmission channels would mean nothing more than a cryptographic vulnerability.
A random set of keys was created by using white noise. In fact, a gas-discharge noise device, a glass tube filled with an inert gas with a heated cathode, was used as a source of noise.
BTL was decided to write the keys on encrypted disks (the most reliable and stable key reproduction process). Such a process required precise adjustments, synchronization of all processes of recording mechanisms in time.
As a result of the quantization of the noise signal, a pseudo-random sequence of signals was formed, which were recorded on a vinyl record with the number of quantization levels in amplitude equal to 6.

The key material was recorded on cipher-disks of rotating devices from key streams of 12 transmission channels.

Since each record on the disk could hold only 12 minutes of key material, longer such conversations required several such cipherdisks. To ensure uninterrupted operation of the system and recording, two rotating recording mechanisms with two cipro-disks were used for replication.
The disks had to be the same and run in exactly the same position and at the same time, they were marked with index marks. Operators on both sides should have placed the needle in the correct groove with an index mark. The reading of the key material from the cipher disc occurred during its rotation: the pickup head was moved and the mechanical oscillations of the needle were converted into electrical signals with a certain amplitude.
At the end of each recording of the key material, a pilot signal was sounded to mark the beginning of the recording of the key material on a cipher plate located on the second rotating mechanism.
Although the use of one-time (One-Time) records with randomly generated keys guaranteed absolute encryption security, the production of such shafrodisks was expensive, and each disc / disc contained only 12 minutes of recording time. Therefore, BTL engineers developed a mechanical device with multiple electrical relays that created a pseudo-random key. Of course, such a device (SIGNAL TRANSMISSION WITH SECRECY) has never been used for negotiations at the state level.
Because of the noise that the device created during operation, it was affectionately called the “destruction machine”. The operation of the device is described in detail in US patent 3,937,888 (filed in 1943 and kept secret for more than 31 years until 1975). The car was known as the Alternative Key (AK), later - SIGBUSE. It was used to service less important conversations, as it had a low level of reliability. If during the recording of phonograms the synchronization was lost, the call was immediately terminated.
Later, protocols based on MFSK (Multi-Shift Frequency Keying) began to be used, they were effective for distant HF communications in the presence of interference. The implementation of MFSK required the solution of many new problems and tasks.

Alan Turing
Alan Turing, a British mathematician - Enigma encryption machine, Bombe - was partially involved in the development of the SIGSALY system. In November 1942, he went on a two-month trip to the United States to help work on the Enigma burglary (the M4 was used in the navy).

Enigma (M4)
In the first week of his stay in America, he visited Benjamin DeForest Bailey in New York, with whom he discussed the security of Telekrypton, an old Western Electric encryption machine. Bailey was working on a Rockex cryptographically unbreakable machine.

Rockex
In addition, during his trip, Turing visited BTL, where he was able to observe the process of developing a voice encryption system. The scientist acknowledged the importance of the work done by BTL. The security of the system was not in doubt, although he did not quite like the reservation that SIGSALY would be serviced exclusively by US personnel, yet he gave his consent to install such a device in London.
Turing's approval played an important role in the further development and strengthening of US-British relations, and the Anglo-American agreement (May 1943) on military and economic cooperation (BRUSA) was signed later. Upon returning home, Alan began developing Delilah, a similar SIGSALY system. Although Delilah was never put into production, Turing shared some of his ideas with BTL, these ideas (possibly) were used to improve the SIGSALY system.
The name of the system SIGSALY was not an abbreviation, the first prototype was named The Green Hornet / Green Hornet, because of the buzzing sound. The system was also called: System X, Project X, Ciphony I. In total, 12 SIGSALY terminals were installed and installed worldwide. The following SIGSALY locations have been confirmed:
, SIGSALY « » , , , SIGSALY , . ( 448 ) .
As advertising. These are not just virtual servers! This is a VPS (KVM) with dedicated drives, which can be no worse than dedicated servers, and in most cases - better! We made VPS (KVM) with dedicated drives in the Netherlands and the USA (configurations from VPS (KVM) - E5-2650v4 (6 Cores) / 10GB DDR4 / 240GB SSD or 4TB HDD / 1Gbps 10TB available at a uniquely low price - from $ 29 / month , options are available with RAID1 and RAID10) , do not miss the chance to place an order for a new type of virtual server, where all resources belong to you, as on a dedicated one, and the price is much lower, with a much more productive hardware!
How to build the infrastructure of the building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny? Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA!

Bell Telephone Laboratories (BTL) - an American research company, was founded in 1925. Initially, it was a union of Western electrical research laboratories and the engineering department of the American Telephone and Telegraph Company (AT & T). Over its history, the company bore various names: Bell Laboratory, Bell Telephone Laboratories, Bell Telephone Labs, Bell Labs, AT & T Bell Laboratories, AT & T Bell Labs, Lucent Technologies, Bell Labs Innovations. At the moment - Nokia Bell Labs.

BTL has many important inventions and developments: radio astronomy, transistor, laser, photovoltaic cell, charge-coupled device (eng. CCD, Charge-Coupled Device), the first versions of the UNIX operating system and programming languages C and C ++. In the war years, the Bell laboratory developed the unbreakable telephone system, SIGSALY, to transfer messages between Allied forces.

The SIGSALY system embodied a number of innovative digital communication concepts, including the first pulse code modulation (PCM / PCM), which is used to digitize analog signals.
The SIGSALY system consisted of more than 30 equipment racks, 4 disk rotation mechanisms (two on each side). The system weighed 50 tons, and consumed such a machine of 30 kW. In 1943, the cost of one such terminal was 1 million US dollars. A total of 12 SIGSALY terminals installed worldwide, the first system in the Pentagon.
The second system was installed in London, in the basement of Selfridges department store in London on the famous Oxford Street. Another system worked on a ship plying the ocean under the command of General Douglas MacArthur (during the times of the Pacific campaigns). Although MacArthur was plagued by doubts about the reliability of classifying telephone conversations, he preferred to use the direct-printing SYGTOT radio communications equipment with preliminary encryption of information. After installation, the systems were serviced by specially trained and reliable members of the 805 communications company of the United States Armed Forces. During the period 1943 - 1946, over 3,000 telephone conversations at the highest state level were conducted by means of 12 working terminals SIGSALY.
SIGSALY provided full-duplex voice communication over high-frequency (HF) radio channels in the HF band. Each half of the channel used 12 separate data channels or carrier frequencies, MFSK (Multi-Shift Frequency Keying) data transmission protocols were used, such protocols did not have a range limitation and were resistant to interference occurring on the low-frequency HF bands.
Human speech was analyzed only 50 times / second, every 20 ms it was broken up into components, and then encoded and sent across the Atlantic. On the receiving side, the data was decoded, restored, after which the original speech was reproduced.
As a result of the low data transfer rate (today comparable to 1500 baud) it was difficult to recognize a person by voice at the other end. Later the technology was improved, other speech coding algorithms appeared, such as LPC-10, CELP and MRELP (for example, in STU-I equipment).
After the system was ready, the BTL developers conducted the rest of the war, working on the successor to SIGSALY, known as Junior X or AN / GSQ-3. Junior X was planned as a mobile version and occupied "only" six racks, could be installed in a mobile van, but the project was never completed on time, and therefore was not used. After the war, the SIGSALY system was decommissioned, partially destroyed, including documentation, the racks were thrown overboard in 1946.
Disk rotation mechanisms

The SIGSALY system used a cryptographically unbreakable coding scheme based on the so-called OTP (One-Time Pad / disposable notebook)
The principle of this scheme was as follows: the human voice was initially digitized, then mixed with an element from a previously randomly generated key stream. When properly applied, such a system could be unbreakable. The main requirement is that both parties should have a sufficient amount of key material.
In the SIGSALY system, a random key stream was recorded on encrypted disks. Only two copies of records were made, one copy was sent by a special courier to the other end of the line. Since each disc could contain only 12 minutes of key material, accordingly, more than one such disc and the correct distribution of key material were required for long conversations.
In addition to the key distribution problem, there was another difficulty - synchronization. At the two ends of the radio link, not only identical cipher-disks had to be installed, but they also had to work at the same rotational speed in order to ensure synchronization of key sequences generation.
As mentioned earlier, the record contained 12 minutes of key material, two synchronized encryption disks were used, the second was a replica of the first one. Since SIGSALY was a full duplex system, each terminal had four players: two transmitters and two receivers. Vinyl records were originally used (1943). They had a code name - SIGGRUV. Later they were replaced by thin-coated aluminum plates of acetate varnish codenamed SIGJINGS.
Such plates with SIGGRUV and SIGJINGS records are called OTP records or disposable records (OTR). After use, such records were immediately destroyed, so that the enemy could never decipher any part of the secret conversation.
SIGSALY system in Washington

The first SIGSALY terminal was installed at the Pentagon (Washington, USA), the new headquarters of the US Department of Defense, whose construction was completed in January 1943. It was originally planned to place the car in the White House, but because of its size, this idea was rejected. Instead, the Pentagon became the home of SIGSALY, and an additional line of communication was laid to the presidential residence. After installation, 805 communications companies of the United States Armed Forces took up maintenance. The members of the company were selected and underwent special training from BTL employees at a special school established for this purpose in New York. In 1944, except for the 805 company, and the school itself was moved to the Pentagon. 193 officers were trained in the use of SIGSALY. 805 company consisted of 356 people: 81 officers and 275 soldiers, who were divided into 12 troops. In each detachment there were 5 officers and 10 servicemen. They followed the work of the system 24/7.
London SIGSALY system

In the UK, the SIGSALY system was located in the SWOD basement to Selfridges department store on Oxford Street (London). The first conference was held on July 15, 1943; British Prime Minister Winston Churchill was among the users of this machine.
The image above is the main building of the Selfridges department store on Oxford Street (1929) ten years before the start of World War II. At the time, the Selfridges building had a basement known as SWOD, it was named after the four roads that surrounded it: Somerset, Wigmore, Orchard and Duke (the last three streets still exist). So this basement had its basement 60 meters below the ground. In 1942, after the United States entered World War II, the SWOD basement room was used by the United States Army because the room was a safe bomb shelter. Here we had a secure communication line, and in April 1943 we installed the SIGSALY terminal. The first negotiations between the two countries probably concerned the Allied invasion of Sicily and the upcoming invasion of Italy.

The map above shows that Selfridges basement was located close to the US Embassy. Even today there are rumors about a tunnel between two objects. Initially, in order to use SIGSALY for a safe conversation with the US president, Selfridges had to come, later the system was connected via extended lines to the US embassy, to the office of British Prime Minister Winston Churchill on Downing Street, to the bunker. Churchill could, if necessary, contact the US president at any time of the day or night.
Extension lines
Because of its size, the SIGSALY system, as a rule, was not installed in the office, but was located, as a rule, in large rooms nearby. The offices, in turn, were connected to the SIGSALY terminal through special protected extension lines, known as OPEPS.

OPEPS is short for Off-Premises Extension Privacy System. In Washington, two OPEPS lines were conducted from the Pentagon to the White House and to the building of the Naval Ministry (USA). In London, three such lines were carried out: one to the US embassy, the other to the cabinet of British Prime Minister Winston Churchill on Downing Street, and the third to the bunker (Church War Cabinet).

Since these extended lines allowed “top-secret traffic” to pass through at a high state level, various security measures had to be applied to protect them from both wiretapping and external interference. Cables and connections between SIGSALY and its extended lines have been protected using gas and microswitches. Any interference led to a drop in gas pressure, which triggered the alarm. At the slightest interference, an imbalance occurred on the line, causing strong noise interference, the user heard noise and understood that the line was unsafe at that moment.
Do not confuse OPEPS with the SIGSALY system, the lines connecting the system with Secraphone - known as the scrambler. Although both phones looked the same and served similar purposes, Secraphone was not so secure and protected. It was used to protect against accidental eavesdropping, for example, by a telephone exchange operator, but not against professional wiretapping. Synonym for him is confidentiality, but not secrecy.

Secraphone

A bit of history
At the beginning of World War II, the United States Armed Forces used the A-3 voice scrambler developed by Western Electric for state-level negotiations. The A-3 scrambler was used by both sides during the war, although it was known that it did not have a sufficient measure of reliability and security, the information could be easily intercepted and cracked using simple tools such as a regular oscilloscope. The fact remained a fact, and the issue of creating a secure connection reached its climax. As early as October 1940, Bell Telephone Laboratories (BTL) began the development of an unbreakable transatlantic voice telephony system called Project X.
In Bell, the study was carried out by two teams: one conducted basic research, and the second was engaged in solving practical problems of design, construction, and instruction. During the research, Peterson and Dudley's works on the invention and principle of operation of the vocoder were taken.
Vocoder Dudley, dubbed Voder 3, was demonstrated by BTL at the New York World's Fair in 1939, the company showed how, by analyzing the speech signal, the voice path is modeled by a shaping filter. Vocoder compressed 10: 1 voice bandwidths. The device determined the main parameters of the signal, encoded them and transmitted the radio signal via short-wave channels. Such a digital encryption system is similar to that developed by Gilbert Vernam.

But before the secure, secure transatlantic telephone system saw the world, it was necessary to solve many technical and mathematical problems. Numerous tests and experiments were conducted, as a result of which it was decided to combine the principles of operation of the vocoder and the device for encrypting alphanumeric information. The frequency spectrum (150 Hz - 2950 Hz) was divided into 10 channels, each of which was digitized.
In the process of developing the system and solving its problems, many discoveries and inventions were made, a considerable number of (secret) patents were filed, some of which for 35 years remained under the “secret” stamp.

By the end of 1941, the designs of individual parts of the system were more or less ready, and the layouts were created. The next stage - the creation of a prototype - was taken up by the AM Curtis research group. The system was assembled on the 12th floor of the Graybar-Varick building in New York.

Graybar-Varick, New York
In fact, Western Electric (WE) was involved in the production of machines. BTL engineers used standard spare parts from WE, which were easily accessible, and not “original-designed” parts for the machine. Because of this, the dimensions of the system have increased, but this significantly reduced the time to manufacture.
The system included 12 parallel data transmission channels. In March 1942, the data channel was tested using a signal level control, imitating a transatlantic radio. In April 1942, after the successful completion of the tests, they set up the remaining channels. The experimental model of the system was completed by the end of the summer of 1942.
In November of the same year, the system was first tested on transatlantic radio, later the system was tuned and improved.
The prototype was nicknamed The Green Hornet / Green Hornet, in honor of the popular radio show of the 1930s with the same name. The melody of the show was reminiscent of a buzzing sound, reminiscent of sound when transmitting coded signals.

It is necessary to emphasize the fact that all work was initiated by BTL, although both the National Defense Research Committee and the Corps of Communications were aware of the work, they became interested in this program as early as 1942. After completing work on an experimental model, the Corps of Communications Troops sponsored the development of several terminals. From that moment on, the project began to carry the code name SIGSALY.
After completing and testing some parts of the Western Electric system, they were sent to Room L30 on West Street, the former sound film lab, where they were assembled into a single system. Work on the first system was completed on April 1, 1943, the second system was soon ready, and this allowed the first real test to be carried out.
At the end of April 1943, the first terminals were installed in Washington (Pentagon), London and North Africa. In the middle of summer systems appeared in other countries of the world.
SIGSALY is considered to be the official date of installation and commencement of work on July 15, 1943, shortly after the invasion of Sicily. On that day, at a meeting on the occasion of the launch of the machines at the Pentagon, those present were Lieutenant-General T. McNarni, President of BTL, Lieutenant-General Bregon Somervell.
At the same time, Lieutenant General JL Devers, Major General IH Edwards and others attended the meeting in London. Oliver Buckley, BTL president, gave a short speech to the participants.
SIGSALY system overview. Technical description

The entire SIGSALY terminal consisted of more than 30 racks. About half of these racks were used for the receiver system, while the other half were used for the transmitter system.
The simplified block diagram below shows how SIGSALY works. On the left, an analyzer that converted analog speech to a digital signal, after which the converted signal was encrypted and modulated onto the transmitter. The encryption key was created on a one-time key (one-time) resembling a regular gramophone record disc recorded on devices for recording encrypted disks. An important condition was the need to establish identical cipherdisks, to ensure the same speed of their rotation and synchronization of the generation of key sequences on both sides of the radio link. Therefore, it was necessary to synchronize the turn-on time of the disk rotation mechanisms.

Synchronization of the rotation of the disks at the stations was achieved with the help of transmitted synchronization signals and phase adjustment of the rotational speed of the disk by the operator. After demodulation of the incoming signal, it was decrypted and fed to a speech synthesizer, which converted it into audio analog speech. On each side, the system had two mechanisms for rotating discs, in case the talk time exceeded 12 minutes.
Vocoder

Vocoder is a device for changing human speech by increasing the bandwidth of voice information transmission channels (telephone lines) by reducing the necessary bandwidth of frequencies. In the analysis, the original signal was split across the spectrum (150 Hz - 2950 Hz) into 10 equal frequency bands, in each of which the change in amplitude was monitored. A so-called linear rectifier was used, a low-pass filter of 25 Hz was used to smooth the ripple.
A separate system was used to determine vocalized (such as a, e, o) or unvoiced (such as s, f, k) signals.

As a result, there were 12 low-frequency data channels that were sent to the receiving terminal for synthesizing into human speech. If the original sound was unvoiced, the synthesizer generated white noise (stationary noise, the spectral components of which are evenly distributed over the whole range of frequencies involved). The speech synthesizer repeated the amplitude changes in the same frequency bands - and as a result, the source code, the original speech, was recreated.
Analog to digital conversion. Quantization
The above diagram shows the 11 data transmission channels, they are marked with red dotted lines and contain analog information, such data cannot be sent over a narrow-band radio channel, and it is not easy to encrypt them. This problem is solved in several steps by converting information. This process is known as quantization. In the SIGSALY system, the data was converted into 6 (non-linear) steps.

The original (analog) signal in the diagram is indicated by a black line. This signal is “sampled” at a certain interval on one of 6 levels (marked in red). Each of the 10 frequency / amplitude signals is quantized separately. In the BTL laboratory, quantization was called STEPPING, and the sampling scheme itself was called STEPPER. In terminology, the process is known as pulse code modulation.
Speech recognition (namely, the fundamental frequency of the human voice) is a slightly more complex process than conversion. The first experiments of BTL showed that for a good reproduction of a speech signal a greater number of quantization levels are needed than 6 steps, ideally more than 30 steps. The solution was found - the use of two 6-level channels for transmission.
Synchronization
In the digital system SIGSALY timing (determining the point in time) was of paramount importance. For the system to work correctly, a prerequisite was the synchronized operation of the mechanisms for rotating cipherdisks during the entire conversation on two sides of the Atlantic. It was necessary to take into account the fact that the radio communication could stop - since the distance was 14,000+ km. Initially, this seemed to be a difficult task, but in reality everything turned out to be much simpler, the sampling rate of 20 ms (50 Hz) was chosen.
All that was required to ensure the stability of the rotational speed of the discs was the presence and use of reference oscillators with quartz frequency stabilization. As soon as both systems were synchronized, they remained “in this state” for several hours. Short-term signal loss was not a problem for the sampling rate, and long-term could easily be compensated. BTL engineers have developed an automatic frequency correction system (AFC).
In practice, synchronization has never caused serious problems. Even if the signal disappeared completely due to atmospheric conditions, the system worked correctly after the transmission was restored. Timing was critical for the key receiving mechanism.
As a result of the analog-to-digital conversion, the amplitude value of the signal in each of the bandpass filters was encoded with one hexadecimal digit, and the frequency and type of the excitation signal — two hexagonal digits. Simultaneously with the determination of the digital parameters of the speech signal, a key pseudo-random sequence of hexadecimal digits was generated in the developed equipment. As a result of summing modulo 6 telephone signal parameters with a key sequence, the transmitted message was automatically encrypted.

Generation and duplication of key material are the most important components of the system, it was they who determined the level of encryption security. Each part of a key or step had to be random, and a random sequence of keys was never repeated. For each of the 12 transmission channels, a separate stream of random keys was required, using the same key for all transmission channels would mean nothing more than a cryptographic vulnerability.
A random set of keys was created by using white noise. In fact, a gas-discharge noise device, a glass tube filled with an inert gas with a heated cathode, was used as a source of noise.
BTL was decided to write the keys on encrypted disks (the most reliable and stable key reproduction process). Such a process required precise adjustments, synchronization of all processes of recording mechanisms in time.
As a result of the quantization of the noise signal, a pseudo-random sequence of signals was formed, which were recorded on a vinyl record with the number of quantization levels in amplitude equal to 6.

The key material was recorded on cipher-disks of rotating devices from key streams of 12 transmission channels.
Rotating mechanisms for writing encrypted disks

Since each record on the disk could hold only 12 minutes of key material, longer such conversations required several such cipherdisks. To ensure uninterrupted operation of the system and recording, two rotating recording mechanisms with two cipro-disks were used for replication.
The disks had to be the same and run in exactly the same position and at the same time, they were marked with index marks. Operators on both sides should have placed the needle in the correct groove with an index mark. The reading of the key material from the cipher disc occurred during its rotation: the pickup head was moved and the mechanical oscillations of the needle were converted into electrical signals with a certain amplitude.
At the end of each recording of the key material, a pilot signal was sounded to mark the beginning of the recording of the key material on a cipher plate located on the second rotating mechanism.
Alternative solution: SIGBUSE
Although the use of one-time (One-Time) records with randomly generated keys guaranteed absolute encryption security, the production of such shafrodisks was expensive, and each disc / disc contained only 12 minutes of recording time. Therefore, BTL engineers developed a mechanical device with multiple electrical relays that created a pseudo-random key. Of course, such a device (SIGNAL TRANSMISSION WITH SECRECY) has never been used for negotiations at the state level.
Because of the noise that the device created during operation, it was affectionately called the “destruction machine”. The operation of the device is described in detail in US patent 3,937,888 (filed in 1943 and kept secret for more than 31 years until 1975). The car was known as the Alternative Key (AK), later - SIGBUSE. It was used to service less important conversations, as it had a low level of reliability. If during the recording of phonograms the synchronization was lost, the call was immediately terminated.
Later, protocols based on MFSK (Multi-Shift Frequency Keying) began to be used, they were effective for distant HF communications in the presence of interference. The implementation of MFSK required the solution of many new problems and tasks.

Alan Turing
Alan Turing, a British mathematician - Enigma encryption machine, Bombe - was partially involved in the development of the SIGSALY system. In November 1942, he went on a two-month trip to the United States to help work on the Enigma burglary (the M4 was used in the navy).

Enigma (M4)
In the first week of his stay in America, he visited Benjamin DeForest Bailey in New York, with whom he discussed the security of Telekrypton, an old Western Electric encryption machine. Bailey was working on a Rockex cryptographically unbreakable machine.

Rockex
In addition, during his trip, Turing visited BTL, where he was able to observe the process of developing a voice encryption system. The scientist acknowledged the importance of the work done by BTL. The security of the system was not in doubt, although he did not quite like the reservation that SIGSALY would be serviced exclusively by US personnel, yet he gave his consent to install such a device in London.
Turing's approval played an important role in the further development and strengthening of US-British relations, and the Anglo-American agreement (May 1943) on military and economic cooperation (BRUSA) was signed later. Upon returning home, Alan began developing Delilah, a similar SIGSALY system. Although Delilah was never put into production, Turing shared some of his ideas with BTL, these ideas (possibly) were used to improve the SIGSALY system.
Summing up
The name of the system SIGSALY was not an abbreviation, the first prototype was named The Green Hornet / Green Hornet, because of the buzzing sound. The system was also called: System X, Project X, Ciphony I. In total, 12 SIGSALY terminals were installed and installed worldwide. The following SIGSALY locations have been confirmed:
- Washington (United States, Pentagon)
- (, Selfridges)
- Algeria
- ()
- - ()
- (, )
- (, )
- (, )
- ( ) 1 ➤
- (, )
- (, )
- (, )
- ()
, SIGSALY « » , , , SIGSALY , . ( 448 ) .
As advertising. These are not just virtual servers! This is a VPS (KVM) with dedicated drives, which can be no worse than dedicated servers, and in most cases - better! We made VPS (KVM) with dedicated drives in the Netherlands and the USA (configurations from VPS (KVM) - E5-2650v4 (6 Cores) / 10GB DDR4 / 240GB SSD or 4TB HDD / 1Gbps 10TB available at a uniquely low price - from $ 29 / month , options are available with RAID1 and RAID10) , do not miss the chance to place an order for a new type of virtual server, where all resources belong to you, as on a dedicated one, and the price is much lower, with a much more productive hardware!
How to build the infrastructure of the building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny? Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA!
All Articles